Text4Shell: Detect, Prioritize and Remediate The Risk Across On-premise, Cloud, Container Environment Using Qualys Platform
Last updated on: January 20, 2023
Table of Contents
- About Apache Common Text
- Potential Impact of Text4Shell Vulnerability
- Discover Vulnerable Assets Using Qualys CyberSecurity Asset Management (CSAM)
- Tagging Vulnerable Assets Using Qualys CyberSecurity Asset Management (CSAM)
- Discover Vulnerable Assets Using Qualys Vulnerability Management Detection and Response (VMDR)
- Windows Out-of-Band Detection for Text4Shell
- Execute the Detection Utility with Qualys Custom Assessment and Remediation (CAR)
- Gain exposure visibility and remediation tracking with Text4Shell Unified Dashboard
- Contributors:
On 2022-10-13, Apache Security Team disclosed a critical vulnerability with CVE-2022-42889 affecting the popular Apache Commons Text library. This vulnerability is popularly named “Text4Shell” which when exploited can allow an unauthenticated attacker to execute arbitrary code on the vulnerable asset. A CVSSv3 score of 9.8/10 is assigned to this vulnerability.
Apache Common Text versions 1.5 through 1.9 are impacted by this vulnerability and have been patched with Apache Commons Text version 1.10 and above.
About Apache Common Text
Apache Commons Text is a widely popular low-level library for performing various text operations, such as escaping, calculating string differences, and substituting placeholders in the text with values looked up through interpolators. When using the string substitution feature, some of the available interpolators can trigger network access or code execution. This is intended, but it also means an application that includes user input in the string passed to the substitution without properly sanitizing it would allow an attacker to trigger those interpolators.
Potential Impact of Text4Shell Vulnerability
Successful exploitation of this vulnerability allows an unauthenticated attacker to execute arbitrary code on the vulnerable asset. PoC exploits for this vulnerability are already available in the public domain.
Qualys QID Coverage
Qualys is releasing the QIDs in the table below as they become available, starting with vulnsigs version VULNSIGS-2_5_617 and in Linux Cloud Agent manifest version LX_MANIFEST-2.5.617.2-1
| QID | Title | Supported On |
|---|---|---|
| QID 377639 | Apache Commons Arbitrary Code Execution (ACE) Vulnerability (Text4Shell) (CVE-2022-42889) | Scanner + Agent + CS Sensor |
| QID 988179 | Java (Maven) Security Update for org.apache.commons:commons-text (GHSA-599f-7c49-w659) | CS Sensor |
| QID 377701 | Apache Commons Arbitrary Code Execution (ACE) Vulnerability (Text4Shell) (CVE-2022-42889) Scan Utility | Scanner + Agent |
Please check Qualys Vulnerability Knowledgebase for the full list of coverage for Text4Shell vulnerability.
The following guides Qualys customers on how to detect, track and report on Text4Shell in their environment.
Discover Vulnerable Assets Using Qualys CyberSecurity Asset Management (CSAM)
Identify Assets with Apache Commons Text or Apache Maven Installed
The first step in managing this critical vulnerability and reducing risk is the identification of all assets with Apache Common Text. Qualys CyberSecurity Asset Management (CSAM) makes it easy to identify such assets.
software:(name:Apache Commons) or software:(name:Apache Maven)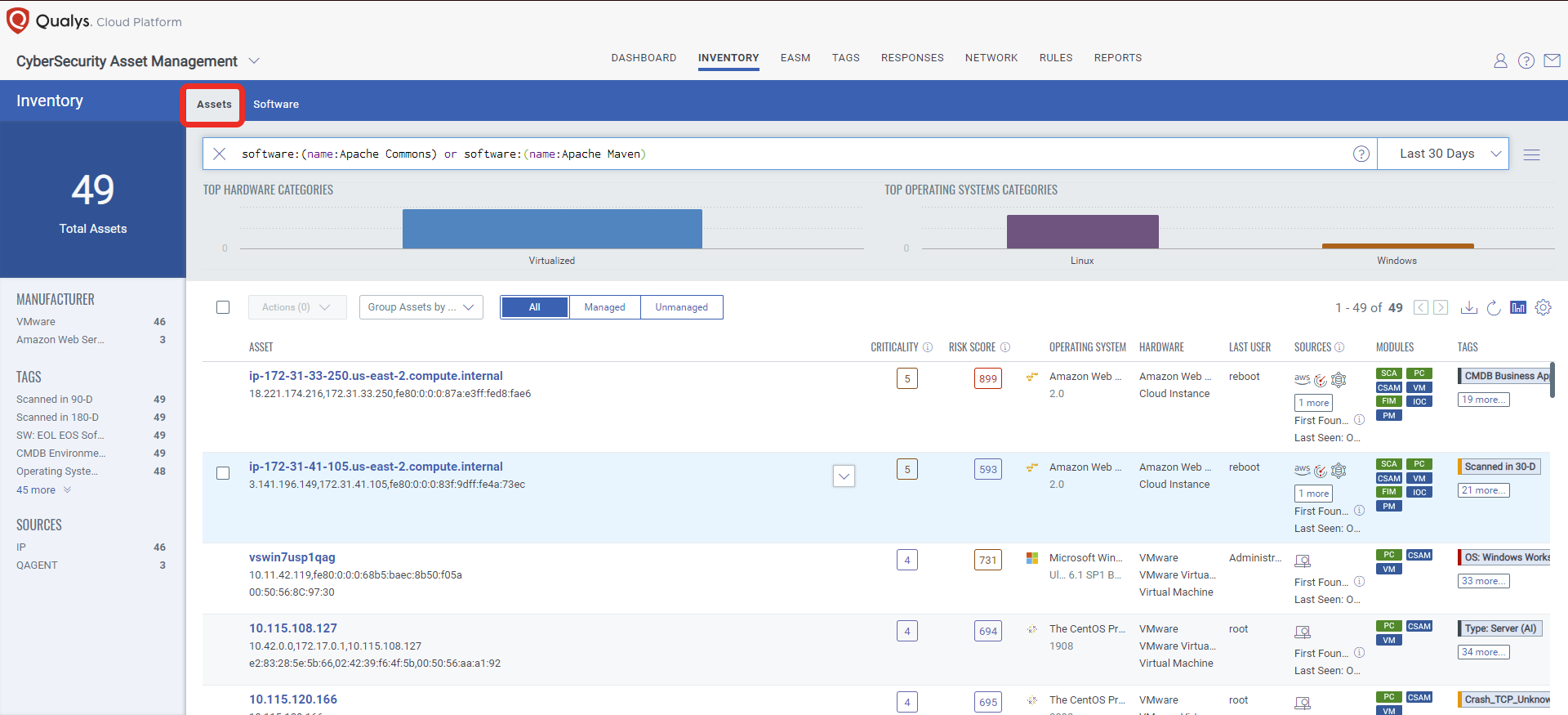
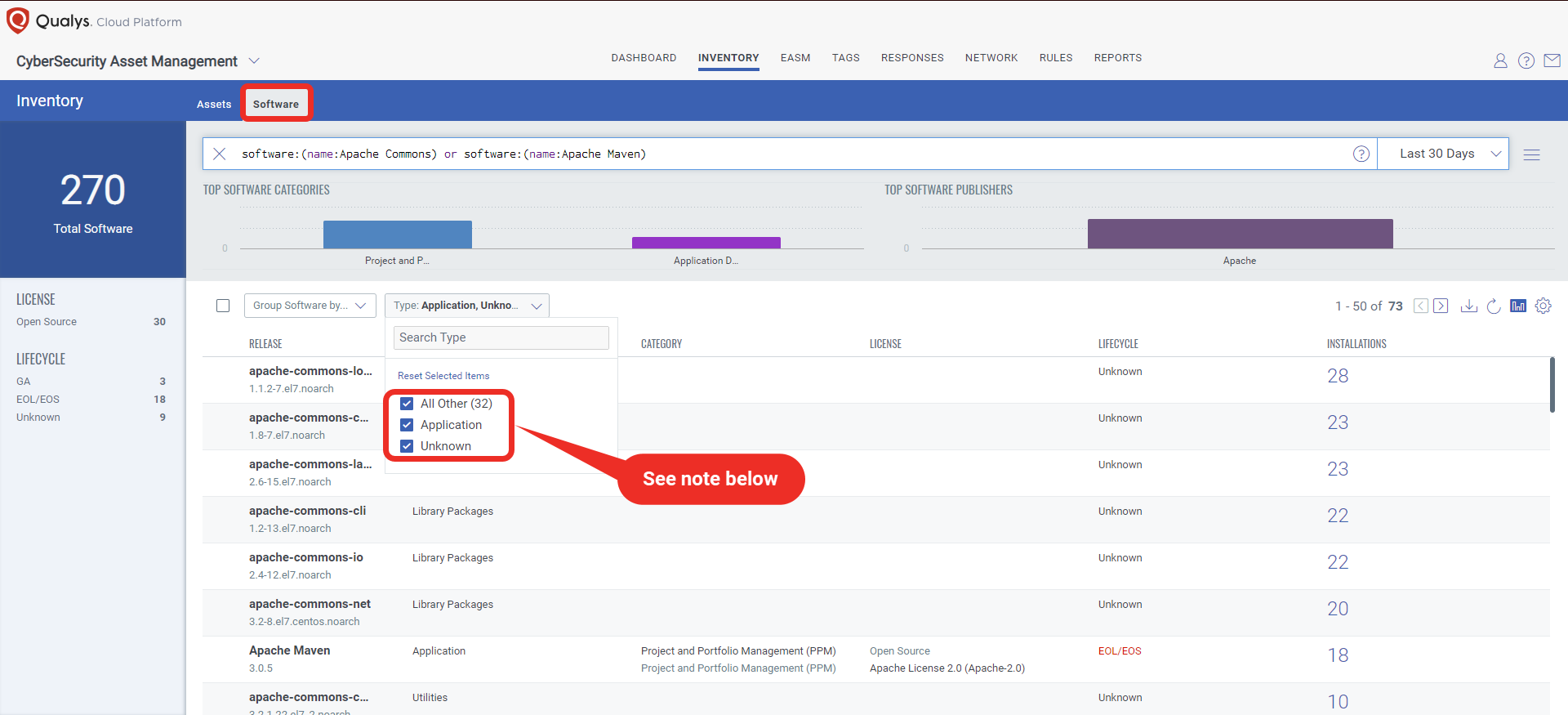
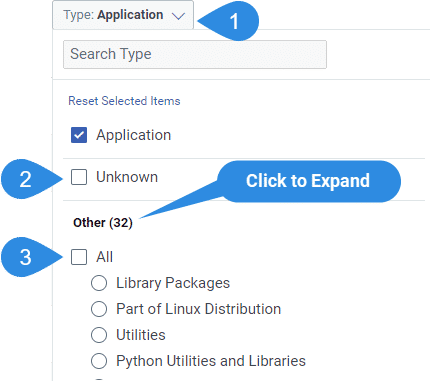
Note: Make sure you have selected Applications, Unknown, and All Other in the “Type” filter.
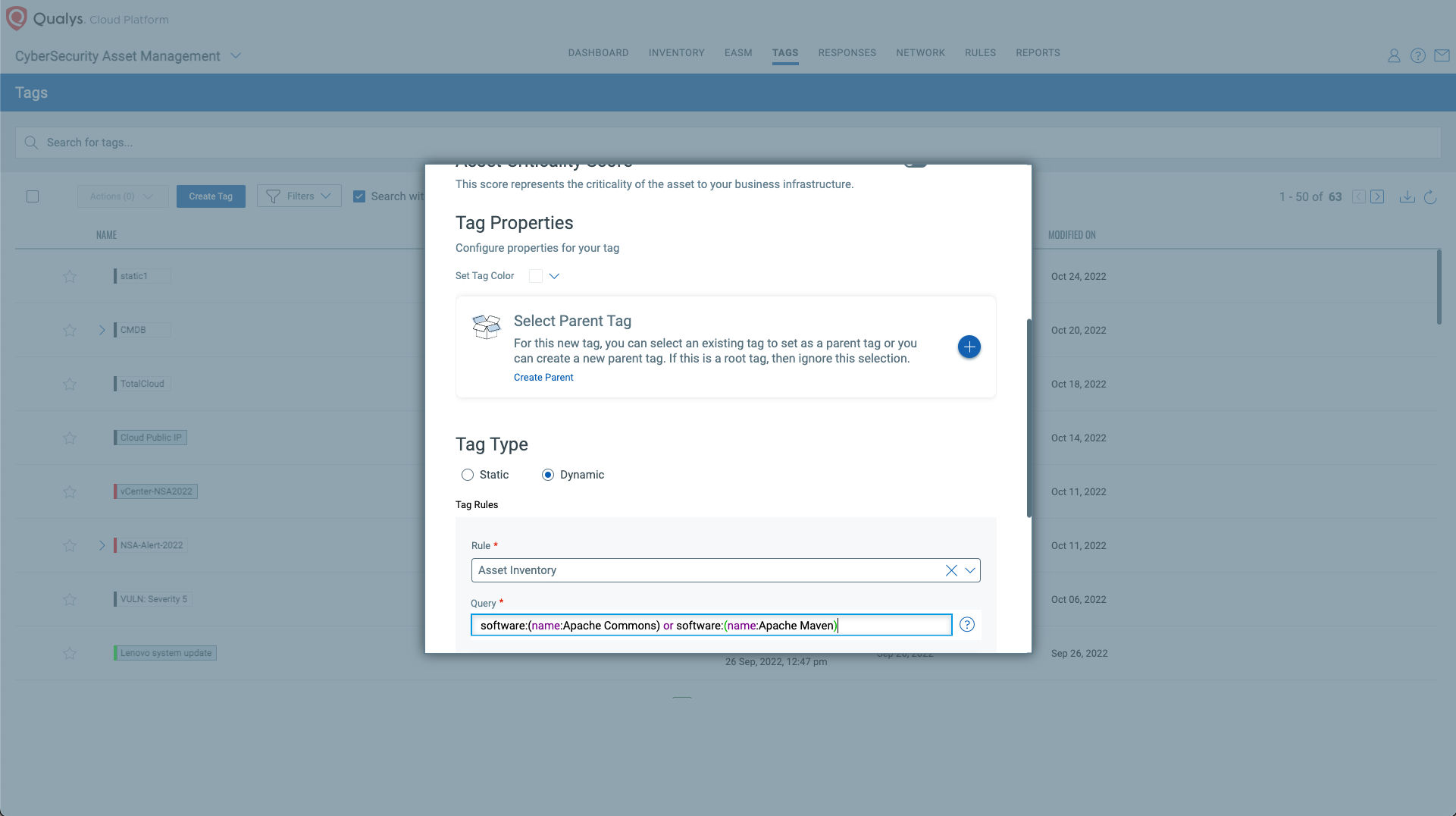
Tagging Vulnerable Assets Using Qualys CyberSecurity Asset Management (CSAM)
Once the hosts are identified, they can be grouped together with a ‘dynamic tag’; let’s say: “Apache Common Text Assets”. This helps by automatically grouping existing hosts with the above vulnerabilities as well as any new assets that spin up in your environment. Tagging makes these grouped assets available for querying, reporting, and management throughout the Qualys Cloud Platform applications.
Discover Vulnerable Assets Using Qualys Vulnerability Management Detection and Response (VMDR)
Qualys provides coverage and visibility for Text4Shell by enabling organizations to quickly respond, prioritize and reduce the risk from these vulnerabilities.
Using Qualys Vulnerability Management Detection and Response (VMDR) with TruRisk the Qualys Query Language (QQL) lets you easily search and prioritize all your assets that are vulnerable to Text4Shell.
Use this QQL statement:
vulnerabilities.vulnerability.cveIDs:`CVE-2022-42889`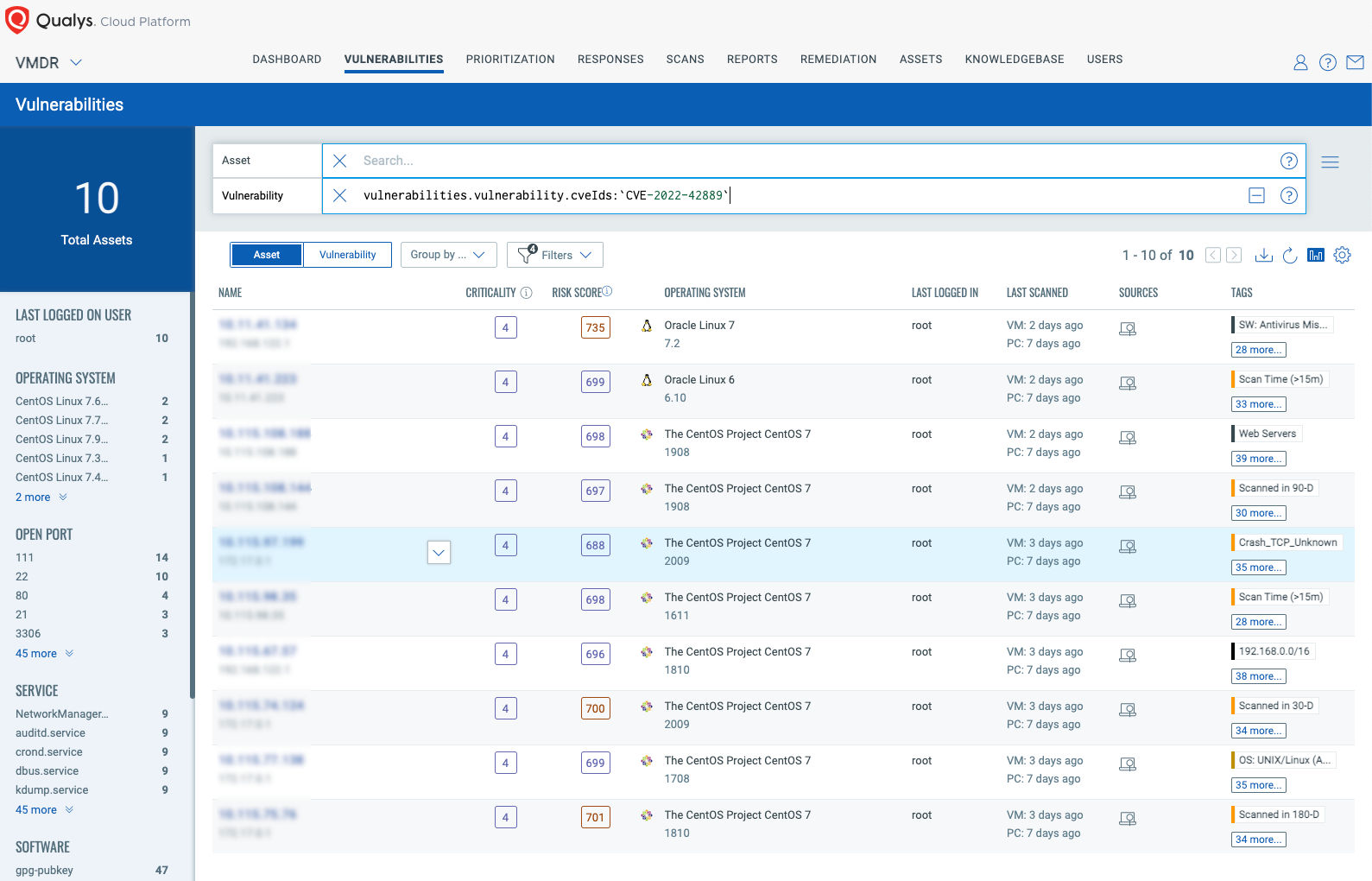
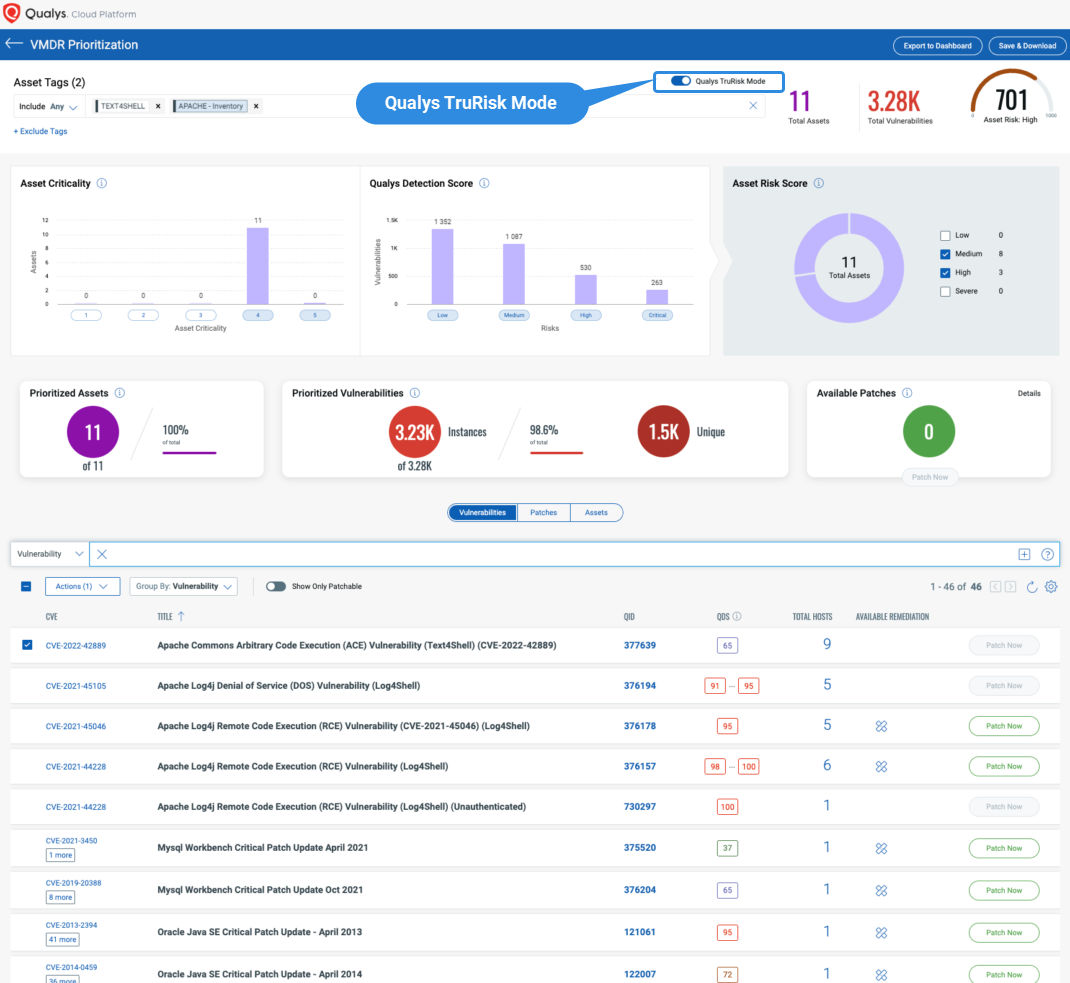
Prioritize Text4Shell easily with Qualys VMDR TruRisk Mode!
Qualys TruRisk VMDR Prioritization makes it easy to prioritize all your Text4Shell vulnerabilities and other vulns on the same assets which increases the TruRisk of the asset. To do so, apply the tag which has the inventory of assets with exposure to Apache Commons and enable/toggle Qualys TruRisk Mode then select prioritize.
Leveraging Qualys’ Software Composition Analysis (SCA) Capabilities for Container Security
 Qualys Blog | CVE-2022-42889: Detect Text4Shell via Qualys Container Security
Qualys Blog | CVE-2022-42889: Detect Text4Shell via Qualys Container Security
Open-source libraries and packages are notoriously difficult to inventory and report on leaving a large hole in an organization’s security posture and open to risk due to the use of OSS packages in their organization.
With Qualys’ Software Composition Analysis capabilities for Container Security, you will gain insight into vulnerabilities in your container images, not just for the OS and third-party vulnerabilities but also for any open-source software libraries and packages used by your custom applications.
Qualys Container Security customers can leverage Qualys QID: 988179 specifically built on the SCA capability to identify vulnerable Text4Shell images.
To see all the images impacted by these vulnerabilities, navigate to the Container Security application, go to Assets > Images, and search using the following QQL query:
vulnerabilities.qid: `988179`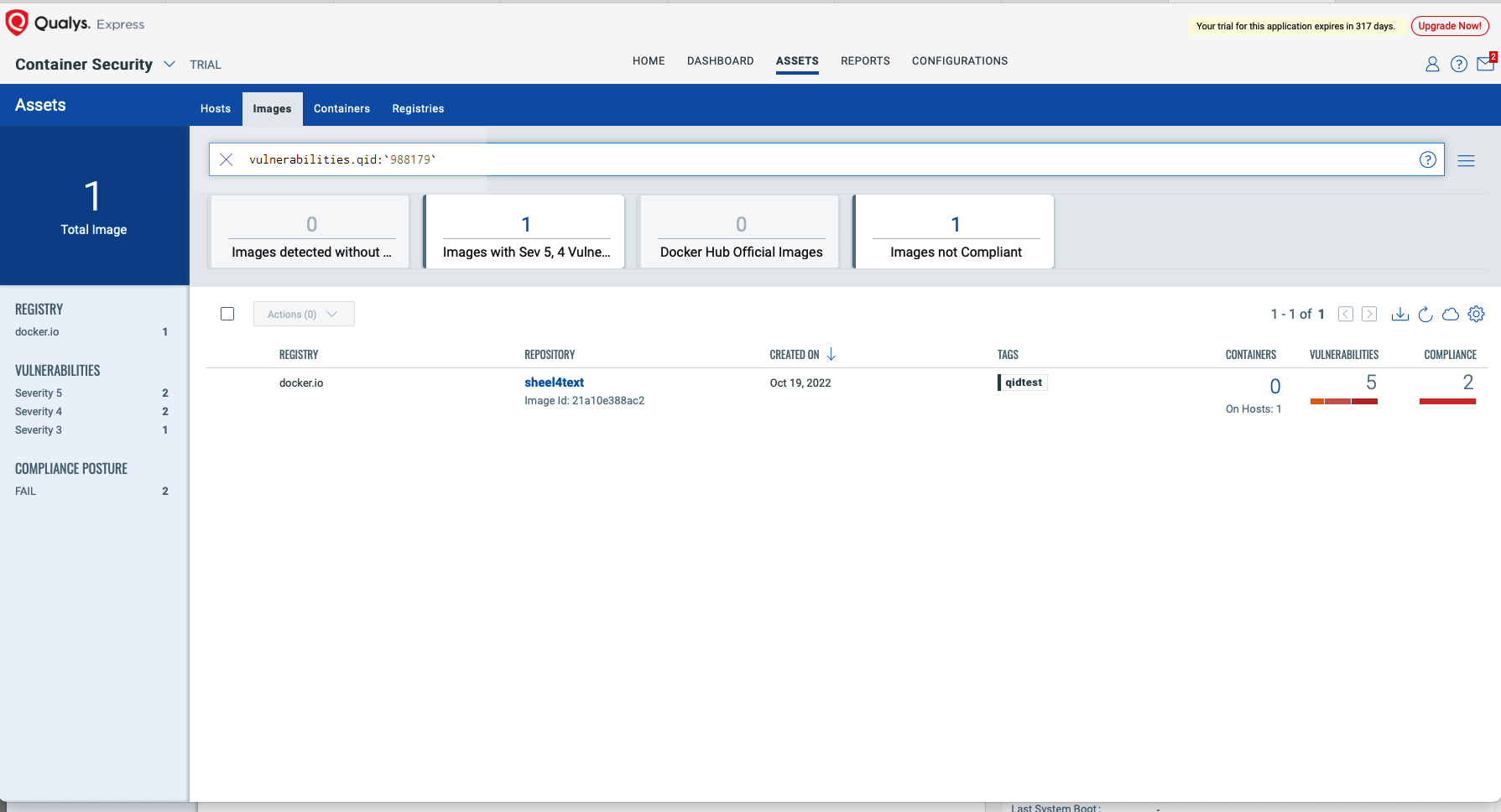
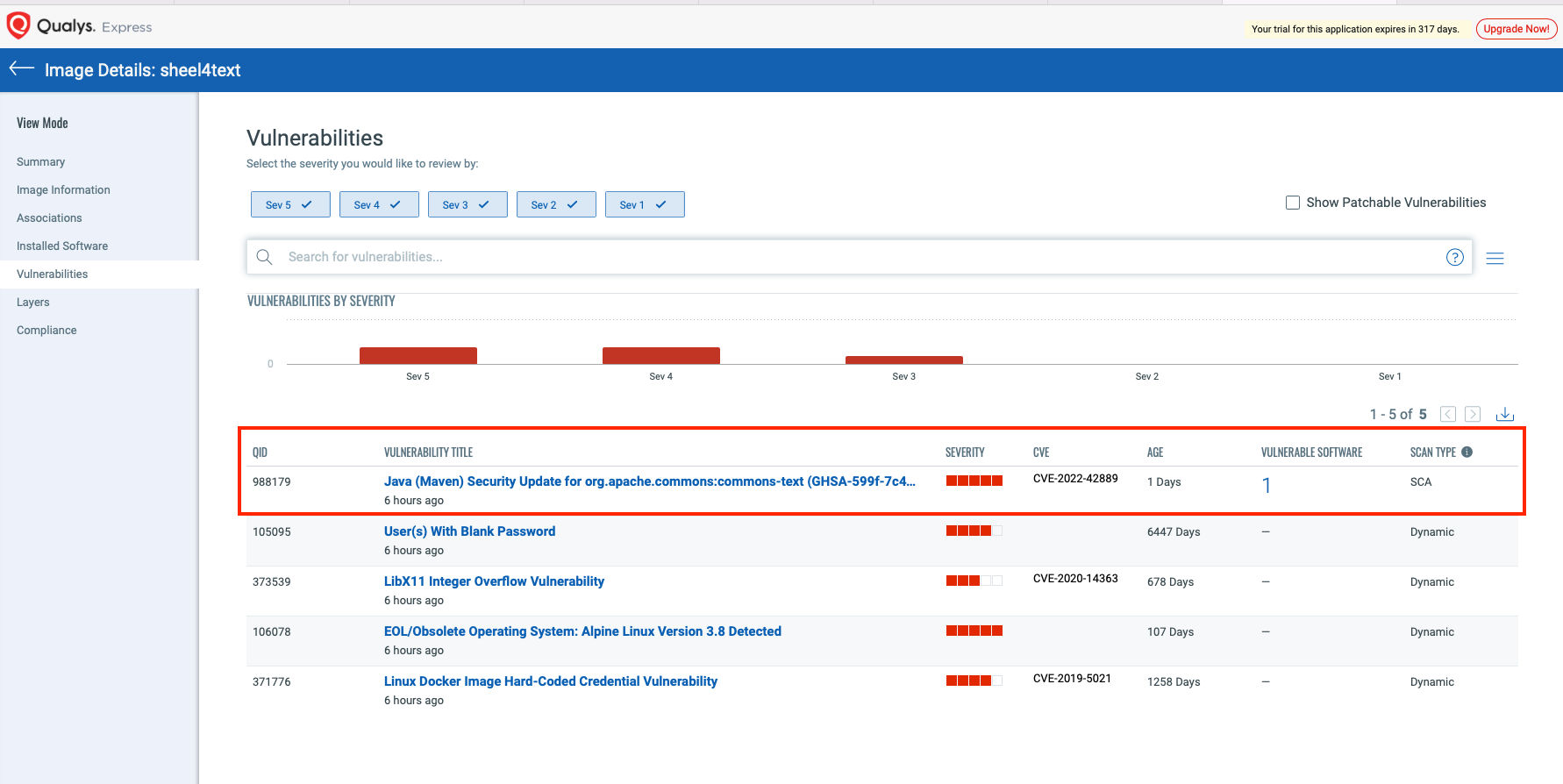
Select the image and navigate to the Vulnerabilities tab to view details of the vulnerability.
Windows Out-of-Band Detection for Text4Shell
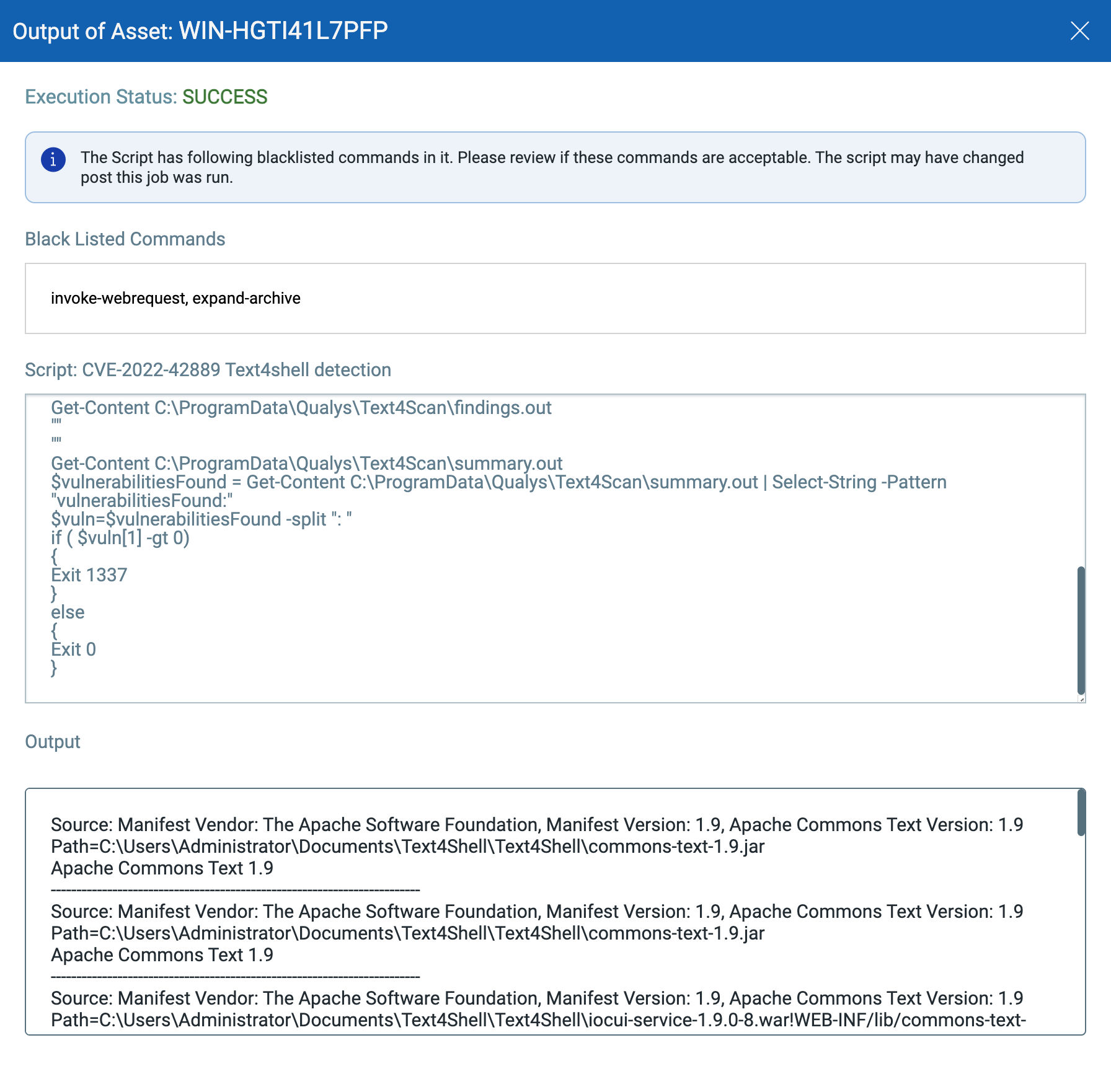
To help our customers, the Qualys team has created an out-of-band utility for Windows which performs a “deep” file scan to find all instances of vulnerable Apache Commons Text libraries.
The benefit of such a tool is that it should find all vulnerable instances regardless of the Java application coding, packaging, and deployment method used as it will scan the entire hard drive(s) including archives (and nested JARs) for the Java libraries, the utility will output its results to a console and to "%ProgramData%\Qualys\Text4Scan\findings.out".%
The disadvantage is that this tool performs a “deep” search on the entire hard drive, including archives, which is a time-consuming and CPU-consuming task. As such, we recommend running this tool “out-of-band”.
QID 377701: Apache Commons Arbitrary Code Execution (ACE) Vulnerability (Text4Shell) (CVE-2022-42889) Scan Utility will be flagged based on the output of the utility (“%ProgramData%\Qualys\Text4Scan\findings.out”.%).
Execute the Detection Utility with Qualys Custom Assessment and Remediation (CAR)
Time is a critical factor in such zero-day situations. Any delays in detection and remediation leave organizations vulnerable to security risks. Qualys Custom Assessment and Remediation (CAR) allows security practitioners to quickly create and execute custom scripts to collect data and initiate response actions on endpoints. This can reduce the organization’s mean time to remediation (MTTR) to zero-day attacks and other threats by 50% or more.
Qualys CAR customers can execute the Out-of-Band Detection utility for Text4Shell on required assets/asset tags.
The PowerShell script to execute this utility can be found under Script Library on GitHub – CVE-2022-42889 (Text4Shell)
IMPORTANT: Scripts tend to change over time. Please refer to the Qualys GitHub Zero Day link to ensure the most current version of a given CVE-2022-42889(Text4shell) is in use.
Please refer to the script output in Qualys CAR:
Free Trial
Get started with 30-day Free Trial
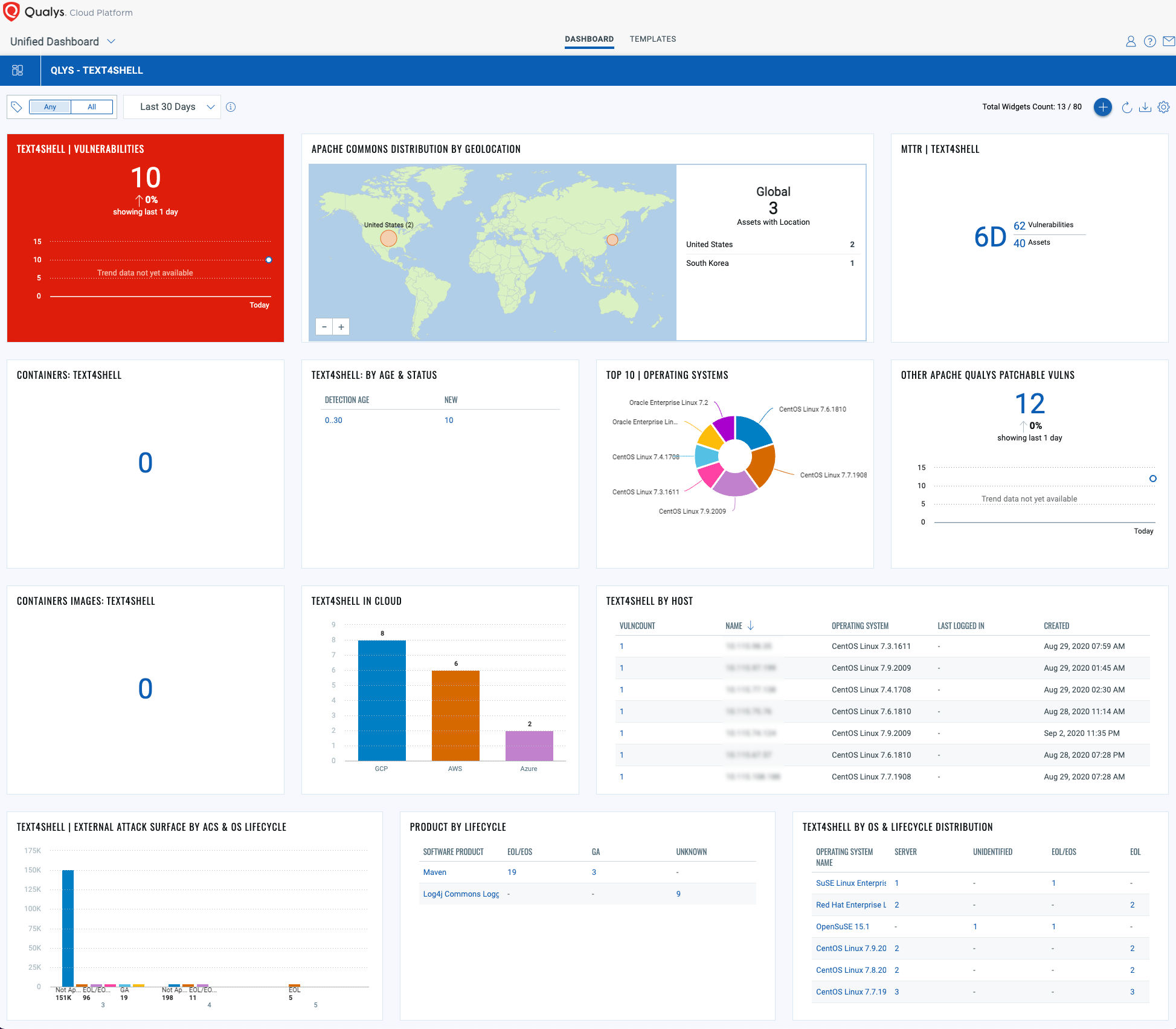
Gain exposure visibility and remediation tracking with “Text4Shell” Unified Dashboard
With the Qualys Unified Dashboard, you can track the vulnerability exposure within your organization and view your impacted hosts, their status, distribution across environments, and overall management in real-time, allowing you to see your mean time to remediation (MTTR).
View and download the “Text4Shell” dashboard
Contributors:
- Felix Jimenez, Director, Product Management, Qualys
- Himanshu Kathpal, Director, Product Management, Qualys
- Saeed Abbasi, Manager, Vulnerability Signatures, Qualys
- Pablo Quiroga, Director of Product Management, Qualys
- Mohd. Anas Khan, Compliance Research Analyst, Qualys
- Mukesh Choudhary, Compliance Research Analyst, Qualys
- Lavish Jhamb, Solution Architect, Compliance Solutions, Qualys