Defense for the 0-Day in IE8
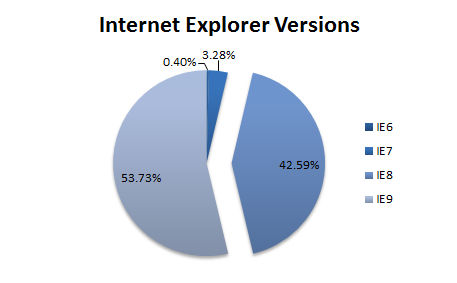
Microsoft is currently dealing with an exploit (KB2847140) for a 0-day vulnerability in Internet Explorer (IE). Machines attacked by this exploit will yield full control to the attacker and allow him to install more advanced malware such as the well known RAT Poison Ivy. The exploit was first discovered last Wednesday on a website of the Department of Labor specialized in nuclear technology. It has since spread to other websites and is now also available in Metasploit. The exploit works only against IE version 8 (IE8), which limits the exposure to about 42% of all systems, according to last count from our BrowserCheck service.
IE8 is the latest version available on Windows XP, and was also the original version installed on Windows 7. This explains the rather high numbers that we are seeing for this older browser. Windows 7 users have access to IE9, which is not affected by this attack and has a much better security architecture. Upgrading to IE9 is a straightforward way to defend against the attack.
Mitigation with EMET
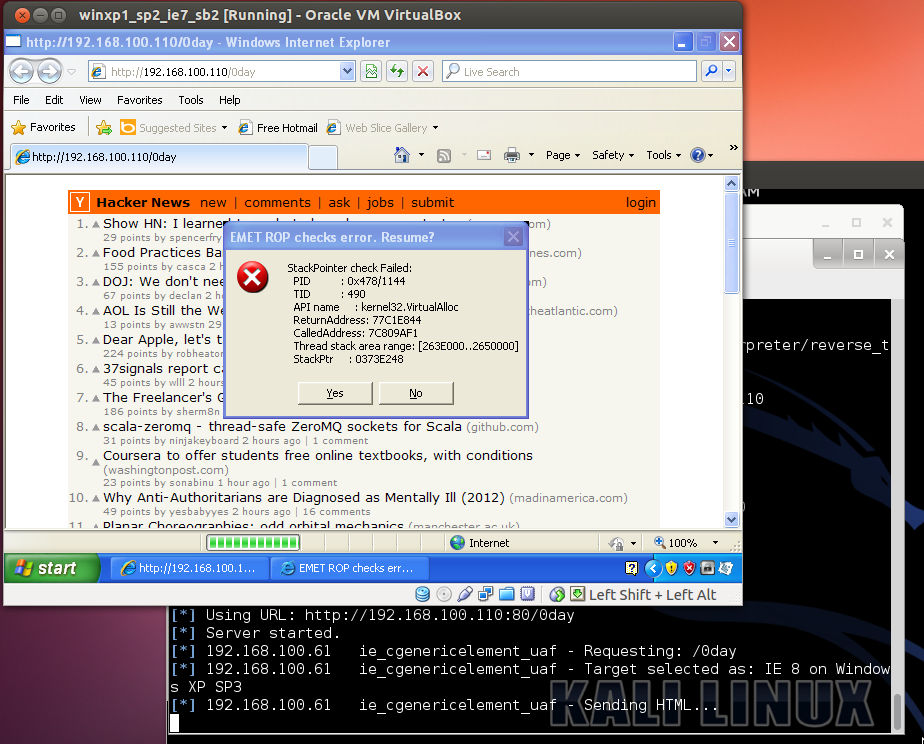
Microsoft’s Enhanced Mitigation Experience Toolkit (EMET) is a free toolkit that oversees the Windows processes and applies a number of mitigation techniques to detect attack against memory corruption vulnerabilities. The latest version is 4.0 and brings a number of new management features, including an audit mode and more granular protection settings. We ran EMET through it paces with the Metasploit module for CVE-2013-1347, and it indeed catches the exploit before it can install the RAT program.
EMET is an effective way to harden your installation against new threats such as 0-days targeted at browsers. It has prevented past attacks such as against the IE January 0-day, patched as MS13-008. I have run EMET on my laptop for the last year without any negative impact or false positives, and I have heard of a number of organizations are evaluating its use on all workstations that have Internet access. We recommend it as a tool to include in your base OS builds.
Microsoft will no doubt address this flaw, either next week at Patch Tuesday or soon after, if their testing can’t be finished in time. You should apply the patch for it as soon as possible, but the additional protection that EMET can bring against these rather frequent 0-days (MS13-008, MS13-021) is definitely worth evaluating.