Qualys Supports New Cisco Threat-Centric NAC
Integrated Vulnerability Data Dynamically Alters User Permissions Based on the Fluctuating Threat Ratings of a Device
The onslaught of new devices and applications in the enterprise has clouded visibility into who and what is connecting to the network. This raises increased security concerns, since more devices mean more potential ways to compromise the network. Enterprises have generally responded to these concerns by continually adding security systems from multiple vendors to their networks.
However, this heterogeneous security environment has a huge downside: Organizations end up with siloed repositories of information. To identify network threats and appropriate remediation, enterprises have tried to piece together these repositories either manually or with additional tools such as SIEM, with varying results.
Fortunately Cisco has recognized this scenario and created Cisco Rapid Threat Containment. This offering uses an open integration of Cisco’s security products, technologies from Cisco security partners, and the network control of the Cisco Identity Services Engine (ISE, which shares details through the Cisco Platform Exchange Grid (pxGrid)). In addition, one can protect critical data through the solution’s Threat-Centric NAC feature, which can dynamically change users’ access privileges when their threat or vulnerability scores increase via seamless integration with Qualys Vulnerability Management (VM).
Cisco has integrated Qualys to enable ISE to retrieve Common Vulnerability Scoring System (CVSS) classifications from Qualys VM. This integration enables one to make graceful manual or automatic changes to a user’s access privileges based on their security score (see Figure 1 below).
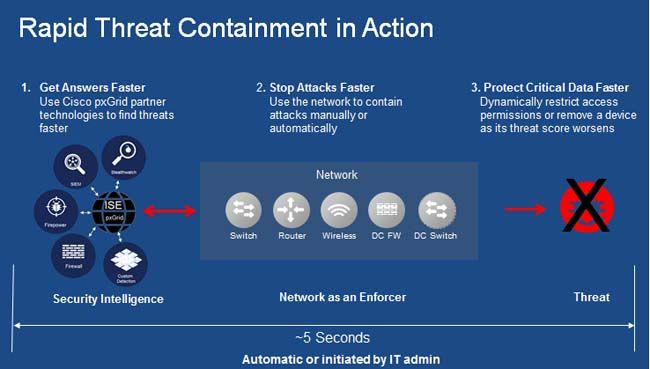
For instance, if a user’s device is clean, you can grant it full access to all authorized services and data. But if the device develops a few vulnerabilities, you can have its access to critical data restricted while allowing access to less critical applications such as email. The user can still work while you protect assets that you can’t afford to lose to malware or ransomware. But if high potential data loss vulnerabilities are discovered on the device, the network can immediately move the device to a quarantine before it can cause further damage.
Qualys VM is a cloud service that gives you immediate, global visibility into where your IT systems might be vulnerable to the latest Internet threats and how to protect them. It helps you to continuously secure your IT infrastructure and comply with internal policies and external regulations.
Qualys VM is part of the Qualys Cloud Platform, an integrated suite of solutions that helps organizations simplify security operations and lower the cost of compliance by delivering critical security intelligence on demand and automating the full spectrum of auditing, compliance and protection for IT systems and web applications.
Qualys VM is the only vulnerability management solution that is presently integrated with Cisco Rapid Threat Containment and Threat-Centric NAC. To learn more about the Qualys Cloud Platform, Cisco Rapid Threat Containment and Threat-Centric NAC, please visit Qualys’ booth (#1912) at Cisco Live or the Cisco Security Partners demonstration pod in the Cisco Partner Pavilion.
Do all versions Qualys support this feature integration; Express Lite, Express, Enterprise?
The integration is licensable with Enterprise and Express.