New Java 0-day vulnerability – Update 3
Last updated on: September 7, 2020
Update 3:
Oracle just published Java JDK 7 update 11 that addresses the 0-day vulnerability CVE-2013-0422. Quick reaction to a rapidly expanding threat.
And Java works again on my Mac, XProtect Blacklisting lets it pass as expected. 
I still recommend disabling Java in the browser using the Java Control Panel. for better security against future threats that tend to come down through the browser attack vector. If you have to have Java installed at all, I have it for the local applications Minecraft and Crashplan, then you should look into unchecking that option:
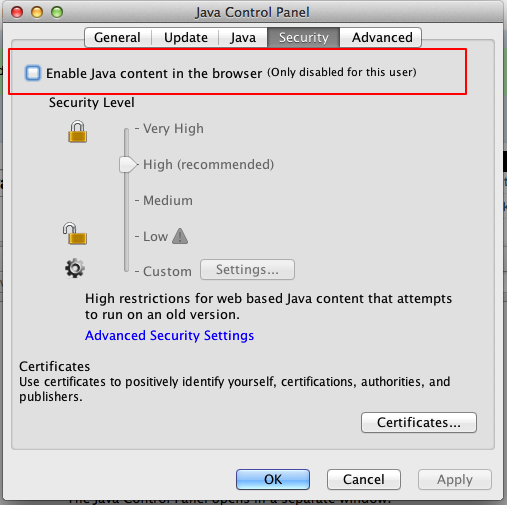
Update 2:
Oracle has made a statement that we can expect a fix for the current Java 7 0-day vulnerability shortly, but has not given a specific date yet. However, next week on Jan 15 is Oracle’s quarterly Critical Patch Update (CPU) Tuesday on when Oracle updates all of its other software packages with security fixes.
Meanwhile Apple has blacklisted the current Java build 1.7.10.18 on Mac OS X in its PlugInBlackList, which prevents it from running inside the browser.

Update:
The exploit has now been integrated in the Metasploit framework, making it available for your internal testing.
Other exploitkits, besides Blackhole that feature the exploit are Nuclear and RedKit. We can expect the exploit to get integrated into more kits rather quickly.
Original:
The US-CERT is warning of a Java 0-day vulnerability present in the latest version of Java 7 update 10. The typical attack vector is a malicious website and researchers are aware of sites hosting exploits for the vulnerability and Brian Krebs reported today that it has been integrated into the BlackHole exploit kit already.
Since there is no patch available, IT administrators should look into the option of disabling Java in the browser. This process has been made easier in the most recent version of Java 7 by including the option in the Java Control Panel:
We will keep you posted on updates to the situation.
