Boosting Patch Management Is Key for Breach Prevention
Last updated on: September 6, 2020
 Vulnerabilities that vendors have disclosed and issued patches for remain a major source of breaches. Why? Too many organizations take too long to deploy those patches — or never do.
Vulnerabilities that vendors have disclosed and issued patches for remain a major source of breaches. Why? Too many organizations take too long to deploy those patches — or never do.
That was the case with WannaCry. The ransomware exploited Windows vulnerability MS17-010, which Microsoft disclosed in mid-March 2017, rating it “Critical” and issuing a patch for it. The attacks began two months later. It was only then that most affected organizations began to install the patch. When the dust cleared, WannaCry had infected 300,000-plus systems, disrupting critical operations globally.
So why does this baffling problem persist?
As is true for most IT and security challenges, the patch management problem and its solution depend on a combination of the technology being used and of the processes in place.
Read on to learn about patch management best practices, and about Qualys’ new patch management cloud app.
Patch management tips and best practices
Adopt integrated breach prevention
Patch management should be part of an integrated, cloud-based set of solutions for breach prevention that also includes asset inventory, vulnerability management, and remediation prioritization.
When patch management is isolated, problems arise. For example, correlating vulnerabilities to patches becomes hard and time-consuming, and prioritizing remediation gets difficult. Consequently, time-to-remediation slows down.
Make PM a proactive practice
Organizations shouldn’t find themselves frequently going into emergency patching mode as happened with WannaCry. Instead, they should proactively remediate as patches are released, based on prioritization analysis.
In such a program, patch management is done routinely, in sync with vendor patch cycles. You shouldn’t wait for a vulnerability detection to trigger the patch management process.
For example, patch deployment jobs can be created for different types of devices to run on specific schedules. Rules and workflows can be configured so that patches are deployed automatically when they meet certain criteria, like severity level, CVSS score or product name.
That’s the goal of a patch management program: To have repeatable patching. Of course, you also need flexibility to occasionally go outside of the regular patching process and deploy an “out of band” patch, should you need to.
Get full patch visibility and centralized control
Organizations need to know which patches they’ve deployed, which are missing, and how the process should flow for optimal results. Otherwise, they’ll experience delays and gaps in patching, putting the organization at risk.
Thus, it’s essential to discover missing patches quickly, comprehensively and at scale across assets located on prem, in clouds, and at remote endpoints. Moreover, organizations must be able to track patch status from a central dashboard, and generate reports that can be customized for different types of recipients.
Correlate vulnerabilities and patches automatically
To increase remediation response time, organizations must move from manual to automated correlating of vulnerabilities and patches, to more quickly identify what patches must be deployed to fix the detected vulnerabilities.
To fix one CVE (Common Vulnerabilities and Exposures), it’s often necessary to install multiple patches, because the vulnerability could be present in different versions of the same software product.
If you have to manually track down which patch goes with which vulnerability, your mean-time-to-remediation will be inevitably long. To automate this task, your patch management product should index patch data with vulnerability information, so that when a user enters a CVE number, they instantly get a list of required patches.
Check right away the effectiveness of remediation
It’s advisable to use continuous agent-based scanning, and also to do frequent authenticated scans, so your patching’s effectiveness — or lack thereof — becomes quickly clear by tracking patches on an ad hoc basis from a central dashboard.
Many patch teams have to wait for a scheduled vulnerability management report to find out if the latest deployed patches in fact worked. Sometimes these reports come out weekly or even less frequently. This becomes an issue particularly when a patch has to be re-deployed. If you’re waiting a week to scan your systems, that’s a week before you know whether your remediation is working.
Don’t forget about remote systems
It’s a challenge to deploy patches on remote systems that connect to the corporate network intermittently and infrequently. But you have to. Those systems are out there vulnerable, being used to surf the web and conduct e-commerce transactions, and they must have the latest patches. This process can be simplified and streamlined with a patch management product that leverages agents installed on each asset, because it can use the agents to deploy patches to these systems.
Make patch management OS- and vendor-agnostic
It’s common for patch management tools to work only with products from one vendor, or with one type of software. This forces organizations to have multiple patching products, and prevents them from having a unified view of the patching process. Instead, look for a product that can be used to patch operating systems and applications from different vendors, and that can manage vendor-specific patch repositories.
How Qualys can help
The recently launched Qualys Patch Management cloud app streamlines and automates the entire patching process, helping organizations fix bugs quickly, proactively and consistently.
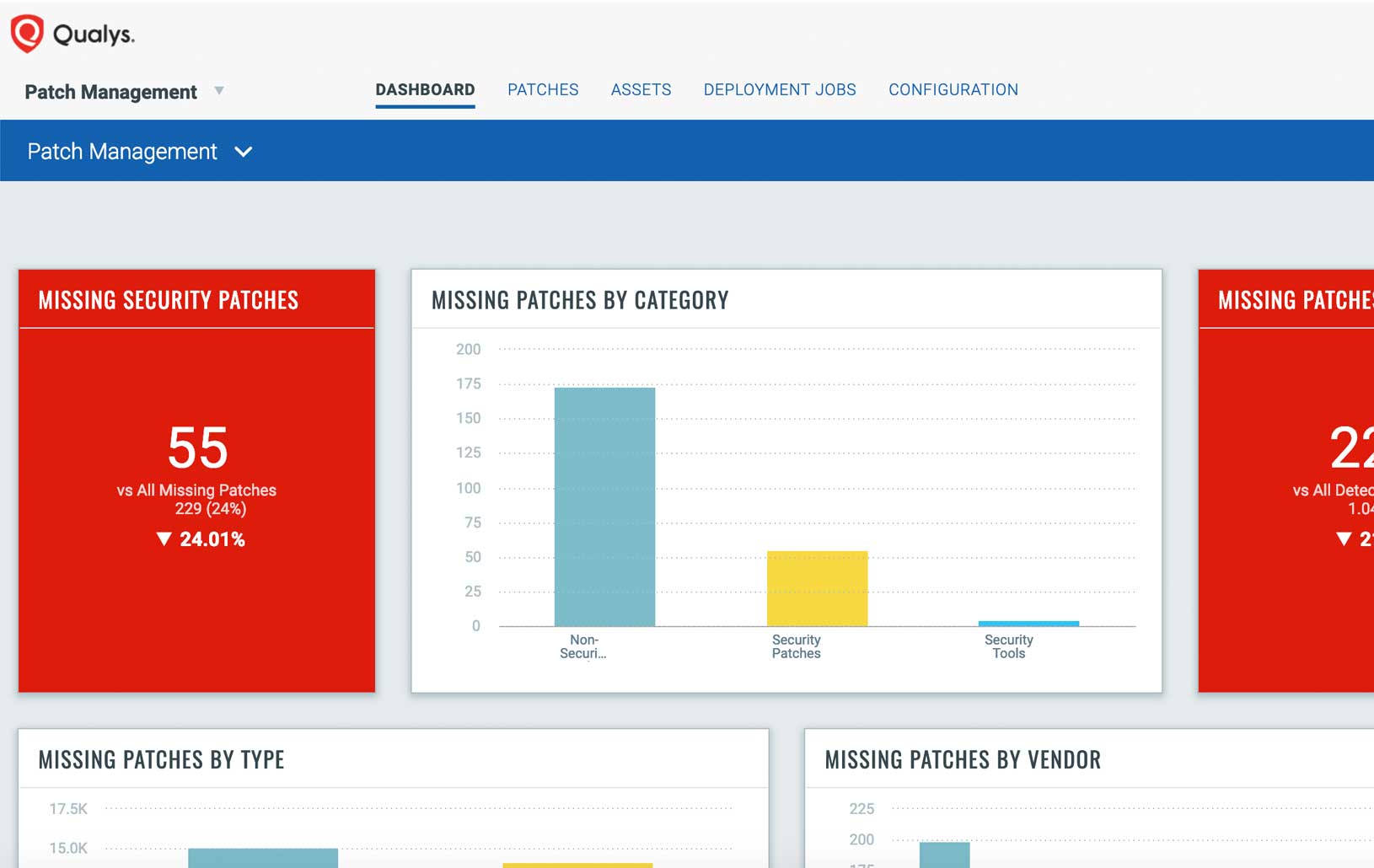
Qualys PM keeps organizations up to date on missing patches. It evaluates patch detections on the same schedule as vulnerabilities, and recommends by default a patch’s most current version. Its configurable dashboards and reporting functionality allow organizations to easily track patch status.
Qualys PM also correlates vulnerability and patch data, so organizations know which vulnerabilities are fixed by a specific patch, as well as which patches fix a specific vulnerability. Because it uses the Qualys Cloud Agent, as other Qualys apps do, Qualys PM works on internal, roaming and cloud-based assets.
Qualys PM can be used for scheduled patching, and for one-off jobs, like emergency patches. It unifies reporting and visibility, so organizations have in one place all the information about vulnerabilities, patches, and issues that must be remediated urgently.
In addition, Qualys PM is integrated with Qualys Asset Inventory, Qualys Vulnerability Management, and Qualys Threat Protection, providing comprehensive breach prevention. As such, vulnerabilities are detected across all IT assets, wherever they reside. A continuously updated asset inventory provides a unified view of IT and security data. And real-time threat information is layered on top of the vulnerability detections for remediation prioritization.
In short, with Qualys PM, organizations can shift from reaction mode to proactive operational security, and help their IT and security teams speak the same language in the context of assets and vulnerabilities.
(Jimmy Graham is Senior Director of Product Management at Qualys)