Securing IT Assets By Prioritizing Protection And Remediation
Last updated on: September 6, 2020
 As hackers get faster at weaponizing exploits for disclosed bugs, InfoSec teams need — more than ever — automated, continuous and precise IT asset inventorying, vulnerability management, threat prioritization and patch deployment.
As hackers get faster at weaponizing exploits for disclosed bugs, InfoSec teams need — more than ever — automated, continuous and precise IT asset inventorying, vulnerability management, threat prioritization and patch deployment.
Critical vulnerabilities that linger unpatched for weeks or months offer hackers easy opportunities to breach systems. These bugs open the door for bad guys to steal confidential data, hijack PCs, commit financial fraud and create mayhem.
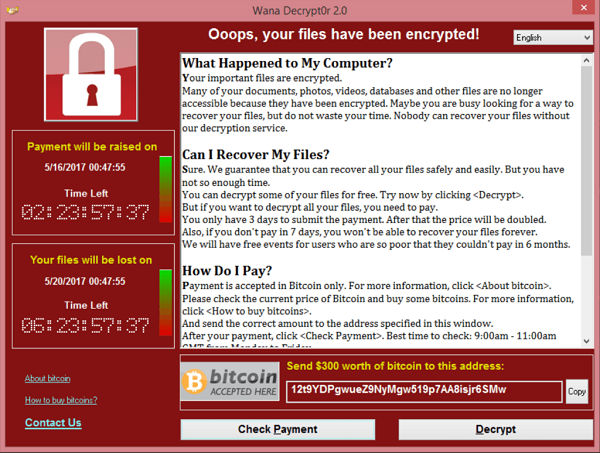
The WannaCry ransomware attack, which infected 300,000-plus systems and disrupted critical operations globally in mid-May 2017, highlighted the importance of timely vulnerability remediation.
WannaCry spread using the EternalBlue exploit for a Windows vulnerability (MS17-010) that Microsoft had patched in mid-March. At the time, Microsoft rated the vulnerability as “Critical” due to the potential for attackers to execute remote code in affected systems.
Organizations had a window of about two months to install the patch before WannaCry was unleashed. Had most affected systems been patched, WannaCry’s impact would have been minor.
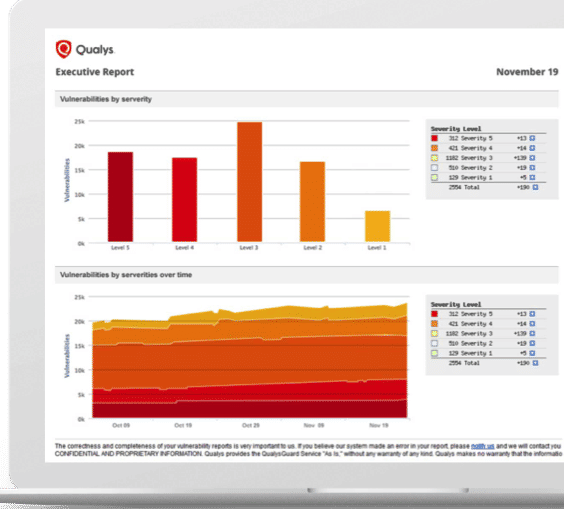
Unfortunately, high severity vulnerabilities still take organizations on average more than 100 days to patch. With Qualys, organizations can have broad and detailed IT asset visibility, unparalleled vulnerability detection accuracy, granular threat prioritization and, very soon, solid patch management.
“With Qualys Vulnerability Management, AssetView and Threat Protection, we’ve nearly completed the vulnerability lifecycle,” Jimmy Graham, Director of Product Management at Qualys, said during a recent webcast.
Using both Qualys scanners and the Qualys Cloud Agent, Qualys VM detects vulnerabilities across all of an organization’s IT assets, including those that are located on-premises, roaming outside of the network, and in private and public clouds.
“Qualys VM is very accurate, very scalable, and works in environments of any size,” Graham said.
Meanwhile, Qualys AssetView takes all of that vulnerability detection data and combines it with assets’ hardware and software inventory data, giving organizations a unified view of both their IT and security data.
“All this information is searchable in seconds within AssetView, and that same search engine powers the customizable dashboards that let you choose how you want the information to be displayed,” Graham said.
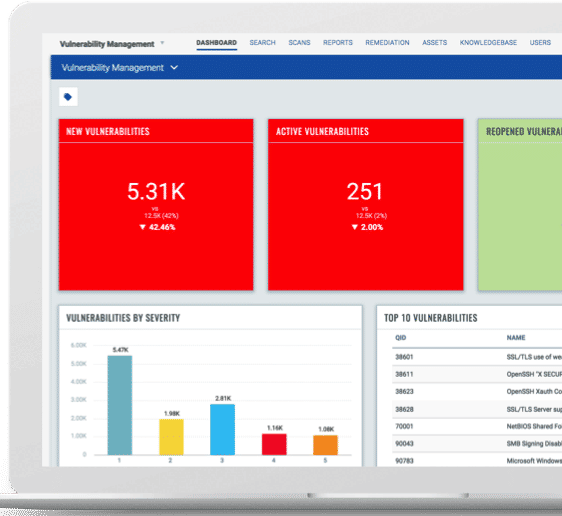
Knowing you have thousands of vulnerabilities present in your IT assets is only part of the equation. It’s key to identify which vulnerabilities must be remediated first. That’s where Qualys Threat Protection comes in.
Qualys TP layers real time threat information on top of the vulnerability detections, so that organizations can prioritize remediation across all of their assets. This automated remediation prioritization is based on indicators such as vulnerabilities with public exploits and with active attacks, and on other types of real time threat information.
Later this year, Qualys will introduce Qualys Patch Management, to complement Qualys VM’s discovery at scale, AssetView’s reporting and research, and Threat Protection’s threat prioritiziation. Qualys PM’s dashboard shows such information as failed patch installs, missing patches, and assets that must be rebooted.
“You’ll be able to discover, correlate and deploy patches on Windows, Linux and MacOS systems, completing that vulnerability lifecycle for your most common assets,” Graham said.
Also on tap for this year is Qualys Asset Management, which builds upon already collected asset data by normalizing data points like installed software, and OSes, and enriches this data with asset intelligence. This will allow organizations to better track assets and software, giving them full visibility of both asset and software lifecycles.
“This product will augment a lot of the asset management capabilities we already have today,” Graham said.
To see a demo of Qualys Vulnerability Management, AssetView, Threat Protection and the upcoming Patch Management, watch the recording of Graham’s webcast, in which he also took questions from the audience.
See all of the presentations in the Continuous Security and Compliance Webcast Series.