New critical glibc vulnerability
Last updated on: September 6, 2020
Last week, Fermin Serna from Google posted a report of a critical vulnerability in the glibc library used in very fundamental level in almost all Linux systems. The vulnerability CVE-2015-7547 is in the getaddrinfo() function and can be used to gain Remote Code Execution.
A malicious DNS server provides an overlong, specially formatted answer to a normal address query, which overflows a statically allocated internal 2K buffer with data. The data is then executed within the getaddrinfo() function.
Google published a PoC to illustrate the problem and mentioned a couple of attack vectors – SSH which originally tipped them off for example, but made it clear that many other vector exist. This makes sense since almost all programs include glibc and many will end up using the getaddrinfo() function to resolve DNS names.
This is a critical vulnerability both on Linux servers and clients and you should patch as quickly as possible. Further work by security researchers during the last week has only increased the urgency:
- Dan Kaminsky blogged about the multiple attack vectors for the bug. He notes that compared to the GHOST vulnerability found last year by Qualys Vulnerability Research team CVE-2015-7547 is much more prevalent and thus attackable. With a single hour of setup he was able to crash a number of standard Linux applications such as apache, smbclient, gpg and mysql:
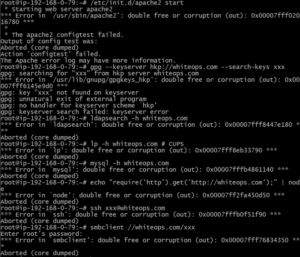
- Dan also pointed out that the one thing that is buying us time at the moment (direct access to the malicious DNS server required) might be going away any time soon, as he (and others for sure) are working on making the exploit capable of traversing the DNS cache server network, which would open a whole new set of machines to the attacks.
- Chris Rohlf of the security team at Yahoo indicated they have a working code execution against the Apache/PHP server:
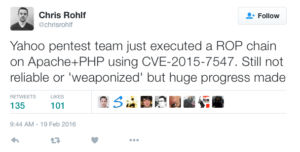
Anyway one looks at it: this is critical and will only get worse in the next couple of weeks. Patch the glibc library in use as soon as possible. The mitigations listed by Redhat in their article have the potential to interfere in normal DNS operations so they are only an option if you are certain of your DNS usage.
To track your patching progress frequent scans are crucial. Fast moving environments that make use of virtual machines in cloud environments such as Amazon EC2 should look at making use of our Cloud Agent. It provides vulnerability data automatically as soon new machines get booted up and keeps you on top of the changes happening.