Microsoft Released Out-of-Band Advisory – Windows Adobe Type Manager Library Remote Code Execution Vulnerability (ADV200006)

Today, Microsoft released an out-of-band security advisory ADV200006 to address two critical remote code execution vulnerabilities in Adobe Type Manager Library. Microsoft is also aware of limited, targeted attacks that attempt to leverage this vulnerability.
The Vulnerability
Microsoft Windows Adobe Type Manager Library is affected by two remote code execution vulnerabilities as it improperly handles a specially-crafted multi-master font (Adobe Type 1 PostScript format). Successful exploitation would require a remote attacker to convince a user to open a specially crafted document leading to memory corruption and executing arbitrary code on the system. This may result in complete compromise of vulnerable system.
Affected Systems
All supported Windows and Windows Server operating systems are affected: Windows 7, 8.1, RT 8.1, 10, Windows Server 2008, 2008 R2, 2012, 2012 R2, 2016, 2019.
Detecting ADV200006 with Qualys Vulnerability Management
The best method for identifying vulnerable hosts that do not have workarounds in place, is through the Qualys Cloud Agent or via Qualys authenticated scanning. Qualys has issued QID 91617 for Qualys Vulnerability Management that is included in signature version VULNSIGS-2.4.849-4. Cloud Agents will automatically receive this new QID as part of manifest version 2.4.849.4-3.
QID 91617 : Microsoft Windows Adobe Type Manager Library Remote Code Execution Vulnerability (ADV200006) (Zero Day)
Update: 03/24/2020 : Microsoft revised MS advisory bulletin ADV200006 for Windows 10. QID 91617 detection logic has been updated and new changes are included in VULNSIGS-2.4.850-3 and later.
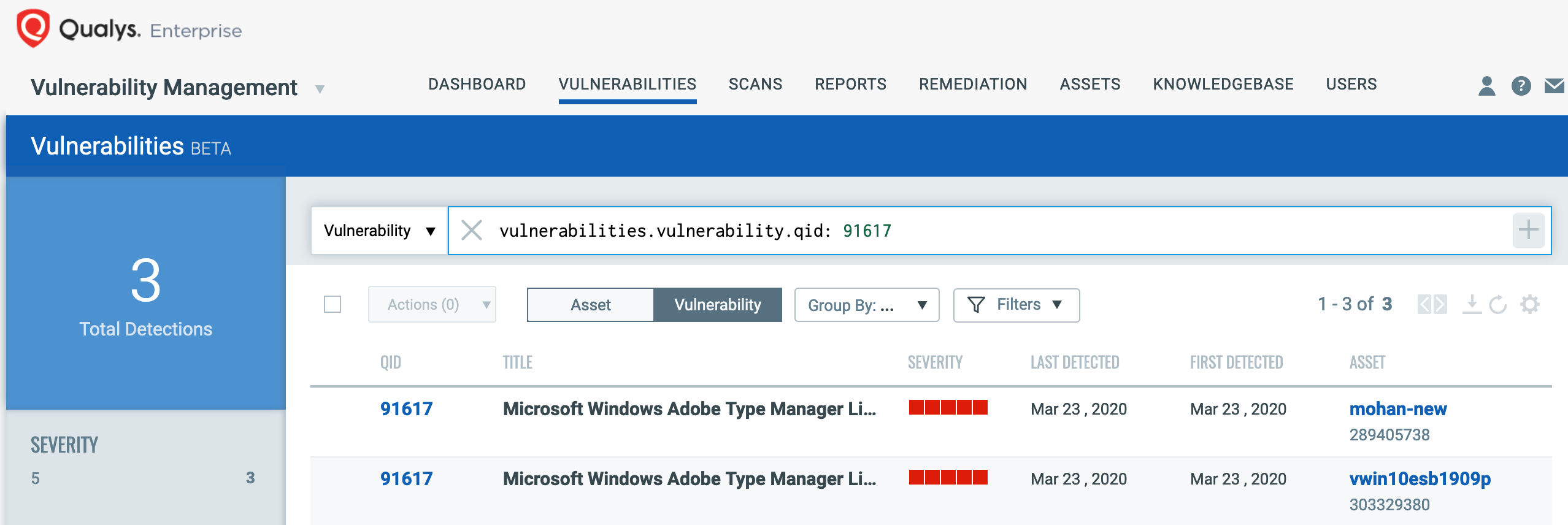
You can search for this within VM Dashboard by using the following QQL query:
vulnerabilities.vulnerability.qid: 91617
This will return a list of all impacted hosts.
Detection Dashboard
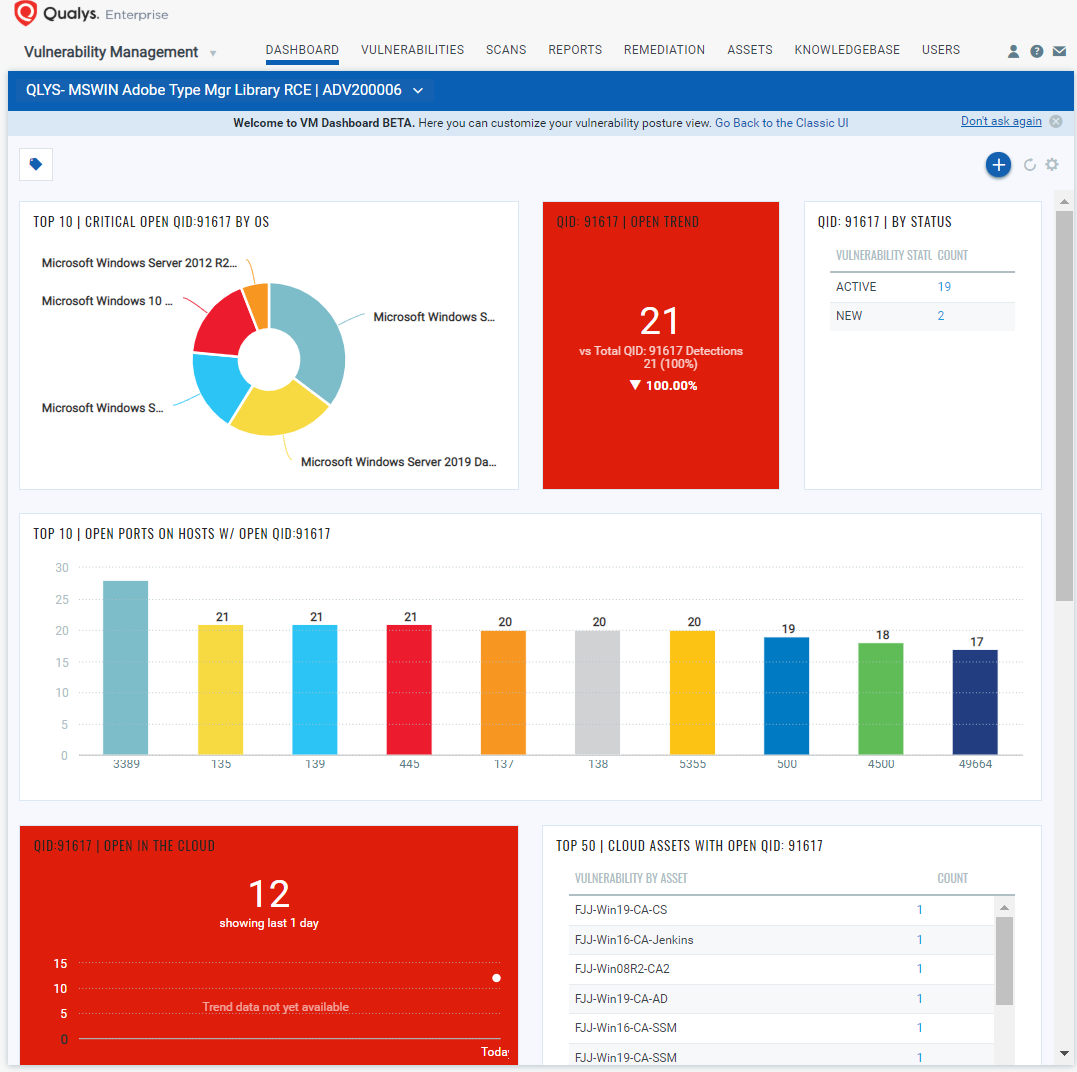
You can also track all hosts impacted by ADV200006 vulnerability in your environment with the Microsoft Adobe Type Manager Library RCE Vulnerability Dashboard that leverages data in your Qualys Vulnerability Management subscription, as shown below:
Qualys Threat Protection
Qualys customers can locate vulnerable hosts through Qualys Threat Protection. This helps accelerate identification and tracking of this vulnerability.
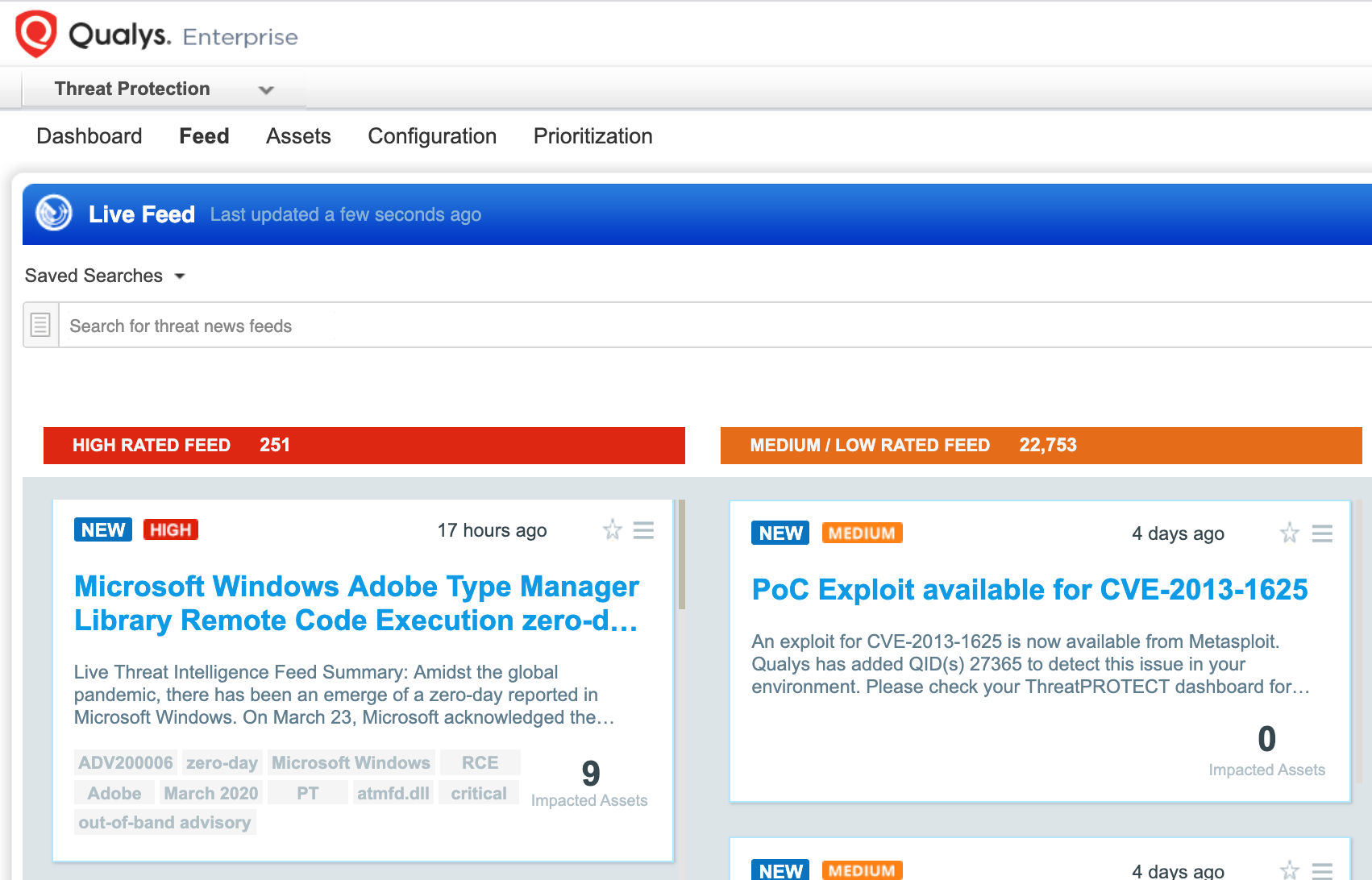
Simply click on the impacted assets number to see a list of hosts with this vulnerability.
Workaround:
While patches are not available yet, Microsoft provided workarounds to secure vulnerable systems:
- Disable the Preview Pane and Details Pane in Windows Explorer (WE)
- Disable the WebClient service
- Rename ATMFD.DLL or disable the registry key for Windows 8.1 and below
The first two workarounds provide less security against the vulnerability, as the attack could still be conducted with permissible conditions. In the first case, a local, authenticated user can still exploit this vulnerability from running a specially crafted program. In the second case also, it is still possible for remote attackers to run programs located on the targeted user’s computer or the LAN. However, users will be prompted for confirmation before opening arbitrary programs from the Internet.
When applying the third workaround, Microsoft says Disabling registry key may cause certain applications to stop working properly as OpenType fonts is not Windows native application and is installed via third-party applications.
Disable the Preview Pane and Details Pane in Windows Explorer(WE)
Open WE, click Organize, and then click Layout.
- Clear both the Details pane and Preview pane menu options.
- Click Organize, and then click Folder and search options.
- Click the View tab.
- Under Advanced settings, check the Always show icons, never thumbnails box.
- Close all open instances of WE for the change to take effect.
Disable the WebClient service
Disabling the WebClient service helps protect affected systems from attempts to exploit this vulnerability by blocking the most likely remote attack vector through the WebDAV client service.It is still possible for remote attackers who successfully exploit this vulnerability to cause the system to run programs located on the targeted user’s computer or the LAN, but users will be prompted for confirmation.
To disable the WebClient Service, perform the following steps:
- Click Start, click Run, type Services.msc and click OK.
- Right-click WebClient service and select Properties.
- Change the Startup type to Disabled. If the service is running, click Stop.
- Click OK and exit the management application.
Rename ATMFD.DLL:
- Enter the following commands at an administrative command prompt:
- cd “%windir%\system32”
- takeown.exe /f atmfd.dll
- icacls.exe atmfd.dll /save atmfd.dll.acl
- icacls.exe atmfd.dll /grant Administrators:(F)
- rename atmfd.dll x-atmfd.dll
- Restart the system.
Optional procedure for Windows 8.1 operating systems and below (disable ATMFD):
- Method 1 (manual):
- Run regedit.exe as Administrator.
- In Reg Editor, navigate to the following sub key (or create it) and set its DWORD value to 1: HKLM\Software\Microsoft\Windows NT\CurrentVersion\Windows\DisableATMFD, DWORD = 1
- Close Registry Editor and restart the system.
- Method 2 (using a script):
- Create a text file named ATMFD-disable.reg that contains the following text:
Windows Registry Editor Version 5.00
[HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows]
“DisableATMFD”=dword:00000001 - Run regedit.exe.
- In Registry Editor, click the File menu and then click Import.
- Navigate to and select the ATMFD-disable.reg file that you created in the first step.
- Click Open and then click OK to close Registry Editor.
- Create a text file named ATMFD-disable.reg that contains the following text:
Customers are advised to apply workarounds ADV200006 for affected operating systems until a patch is released to be protected from this vulnerability.
Hi Animesh, Since you published this MS has updated the advisory to exclude Windows 10 and newer server versions that do not include the dll anymore. Apparently Didier Stevens researched it and found around W10 1703 it was removed. Is there any way to get the QID updated to reflect that or should I be looking at this a different way?
Hi Tom,
Thanks for reaching out.
We updated detection logic for QID 91617 yesterday, since MS updated advisory ADV200006. Please use signature manifest version VULNSIGS-2.4.850-3 or later for latest changes. You can also refer to updated section “Detecting ADV200006 with Qualys Vulnerability Management” in the blog. Thanks,
Can you please help me with list of windows versions where we have this atmfd.dll.
Hi Animesh,
Seems Qualys still reports this vulnerability for Windows Datacenter 2019 Version 1809, even though it is not affected according to ADV200006. Can that QID also be fixed to consider server versions as well? Thanks
Based on the MS link of ADV200006, I understand that the latest April 2020 monthly security update will addressed this vulnerability. However, the solution QID 91617 mentioned to perform the workaround. Will there any new QID that will be released or Qualys is going to update the QID91617 solution information ?
Thank you in advance.