Patch Tuesday October 2013
Last updated on: October 27, 2022
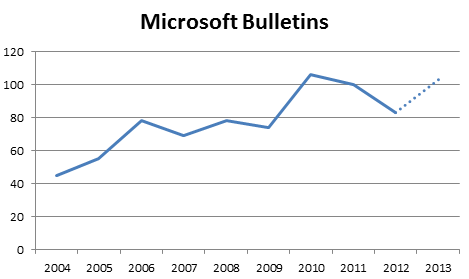
The 10th anniversary of Patch Tuesday is bringing a busy month for IT administrators, with patches from Microsoft, Adobe and Oracle due this month. Just from a Microsoft perspective, it looks as if we will reach or exceed the 100 mark of bulletins this year:
Microsoft Patch Tuesday for October 2013 has eight bulletins addressing 26 vulnerabilities. Five of the Microsoft bulletins have Remote Code Execution potential, and of course we are also getting an updated Internet Explorer that addresses the currently open 0-days. Yes, 0-days in plural, because MS13-080 actually patches two vulnerabilities that are out and used in the wild.
The top bulletin this month is MS13-080, which fixes 10 vulnerabilities, including CVE-2013-3893, the 0-day that Microsoft originally acknowledged in September as having limited and targeted attacks in Asia. KB2887505 provides a Fix-it link that uses a Microsoft mechanism called “appcompat shim” to counter that exploit reliably. The discussion around a potential earlier release of this bulletin, MS13-080, really depended on the amount of ongoing attacks that were being detected by Microsoft and the security community in general. Since the volume continued to stay low, even after Metasploit added their implementation, Microsoft opted for a normal release schedule during Patch Tuesday, which places the least stress on IT organizations.
MS13-080 also addresses CVE-2013-3897 in an interesting case that illustrates the concurrent discoveries of vulnerabilities. The vulnerability underlying CVE-2013-3897 was found internally at Microsoft and would have been fixed in MS13-080 as part of the normal security engineering and hardening that the product undergoes constantly. However, in the last two weeks, attacks against the same vulnerability became public, again limited and targeted in scope, but since the fix was in the code already, it enabled Microsoft to address the vulnerability, CVE ID CVE-2013-3897, in record time. By the way the same, but less public reasoning about attack volume as for CVE-2013-3893 has been applied in this case as well: if there had been widespread reports of the vulnerability being used to exploit networks it would have triggered an out-of-band release. Take a look at Microsoft’s SRD blog for a more details on both CVEs.
Anyway, MS13-080 is your most important patch this month. There is definitely a large possibility that the exploit CVE-2013-3893 will become incorporated into the common Exploit Kits and will become more widely used. You should apply this bulletin as fast as possible.
The next bulletin on our list is MS13-081, which addresses seven vulnerabilities in the Windows kernel. It is rated “critical” because two of the vulnerabilities are in font handling and can be triggered remotely through malicious web pages and maliciously formatted Office documents. There are no known exploits at the moment, but you should patch these flaws urgently as we have seen font type vulnerabilities abused before.
Next on our priority list are MS13-085 and MS13-086, both Remote Code Execution-type vulnerabilities in Microsoft Excel and Microsoft Word. Both address flaws that were found during a fuzzing exercise at the Google Security Team. The most likely attack vector would be through spear-phishing by sending malicious Office files to selected targets.
This is also the same class of vulnerability that is being addressed by Adobe today. Their new version of Adobe Reader (APSB13-25) should be high on your patching priority list as well, as PDF is a frequently attacked file-format.
Back to Microsoft, MS13-083 addresses a flaw in the widely used “comctl32” library. There is no Microsoft product that exposes a direct attack vector, but it is possible that your third party programs could be used for an external attack. You should include it in your normal patch cycle.
The remaining bulletins MS13-082, MS13-084 and MS13-087 are rated “important” and respectively address a .NET XBAP application. Sharepoint and Silverlight and should be included in your normal patching routine if you run the affected products.
Overall, this is a challenging and busy month with the high priority Internet Explorer patches and the additional patching from Adobe, plus the patches for next week that we can expect for all Oracle products, including Java. Our perspective has certainly evolved from 10 years ago when Patch Tuesday was started, back then vulnerabilities were clear cut and straightforward to understand, today the amount of complexity that goes into the detection and remediation process is truly impressive. At the same time, attackers have shifted to client side vulnerabilities, a change that we only partly assimilated; we are good in addressing the browser vulnerabilities, but generally lag behind in other areas that will be in focus this month such as Adobe Reader and Java.
Stay tuned to this blog, as we will update it as soon as we get more information.