A Modern Approach to Risk Management and Compliance
Last updated on: January 27, 2021
For far too long, organizations had to rely on traditional Governance, Risk and Compliance (GRC) tools — with their modular and siloed approach — to address their risk management and reporting compliance posture. With an increasing number of organizations looking at the Integrated Risk Management (IRM) path, it’s clear they want a scalable and dynamic way to define the scope of risk and audits, whether it’s for the assets or the controls. They also want the ability to aggregate insights from security assessments and to communicate risk and compliance in real time, as I explained in my Qualys Security Conference presentation “A Modern Approach to Risk Management and Compliance.”
However, a mere name change from GRC to IRM is not enough. You need a risk management program that truly integrates processes such as:
- Definition of your harmonized list of control objectives, derived from all your compliance requirements and risk objectives
- Automatic operationalization of these controls through security tools for your in-scope IT assets, vendors, and processes
- Automated correlation of insights and reporting for audit and compliance along with risk-based prioritization, consolidating vendor risk with your technical and procedural control risk
- Continuous optimization and improvement by, for example, starting IRM process in CI/CD from the source itself
Although this sounds good in theory, the reality is that these processes are usually not integrated. Our customers tell us the main reason these processes are performed in silos is because of the tools supporting them. Customers still must rely on an average of 25 IRM (previously GRC) point solutions for defining controls and performing assessments. Then they must rely on expensive orchestrations and scripts for correlating data and re-mapping it against compliance requirements for reporting to auditors. In such a scenario, bringing this compliance assessment process in CI/CD appears to be a distant dream.
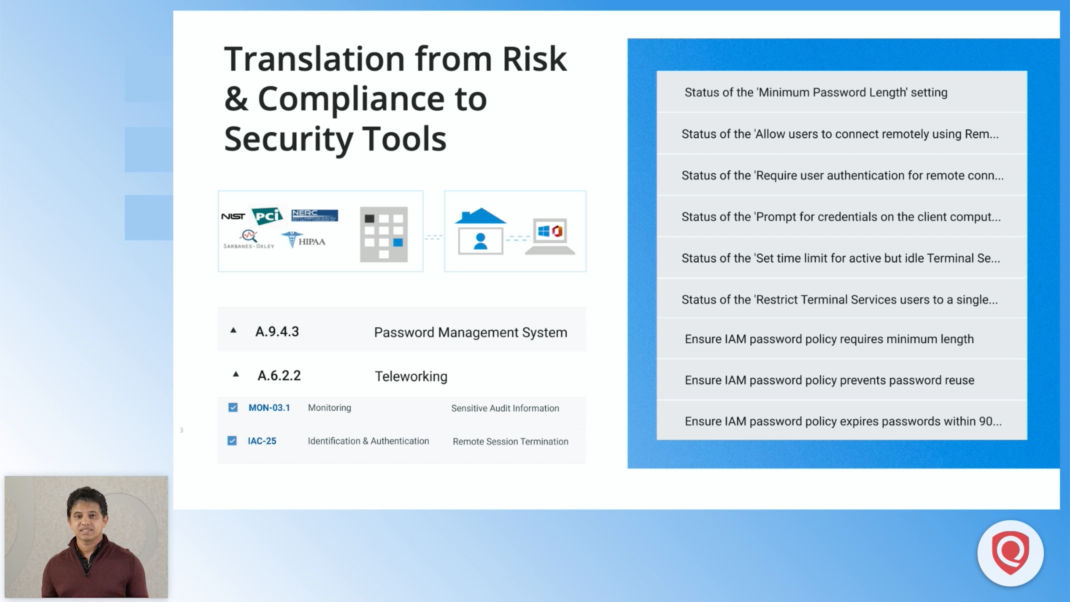
For example, imagine if you have to operationalize and report against a simple control like password management from compliance mandates such as PCI-DSS or HIPAA or FedRAMP (NIST). You’ll have to put in a tremendous amount of work, since password management must be performed for all your ‘in-scope’ assets in the cloud and on premises, including containers, databases, emerging technologies, and mobile devices. For this, you would bring in various tools and define a baseline of granular password checks, like requiring that default passwords be changed, or establishing password strength criteria. You would have to establish password policies in IAM cloud security tools, data center configuration assessment tools, mobility security tools and more.
Adding to the complexity is the issue of asset scope, which is one of the top reasons auditors find compliance faults. Specifically, compliance and security teams struggle to discover and include all in-scope assets and data in their assessment. You will also need to run a vendor risk campaign to poll them about their password policies. With the increasing use of SaaS apps, you will have to use yet another tool to check your SaaS apps’ password settings.
It’s a struggle all the way to the end of the process when it’s time to generate the final report. Because the data is siloed, teams have to use scripts to manually correlate and merge the data from various reports and spreadsheets just to show the posture of your password management control. Most of the compliance analysts I have talked to say that more than half of their time is spent operationalizing the control or correlating data from dispersed tools in spreadsheets. This makes the compliance job less about research and risk algorithms and more about operations.
In response to these difficulties, Qualys is building a unified risk and compliance capability on the same platform which enables real-time continuous assessment of your assets across your hybrid environment. With Qualys, you’ll be able to streamline and automate key compliance requirements outlined in the CIS Top 20 Controls, such as asset inventory, vulnerability and configuration management, checking and controlling of privileged administrative access, and analysis of logs.
Qualys Unified Risk and Compliance
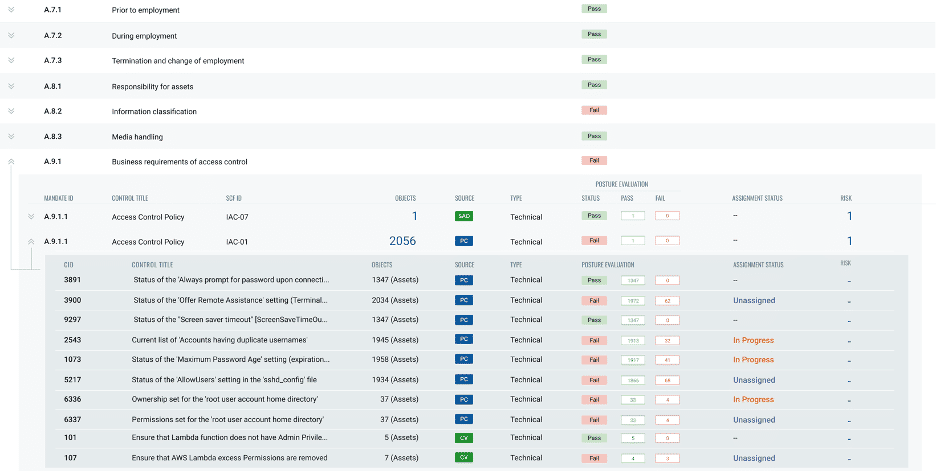
With Qualys Unified Risk and Compliance, you can:
- Define technical and procedural controls for your compliance and security policies.
Leveraging the control library of Secure Control Framework (SCF), you can simply select your compliance controls defined by your auditor mandates as a profile. The Qualys research team has cross-mapped SCF and compliance controls to various Qualys apps and their checks, queries and reports. - Automatically drive assessment through underlying Qualys apps such as Qualys VMDR, Policy Compliance, CloudView, IT Asset Inventory, and more.
As soon as your profile of controls is defined, a baseline of granular checks will be automatically pushed to various Qualys apps for operationalizing scans and evaluations. - Report security data generated by Qualys apps against compliance and risk in real time.
As data and reports from Qualys apps are already mapped against your profile, you will get a real-time view of your compliance posture on an ongoing basis. This eliminates the need to do correlation in spreadsheets.
For more information or if you want to see this capability in play for managing your end-to-end compliance audit, be it for PCI-DSS or FedRAMP, please contact your TAM to learn more.
We are continuously adding new functionalities to the existing Qualys compliance apps to cover your risk blind spots.
Policy Compliance
Qualys Policy Compliance, a configuration compliance space leader, covers 250+ technologies for 15000+ controls, 50% more than CIS benchmark checks. It’s increasingly leveraged by security teams to add context to security, especially for managing overall remote endpoint security risks.
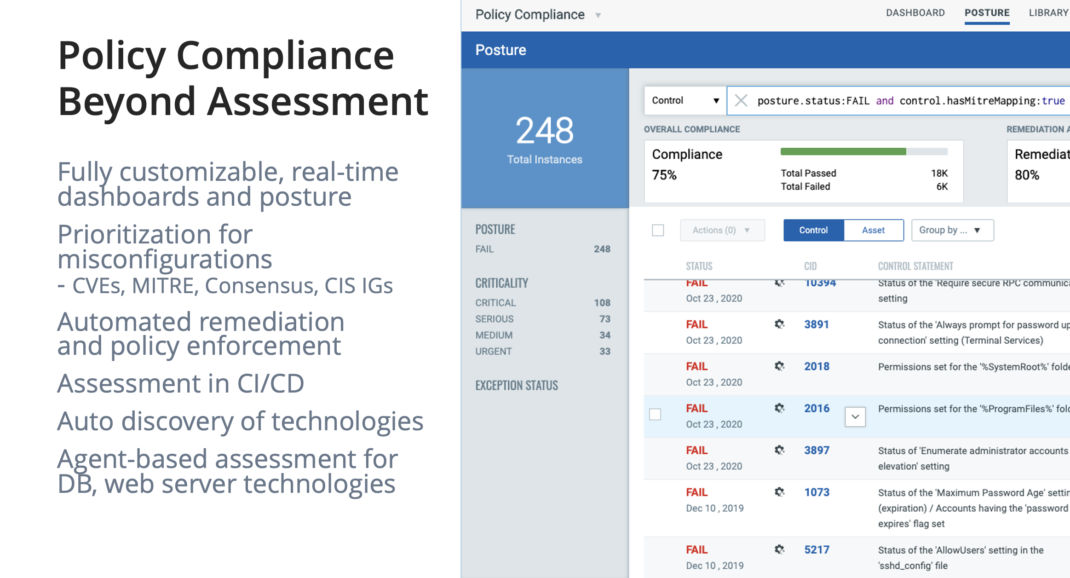
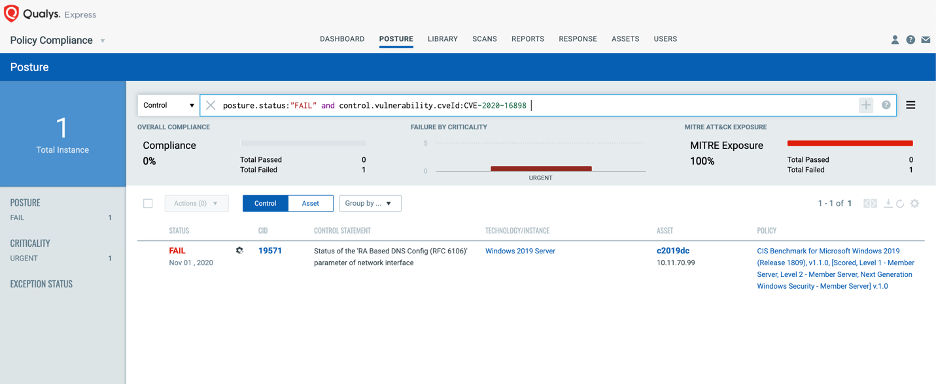
A new version of Qualys Policy Compliance will be out by the end of this year, with a brand-new UI and backend. You’ll be able to create dynamic dashboards, and QQL queries on compliance data. But my favorite part is you will be able to prioritize misconfigurations. There’s a standard way for prioritizing vulnerabilities, but there’s never been a good way to prioritize misconfigurations based on your risk. Qualys Policy Compliance will now provide cross-mappings with vulnerability information such as CVEs or Qualys IDs (QIDs). You’ll be able to easily see which controls you can harden to compensate the risk of certain vulnerabilities. With Policy Compliance mappings to MITRE attack techniques, you can now view which controls can help you reduce the risk of malicious attacks.
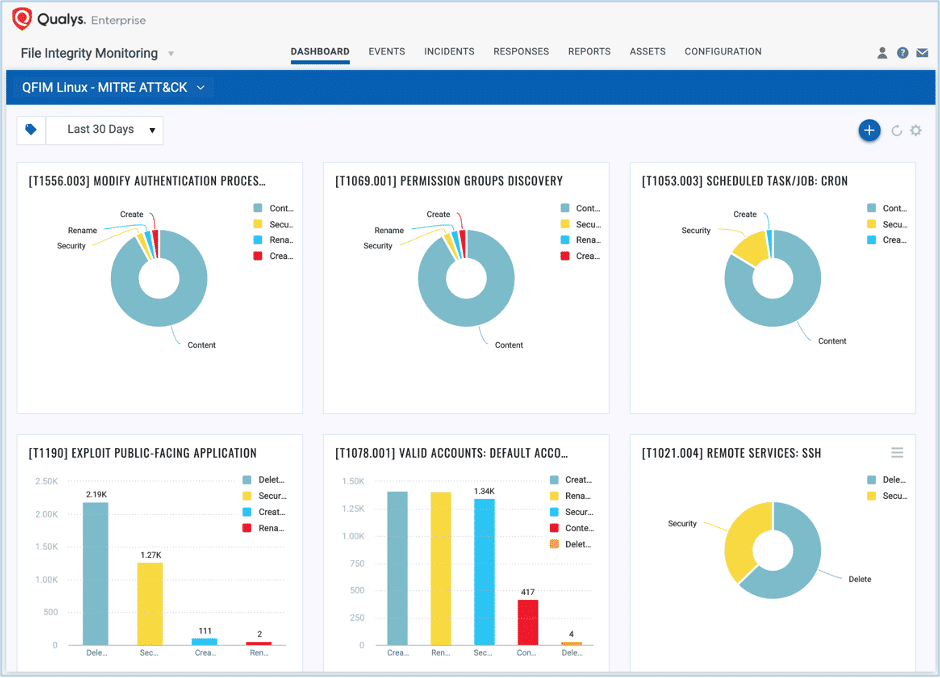
File Integrity Monitoring
With the same Qualys Cloud Agent you are leveraging for vulnerability and configuration management, increasing numbers of security and compliance teams are adopting Qualys File Integrity Monitoring (FIM) for real-time monitoring of critical files at scale. There are a few vulnerability management tools that claim to perform file integrity monitoring. However, these tools neither provide a compliance-driven library of monitoring profiles that define what to monitor, nor do they perform real-time monitoring. The tools are merely driven by hash changes, which does not provide critical information like who changed files, making them unacceptable for compliance programs such as PCI-DSS, FedRAMP and others.
The unique capabilities of Qualys FIM, such as automatically alerting for malicious file creation, based on threat intel and MITRE attack detections, and automatically suppressing event noise for known good changes such as Patch Tuesday, enables security teams to add true context to security monitoring and investigation of malicious attacks such as ransomware.
Sensitive Data Discovery
As more and more attacks result in a data breaches, customers have been asking for the ability to discover critical data. In Q2 2021, Qualys sensors will allow customers to discover sensitive and critical data residing in unstructured form across their hybrid environment, including on-premises data centers, remote user hosts, cloud repositories like S3 buckets, and SaaS apps like Google G suite and Microsoft Office 365. You’ll also be able to automatically group the assets hosting this data with dynamic tagging and classify the data with labels such as PII, PHI and more. With this native capability on the platform, customers can further orchestrate the assessment of vulnerabilities, checking access permissions on data, and monitoring changes to data through various Qualys apps.
Custom Script Manager
Also, in Q2 2021, the Qualys Cloud Platform will open to let customers leverage the Qualys Cloud Agent to execute their scripts, which IT or security teams could use for live operations such as removing Firefox from endpoints or detecting parameters set for their DLP. All such custom scripts can be uploaded, managed for approval, executed and reported for their output on the Qualys Cloud Platform.
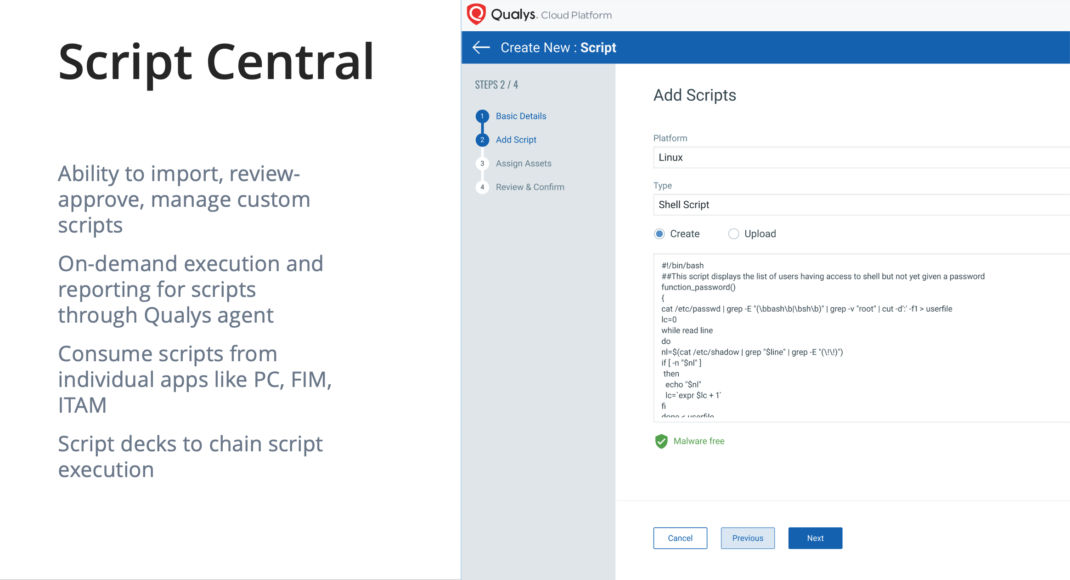
Additionally, these scripts can be consumed by various Qualys apps for their own use cases. For example, you may upload a script to check users in the “/etc/passwd” file format and use an output consumption module as Policy Compliance to pass or fail the custom control if the script’s output contains an unexpected value. You can also use Qualys FIM as a consumption module to continuously check for changes in the output to know if the changes are good or bad.
Unlike some of the tools that support executing scripts, Qualys Script Manager will store your scripts’ output, so you don’t need to flood your endpoints every time you need the output.
More Expansion of Compliance Platform
Qualys compliance apps help compliance teams automate manual processes to better use their time in more valuable tasks, such as conducting compliance research and expanding their auditing scope. The Qualys Cloud Platform will continue to gain more workflows and capabilities so that its compliance assessments add context for security management, as well as accelerate your audit readiness.