Assess Your Risk From Ransomware Attacks, Powered by Qualys Research
Last updated on: December 21, 2022
Table of Contents
- Clear guidelines from authorities for ransomware prevention
- Qualys undertakes research on ransomware to deliver actionable insights
- Challenges in following guidelines for preventing ransomware attacks
- Assess & continuously monitor your ransomware risk, powered by Qualys Research
- Learn more and see for yourself
- Resources
- References
Ransomware attacks are among the most significant cyber threats facing businesses today. Recent warnings about Conti ransomware, issued by a joint cybersecurity advisory from the U.S. Cybersecurity and Infrastructure Security Agency (CISA), FBI and National Security Agency, are a strong signal that ransomware attacks are becoming even more sophisticated and massive via the ransomware-as-a-service operating model. This new model allows attackers to gain affiliates to use already-developed ransomware tools to execute ransomware attacks quickly and launch more massive attacks against almost any target including large and small businesses, schools, hospitals and national infrastructure. While every metric and trend indicate that organizations continue to add more security tools, successful attacks continue, suggesting that adding more tools isn’t the answer to a strong defense.
Over the last two years, phishing, insecure remote desktop protocol (RDP), and unpatched vulnerabilities have been the top attack vectors exploited by ransomware attackers. However, defenses have focused on detection and response. While detection and response help organizations reduce damage from attacks, it is not helping organizations prevent the attacks. For prevention, organizations need consistent remediation of root cause, which is why authorities like CISA, MS-ISAC and NIST recommend organizations adopt better prevention strategies along with tactics to monitor ransomware exposure proactively.
Clear guidelines from authorities for ransomware prevention

While these guidelines are helpful and represent the best ways for enterprises to shore up their defenses, security teams are resource constrained and in constant fire-fighting mode, which makes implementing these best practices a monumental task.
Qualys undertakes research on ransomware to deliver actionable insights
The Qualys security team has extensively researched CISA, MS-ISAC and NIST guidance and operationalized it into a prescriptive, actionable plan to help companies address their unique risk exposure. For example, the team analyzed the leaked Conti Ransomware Playbook and historic ransomware attacks such as REvil, Nefilim, DearCry, DarkSide and Colonial Pipeline to develop comprehensive insights into specific vulnerabilities, misconfigurations, and software applications targeted in Conti, and other attacks. They then developed a targeted remediation plan for prioritized patching and configuration changes.
Spanning five years and 36 ransomware families, the team’s analysis of ransomware attacks stems from darknet forums, open-source tools, attack playbook analysis, threat intel feeds, and MITRE ATT&CK mitigations and tactics recommended by CISA, and best practices published by Fireye Mandiant.
- 110 CVEs leveraged as attack vectors in most common Ransomware attacks, across 36 prevalent ransomware families with patches available for the past several years
The Qualys research team has thoroughly studied the major ransomware attacks in the last five years and determined that these attacks used about 110 CVEs. The following table illustrates the top five CVEs exploited in high-profile ransomware attacks across six ransomware families. These five CVEs have negatively impacted millions of assets across organizations worldwide:
| CVE | Used by Ransomware Family | Patch Available from Vendor | Patch Available Since | Patchable From Qualys |
|---|---|---|---|---|
| CVE-2013-1493 | Exxroute | Yes | March 2013 | Yes |
| CVE-2013-0431 | Reveton | Yes | February 2013 | Yes |
| CVE-2012-1723 | Urausy | Yes | June 2012 | Yes |
| CVE-2019-1458 | NetWalker | Yes | December 2019 | Yes |
| CVE-2018-12808 | Ryuk/Conti | Yes | August 2018 | Yes |
- 17 business software applications that should always be up to date for security patches to reduce the risk of ransomware
| Vmware | F5- Big IP | Citrix AD and Gateway |
| Vmware Esxi | Atlassian | Fortinate FortiGate SSL VPN |
| Vmware Workspace | Telerik | Microsoft Exchange Server |
| Oracle weblogic server | Drupal | Synacor Zimbra |
| Pulse Secure Connect | MobileIron | Zoom |
| Skype | Teams |
Many of the 110 ransomware-related CVEs have had patches available for years, with an average of five years since the date the patch was first available. Researchers found that among the 110 CVEs, most of the CVEs have patches or remediations available. Older unpatched CVEs are a favorite target of attackers, especially those on internet-exposed assets. Further analysis conducted by the Qualys research team on Conti ransomware confirms that adversaries are targeting known vulnerabilities such as Zerologon (CVE-2020-1472), PrintNightmare (CVE-2021-34527), and EternalBlue (a series of CVEs under MS17-010 exploit) for carrying out the attacks.
One of the critical effectiveness measures of a remediation program is mean-time-to-remediate (MTTR). In 2019, the Department of Homeland Security issued a directive to improve vulnerability management within the federal government and bring the average time-to-patch for critical vulnerabilities to 20 days — down from 149 days. A recent report from WhiteHat Security found that the average time to fix critical vulnerabilities has increased from 197 days in April 2021 to 205 days in May 2021. This year, Qualys researchers also published data that on average it took 194 days from the time when a vulnerability was found in the customer environment to when all instances were patched.
Organizations need to urgently prioritize patches for these vulnerabilities, especially on internet-facing assets that are an attacker’s first target and patching critical infrastructure assets hosting critical database systems to reduce the attack surface.
The MTTR data is why authorities such as CISA and NIST recommend focusing on better prevention strategies, swift prioritization and remediation of vulnerabilities as well as reactive patching, and staying continuously up to date on patching of critical software (as noted in the chart above).
- 237 misconfigurations leveraged across multiple MITRE tactics and techniques
Another critical attack vector is misconfigurations such as insecure RDP and admin shares that have been leveraged in multiple ransomware attacks. Qualys research has mapped misconfigurations to the relevant MITRE ATTACK techniques to define 237 configuration checks across five security areas such as RDP hardening, user controls, network, protocol and port configuration security, share and password policies and software update policies, essentially helping organizations proactively prevent 20 attack techniques leveraged in ransomware attacks.
| Initial Access (TA0001) | Credential Access (TA0006) | Privilege Escalation (TA0004) | Execution (TA0002) | Defense Evasion (TA0005) | Lateral Movement (TA0008) | Command and Control (TA0011) | Impact (TA0040) |
| Valid Accounts (T1078) | Brute Force (T1110) | Abuse Elevation Control Mechanism(T1548) | Scheduled Task / Job (T1053) | Impair Defenses (T1562) | Remote Services (T1021) | Non-Application Layer Protocol (T1095) | Data Manipulation: Transmitted Data Manipulation (T1565.002) |
| Supply Chain Compromise (T1195) | Abuse Elevation Control Mechanism: Bypass User Account Control (T1548.002) | Inter-Process Communication (T1559) | Trusted Developer Utilities Proxy Execution (T1127) | Exploitation of Remote Services (T1210) | |||
| Supply Chain Compromise: Compromise Software Dependencies and Development Tools (T1195.001) | Access Token Manipulation (T1134) | Remote Services (T1021) | |||||
| Unsecured Credentials (T1552) | Remote Services: Remote Desktop Protocol (T1021.001) | ||||||
| Remote Services: Remote Desktop Protocol (T1021.002) | |||||||
| Remote Service Session Hijacking (T1563) |
- Potentially risky applications to monitor in datacenter or database environment and monitoring for absence of anti-malware/virus tooling
Along with attack vectors, research indicates that attackers have been able to laterally move inside the organization’s network and drop malicious payloads due to assets lacking security tooling such as anti-malware/antivirus/EDR solutions. CISA guidelines also suggest organizations should ensure antivirus and anti-malware software are installed and running across an organization’s environment to eliminate security tooling blind spots.
Many organizations have a policy defining authorized software for data center assets, especially those hosting critical data, which is distinctly different from software allowed on corporate assets such as employee laptops. NIST highly recommends security teams monitor assets by job function and ensure only authorized applications are in use. Among the 110 CVEs researched, a few vulnerabilities were associated with software typically found on desktop and laptop assets like collaboration tools and web browsers. This suggests that assets hosting database systems or critical enterprise applications should be monitored to ensure they are free of this software.
Additionally, the Qualys research team identified 33 known antivirus or anti-malware tools that provide malware protection against known malware, with continuous updates to the detection. Qualys recommends that organizations continuously assess their IT environment to ensure that all assets are running the latest anti-virus/malware tools.
Challenges in following guidelines for preventing ransomware attacks
The internet is flooded with articles, advice, and guidelines from security vendors and industry groups. Yet, it is clear in conversations with customers and partners that while they are looking to strengthen their prevention strategies, they are running up against issues that prevent them from operationalizing this advice.
- There’s no clear, comprehensive, research-driven list of ransomware-specific data points for monitoring risk exposure, nor is there a prescriptive remediation plan. Additionally, high-level guidelines from CISA and NIST require operationalization.
- Traditional vulnerability remediation involves multiple teams and processes. First, a scanning tool identifies vulnerabilities, and next they are passed to the patching team for remediation. This fundamental challenge leads to longer vulnerability exposure times. A lack of alignment between vulnerability and patch processes and the manual efforts required for vulnerability remediation are among the key causes of delayed patching.
- Many security leaders still rely on security controls such as EDR, XDR, next-generation firewalls (NGFW), or Secure Access Service Edge (SASE) for ransomware protection. Relying solely on detection and response tools, or even on a simple vulnerability management program is not an adequate defense. NIST Tip and Tactics for Dealing with ransomware suggests the basic defense requires a unified and automated approach to assessing internet-facing vulnerabilities and misconfigurations, insecure remote desktop gateways (RDP), and detection of risky software and assets missing anti-malware solutions. This requires multiple security tools and has the potential to result in siloed views.
Assess & continuously monitor your ransomware risk, powered by Qualys Research
To help organizations assess risk from ransomware attacks, Qualys is offering a 60-day, no-cost service to provide clear and actionable insights into your organization’s ransomware exposure, along with an automated remediation plan to reduce the risk of attacks.
Leveraging the Qualys research team’s expertly curated ransomware-specific vulnerabilities, misconfigurations, risky software list, the Qualys Ransomware Risk Assessment solution delivers a prioritized remediation plan that provides:
- A unified view into critical ransomware exposures such as internet-facing vulnerabilities and misconfigurations, insecure RDP, and detection of risky software in the datacenter environment along with alerting for assets missing anti-malware solutions
- Accelerated remediation of ransomware exposures with zero-touch patching by continuously patching ransomware vulnerabilities as they are detected. The remediation plan also enables proactive patching for prioritized software to keep software up to date
- Communicate to executives the true risk associated with multiple ransomware attack vectors
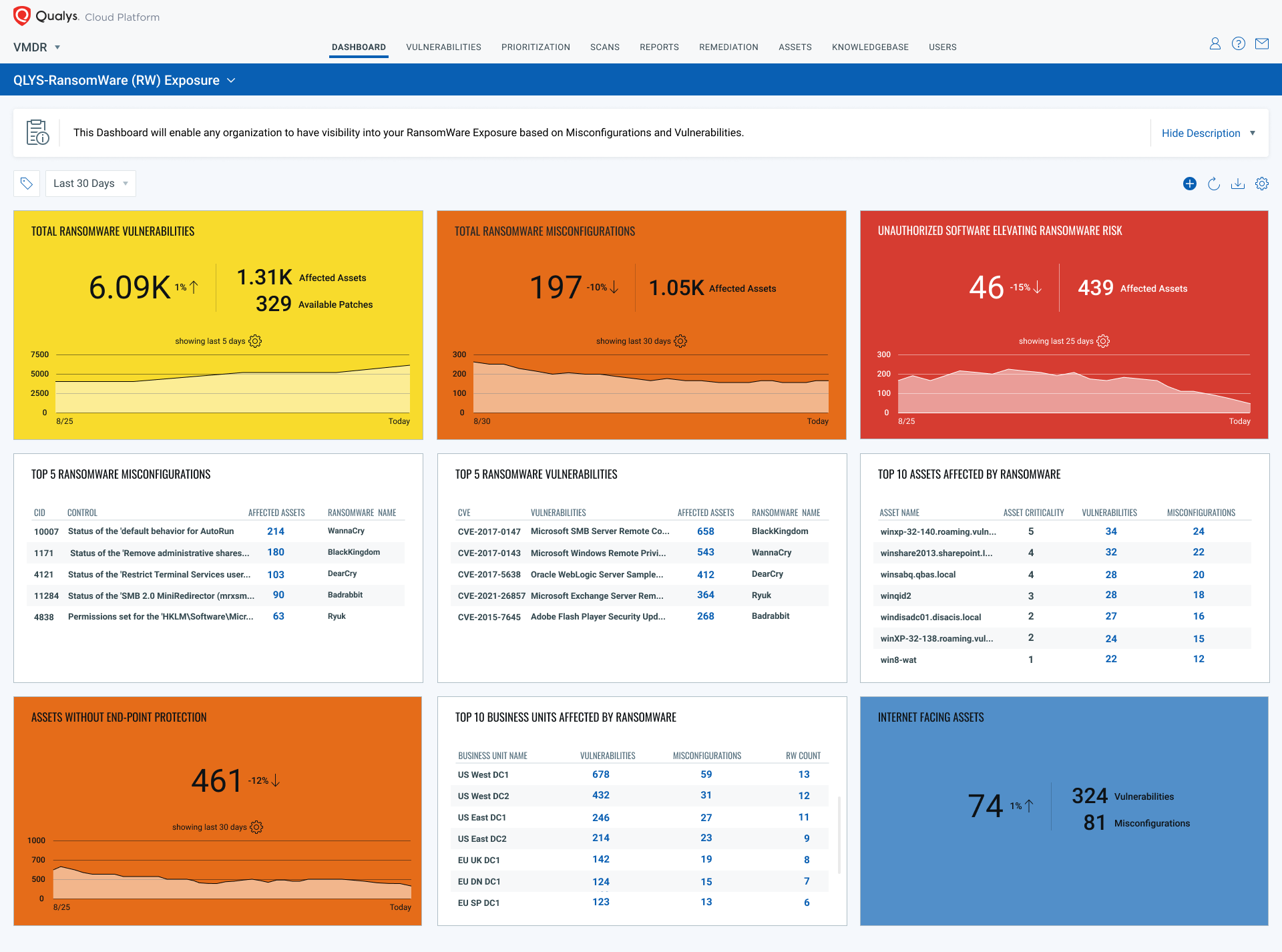
Learn more and see for yourself
To learn more about the research and how Ransomware Risk Assessment & Remediation Service would help reduce your risk to ransomware by joining the webinar, Combating Risk from Ransomware Attacks, on October 21 at 10 am PT. Sign up now!
See the service yourself, and try it at no-cost for 60 days to know your exposure and prescribed patch plan to reduce your ransomware risk.
Resources
- Ransomware Risk Assessment Press Release
- Read the technical blog on the Qualys Ransomware Risk Assessment solution. Learn, what it includes, unified dashboarding of your exposure to drive remediation.
- Register for the Combating Risk from Ransomware Attacks webinar
- Video on Ransomware Risk Assessment