Cyber Criminals using Coronavirus Fears to Spread Information-Stealing Malware
Last updated on: September 6, 2020
Cyber criminals have been leveraging trending cultural and viral news items that drive interest from millions of individuals as mechanisms to target and distribute malware easily and effectively. In the past, cyber criminals have used topics including international sports championships, celebrity divorces, and political elections to spread their malware.
The Coronavirus (COVID-19) pandemic is the latest vehicle for these types of attacks. The conditions of this pandemic are ripe for wide-scale malware distribution: large geographic base affecting both businesses and consumers, fear and uncertainty on the impact of the virus, and the increased use of social media and person-to-person electronic communications to spread news, information, and opinions.
Last week, a new malware attack focused on these effects. A cyber criminal group created a fake Corona Map application for Windows embedded with information stealing malware that once downloaded and installed by the user starts collecting and sending sensitive data like passwords, credit card numbers, bank accounts, and other sensitive data.
This attack, first described by researchers at Reason Labs, leverages a variant of the Azorult malware family repurposed to be embedded and run within this Corona Map application. If this campaign becomes successful, we can expect more variants of this malware and other delivery methods beyond a fake Corona Map application.
Limitations with Single-Detection Anti-Virus Engines for Security Analysts
As of this writing, VirusTotal shows that many anti-virus engines (58 out of 70) have detections for this fake Corona Map malware. That’s the good news that most commercial products will catch this, if the anti-virus is properly installed, running, and configured on each endpoint.
What’s challenging for single-detection anti-virus engines, however, is that many of them have limited analysis of the actual threat itself which doesn’t provide enough actionable information to security analysts to show if Corona Map has truly infected their network, especially if malware authors change the name of the infected file to evade detection.
From the same VirusTotal detection list, some vendors that can detect the Corona Map malware don’t list the malware family name. Their detections describe the threat in the most generic terms, including “Unsafe”, “Win/malicious_confidence_100% (W)”, “Malicious”, “Heuristic”, or “Generic.ml”. (See: https://www.virustotal.com/gui/file/2b35aa9c70ef66197abfb9bc409952897f9f70818633ab43da85b3825b256307/detection)
In addition to not describing this specific threat – which makes it hard for security analysts and incident responders to fully determine if they have been compromised – it may be impossible to differentiate this password and data stealing Corona Map malware attack from other less risky potentially unwanted applications and programs like coupon tool bars. Security analysts’ time is precious; they need to focus on the real threats in their environment first.
Visibility Beyond Anti-Virus and Malware Family Detection
Qualys Indication of Compromise (IOC) takes a malware family detection approach to Endpoint Detection and Response (EDR) based on threat intelligence to classify malware into threats families and threat categories that provides richer context for security analysts and incident responders.
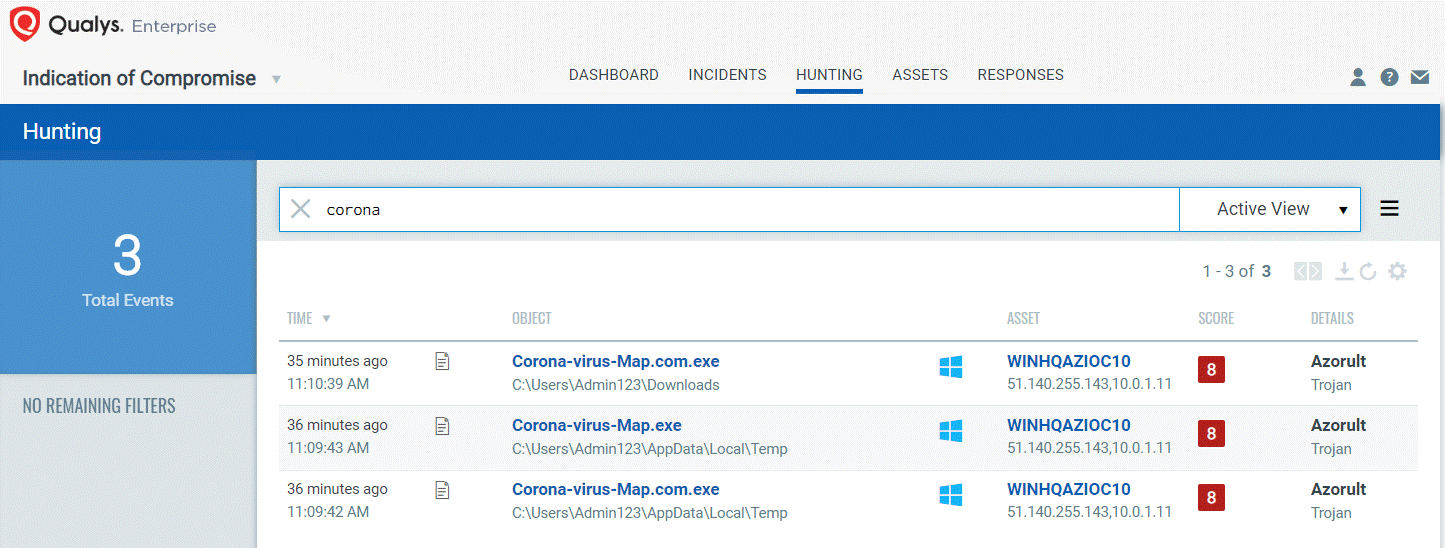
For this same fake Corona Map malware, Qualys IOC detects and scores the malware as “Malicious” (score of 8 denotes a file event, but not running as a process or with any network connections) and provides the malware family name (“Azorult”) and malware category (“Trojan”). This enables security analysts to quickly identify any systems infected with Azorult and automatically alert if there are any trojan malware running in the network.
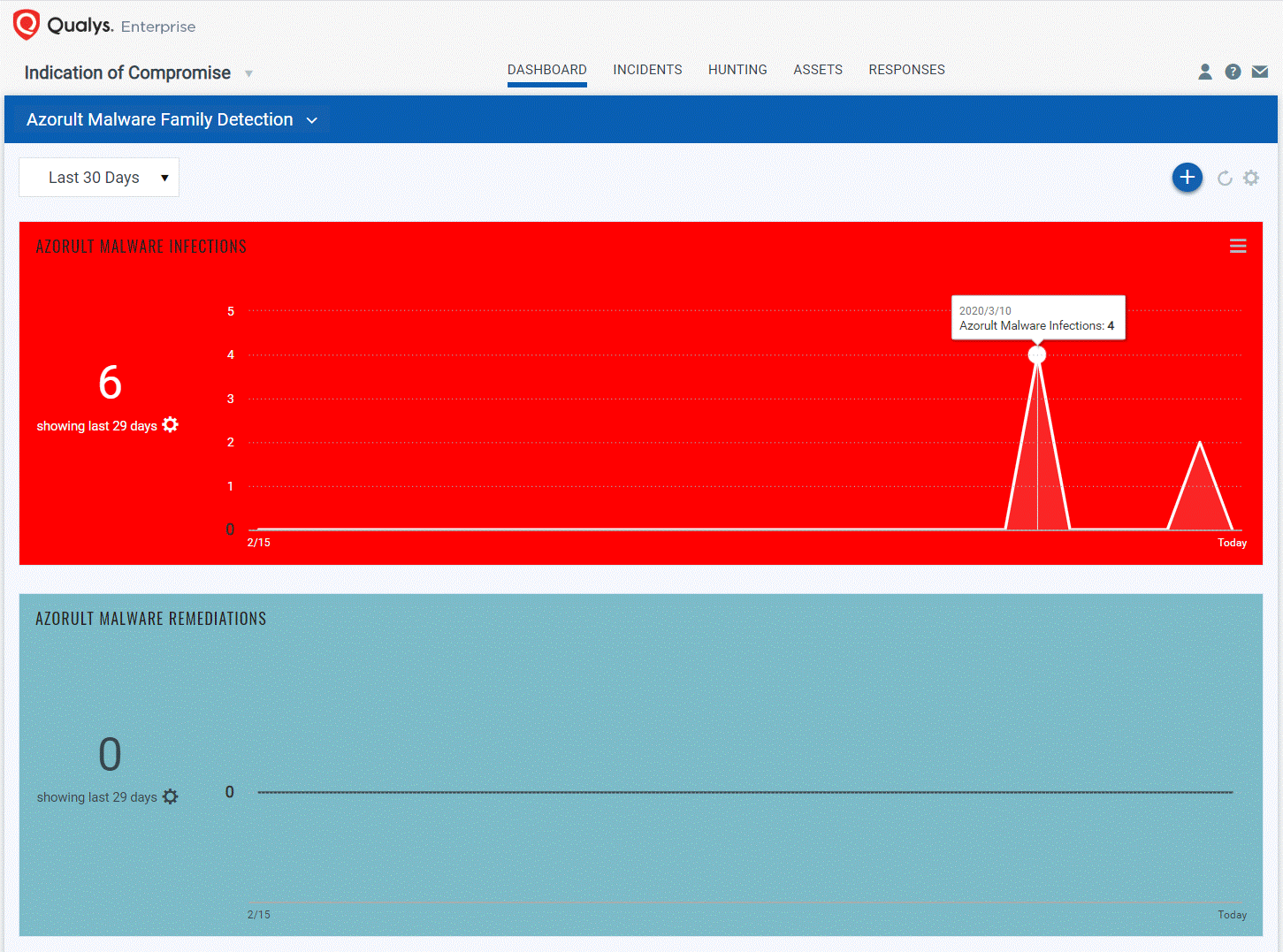
Using dynamic dashboards and widgets available for all Qualys apps, you can easily create trending widgets to track any Azorult infections in your network – regardless of variant or hash – and compare against active remediation efforts. The screen shot below shows active Azorult infections but no remediations. In this case, security analysts should prioritize response efforts to contain and remove all traces of the Azorult malware family.
Qualys Cloud Platform
Qualys Cloud Platform gives you a continuous, always-on assessment of your global security and compliance posture, with 2-second visibility across all your IT assets, wherever they reside. Easily deployable, centrally managed and self-updating, Qualys sensors come as physical or virtual appliances, or lightweight agents for user endpoints, on-premises servers and cloud instances. Nothing to install or manage, all services are accessible on the cloud via web interface.
Request a free trial of Qualys IOC and any Qualys cloud app.