SANS Institute: Hackers Paint a Bullseye on Your Employees and Endpoints
End users and their devices are right smack in the center of the battle between enterprise InfoSec teams and malicious hackers, and it’s not hard to see why.
When compromised, connected endpoints — desktops, laptops, smartphones, tablets — offer intruders major entry points into corporate networks. However, end users are also their organizations’ best threat detection tools.
That’s a key takeaway from SANS Institute’s “2017 Threat Landscape Survey: Users on the Front Line,” a report published in August and co-sponsored by Qualys.
The study, conducted in May and June, polled 263 IT and InfoSec pros from companies of all sizes and major industries such as finance, government, technology and education.
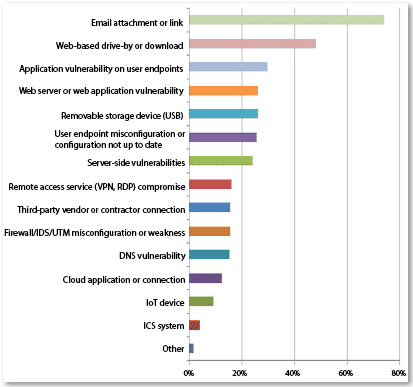
It found that most of the top intrusion methods reported by respondents sought to directly or indirectly compromise end users or their devices. Hackers’ preferred threat vectors included:
- Email attachment or link (flagged by 74 percent of respondents)
- Web-based drive by or download (48 percent)
- App vulnerabilities on endpoints (30 percent)
- Web server / web app vulnerabilities (26 percent)
- Removable storage devices (26 percent)
Unsurprisingly, phishing, including spear-phishing and whaling, was identified by respondents as the threat they detect most often, as well as the one that has the biggest impact in their organization.
It follows, then, that when respondents were asked what they could have done better to prevent breaches, the most popular response (67 percent) was “train our users to be more aware.”
That was also the top response when they were asked to name the primary area where they plan to make a major investment in the next 18 months.
However, the report’s author Lee Neely, a SANS Institute mentor instructor, cautions organizations against focusing too much on end user training and overlooking security tools that automate detection.
“Organizations should examine the path from the services to the endpoint, making sure relevant, current protections are in place that rely less on the user to detect an active attack and more on automation,” Neely wrote.
This is especially important for dealing with what SANS Institute calls “malware-less threats,” a type of attack that is on the rise and is tricky to deal with. It can’t be detected by signature-based defenses because it uses built-in features of the OS to turn it against itself without downloading recognizable files.
Right now, the strongest mechanism to detect these malware-less threats — scripting attacks, compromised credentials, process exploits, malicious binaries — is “a human noticing something odd happening,” Neely said during a webcast where the report was discussed.
In fact, calls from users to their help desk tied for second among the means for discovery of significantly impactful threats. Networking monitoring ranked first, and tied for second was alerts from network perimeter devices, such as firewalls and intrusion detection systems (IDS).
This means that the end user remains a “highly tuned detection mechanism” especially when employees don’t flood the help desk with false positive reports, but instead are alert and able to recognize when something is truly wrong.
Emerging technologies involving automation, artificial intelligence, threat hunting, pattern matching and machine learning are still evolving but appear promising in helping fill this gap. “I’m not always comfortable with relying on the end user to detect a problem,” Neely said.
Qualys’ CISO agreed that “the endpoint is the highest risk area of exposure” and one of the main threat landscape vectors Qualys focuses on.
“What you’ve seen on this survey is high risk from email exposure, from internet browsing usage and from the memory-focused threats that will continue to advance,” he said during the webcast, referring to malware-less attacks.
“We have to get better at behavioral monitoring and memory analysis,” he said. “That’s where the threat vectors are moving and that’s where we’re seeing advanced attacks.”
With your employees and their internet-connected devices in the crosshairs of attackers, you’ll find a lot of concrete insight, tips, best practices and analysis in both the report and the webcast, which touch on topics such as:
- Ransomware
- DDoS attacks
- IT and security staff training
- Discovery and remediation time and techniques
- Zero-day threats
- Vulnerability management
- IoT security
- Third-party risk
- Security tools and services