Microsoft Windows Print Spooler RCE Vulnerability (PrintNightmare-CVE-2021-34527) – Automatically Discover, Prioritize and Remediate Using Qualys VMDR®
Last updated on: December 22, 2022
Table of Contents
- About PrintNightmare
- Affected Products
- Identify Assets, Discover, Prioritize and Remediate Using Qualys VMDR
- Identification of Windows Assets with Print Spooler Running
- Discover PrintNightmare CVE-2021-34527 Vulnerability
- Dashboard
- Response by Patching and Remediation
- Identify and Address System Misconfigurations
- Registry Settings Check After Installing the Updates
- Workaround
- Get Started Now
Update July 9, 2021: Added “Registry Settings Check After Installing the Updates” section below.
Original Post: On June 29, 2021, a zero-day exploit was observed on Microsoft Windows systems which allows authenticated users with a regular Domain User account to gain full SYSTEM-level privileges. On July 1, 2021, Microsoft released a separate advisory linking this zero-day to CVE-2021-34527 as a confirmed Remote Code Execution (RCE) vulnerability. According to the new advisory, the PoC is publicly disclosed and actively exploited in the wild.
On July 6, 2021, Microsoft released patches to address the PrintNightmare zero-day vulnerabilities.
On July 7, 2021, after Microsoft patches were released, some security researchers found that these were incomplete patches and threat actors could still leverage local privilege escalation vulnerability to gain access to the system.
Per BleepingComputer news, “After update was released, security researchers Matthew Hickey, co-founder of Hacker House, and Will Dormann, a vulnerability analyst for CERT/CC, determined that Microsoft only fixed the remote code execution component of the vulnerability. However, malware and threat actors could still use the local privilege escalation component to gain SYSTEM privileges on vulnerable systems for older Windows versions, and for newer versions if the Point and Print policy was enabled.”
About PrintNightmare
PrintNightmare (CVE-2021-34527) is a vulnerability that allows an attacker with a regular user account to take over a server running the Windows Print Spooler service. This service runs on all Windows servers and clients by default, including domain controllers, in an Active Directory environment. Print Spooler, which is enabled by default on Microsoft Windows, is an executable file that manages print jobs sent to the computer printer or print server.
A team of security researchers from Sangfor discovered this zero-day vulnerability. In a tweet they wrote,
“We deleted the POC of PrintNightmare. To mitigate this vulnerability, please update Windows to the latest version, or disable the Spooler service. For more RCE and LPE in Spooler, stay tuned and wait our Blackhat talk.”
The GitHub repository was taken offline after a few hours, but not before it was cloned by several other users.
PrintNightmare execution looks for kernelbase.dll, unidrv.dll files along with any other DLLs written into subfolders of “C:WindowsSystem32spooldrivers” in the same timeframe by spoolsv.exe. A hard-coded printer driver path is not required as one can use EnumPrinterDrivers() to find the path for unidrv.dll.
Affected Products
All Windows servers and clients, including domain controllers.
Identify Assets, Discover, Prioritize and Remediate Using Qualys VMDR®
Use Qualys Vulnerability Management, Detection, and Response (VMDR) for:
- Identification of known and unknown hosts running vulnerable Windows servers with Print Spooler service
- Automatic detection of vulnerabilities and misconfigurations for Windows systems
- Prioritization of threats based on risk
- Integrated patch deployment
Identification of Windows Assets with Print Spooler Running
The first step in managing vulnerabilities and reducing risk is identification of assets. VMDR enables easy identification of windows server hosts with Print Spooler service running
operatingSystem.category1:`Windows` and services.name:`Spooler`
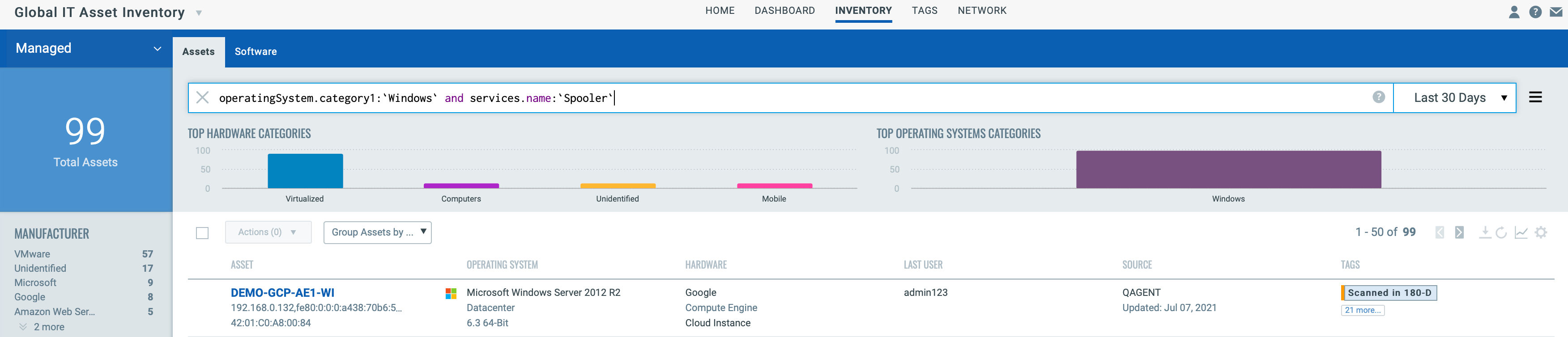
Once the hosts are identified, they can be grouped together with a dynamic tag, e.g. “PrintNightmare”. This helps in automatically grouping existing Windows hosts with the PrintNightmare vulnerability as well as any new host that spins up with this vulnerability. Tagging makes these grouped assets available for querying, reporting and management throughout the Qualys Cloud Platform.
Discover PrintNightmare CVE-2021-34527 Vulnerability
Now that the Windows hosts with PrintNightmare are identified, you want to detect which of these assets have flagged this vulnerability. VMDR automatically detects new vulnerabilities like PrintNightmare based on the always updated Knowledgebase.
You can see all your impacted hosts for this vulnerability tagged with the ‘PrintNightmare’ asset tag in the vulnerabilities view by using QQL query:
vulnerabilities.vulnerability.qid: `91785`
This will return a list of all impacted hosts.
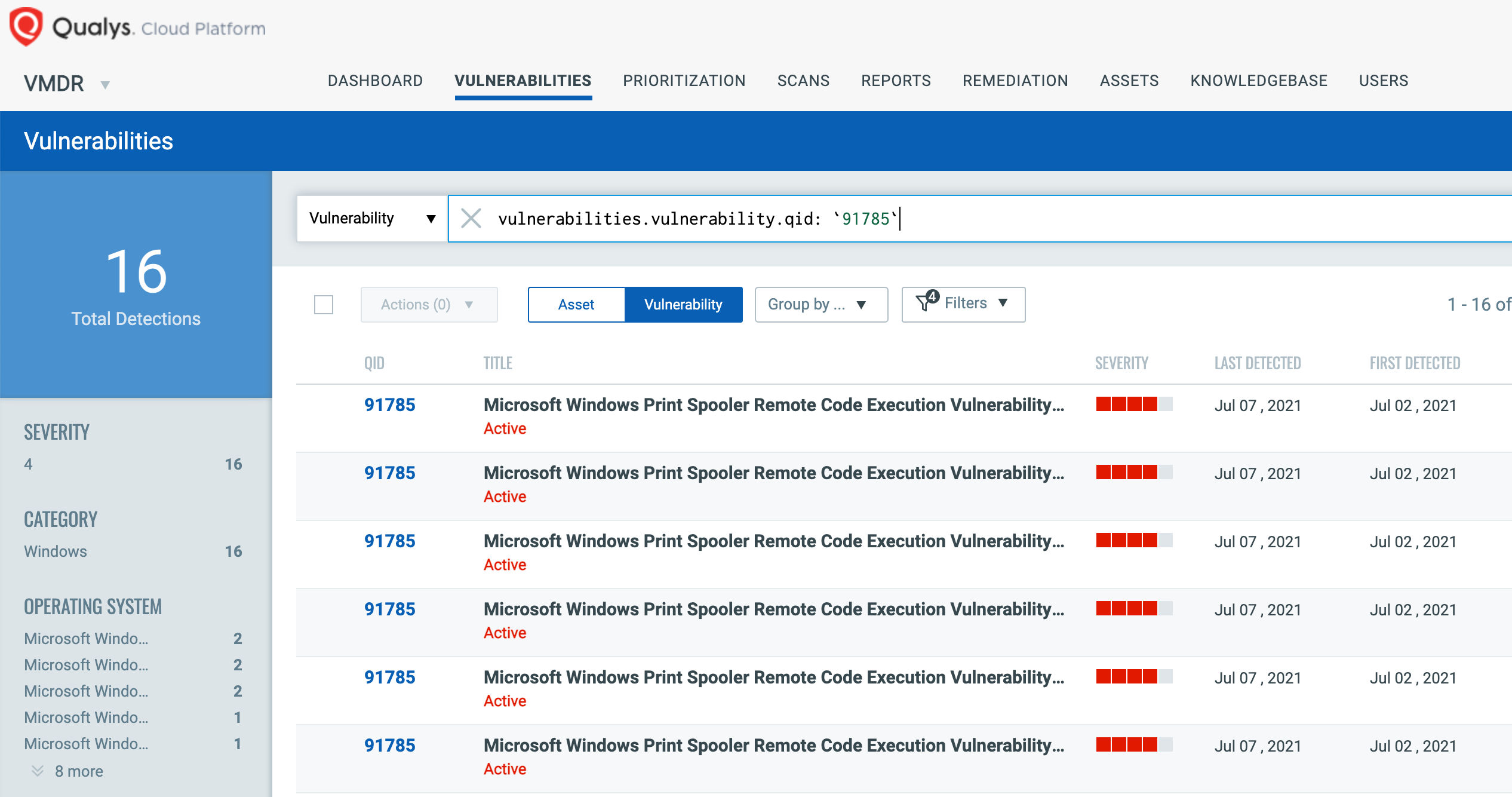
QID 91785 is available in signature version VULNSIGS-2.5.226-3 and above and can be detected using authenticated scanning or the Qualys Cloud Agent manifest version 2.5.226.3-2 and above.
Along with the QID 91785, Qualys released the following IG QID 45498 to help customers identify if Print Spooler service is running on Windows systems. This QID can be detected using authenticated scanning using VULNSIGS- 2.5.223-3 and above or the Qualys Cloud Agent manifest version 2.5.223.3-2 and above.
QID 45498: Microsoft Windows Print Spooler Service is Running
Update July 8, 2021: Qualys released QID 91786 to address the Zero Day. In addition, IG QID is released to identify if Point and Print restrictions are enabled. These QIDs can be detected using authenticated scanning using VULNSIGS- 2.5.228-3 and above or the Qualys Cloud Agent manifest version 2.5.228.3-2 and above.
QID 91786 Microsoft Windows Print Spooler Point and Print Insecure Configuration Detected (PrintNightmare)
QID 45499 Point and Print Restrictions NoWarningNoElevationOnInstall Is Enabled
Using VMDR, the PrintNightmare vulnerability can be prioritized for the following real-time threat indicators (RTIs):
- Remote Code Execution
- Privilege Escalation
- Public Exploit
- Active Attack
- Denial of Service
- High Data Loss
- High Lateral Movement
- Predicted High Risk
- Unauthenticated_Exploitation
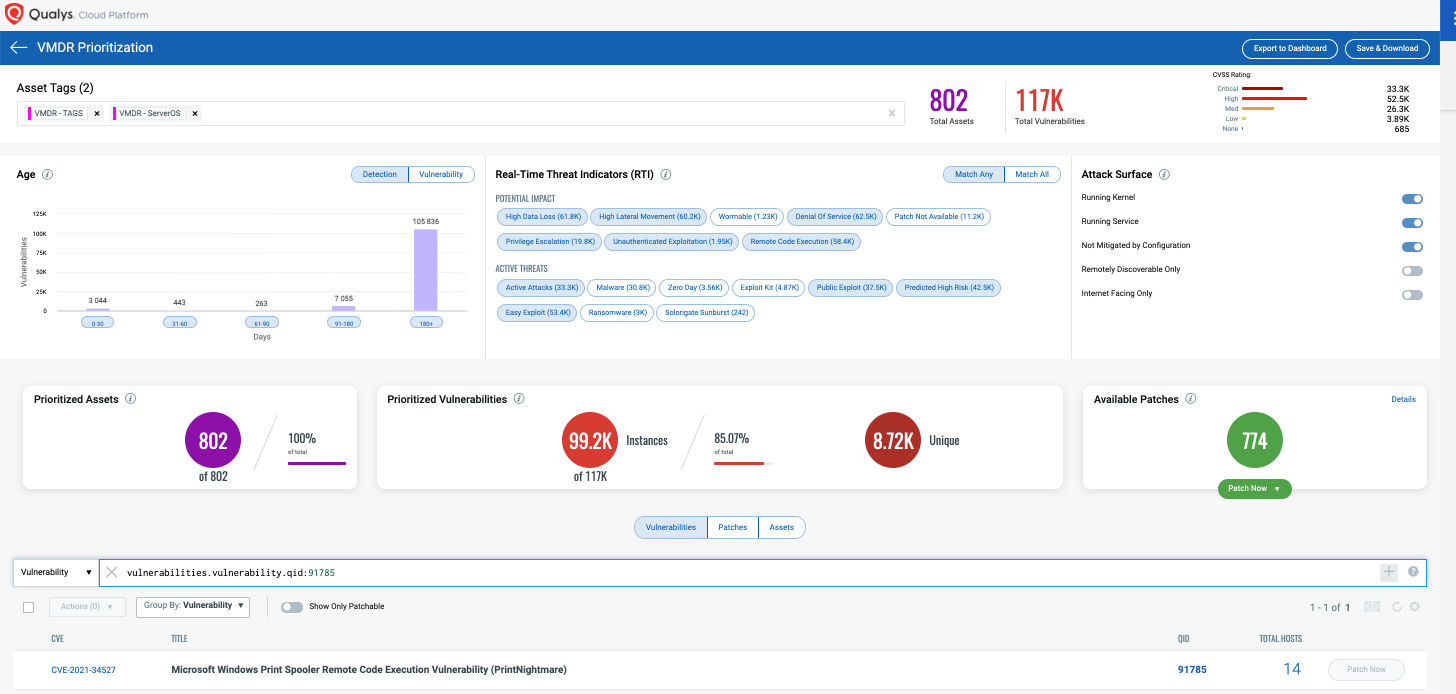
VMDR also enables you to stay on top of these threats proactively via the ‘live feed’ provided for threat prioritization. With ‘live feed’ updated for all emerging high and medium risks, you can clearly see the impacted hosts against threats.
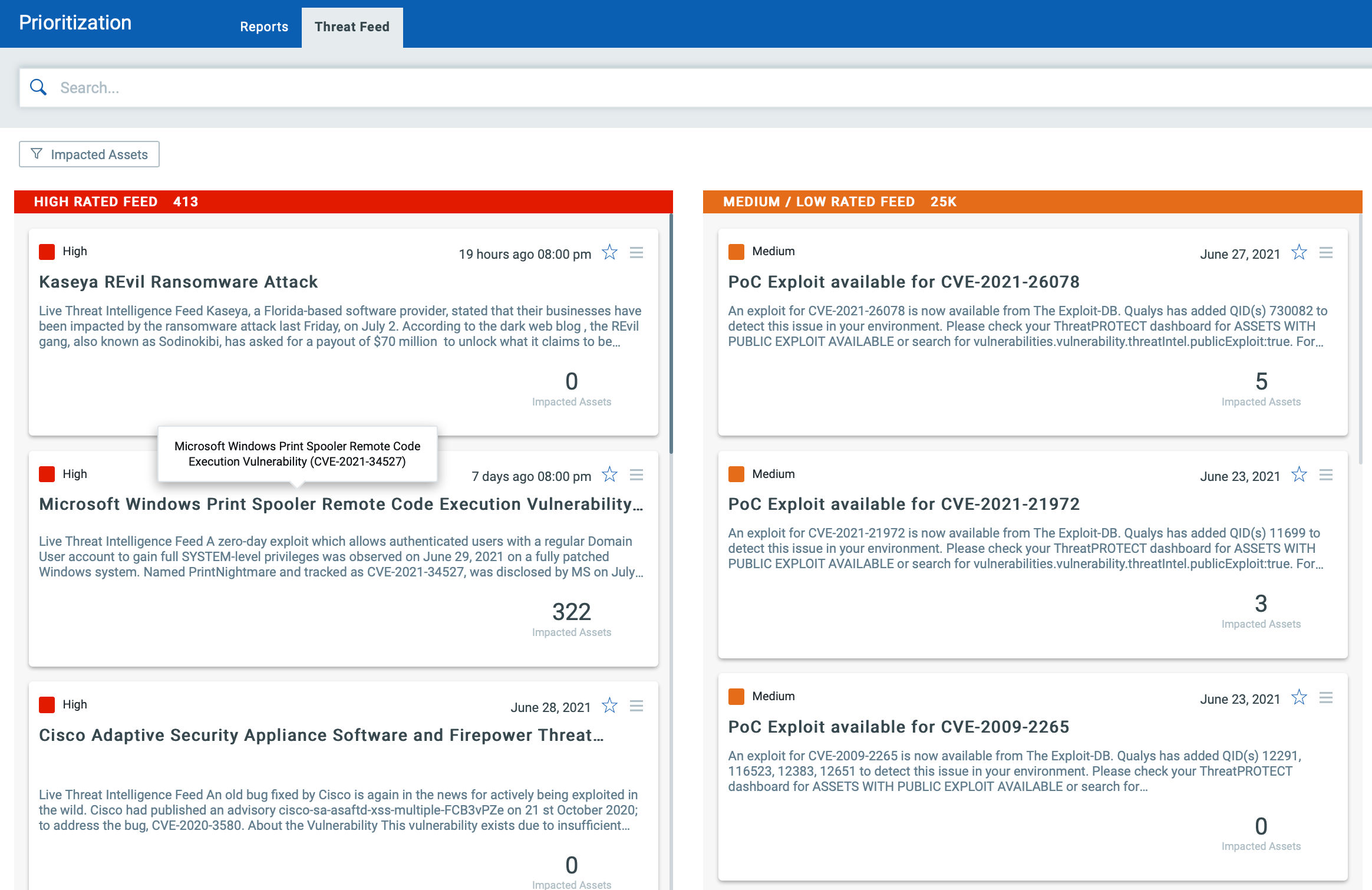
Simply click on the impacted assets for the PrintNightmare threat feed to see the vulnerability and impacted host details.
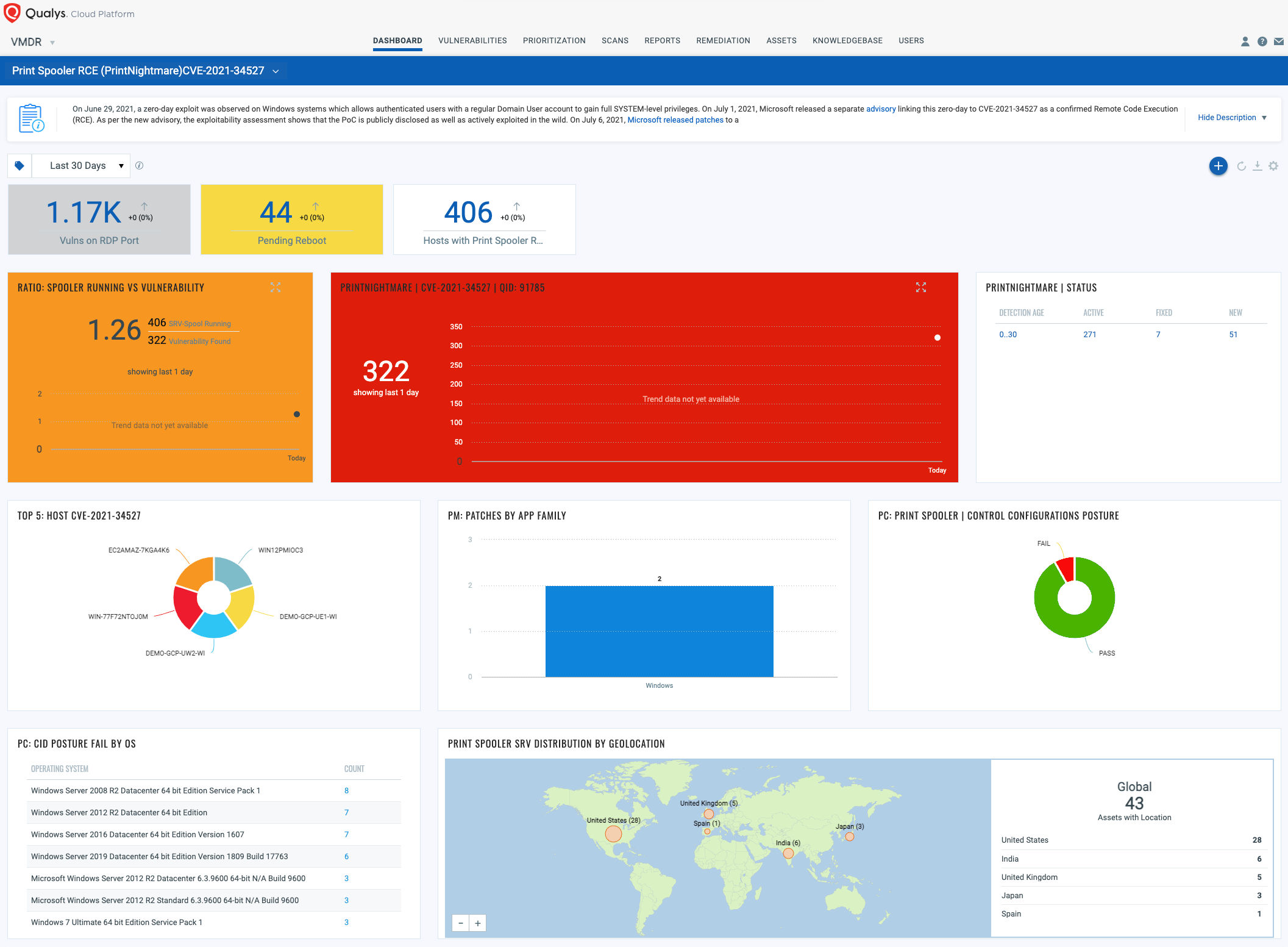
Dashboard
With VMDR Dashboard, you can track PrintNightmare, impacted hosts, their status and overall management in real time. With trending enabled for dashboard widgets, you can keep track of PrintNightmare vulnerability trends in your environment with the PrintSpooler RCE (PrintNightmare) dashboard.
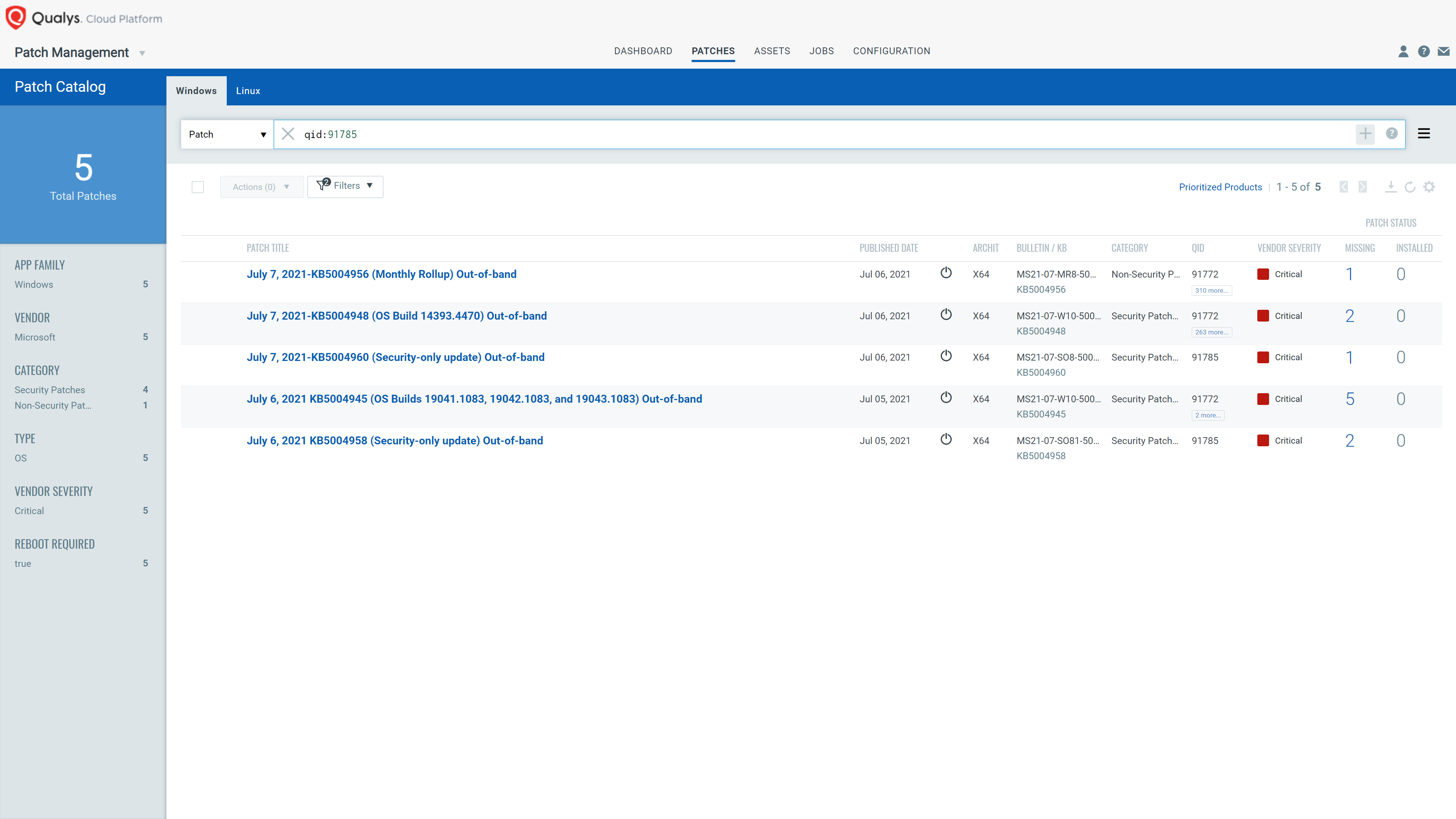
Response by Patching and Remediation
VMDR rapidly remediates the Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply search based on qid:91785 in the Patch Tab and filter on the “Missing” patches to identify and deploy the applicable, available patches in one go for hosts grouped together by a tag – PrintNightmare.
For proactive, continuous patching, you can create a daily job with a 24-hour patch window to ensure all hosts will continue to receive the required patches as new patches become available for emerging vulnerabilities.
Users are encouraged to apply patches as soon as possible.
Identify and Address System Misconfigurations
To reduce the overall security risk, it is important to take care of Windows system misconfigurations as well. Qualys VMDR shows your Windows system misconfiguration posture in context with your vulnerability posture, allowing you to see which hosts have the PrintNightmare vulnerability.
With the Qualys Policy Compliance module of VMDR, you can automatically discover the status of the ‘Print Spooler’ service and if they have misconfigurations in context to the PrintNightmare vulnerability.
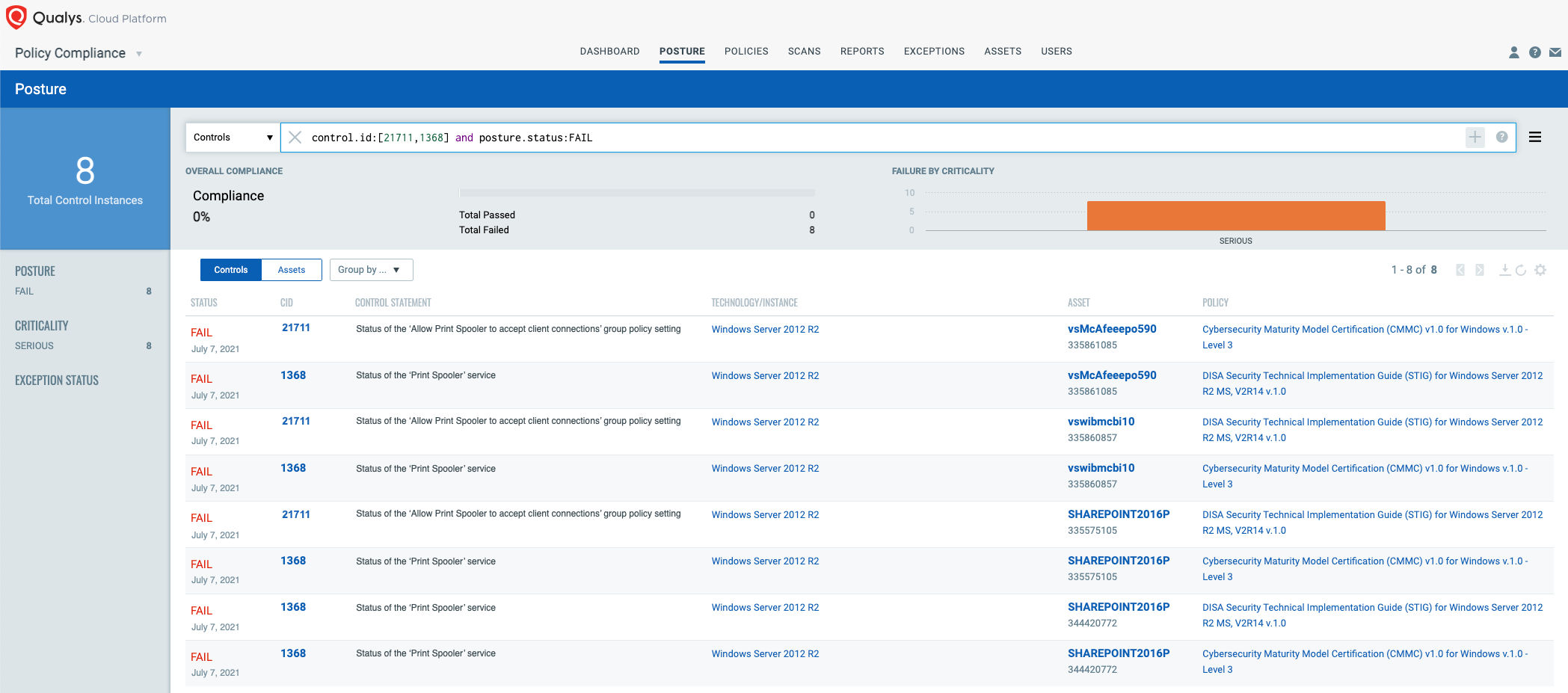
Qualys configuration ID – 1368 “Status of the ‘Print Spooler’ service”
” would be evaluated against all Windows systems as shown below
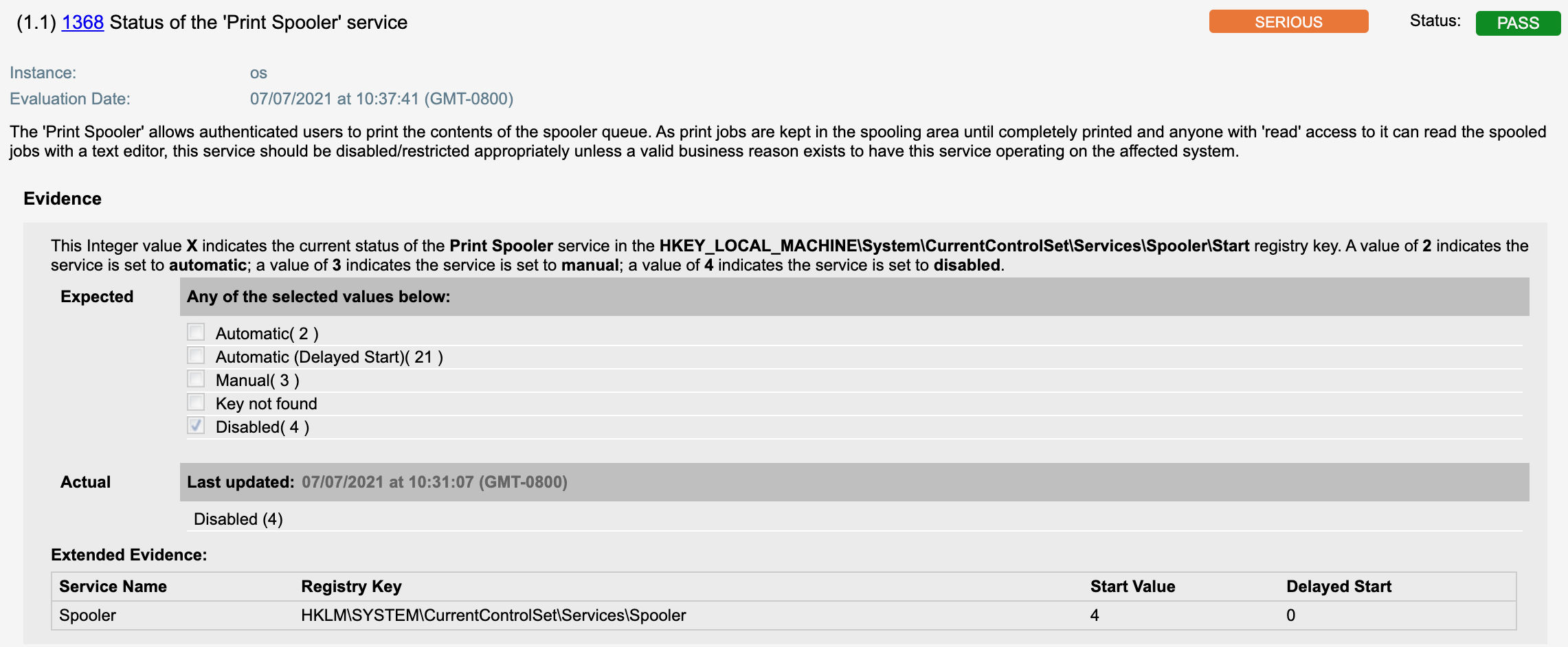
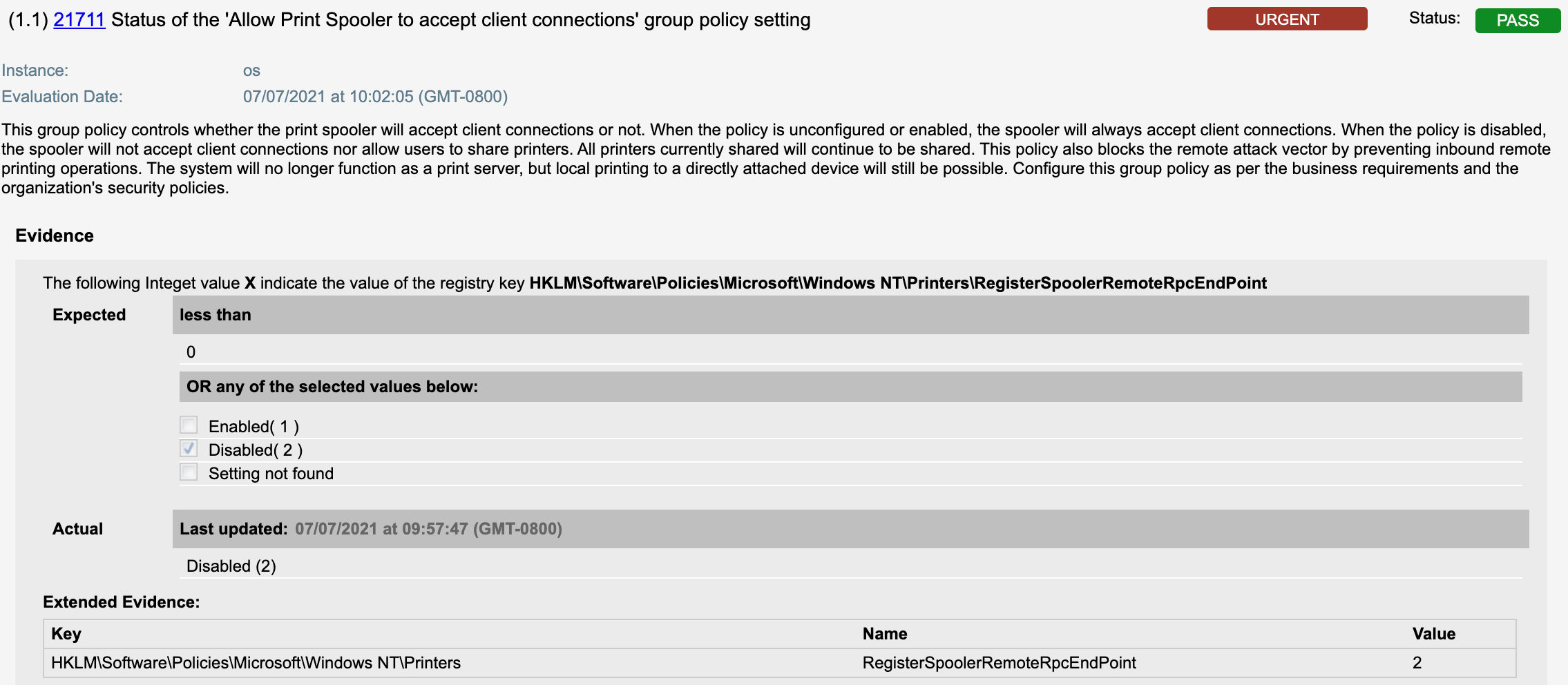
21711 Status of the ‘Allow Print Spooler to accept client connections’ group policy setting would be evaluated as shown below
Registry Settings Check After Installing the Updates
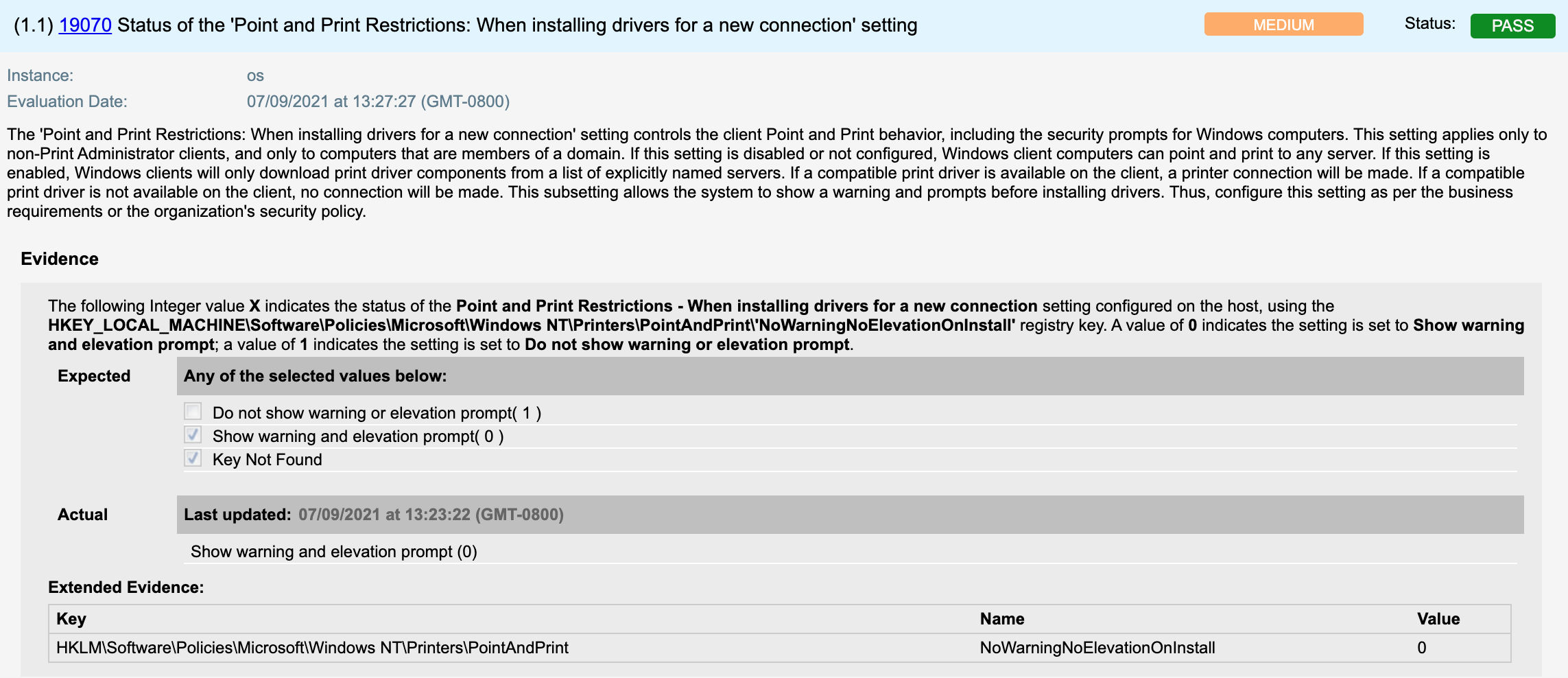
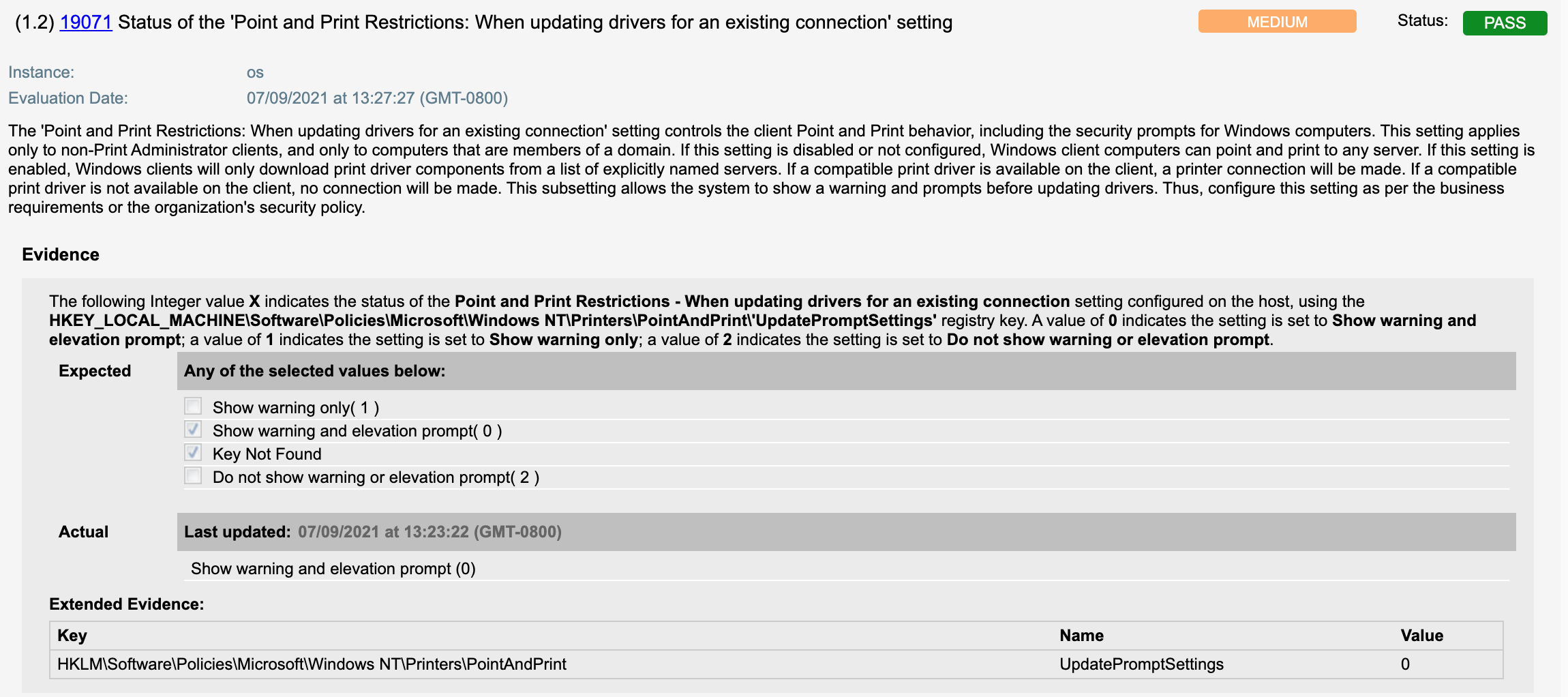
As reported in the Microsoft advisory on July 7, 2021: In addition to installing the updates, in order to secure your system, you must confirm that the following registry settings are set to 0 (zero) or are not defined (Note: These registry keys do not exist by default, and therefore are already at the secure setting.), also that your Group Policy setting are correct.
- HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
- NoWarningNoElevationOnInstall = 0 (DWORD) or not defined (default setting)
- UpdatePromptSettings = 0 (DWORD) or not defined (default setting)
Qualys Policy Compliance customers can evaluate the settings by the following two controls:
19070 Status of the ‘Point and Print Restrictions: When installing drivers for a new connection’ setting
19071 Status of the ‘Point and Print Restrictions: When updating drivers for an existing connection’ setting
Workaround
Users are urged to disable the “Print Spooler” service on servers that do not require it. Microsoft has provided a series of workarounds to be applied.
Determine if the Print Spooler service is running (run as a Domain Admin)
Run the following as a Domain Admin:Get-Service -Name Spooler
If the Print Spooler is running or if the service is not set to disabled, select one of the following options to either disable the Print Spooler service, or to Disable inbound remote printing through Group Policy:
Option 1 – Disable the Print Spooler service
If disabling the Print Spooler service is appropriate for your enterprise, use the following PowerShell commands:Stop-Service -Name Spooler -Force
Set-Service -Name Spooler -StartupType Disabled
Impact of workaround: Disabling the Print Spooler service disables the ability to print both locally and remotely.
Option 2 – Disable inbound remote printing through Group Policy
You can also configure the settings via Group Policy as follows:
Computer Configuration / Administrative Templates / Printers
Disable the “Allow Print Spooler to accept client connections:” policy to block remote attacks.
Impact of workaround: This policy will block the remote attack vector by preventing inbound remote printing operations. The system will no longer function as a print server, but local printing to a directly attached device will still be possible.
Per the above two options, Qualys Policy Compliance customers can do evaluation by the following two controls:
- 1368 Status of the ‘Print Spooler’ service”
- 21711 Status of the ‘Allow Print Spooler to accept client connections’ group policy setting
Get Started Now
Start your Qualys VMDR trial for automatically identifying, detecting and patching critical PrintNightmare vulnerability CVE-2021-34752.
Under the last heading, ‘Get Started Now’, you’ve written CVE-2021-34752 but that should be CVE-2021-34527
The query listed above only shows how to find Windows assets with the Print Spooler service. This does not check if it is actively running, which is the true goal of the search. Adding this to the end with resolve:
operatingSystem.category1:`Windows` and services.name:`Spooler` and services.status:running
The upper given descriptions shows a brief knowledege of print spooler. but it should also check whether it is actively running or not.