Cloud Security Improves, But Much Work Still Remains to Be Done
Last updated on: September 6, 2020
As cloud computing adoption accelerates among businesses, InfoSec teams are struggling to fully protect cloud workloads due to a lack of visibility into these environments, and to hackers’ increasingly effective attacks.
That’s the main finding from SANS Institute’s “Cloud Security: Defense in Detail if Not in Depth” report, which surveyed IT and security pros from organizations of all sizes representing many industries.
“We’re seeing more organizations moving to the cloud. They’re definitely moving quickly. And security teams aren’t wholly comfortable with the way cloud providers are giving us details about what’s going on in the environments,” report author Dave Shackleford, a SANS Institute analyst and instructor, said during a webcast to discuss the study findings.
Meanwhile, 20% of respondent organizations reported being victims of a breach, an eyebrow-raising jump from 10% in last year’s study. “That’s pretty significant,” added Shackleford, who is also Voodoo Security’s founder and principal consultant.
Companies’ love affair with the cloud intensifies
There’s no stopping the cloud computing train, as more and more organizations hop on it and never look back.
- Almost 82% of respondents said their organizations plan to increase the number of business applications they maintain in the cloud.
- Already 83% of respondents’ organizations use two or more public cloud providers, with most using between two and six. However, 15% are using between 7 and 20, and a smaller percentage uses even more providers.
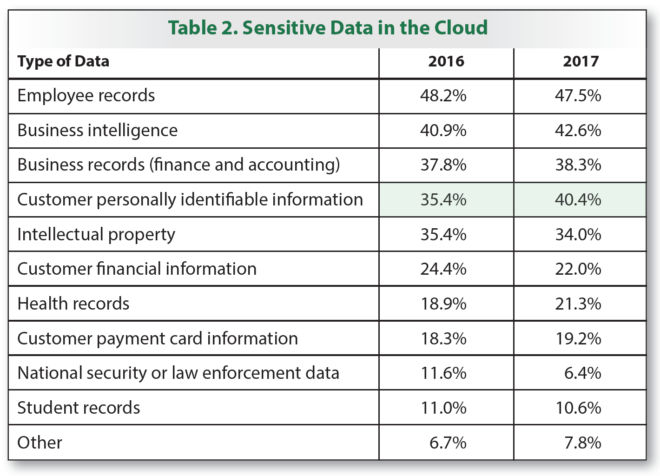
- The storage of sensitive data in the cloud continues to grow. For example, the percentage of respondents who said their organizations store customers’ personally identifiable information (PII) in the cloud rose from 35.4% last year to 40.4% this year.
Organizations also reported using applications in public and private clouds for a wide variety of tasks: business functions, backup and disaster recovery, data storage and archiving, and managed services.
InfoSec teams remain concerned
In contrast with organizations’ unbridled enthusiasm over cloud computing, their InfoSec teams remain wary about a long list of issues, including unauthorized access to sensitive information through insecure, unmanaged devices, or by other public cloud tenants.
They also worry about being unable to properly: respond to security incidents affecting their organizations’ public cloud workloads; encrypt data in those environments; and perform audits for meeting compliance requirements.
This lack of visibility and control over public cloud workloads is a growing source of frustration for InfoSec teams. “While we did see that to some degree last year, it’s really becoming a sore point for a lot of folks,” Shackleford said.
Qualys, which co-sponsored the study, has identified noticed this same vexation among its customers.
“We’re seeing genuine frustration among security teams as they try to understand what is actually happening in multi- or single-cloud environments, and how do they effectively respond to incidents when they are challenged with visibility,” he said.
A majority of respondents — 58% — said they’re not fully confident about being able to control cloud risk. A minority — 16% — reported feeling that they have full control. A substantial one fourth of respondents either don’t know where they stand or have zero confidence.
When asked what type of report they’re looking to get from their cloud providers, the most commonly-mentioned were ISO 27001 (57.3%), CSA Cloud Controls Matrix and STAR Program (41.8%), SSAE 16 SOC 2 (31.1%) and FedRAMP (28.2%).
In terms of actual incidents, downtime of applications tops the list, followed by poor configuration of ephemeral application components like containers. The latter — container security — in particular is an area that InfoSec teams need to learn more about and understand.
“Applications in containers get spun up and down in milliseconds. They’re not deployed in a traditional build and deployment process,” he said. “We need to know what’s being deployed in the container, and also what kind of app services they’re providing.”
To secure containers properly, so that they’re free from vulnerabilities and misconfigurations, Qualys recommends the following approach:
- For prevention, deploy static binary code analysis for application logic and use private image repositories, introduce image and registry configuration checks to validate initial build trust, and monitor container-specific traffic. Since running containers can’t be patched, we now replace existing ones with updated container software versions and configurations.
- For detection, identify and correct vulnerabilities in the DevOps pipeline, verify compliance to internal build and CIS standards, and track container to container communication
- For response, track inventory and container events, record orchestration tool activities for review, enable persistent logging for SIEM tools and set up ticketing workflow integration
- For prediction, track container events, analyze container and microservices behavior and detect anomalies, and quarantine and block anomalous users and containers
Hackers up their game
Deeply concerning is the jump in organizations reporting breaches of cloud apps and data, which was 9% in 2015 and 10% in 2016, but shot up to 20% this year. “This is huge,” Shackleford said.
The reason for the jump: A lethal combination of poor security hygiene and of improved, more frequent cyber attacks against public cloud workloads.
“Maybe we’re not doing a great job overall,” Shackleford said, referring to public cloud security. “The big problem is that the attackers have figured this out.”
“Once the attackers are on to you, you’re going to see those numbers increase,” he added.
Also worrisome is that 21% of organizations didn’t even know whether they’d been breached. “This is incredibly disheartening,” he said. “That’s a problem. We need that knowledge and visibility.”
So how are hackers attacking public cloud workloads? Denial of service (DoS) is the most popular method, followed by exploits of vulnerable or misconfigured hypervisors and of other virtualization managements. Account or credential hacking ranked third, followed by exploits against a hosting provider’s vulnerability.
Taking steps to secure public cloud workloads
Despite the concerns about lack of visibility and control, and hackers’ increased success, InfoSec teams aren’t sitting in a corner whining and licking their wounds. Instead, they’re taking advantage of opportunities to improve security and compliance in their public cloud workloads.
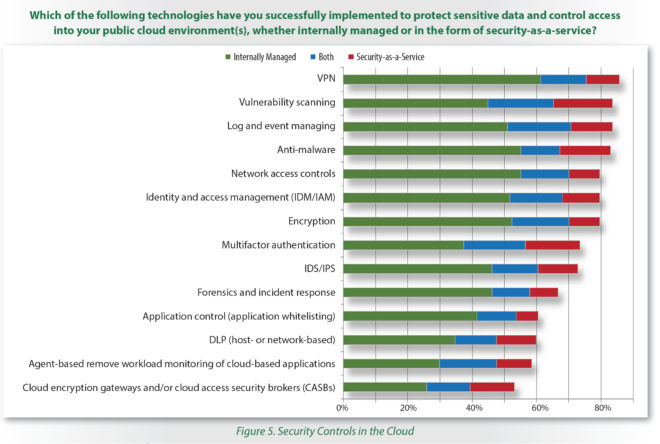
Respondents saying they have implemented cloud security policies and governance jumped from 48% last year to 62%. Meanwhile, a majority of InfoSec teams are using multiple technologies to protect data and control access in their public cloud environments, including:
- VPN
- Vulnerability scanning
- Log and event management
- Anti-malware tools
- Network access controls
- Identity and access management
- Encryption
- Multi-factor authentication
For audit and compliance, almost 50% of respondents said they’re able to perform pen tests against their cloud apps and infrastructure, up from 42% last year. Among those not able to do this, 26% get independent test reports from the providers, while 18% are neither able to do the tests nor get reports.
Regarding detection and response to incidents, the majority of InfoSec teams — 55% — cite as the main challenge gaining access to low-level forensic and event data. Other challenges include a lack of understanding about the information required from cloud providers for analysis, and various difficulties related to multi-tenancy.
There’s been progress, but a long road lies ahead
Overall, respondents have a number of items on their wish lists that they say could help them improve the security and compliance postures of their public cloud workloads, including:
- More native controls offered by providers
- Ability to integrate controls between their on-premises and cloud environments
- Better control over instances of “shadow cloud”, in which an organization’s end users sign up for cloud services without alerting nor seeking approval from the IT team
- Better understanding of data ownership, and clearer mapping of which data can be stored in the cloud and which data needs to stay on premises
- More involvement of the InfoSec team in governance decisions
Overall, in-cloud controls and services still lag cloud computing’s pace of adoption.
“Cloud security is improving, albeit slowly,” Shackleford wrote in the report, which was published in November and co-sponsored by Qualys. “However, until cloud providers become more open and accommodating of security data and controls, it’s likely to be a slow process.”

Read the full report, “SANS 2017 Cloud Security Survey Report: Defense in Detail if Not in Depth”.