So Many Vulnerabilities, So Little Time: Threat Protection Identifies the Assets You Must Patch Now
Last updated on: September 6, 2020
If you are an information security professional, you’ve probably experienced vulnerability disclosure overload. We’re referring to that acute sense of feeling burdened that can afflict even the best infosec teams. This ailment strikes when infosec pros grapple with the constant release of vulnerability announcements, amounting to thousands per year.
The truth is that no IT department has enough staff and resources to promptly patch every single vulnerability within their environment. As a result, infosec teams must be highly selective when drafting their vulnerability remediation plans. They must strategically address the threats that represent the highest risk to their organization at any given point.
Unfortunately, pinpointing which IT assets must be patched with the greatest urgency is no easy task. That’s why Qualys developed Threat Protection, a cloud-based application that takes the guesswork out of the process of prioritizing vulnerability fixes.
What is Threat Protection?
The latest addition to the security and compliance Qualys Cloud Platform, Threat Protection does the heavy lifting for you, performing continuous, in-depth risk analysis of vulnerabilities within your IT environment.
With Threat Protection, you can precisely and quickly determine which among your IT assets has the highest exposure to the latest threats, helping you keep your organization safe from catastrophic breaches.
After all, it’s well known that the overwhelming majority of successful cyber attacks exploit vulnerabilities for which patches have been available for weeks, months or even years. Most breaches can be traced back to fewer than 10 basic attack patterns.
Every morning, Threat Protection greets you with a list of top vulnerabilities to remediate. And throughout the day, as new threats are identified, Threat Protection will refresh this list, so that you always have an up-to-date view of the IT assets requiring immediate remediation.
How Does Threat Protection Work?
Threat Protection constantly collects vulnerability disclosure data and instantly correlates it against your IT asset inventory, leveraging its tight integration with AssetView and Vulnerability Management, two other Qualys Cloud Platform applications.
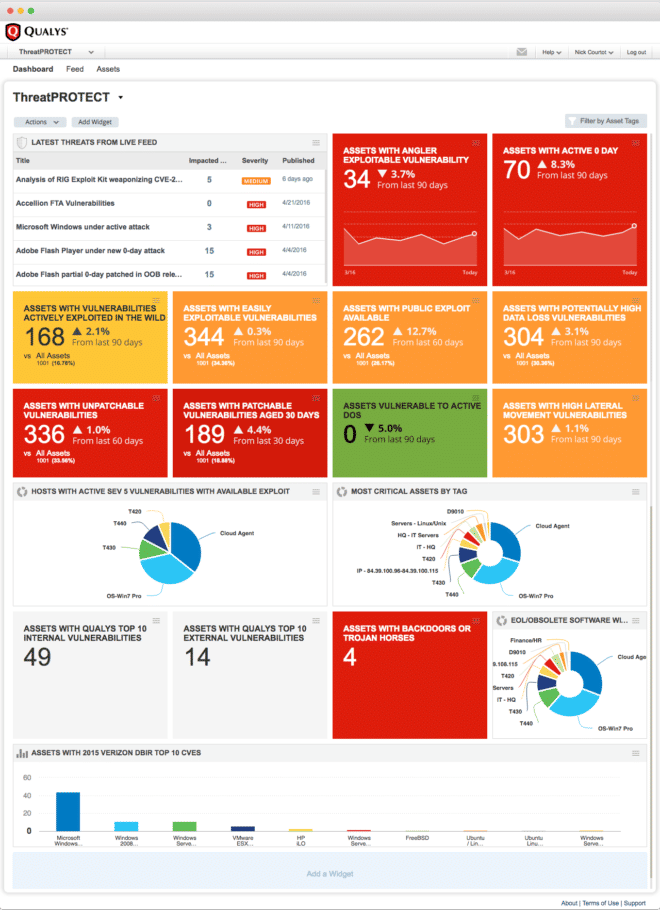
In this way, Threat Protection provides at a glance a clear and comprehensive view of your organization’s threat landscape through its holistic dashboard with customizable views, graphs, charts, search engine and real-time feed of the latest vulnerability disclosures.
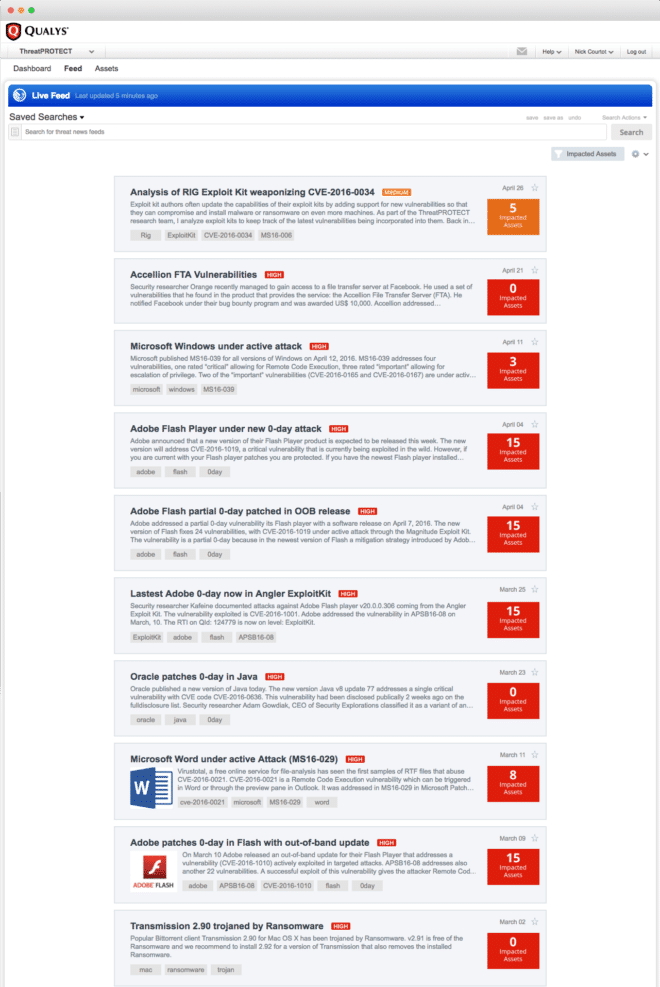
The Live Threat Intelligence Feed: Threat Protection’s Live Threat Intelligence Feed not only lists the latest vulnerability announcements, but also, thanks to the product data correlation capabilities, it displays how many of your IT assets are impacted by each disclosure.
You can click on feed entries and drill down into more granular details of the vulnerability and of your affected assets.
Dynamic Dashboard Views: In addition to the live feed, the Threat Protection dashboard also contains dynamic, customizable views displaying specific stats, such as assets with active zero-day vulnerabilities.
As with the live feed entries, you can click through them and access more information about the assets flagged as vulnerable.
Search Engine: Threat Protection’s search engine offers you a powerful tool when you want to proactively go looking for specific assets.
Queries can contain multiple variables and criteria, such as asset class, vulnerability type, operating system and the like. Search results can then be further sorted and refined using a variety of filtering criteria.
These ad hoc search queries can be saved and turned into permanent dashboard views, so you don’t have to run the same query every time you want to know, say, which Windows 10 PCs have unpatched Adobe Flash vulnerabilities.
Reports, Graphs, Charts, Notifications: With Threat Protection you can generate reports, graphs and charts for display on your dashboard, as well as for sharing them with colleagues.
Threat Protection can also generate and send you notifications when used in conjunction with the Qualys Cloud Platform’s Continuous Monitoring application.
Threat Protection’s Fuel: Threat Analysis from Qualys’ World-Class Research Labs
Qualys’ global team of researchers is constantly monitoring and tracking RTI (real-time threat indicator) data points, such as attacks and exploits. But these Qualys experts go much deeper into the data, analyzing it in depth to further classify these RTIs into more precise categories.
This threat categorization is essential to have in order for infosec teams to prioritize remediation in a way that is truly effective and precise. These are the RTI attributes Threat Protection identifies:
- Zero Day: A vulnerability for which there is no vendor patch available and for which an active attack has been observed in the wild
- Public Exploit: A vulnerability whose exploit knowledge is well known and for which exploit code exists and is publicly available, even if no active attacks have been observed in the wild
- Actively Attacked: A vulnerability that is being actively attacked in the wild
- High Lateral Movement: A vulnerability that, if compromised, lets the attacker propagate the attack broadly throughout the breached network
- Easy Exploit: A vulnerability that can be exploited easily, requiring few skills and knowledge
- High Data Loss: A vulnerability whose exploit will yield massive data loss
- Denial of Service: A vulnerability whose payload is to overload the compromised systems so that they become permanently or temporarily unavailable
- No Patch: A vulnerability for which there isn’t an official fix
- Malware: A vulnerability associated with malware infection
- Exploit Pack: A vulnerability for which an exploit pack is available
Insights and Clarity for Prioritizing Vulnerability Fixes
Not all vulnerabilities are created equal. Some can be devastating, while others are trivial. Threat Protection helps you see these differences across all your IT assets, so that you can prioritize how you address your vulnerabilities.
And it does this continuously, because a vulnerability rated low risk for months can become critical overnight if, say, an exploit kit becomes available for it. Or maybe an IT asset has suddenly turned into a dangerous vector for a possible attack because an employee installed some unapproved software without permission.
Don’t feel overwhelmed by vulnerabilities. Don’t fumble in the dark of your IT asset inventory. Save time. Know what to remediate first. And, most importantly, don’t get breached. Give Threat Protection a try.