Assess Vulnerabilities, Misconfigurations in CI/CD Pipeline
Last updated on: December 19, 2022
Table of Contents
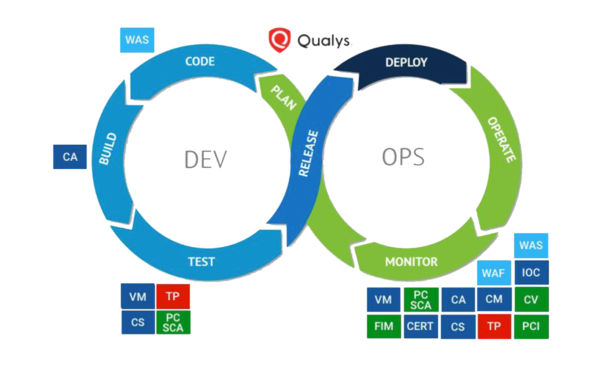
After the publication of Golden AMI Pipeline integration with Qualys, some Qualys customers reached out asking how to integrate Qualys Vulnerability Management scanning into other types of CI/CD Pipelines. To answer these questions, we’ve published the new guide, Assess Vulnerabilities and Misconfiguration in CI/CD Pipelines.
This guide details the integration of Qualys vulnerability scanning into your pipeline in a language-, tool-, and cloud- (technology/platform) agnostic approach. It highlights the design considerations, the associated API calls needed, the response data structures, how to process response data, guidelines on setting pipeline failure thresholds, as well as tips for success.
By walking through what API calls need to be made, how to format the calls, and what the response data will be, this guide takes the guesswork out of designing and implementing a CI/CD pipeline integration with Qualys Virtual Scanner Appliances in your pipelines.
Accompanying this post is a PDF and a Postman collection for all the referenced API calls contained within the document. This Postman collection is used in conjunction with Qualys Postman Environment Collection. Once both collections are installed, you can utilize the Postman client to simulate the API calls in your environment and your subscription data to have a better understanding of your Qualys API query response data.
Reference
Access Vulnerabilities and Misconfiguration in CI/CD Pipelines