Assessing Mainframe Compliance While Minimizing Operational Impact
Last updated on: December 19, 2022
While many in the industry consider mainframes to be inherently secure systems that don’t require additional hardening, this is not the case, according to recent Forrester surveys which reveal that security incidents are commonplace in mainframes.
Mainframes are the backbone of many businesses and often house their most crucial data. 71% of the fortune 500 companies and 90% of the world’s largest banks are heavily dependent on mainframes today. Therefore, it is imperative to have visibility of mainframes alongside other IT assets in a single inventory and be aware of how well these critical systems are prepared for internal and external compliance audits. With these concerns in mind, Qualys now brings mainframes on the radar of your compliance program using Qualys Out-of-Band Configuration Assessment (OCA). In this blog, we will see how OCA effectively evaluates your mainframe’s compliance in a step-by-step manner, presenting a clear picture of the assessment status with the help of widgets on your Qualys dashboard.
Hardening of Mainframes for Secure Configuration
To modernize mainframes and increase the accessibility of these computational giants, there has been an increase in connectivity options like SSH, Customer Information Control System (CICS), FTP, HTTP, etc. All these expand the attack surface of the mainframes. Lack of a single source of truth for listing all vulnerabilities in the mainframes and insufficient skill sets lead to gaps in shielding mainframes against known as well as zero-day vulnerabilities.
External Security Managers (ESM) like RACF, ACF2, and TopSecret help manage access control mechanisms and auditing. For HP Nonstop (Tandem) Servers, security can be managed at the operating system level (Non-Stop OS) or via external applications like Guardian or Safeguard. These ESMs help tighten the security in layers. However, apart from the vulnerabilities in the baseline operating system, the vulnerable applications running on mainframes and the possibility of DDOS attacks on these crucial applications call for hardened configurations and regular assessments.
Updates to operating systems and applications, encryption of data, and giving least privileges to users are some of the generic methods that are also applicable. By following these methods, known risks can be mitigated to a great extent. However, what if the chosen encryption standards are weak, making the data susceptible to access due to weak ciphers? What if the applications can be accessed by illegitimate users violating the principle of least privilege? What if unnecessary classes are installed, thereby expanding the threat surface? What if proper audit trails are not configured, which could hide the malicious actions of intruders? To evaluate all such baseline configurations of settings, it is essential to carry out compliance assessment of mainframes operating systems and ESMs. When hardened with the right configurations, the overall risk posed by known or unknown threats is greatly reduced.
How Qualys OCA Helps Assess Mainframe Compliance
It is often not feasible to perform authenticated scans on any of these servers because of the criticality of the data that they process. Similarly, performance is a crucial factor on these real-time processing systems which means that overhead of scanning them is too high. These challenges are reasonable, but they are not acceptable in a strict compliance regime. This calls for a middle ground, where compliance needs to be assessed against different mandates like PCI, DISA STIG, GDPR, or NIST, again without hampering the performance.
Qualys Out-of-Band Configuration Assessment helps assess these systems using an offline data-push mechanism. OCA doesn’t connect with mainframes directly, nor is Cloud Agent installed on them. Rather, OCA provides connectors to the Qualys Cloud Platform, which are used to push mainframe configuration to the platform. Through OCA, configuration data of IBM z/OS RACF as well as HP Nonstop Systems can be uploaded through UI and API. However, details of the systems such as IP address, hostname, etc., need to be entered in the Qualys Cloud Platform to get a unique identifier for the mainframe. This identifier helps locate your asset in Policy Compliance, in the OCA Asset listing as well as in the global inventory of your assets.
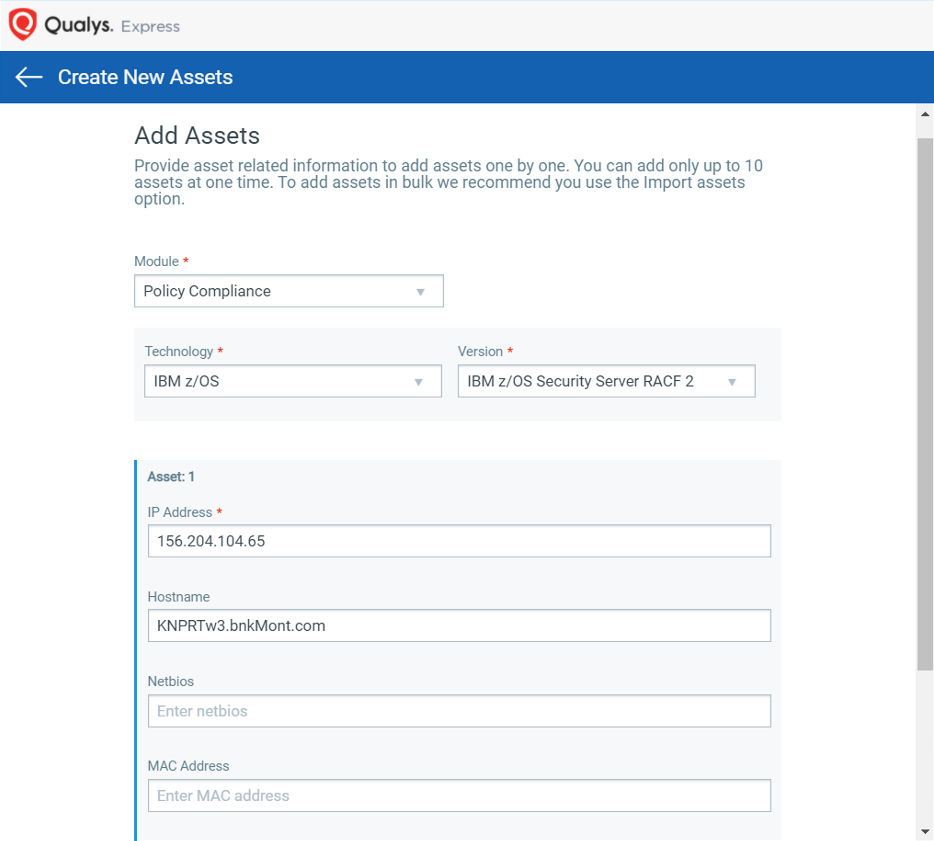
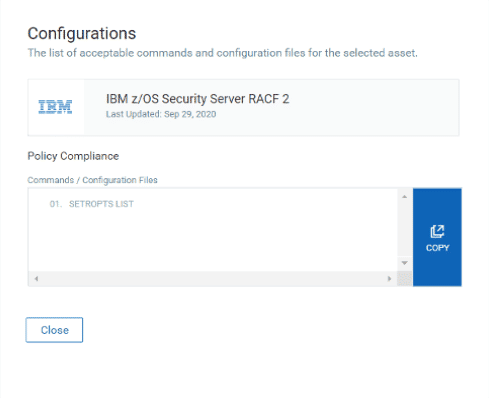
On creating the asset on the Qualys Cloud Platform, a set of commands is prescribed depending on the technology. For example, for RACF, the command that is shown is ‘SETROPTS LIST’.
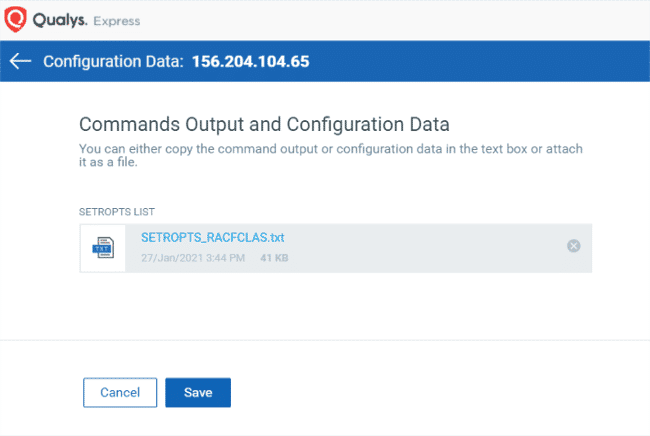
The output of this command needs to be uploaded to the Qualys Cloud Platform. For the concerns mentioned earlier in the blog, Qualys OCA does not directly connect with the mainframe servers. For fetching the output of prescribed commands, customers can have their own automation process or custom scripts. The output then needs to be uploaded to the Qualys Cloud Platform using OCA APIs or the UI.
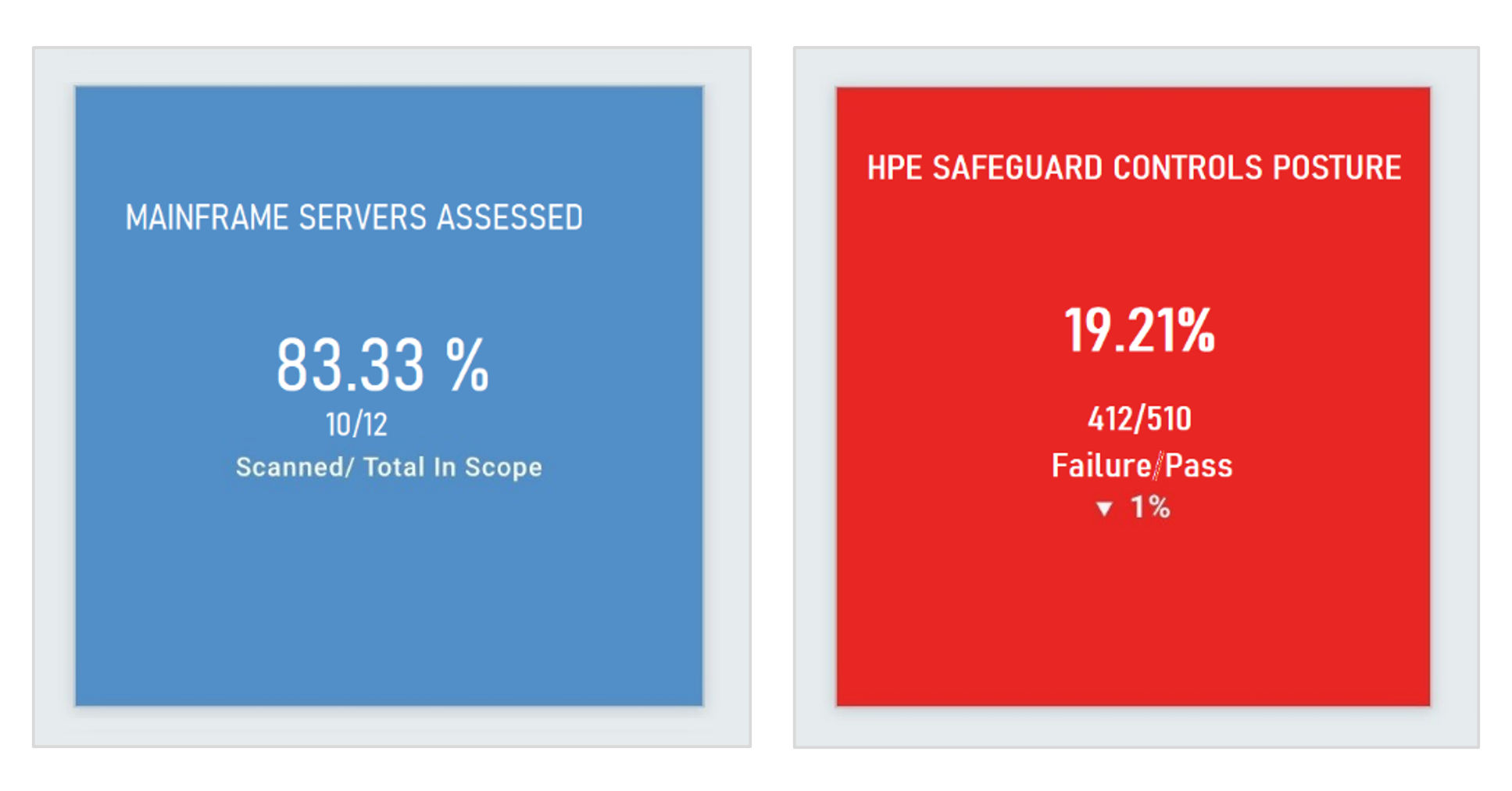
Once the command output is uploaded, compliance signatures are executed on the uploaded data. There are out-of-the-box policies available for assessment for RACF and HP Safeguard in the Policy Compliance library. According to these, the compliance assessment posture can be viewed as any other asset, as shown in the figure below.
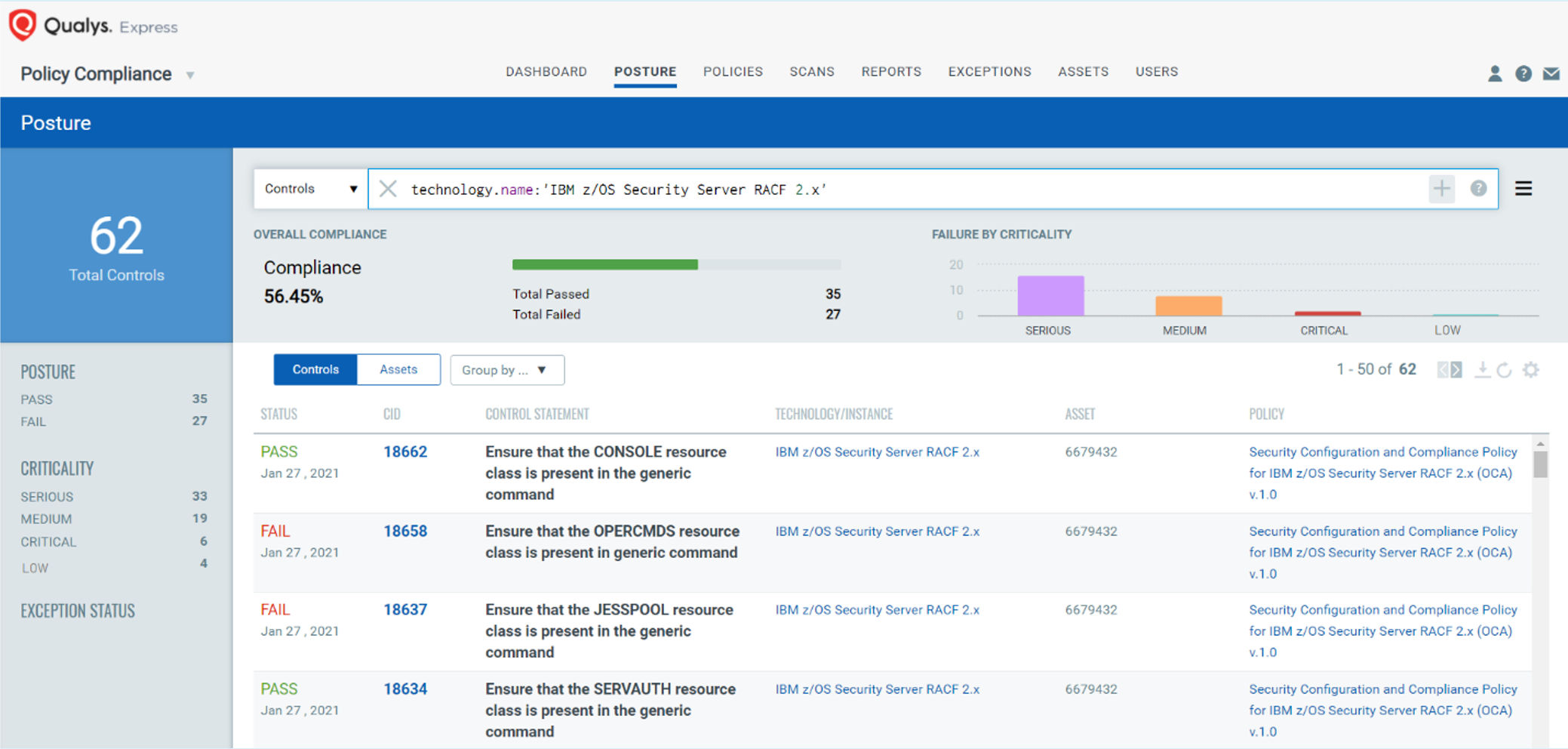
Peek into Compliance Assessment Reporting
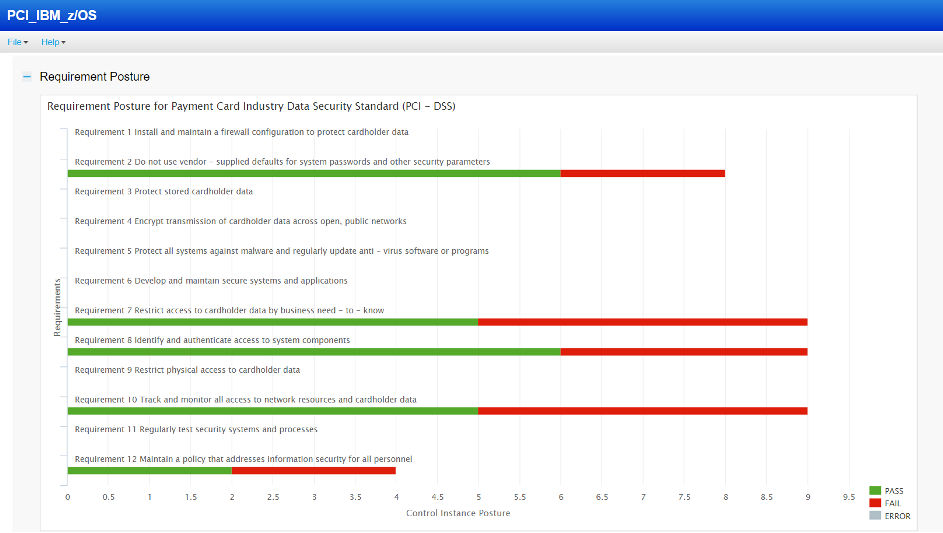
Compliance assessment reports for these servers or ESMs can be scheduled weekly or monthly as per business requirements. Using the powerful backend of Qualys Policy Compliance, the compliance report can be fetched against any mandate or framework. The following is a sample report of RACF configuration controls against PCI-DSS mandate. Similarly, a report can easily be fetched for various other mandates such as CIS Top 20 and SOX. By leveraging the existing integrations with ServiceNow and Splunk for Policy Compliance, the mainframe compliance assessment data can also be pushed from Qualys to ServiceNow and Splunk.
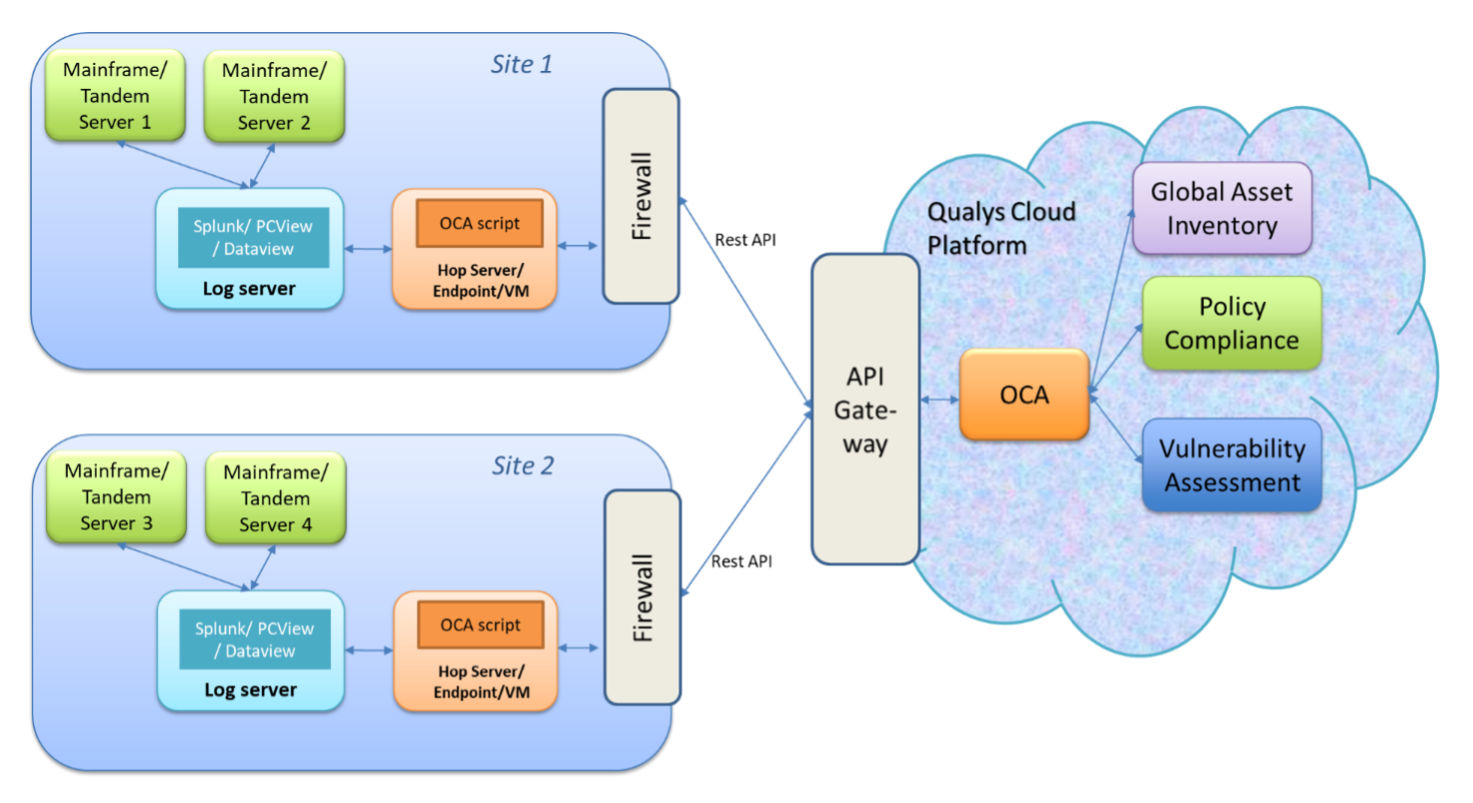
The OCA Architecture and Workflow
The following diagram illustrates the workflow to assess the compliance of mainframe systems. Many organizations, over the years, may have built some form of automation to get the mainframe’s required configuration data. These automation scripts can be customized to fetch the output of the commands that OCA requires. Once the required data is fetched, it can be fed to OCA using a virtual machine or a hop server in your network. Once the data reaches the platform, Qualys evaluates the signatures written for STIG or CIS or any other framework and produces the compliance reports.
Roadmap of Mainframe Assessment Using OCA
Currently, Qualys helps assess RACF 2.x on Z-systems and HPE Safeguard application on HP Nonstop systems. The mainframe assessment roadmap includes full support for DISA STIG, RACF, and baseline z/OS, and it supports Swift CSP compliance for HP NonStop Tandem systems. One more important addition in the pipeline is assessing databases hosted on z/OS, which is extremely crucial for most mainframe customers.
Mainframe Visibility and Assessment
Qualys OCA provides a convenient way to yield visibility into your mainframe servers and ESMs. It helps assess these systems for compliance with respect to standards like PCIDSS, GDPR, STIG, SOX etc. Using the Qualys Cloud Platform, APIs and existing automation around mainframes, the compliance assessment reports can be scheduled weekly or monthly per business requirements. Thus, implementing OCA helps generate timely and accurate assessment reports, frees up mainframe staff from manual auditing efforts, and improves the auditing capabilities without hampering the crucial systems’ real-time performance.