Qualys Continuous Monitoring 1.4 New Features
Last updated on: September 6, 2020
Many enterprise customers use Security Information and Event Management (SIEM) solutions to correlate security threat data from different sources, and to create reports for auditing purposes. We’re pleased to introduce the new Continuous Monitoring (CM) API that allows users to directly integrate CM alerts with existing SIEM solution. Use this API to download alerts in CEF format – an industry standard format – and search and get information from your CM account.
The latest version of Qualys Continuous Monitoring (CM) version 1.4 includes the following new features and enhancements:
- New CM API to Integrate CM Alerts with your SIEM
- Enhancements to the Ruleset Builder
- Get alerts on PCI vulnerabilities
You can run these CM API operations: Get Alert | Get Profile | Get Ruleset | Get Rule | Search Alerts | Search Profiles | Search Rulesets | Search Rules | Download Alerts (cef and csv formats)
Download Alerts Example
Download all Open Port alerts in CEF format.
API Request
curl -u "USERNAME:PASSWORD" -H "content-type: text/xml" -X "POST" --data-binary @- "https://qualysapi.qualys.com/qps/rest/1.0/download/cm/alert/?format=cef" < file.xmlNote: “file.xml” contains the request POST data.
API Request POST Data
<ServiceRequest>
<filters>
<Criteria field="eventType" operator="EQUALS">PORT_OPEN</Criteria>
</filters>
</ServiceRequest>Sample CEF Output
Jun 06 2014 15:43:9 83306MM.local 10.40.2.210
CEF:0|QUALYS|QualysGuard|CM-1.4|PORT|PORT_OPEN|0|cat=PORT dhost=2k8core-30-21.2k864sp0.qualys.com dst=10.10.30.21 dmac=NA dntdom=2K8CORE-30-21 rt=Nov 05 2013 15:57:21 cs1operatingSystem=Windows 2008 Enterprise Server Service Pack 2 dpt=61466 cs2protocol=udp cs3defaultService=NA
CEF:0|QUALYS|QualysGuard|CM-1.4|PORT|PORT_OPEN|0|cat=PORT dhost=2k8core-30-21.2k864sp0.qualys.com dst=10.10.30.21 dmac=NA dntdom=2K8CORE-30-21 rt=Nov 05 2013 15:57:21 cs1operatingSystem=Windows 2008 Enterprise Server Service Pack 2 dpt=61466 cs2protocol=udp cs3defaultService=NA
CEF:0|QUALYS|QualysGuard|CM-1.4|PORT|PORT_OPEN|0|cat=PORT dhost=xp-30-32.qualys.com dst=10.10.30.32 dmac=NA dntdom=XP-30-32 rt=Nov 21 2013 19:42:56 cs1operatingSystem=Windows XP dpt=445 cs2protocol=tcp cs3defaultService=microsoft-dsYou can also download alerts in CSV format. Use format=csv in the API request.
Sample CSV Output
"AlertId","Event Type","ProfileId","Profile Name","IP Address","Hostname","Operating System","Event Date","Alert Date"
"237124","PORT_OPEN","7401","All Critical","10.10.30.21","2k8core-30-21.2k864sp0.qualys.com","-","2013-12-31 15:57:21","2013-12-31 15:57:22"
"237172","PORT_OPEN","5601","Matt’s Profile","10.10.30.21","2k8core-30-21.2k864sp0.qualys.com","-","2013-12-31 15:57:21","2013-12-31 15:57:23"
"238503","PORT_OPEN","7401","All Critical","10.10.30.32","xp-30-32.qualys.com","-","2014-01-16 19:42:56","2014-01-16 19:42:58"For more details, please refer to the Continuous Monitoring API blog post.
Enhancements to the Ruleset Builder
You can now create more complex rules using the Ruleset Builder. Create a rule that includes different sets of criteria like port criteria and host criteria. This could be used for example to get an alert for a specific host rather than being alerted on all hosts.
For example, create rules to get alerts in these cases:
- Open ports (except 80 or 443) on Linux hosts
- Certificates expiring in the next 30 days on hosts with “order” in the hostname (e.g. order01.phoenix.acme.com)
- Firefox installed on Windows hosts
Want to add a second rule to the Ruleset? Start by dragging a rule type from the left to the right. Then customize the new rule. Rules in the ruleset will be labeled Rule 1, Rule 2, Rule 3, and so on.
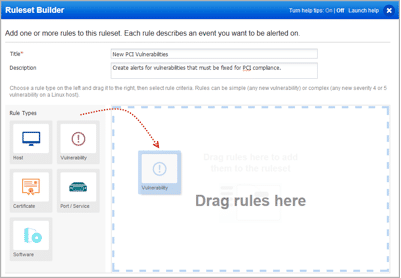
Get Alerts on PCI Vulnerabilities
With this release you can monitor for PCI vulnerabilities – vulnerabilities that must be fixed in order to maintain PCI compliance. It’s easy to set this up.
Let’s say you want to get alerts for all new vulnerabilities that impact PCI compliance.
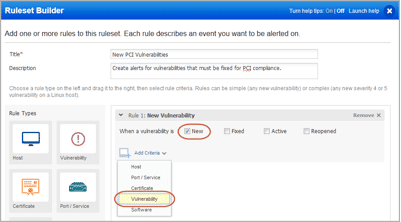
1. In the Ruleset Builder, drag the Vulnerability rule type from the left to the right.
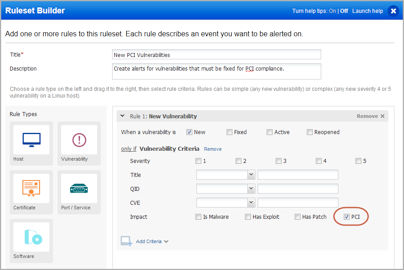
2. Now customize the rule – select New, and then choose Vulnerability from the Add Criteria drop-down.
3. Select the PCI option. This means you’ll get alerts for vulnerabilities that impact PCI compliance.
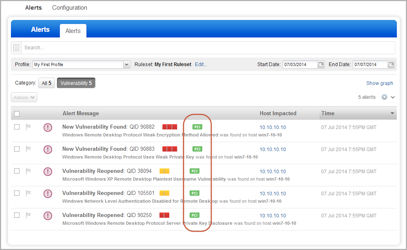
4. Alerts for PCI vulnerabilities are flagged with ![]() so you can easily find them and take action
so you can easily find them and take action