Patch Tuesday February 2016
We are back to normal numbers on Patch Tuesday. After a light start with nine bulletins in January we are getting 12 bulletins (five critical) in February, which is in line with the average count for last year: 12.25/month:
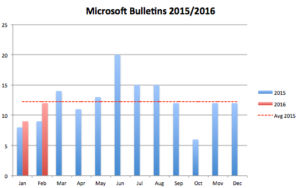
Actually it is 13, but the last one this month, MS16-022, is more of a packaging change. It concerns Adobe Flash, a software package where updating has already been handled by Microsoft for the last 3 ½ years in the Internet Explorer 10 and 11 browsers. In the past this update was tracked under the single under the security advisory KB2755801. Now there is a real bulletin for it. At the very least the new format provides better handling and tracking. None of the vulnerabilities described is in the use in the wild, but many are rated as easily exploitable by both Microsoft and Adobe, so you should address them quickly.
MS16-022 leads our priority list at Qualys for this month. The update for Adobe Flash (APSB16-04) contains fixes for 22 vulnerabilities, all of them rated as “critical”, i.e. capable of handing the attacker complete control over the target machine. Attack scenarios vary from compromised, but otherwise innocent websites (look at some of the recent WordPress issues for example) that link to malicious attacker controlled domains to Flash embedded in other files such as Office documents, which targets access through e-mail. In addition attackers have shown last year that they invest into Flash based attacks, so this bulletin is on our top spot.
MS16-015 is the second ranked bulletin in our list. It addresses seven vulnerabilities in Microsoft Office in Word, Excel and Sharepoint. The Word vulnerabilities CVE-2016-0022, CVE-2016-0052 and CVE-2016-0053 are all RTF file format vulnerabilities and can be triggered without user interaction through the preview pane in Outlook and are rated as “critical”. I am surprised that Microsoft does not offer mitigating factors here, but I believe that the configuration changes in MS14-017 continue to be valid:
- Read e-mail in plain text in Outlook
- Disable RTF files in Microsoft Word through the File Block Policy
The next vulnerabilities on our list are MS16-009 for Internet Explorer and MS16-011 for Microsoft Edge. They address 13 and 6 vulnerabilities respectively, with 7 and 4 rated on the critical level. Exploitation of these vulnerabilities would be through the web browsing, leading to the access of malicious websites either directly, or through search engine poisoning attracting your user to the specifically prepared website, or through the compromise of an otherwise legitimate site or even by inclusion in an advertising network. This attack vector is one of the largest in your organization and we recommend patching these vulnerabilities as quickly as possible.
Last month Microsoft stopped supporting the legacy Internet Explorer browsers on each of their operating system limiting updates to the latest browsers on each platform. The exact rules are laid out in Microsoft’s Lifecycle document, but for most end-points (Windows 7,8.1 and 10) that means Internet Explorer 11. Everything else is unsupported and you are exposing your users to an attack vector that will be difficult to contain as more time goes by.
The next critical bulletin MS16-013 is for Microsoft Journal. A malicious file with extension .JNL needs to be opened by the user to trigger the vulnerability. Under Windows 7, one can disassociate the file extension from the application and neuter the attack. This makes sense since there is a steady stream of patches in MS15-114, MS15-098 and MS15-045, etc. that could be downgraded if your users were prevented from opening these files.
The last critical bulletin is for Microsoft PDF Reader. PDF Reader is only available under Windows 8.1, 10 and Server 2012 and so MS16-012 only applicable the users that runs on the newer versions. This is a first patch for this software and it will be interesting to see how many more vulnerabilities security researchers can find. Remember in 2012 when Google used their fuzzing technology to look at Adobe Reader? Do you use the Windows PDF reader or have you standardized on Adobe Reader even on these platforms?
There are other interesting patches in today’s lineup, Windows itself gets patched in MS16-014 and MS16-018, MS16-016 addresses WebDAV escalation of privilege hole, if you expose RDP on the Internet, MS16-017 but the attacker needs to be authenticated already, MS16-020 closes a DoS gap in Active Directory and MS16-021 a similar hole in Radius.
As always an accurate directory of installed software will be helpful to decide where to act first. Automatic updates wherever possible, on generic end-users machines for example can also take away much of the burden of actively rolling out patches.
If you are going to come to RSA Conference in San Francisco, stop by at our booth. We will have plenty of new products to talk about, and I always enjoy meeting you in person.
Microsoft may have fixed 36 flaws but it seems to have screwed up far more PCs judging by the number of new threads in the Microsoft Community, including mine http://answers.microsoft.com/en-us/windows/forum/windows_10-update/todays-win10-updates-screwed-up-my-upgraded-from/45536902-c167-4fbb-b455-4a409878f789