Continuous Web Security Assessment for Production and DevOps Environments
Last updated on: September 7, 2020
Web applications have become essential for business, as they simplify and automate key functions and processes for employees, customers and partners, making organizations more agile, innovative and efficient.
Unfortunately, many web applications are also unsafe due to latent vulnerabilities and insecure configurations. Web application attacks rank as the most likely to trigger a data breach, according to the 2016 and 2017 editions of the Verizon Data Breach Investigations Report.
Those findings are consistent with SANS Institute’s 2016 State of Application Security Report, which found that “public-facing web applications were the largest items involved in breaches and experienced the most widespread breaches.”
“Insecure web applications are a real problem today,” Dave Ferguson, Director of Product Management for Web Application Scanning at Qualys, said during a recent webcast. “Web apps are a foothold into your organization for potential attackers.”
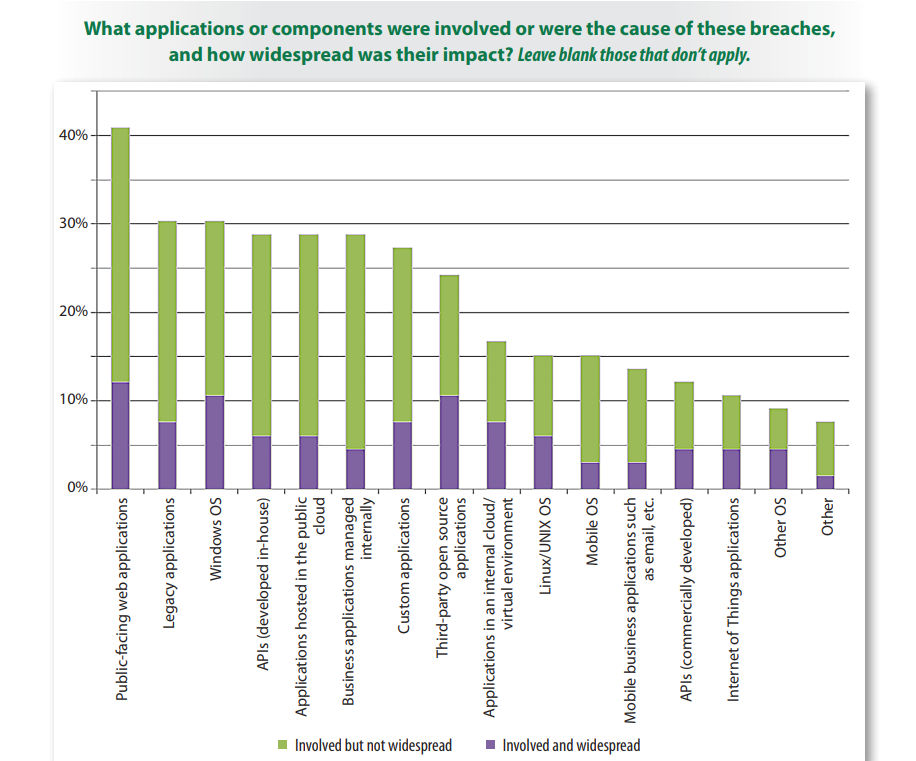
Web apps drive digital transformation, but security is an afterthought
As organizations rush to digitally transform their operations, the preferred delivery method for these innovations are web apps in all their forms: Internet-facing, internal and cloud-hosted web apps, and REST API-based web services.
But as organizations drive their developers to create web apps at lightning speed, they’re failing to incentivize them to make them secure, according to Ferguson. Rather, organizations steer developers towards making sure apps perform well and have all the necessary features.
The quality assurance (QA) and testing team will be checking for functional bugs, or for missing features. Security vulnerabilities and misconfigurations will slip through if no one is deliberately trying to find them.
“There will be security flaws unless there are very explicit steps taken to avoid them,” Ferguson said.
The right approach for web app security
Making security an afterthought or ignoring it altogether is a recipe for disaster. Thus, organizations need a tool that automates web application scanning tasks, because manual testing, while effective, requires a large and specially-trained staff, making it too costly and difficult to scale.
Here are key features an automated web application security scanning tool should have:
- Discovery: The product should be able to detect all web applications in your environment, wherever they reside, and create an inventory.
- Scalability & accuracy: Many organizations have hundreds and even thousands of web applications, so the tool should scale accordingly. It also needs to be highly accurate, returning few false positives and catching most flaws.
- REST API testing: More and more apps are being built that simply invoke APIs. These web services can have many of the same types of vulnerabilities – SQL injection for example – although they’re not browser-based web apps.
- Adaptable to new technologies & frameworks: In the application development world, new technologies are constantly being created, and developers are always eager to adopt them right away.
- Scan scheduling: The product should offer flexibility for scheduling web application scans during off-hours or approved scanning windows.
- Robust API: The product should provide an API so that you can programmatically launch scans, pull down results, and integrate it with other systems
- CI/CD: You should be able to integrate the product with CI/CD (continuous integration / continuous deployment) tools, so that you can automate security testing of apps early and often in the development lifecycle.
- Authentication: For deep scanning, the security tool must be able to authenticate to the web application to access and test the authenticated areas of the web app. Otherwise, you’ll be missing a lot of potential vulnerabilities.
- Malware detection capability: Hackers are constantly trying to find ways to get malware onto very popular websites so you must monitoryour sites to make sure you’re not unknowingly serving up malware to your visitors.
Qualys WAS
If your organization lacks visibility into its web application inventory and isn’t frequently scanning them for security flaws, Qualys Web Application Scanning (WAS) provides continuous web application discovery and detection of vulnerabilities and misconfigurations.
Qualys WAS performs automated crawling and testing of custom web applications to identify vulnerabilities, including cross-site scripting (XSS) and SQL injection. It enables regular testing that produces consistent results and reduces false positives.
Qualys WAS includes Qualys Malware Detection (MD), which proactively monitors websites for malware infections, sending alerts to website owners to help prevent blacklisting and brand reputation damage.
During the webcast, Ferguson outlined four key use cases for Qualys WAS:
- Web application discovery and inventory
- Web application monitoring in production environments
- Web application scanning in development or QA environments
- Scan automation in CI/CD DevOps pipelines
Let’s look at each one in more detail.
Web application discovery and inventory
The landscape of web applications and APIs at the average organization is constantly changing. For example, new web apps are rolled out temporarily for a marketing push, while new APIs are established to support mobile apps.
For web application security, having a reliable, continuously updated inventory is crucial. “You can’t secure what you don’t know about,” Ferguson said. “But only a small fraction of organizations maintain a single source of truth.”
Qualys WAS provides a continuously updated inventory of all of your web apps. Its Web App Catalog feature provides a repository and triaging area for web apps and APIs discovered by WAS and by Qualys Vulnerability Management (VM) scans. An upcoming passive network analysis tool from Qualys will also contribute to web application discovery.
Within the WAS catalog dashboard, you can mark web servers as “approved,” “new,” “rogue,” or “ignored,” and tell Qualys WAS to perform deep scans of specific apps.
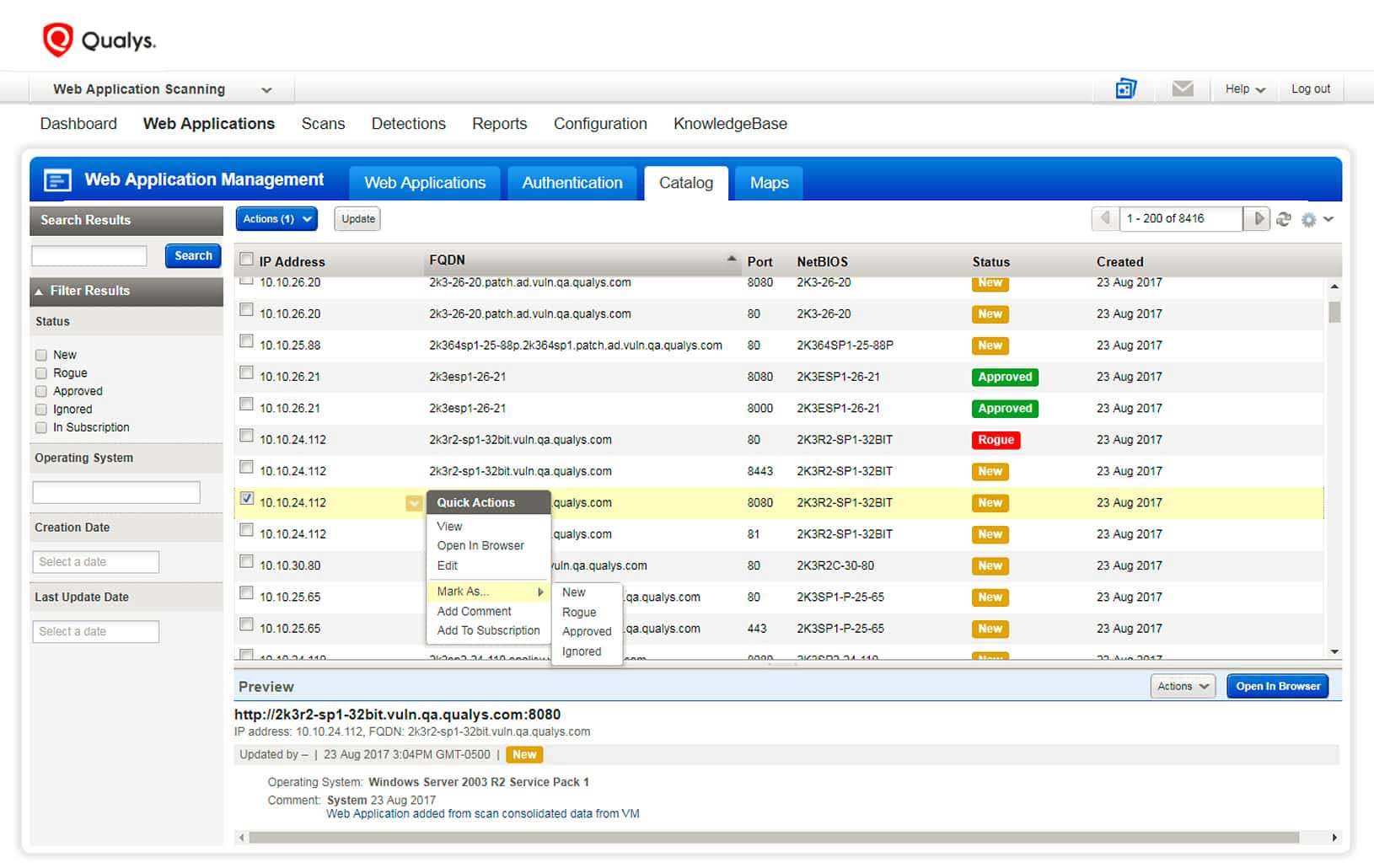
Web application monitoring in production environments
After a web application has been developed, tested and rolled out into production, it’s in maintenance phase, whether it’s public facing or internal. An organization can have hundreds or thousands of web applications in this stage, during which security teams must remain vigilant, especially as code gets tweaked.
“Vulnerabilities often creep in when changes are made to apps already in production, because there isn’t rigorous testing, especially security testing,” Ferguson said.
Qualys WAS can help with testing of production applications in a number of ways. It’s able to do large-scale dynamic scanning, leveraging the robust Qualys Cloud Platform. Public-facing apps can be scanned within minutes after onboarding with Qualys’ Internet-based scanners, while internal web apps are scanned with Qualys virtual appliances. All scan data is presented and reported in a uniform way in a single dashboard.
Another key Qualys WAS feature is its sophisticated scheduling capability, which gives you the flexibility to work within your organization’s scan window restrictions. For example, you can schedule a scan to run between midnight and 3 a.m. every other Thursday.
A related capability is multi-site scanning, which allows you to tag applications and group them under a common label, and then schedule a scan for all web apps in that group, instead of having to do it for each one individually.
Qualys WAS also offers progressive scans, which let you break up into two or more segments the scanning of a very large web app. For example, if your scan window is never longer than four hours, and a large web app is going to take 12 hours to complete, you can break up the job into three scans.
Qualys WAS also lets you do authenticated web app scans, which means that the product can check for security issues in the part of the code that’s only used when users are logged in with an account.
Finally, Qualys WAS includes malware scanning capability to detect malware being served by your public-facing websites.
Web application scanning in development or QA environments
There’s a lot of interest in embedding security testing in application development to catch vulnerabilities and misconfigurations early in the process. “Security testing should be an integral part of your software engineering practice,” Ferguson said.
Organizations have different options for scanning at this stage: Dynamic scanning of running apps, static code analysis and manual pen testing. However, as mentioned before, manual security tests require costly staff to perform them, and don’t scale, potentially delaying deployments, a big no-no in this age of digital business and agile development.
Meanwhile, static code analysis is falling short with new programming languages and the rising popularity of microservice architectures, where the application codebase is no longer monolithic but rather consists of a set of HTTP-based API calls.
With Qualys WAS, you can introduce a self-service model where development teams are given access to the scanning tool and given the responsibility for scanning their own apps. “The advantage here is that scans are going to happen earlier in the SDLC,” making apps more secure and reducing costs, Ferguson said.
Scan automation in CI/CD DevOps pipelines
In this scenario, the Qualys WAS API is used to integrate with CI/CD tools like Jenkins. As developers make code changes, check in code, commit code to source control, and so on, the CI/CD tool compiles a build and pushes it out to various environments, like staging, test/QA or development.
Once the build hits one of those environments, a Qualys WAS scan is automatically launched via an API call.
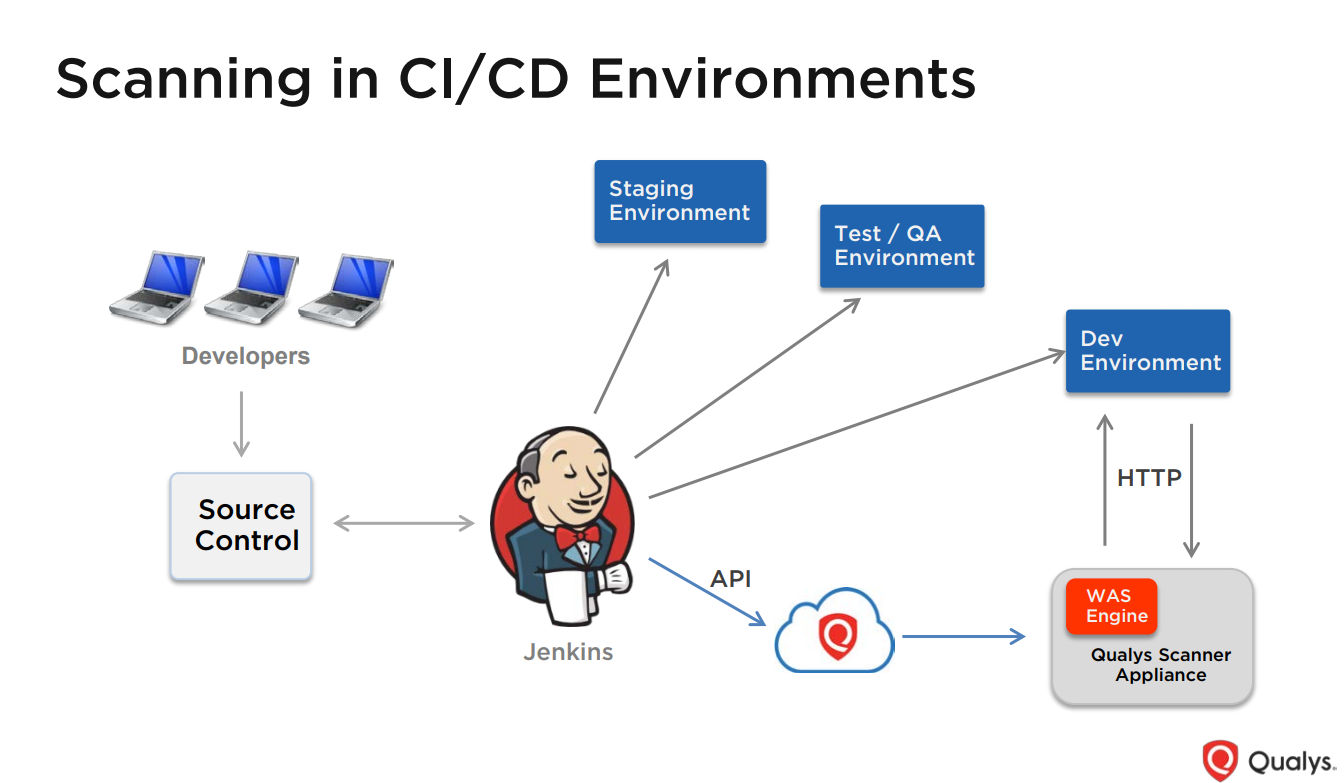
“No one is manually launching a scan, or scheduling a scan,” Ferguson said. “It’s automatically kicked off as part of the build process.”
We invite you to listen to a recording of the webcast, which has a lot more details about this topic and about Qualys WAS, as well as a live demo of the product and a Q&A session with the audience.
See all of the presentations in the Continuous Security and Compliance Webcast Series.