2016 Year-End Summary for Adobe and Another 0-day Fix in December
Last updated on: September 6, 2020
Adobe released nine security bulletins today in the December Security updates. The most notable update was APSB16-39 for Flash which fixed a 0-day vulnerability with exploits in the wild that is being used in targeted attacks. Adobe products including Flash and Acrobat PDF reader have long being targeted by exploit kits. In addition to the 0-day (CVE-2016-7892), 17 other vulnerabilities were fixed in Flash. This update address critical vulnerabilities that could potentially allow an attacker to take control of the affected system. Other updates included in today’s release fixed Coldfusion (APSB16-44) , Robohelp (APSB16-46), Adobe Digital Editions (APSB16-45), InDesign (APSB16-43) , Experience Manager (APSB16-42) , DNG Converter (APSB16-41) and Animate (APSB16-38).
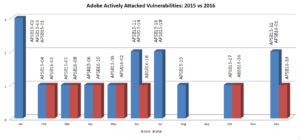
In 2016 Adobe vulnerabilities that are actively exploited in the wild reduced by half.
The graph below shows number of 2016 Adobe vulnerabilities that are being actively attacked and compares it to prior year. In 2015 there were 15 issues that were actively exploited while the number dropped to 7 in 2016. Attacks using CVE-2015-8651 were detected in 2015, and although the bulletin name indicates 2016 (APSB16-01), it was released as an emergency patch for December 2015.
In 2016 the time to patch Adobe Flash vulnerabilities was about 40% faster as compared to the previous year.
Adobe Flash has been the top target for Exploit Kits like Rig and Angler for a long time. The internet is rich with Flash content and all it takes is one click for a victim to get compromised and for attackers to take complete control of the victim machine. Out of more than 3 billion scans that Qualys performs each year we saw that in 2016 Adobe flash vulnerabilities were patched about 40% faster as compared to the prior year. This implies that the industry is doing a better job with patching Flash, and although Flash is not dead it is being fixed more quickly. To calculate this we measured the time it takes for each Flash vulnerability to relatively plateau, i.e. become flat in the graph or reach a state of little or no change. We call this the ‘plateau time’.
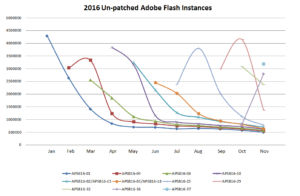
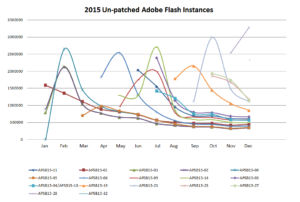
The two graphs above show aggregate number of times a Flash vulnerability was detected per month in 2016 and in 2015 respectively. Since most patches are released in the second week of each month and due to varying scanning cycles sometime there is a jump in the numbers for the second month – which is expected. In 2016 the plateau time or time to patch Adobe Flash vulnerabilities was about 40% faster as compared to the previous year. It hovers around 3 months which is still a bit slow in my opinion.