Stronger Security with Global IT Asset Inventory
Last updated on: September 6, 2020

On a Friday afternoon before a long holiday weekend, a company’s security operations center receives a potentially serious alert: It appears that a domain controller has been tampered with. After examining event logs and overlaying network traffic, a SOC analyst confirms that a suspicious system did in fact connect to the controller, extracted credentials, and performed other actions.
Worried this could be a hacker, the SOC team spends hours doing network analysis. Eventually they determine it’s a false alarm: An administrator had logged into the network to check his email with his personal laptop, whose use the company had authorized a month before.
Why did it take the SOC team so long to solve this mystery? They lacked a comprehensive IT asset inventory that would have allowed them to either quickly find that laptop on a list of devices owned by employees and approved for work use, or else determine it was a rogue device.
This hypothetical incident shows the importance of a continuously updated IT asset inventory, which would have slashed the SOC’s investigation time, and made a big difference if instead there had been an attack, according to security experts from SANS Institute and from Qualys.
“If that time is measured in a minimum of hours or days, then there’s a real problem,” Matt Bromiley, a SANS Institute analyst, said during a webcast in which he discussed this scenario.
It’s a fight against the clock when you’re trying to identify and contain a breach. When every minute counts, an IT asset inventory is a critical tool that security teams must have. “IT asset inventory is the foundation for any organization’s security infrastructure,” said Pablo Quiroga, a Qualys Director of Product Management.
Read on to learn more about IT asset inventory challenges and best practices, and about how Qualys can help you.
IT asset inventory challenges
For decades, companies have struggled to maintain detailed, up-to-date IT asset inventories. The task isn’t getting any easier as IT environments become more hybrid and distributed.
Keeping track of hardware and software gets more complicated with the adoption of cloud computing, virtualization, containers, mobility, BYOD (bring your own device), and IoT. The implications for the security team are critical.
“How can you be expected to effectively manage and secure a network if you don’t know what’s inside the network?,” Bromiley asked during the webcast titled “Stronger Security with Global IT Asset Inventory,” sponsored by Qualys. “If I don’t have visibility into something, I can’t really protect it.”
Without an IT asset inventory, dangerous blind spots will emerge. The organization won’t properly understand its environment to prioritize assets, assess risk, and plan further visibility and protective measures.
Using IT asset inventory for security
If the security team can leverage detailed, current data of IT assets, it will be able to see the whole picture, minimize the organization’s attack surface and quickly flag systems, Bromiley said.
“End to end, all of these things, can be addressed in some way, shape or form, through effective global asset inventory and management,” he said. “IT asset inventory and security are a natural combination.”
Key features that an IT asset inventory system should have include:
- Scalability
- Cross-platform support
- Continuous discovery
- Continuous normalization and classification
- Integration with other data sources
How Qualys can help
The new Qualys Asset Inventory (AI) app, now in beta, helps companies maintain full visibility of all global IT assets via a continuously updated inventory — on premises, in clouds and at endpoints, Quiroga said.
It all starts with the Qualys Cloud Platform’s scalable, self-updating and centrally-managed set of sensors:
- physical scanners for on-premises, legacy assets
- virtual scanners for private clouds and virtualized infrastructure
- pre-certified scanners for public cloud platforms
- lightweight, multi-platform Cloud Agents installed on assets
- APIs for integration with third-party sources of asset telemetry
- a passive network sensor (beta)
Specifically, the network sniffer, called Passive Network Sensor (PNS), will help eliminate blind spots by continuously monitoring traffic to detect and profile assets the moment they connect to the network. It will add details such as traffic data, while discovering systems that may be unsuited for active probing or agents, like some IoT, medical, and SCADA systems.
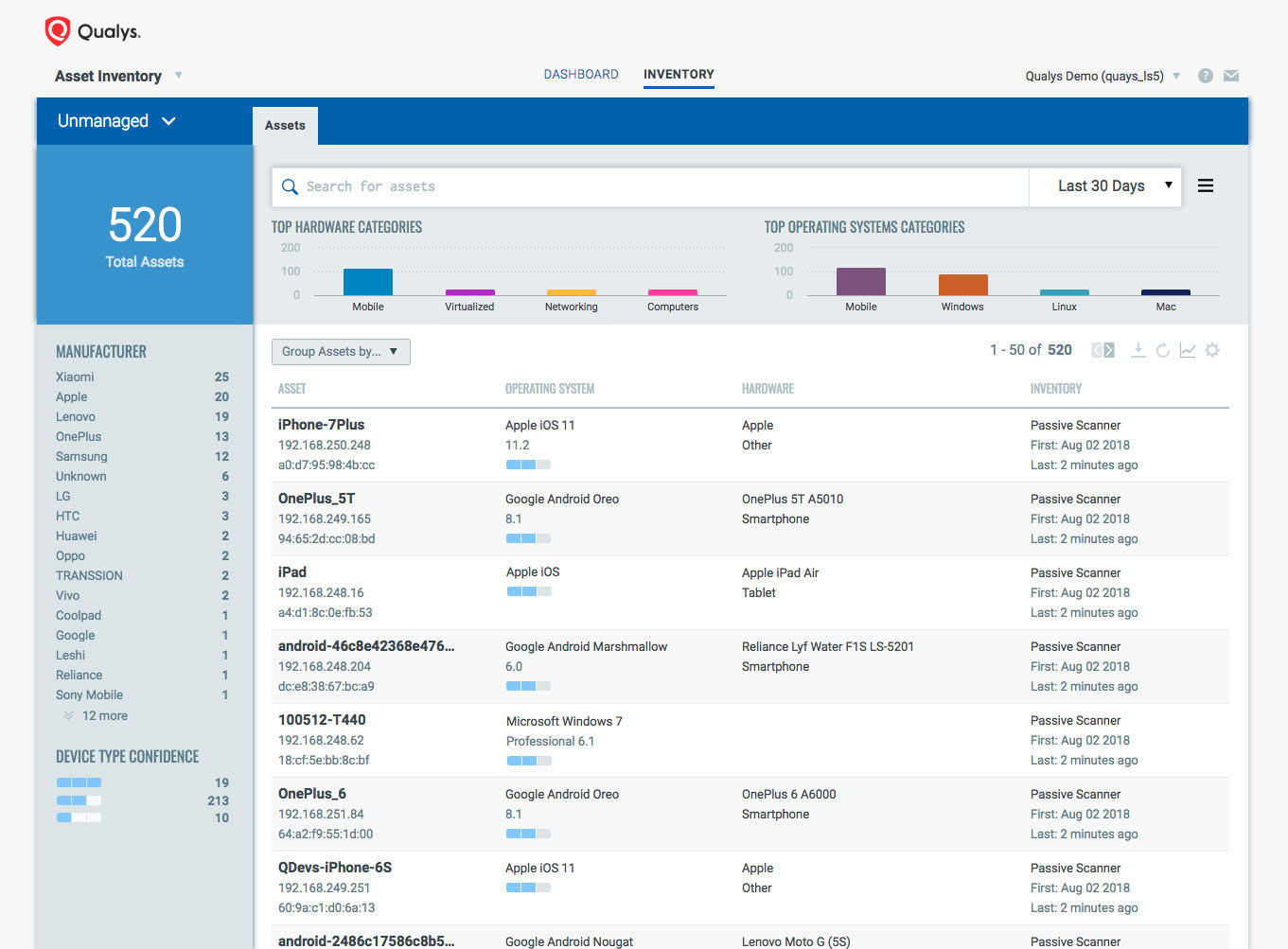
With this versatile set of sensors, Qualys can discover all asset types and collect deep, granular asset details, Quiroga said.
The asset telemetry collected by these sensors is transmitted to the Qualys Cloud Platform’s backend for storage and analysis, leveraging “big data” technology like Kafka, Elasticsearch and Cassandra.
The platform annually detects 1+ trillion security events and conducts 3+ billion device assessments and audits with Six Sigma accuracy (99.99966%). Currently, it is indexing 250+ billion data points in its Elasticsearch clusters.
The security and compliance data is then made available through Qualys’ over 15 integrated, self-updating apps. Accessible from a central console, the apps provide specific and actionable views of the data.
“This speaks to the scale of our platform. We have customers with 2+ million assets, and they can do a search on any data point of their assets across clouds and on-premises — in two seconds,” he said.
Qualys AI in detail
Qualys AI discovers all assets in global, hybrid infrastructures, and normalizes and categorizes information for both hardware and software assets. It also further enriches the inventory with non-discoverable metadata and indexes it so it’s instantly available.
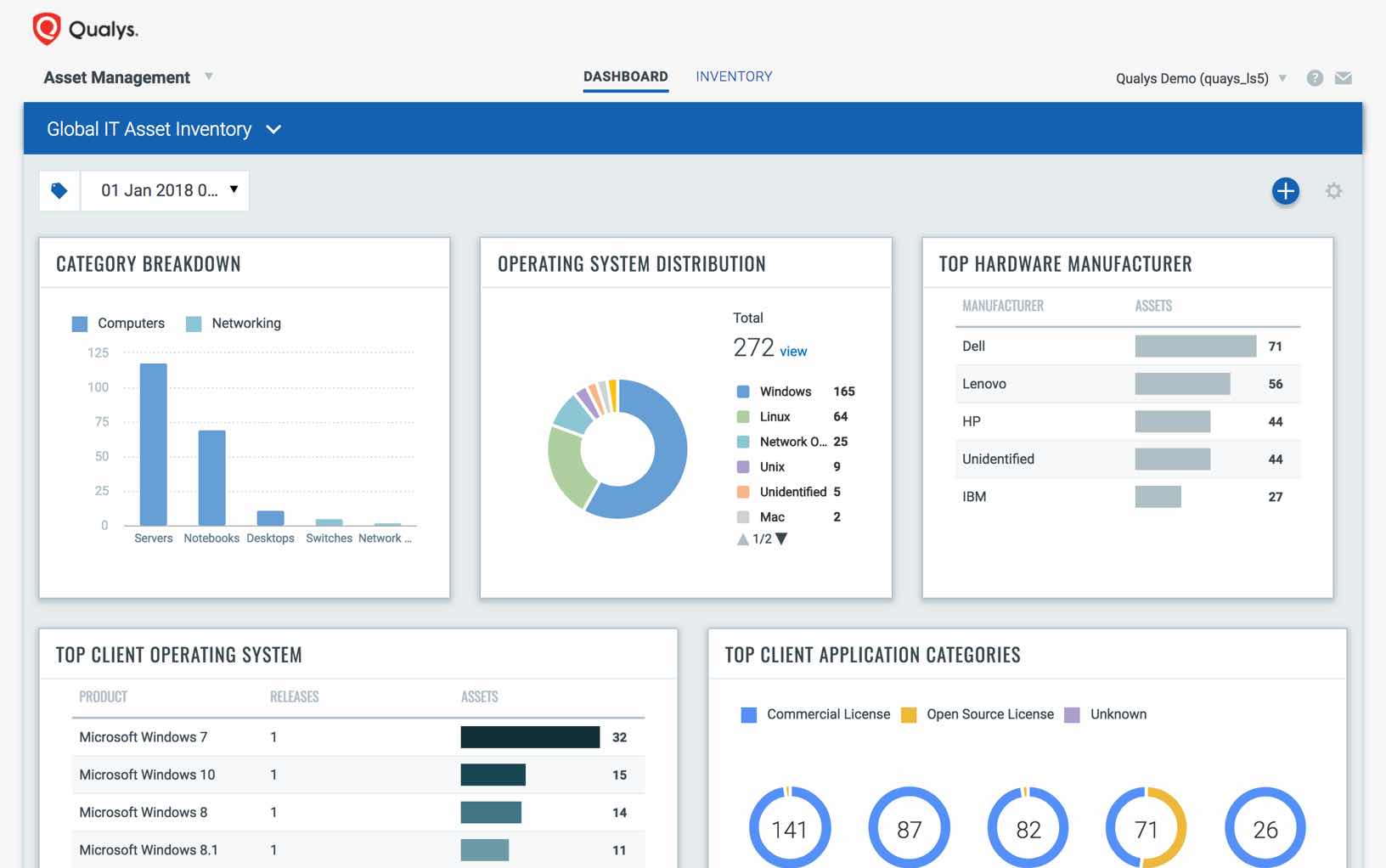
With Qualys AI, organizations get a granular, multidimensional view into assets and their components, including, but not limited to:
- Hardware and systems specs
- Installed software (OS, applications, drivers, utilities, plug-ins and more)
- Network connections
- Open ports
- Approved users
- Running services
- Geographic location and time zone
The normalization and classification functionality places every asset into meaningful, functional categories, such as “devices,” and then further into narrower sub-categories, such as “notebooks,” he said. It also helps eliminates data variations in vendor names, product names, and product versions.
Qualys AI also provides actionable insights with non-discoverable asset metadata, such as vendor lifecycle information (product release date, end-of-life and end-of-service dates), license categories, and product lineage.
Furthermore, Qualys AI lets you add your own business context information (business unit, asset owner) via static and dynamic asset tags, which are shared across all other Qualys apps.
In addition, Qualys AI also has capabilities to sync with Configuration Management Databases (CMDBs) to keep asset data up-to-date. For example, Qualys offers a certified ServiceNow app that can sync complete asset data from Qualys to ServiceNow CMDB.
In summary, Qualys AI gives security teams a “single source of truth” for IT asset data that they can then use to better prevent incidents, and to more quickly respond to them when they do happen.
Please watch a recording of the webcast, which goes into much more details about this topic, a demo of Qualys AI, and a Q&A session with the audience. You can also read a companion white paper written by Bromiley.