Countdown to GDPR: For GDPR Compliance, Web App Security Is a Must
With web and mobile apps becoming a preferred vector for data breaches, organizations must include application security in their plans for complying with the EU’s General Data Protection Regulation (GDPR.)
First discussed in the 1990s and turned into law in 2016, GDPR goes into effect in May of this year, imposing strict requirements on millions of businesses and subjecting violators to severe penalties.

The complex regulation applies to any organization worldwide — not just in Europe — that controls and processes the data of EU citizens, whose privacy the GDPR is meant to protect. Fines are stiff, including up to 4 percent of an organization’s annual revenue, or €20 million, whichever is higher.
While GDPR makes only a few, vague references to technology requirements for compliance, it stresses that data “controllers” and “processors” must safeguard customer information by implementing “appropriate technical and organisational measures.”
The regulation also highlights the need for organizations to have in place secure IT networks and systems that can “resist, at a given level of confidence, accidental events or unlawful or malicious actions.”
“This could, for example, include preventing unauthorised access to electronic communications networks and malicious code distribution and stopping ‘denial of service’ attacks and damage to computer and electronic communication systems,” reads the document.
Despite the lack of technology requirement prescriptions in the 88-page document, the bottom line message is clear: Organizations must do whatever is in their power to prevent accidental or malicious incidents that compromise the “availability, authenticity, integrity and confidentiality of stored or transmitted personal data.”
The typical organization uses hundreds or thousands of custom and commercial web apps, which often aren’t securely developed nor properly tested, and contain dangerous vulnerabilities and misconfigurations.
Since they’re usually linked to back end systems, breached web apps offer hackers a direct conduit to corporate data, including personal information from customers. In its 2016 Data Breach Investigation Report, Verizon found that, compared to the other attack patterns, web app attacks had become the most likely to trigger a data breach, a finding reconfirmed in the 2017 version of the Verizon study.
Clearly then, organizations must have solid web application security to comply with GDPR. But what’s the criteria for determining your organization is doing its best to protect customer personal data from web application attacks?
Below we outline a series of risks and best practices culled from the non-profit Open Web Application Security Project (OWASP)’s OWASP Top 10 Privacy Risks Project and OWASP Top 10 Application Security Risks, and we explain how Qualys can help organizations slash their risk of data breaches caused by web app hacks.
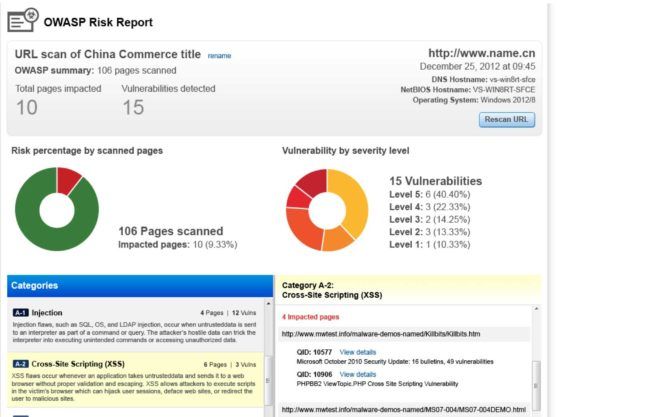
Specifically, Qualys Web Application Scanning (WAS) and Qualys Web Application Firewall (WAF) can help customers adopt the OWASP privacy and security best practices that are detailed in the next two sections, through a DevSecOps approach, in which security tools and processes are automated and embedded into the application development and deployment lifecycle.
Since all web apps are different, there’s no silver bullet for tracking personal user data and enforcing its protection. With Qualys, one can understand the inner security and compliance status of an application via WAS discovery and vulnerability scans, before addressing the GDPR policy requirements, possibly through WAF security rules.
OWASP Top 10 Privacy Risks Project
The Top 10 Privacy Risks Project’s goal is to shine a light on real-life web app dangers and to offer developers concrete tips for mitigating them.
Unsurprisingly, “web application vulnerabilities” top this list, because, as OWASP explains, “failure to suitably design and implement an application, detect a problem or promptly apply a fix (patch) is likely to result in a privacy breach.”

OWASP warns that, for example, injection flaws let attackers copy or manipulate data. Other issues can be sensitive data exposure, use of insecure direct object references, use of software components with known vulnerabilities, and security misconfigurations.
“In general it is possible for attackers to gain access to, manipulate or delete personal data that the application is processing by abusing rights, entering malicious code or eavesdropping on communications,” OWASP states in this companion document to the Top 10 Privacy Risks Project.
Among the recommendations: perform penetration tests frequently, install updates and patches on a regular basis, track remediation, and apply secure development procedures.
Second on the list is “operator-sided data leakage,” which OWASP describes as “failure to prevent the leakage of any information containing or related to user data, or the data itself, to any unauthorized party resulting in loss of data confidentiality.” Whether triggered by malicious breaches or unintentional mistakes, these data leaks are caused by “insufficient access management controls, insecure storage, duplication of data or a lack of awareness.”
Recommendations include having an appropriate identity and access management system, using strong encryption for all personal data stored, and masking personal data via methods like anonymization and pseudonymization.
Below we highlight other items on the list that are relevant for information security teams working on GDPR compliance:
Insufficient Data Breach Response
You need to inform affected individuals about actual or suspected data breaches. In addition, you must fix the cause behind the breach, whether it was accidental or intentional, and attempt to limit the leaks.
OWASP recommendations fall into two buckets: First are the steps to take in advance, such as continuously monitoring for personal data leaks and loss. The second category outlines how to respond to a breach, including assembling a response team and notifying the affected individuals.
Insufficient Deletion of personal data
This item refers to the ability to quickly and comprehensively delete personal data once it’s no longer needed, or once consumers request that it be erased.
Best practices include following data retention, archival and deletion policies, verifying deletion, limiting access to data that can’t be erased, taking note of historical data stored in older cloud snapshots, and considering data that was backed up or shared with third parties.
Sharing of data with third parties
Sharing customers’ personal data with third parties, such as partners and affiliates, creates its own set of risks, and it’s specifically addressed in GDPR, which states that “data owners” are responsible and liable for the non-compliance of their third parties. Organizations should lay the legal ground work now, amending service agreements, to ensure they are able to collect evidence automatically via web application scans of the supplier ecosystem, or using security assessment questionnaires.
OWASP recommends that organizations use their servers as a proxy for content they share, deploy full Do Not Track capabilities per the latest W3C standard, strongly consider using tokenization or anonymization when sharing data, and develop a third-party monitoring strategy.
Outdated personal data
Using outdated or erroneous customer data, and failing to update it and correct it, can also put an organization in GDPR hot water.
OWASP suggests checking for possibilities to update personal data in the web app, including regular checks to validate that data is still accurate, and creating a mechanism to share data changes and updates with third parties that have older versions of those data sets.
Missing or Insufficient Session Expiration
A web app that doesn’t effectively terminate sessions leaves a user’s account and data potentially exposed for malicious use, or cause user data to be collected without their consent.
OWASP recommendations include featuring logout buttons prominently and setting up automatic session timeouts in the web app.
Insecure Data Transfer
Data must be protected during transfers to prevent it from being intercepted and compromised.
OWASP countermeasures include using secure protocols for personal data, avoiding personal information in URLs, enforcing HTTPS for the entire web app session, supporting TLS/DTLS instead of SSL v3, and using ECDHE and GCM ciphers, instead of static RSA key exchange and CBC-based ciphers.
OWASP Top 10 Application Security Risks
Another great resource from OWASP is its list of Top 10 Application Security Risks, which was updated in 2017. Although there are overlaps with the privacy risks lists, this one has a more technical focus that’s not necessarily centered on privacy issues. However, the security risks on this list are all relevant for infosec teams tasked with protecting customer data for GDPR compliance.
These top security risks include:
- Injection flaws, such as SQL, NoSQL, OS, and LDAP injection, which let an attacker execute commands and access data
- Broken authentication, where improper authentication and session management can allow attackers to compromise passwords, keys, or session tokens, and hijack accounts
- Sensitive data exposure, which refers to the transfer and storage of sensitive data without appropriate protections, such an encryption
- XML external entities, which can exploited to disclose internal files and execute remote code if the XML processor is older or poorly configured
- Broken access control, which refers to improperly enforced restrictions on actions of authenticated users
- Security misconfiguration, which involves issues such as insecure default configurations, open cloud storage, misconfigured HTTP headers, and verbose error messages
- Cross-site scripting, which lets attackers execute scripts in browsers to hijack user sessions, deface websites, or redirect users to malicious sites
- Insecure deserialization, which can lead to remote code execution
- Vulnerable component usage, which introduces known bugs into an application, creating easy opportunities for successful attacks against it
- Insufficient logging and monitoring, which keeps infosec teams in the dark about ongoing breaches
Mitigating these risks will go a long way towards securing your web applications, and specifically towards protecting the personal data of EU residents that you hold, share and process.
Qualys offers comprehensive web application security for GDPR compliance
Qualys combines web application scanning with web application firewall protection for complete, accurate and scalable web security. With Web App Scanning (WAS) and Web App Firewall (WAF), Qualys provides a single interface for identifying, managing and fixing all of the vulnerabilities and misconfigurations on web applications deployed in private, public and hybrid clouds.
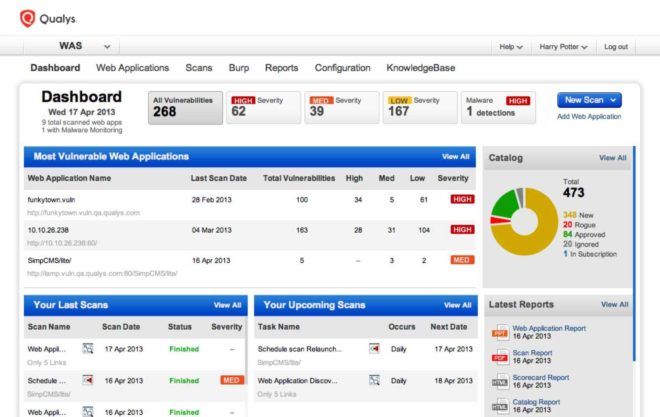
Qualys WAS continuously discovers and catalogs web apps in your network – including new and unknown ones — giving you full visibility, and allowing you to proactively tag those that are within the GDPR scope accordingly.
Qualys WAS detects vulnerabilities and misconfigurations comprehensively and continuously, and gives you automated, extensive detection capability to protect against the OWASP Top 10 Application Security Risks and beyond.
“The vulnerability detections in Qualys WAS are consistent with, but more granular than, the OWASP Top 10. The WAS QIDs representing vulnerabilities do not always directly refer to a Top 10 item, but most of the QIDs fall under one or more of the Top 10 items. WAS also includes some QIDs for vulnerabilities not explicitly covered by the OWASP Top 10 but [that] nevertheless pose a risk to web applications,” reads the Qualys WAS and OWASP Top 10 2017 Coverage document published in November 2017.
Scaling up to thousands of web apps, Qualys WAS conducts incisive, thorough, precise scans, with few false positives. Its seamless integration with Qualys Web Application Firewall (WAF) gives you one-click patching of web apps, including mobile apps and IoT services. With WAS, you can also insert security into DevOps environments by detecting code security issues early and often in the app development and deployment pipeline. Qualys WAS also includes scans that identify malware infections on your websites using behavioral, heuristic, and reputational analysis.
Meanwhile, Qualys WAF reduces application security cost and complexity with a unified platform to detect and virtually patch web application vulnerabilities. Simple, scalable and adaptive, Qualys WAF lets you quickly block attacks, prevent disclosure of sensitive information, and control when and where your applications are accessed, while legitimate traffic is not logged by the Qualys Cloud Platform. Qualys WAF can be deployed in minutes, supports SSL/TLS and doesn’t require special hardware.
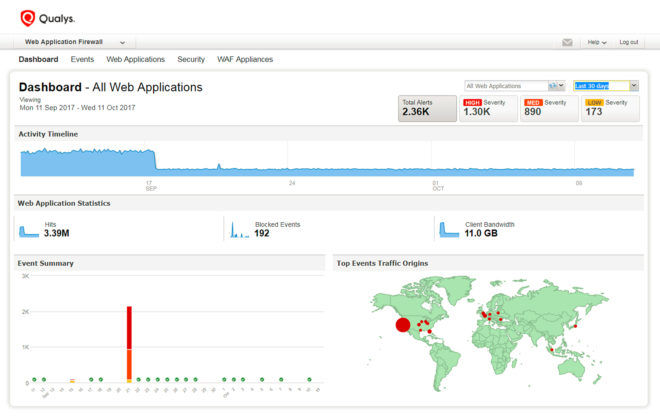
Qualys WAF and Qualys WAS work together seamlessly. You scan web apps transparently with Qualys WAS and assess both the application and its WAF policy, deploy one-click virtual patches for detected vulnerabilities in WAF, and manage it all from a centralized cloud-based portal.
In short, with Qualys you’ll be able to have clear, widespread visibility into all your web applications, and continuous detection of vulnerabilities, malware and misconfigurations. That way, you’ll dramatically reduce web app attacks that trigger data breaches that could put you on the wrong side of GDPR.
Read Other Posts in the Countdown to GDPR Series:
- Reduce Your Risk
- Get 20/20 Visibility Into Your IT Assets
- Prioritize Vulnerability Remediation
- Assess Vendor Risk
- Manage Vulnerabilities
- IT Policy Compliance
(Rémi Le Mer is a Security Solution Architect and SME for Qualys WAF)
To learn more about how Qualys solutions can help you become GDPR compliant, visit qualys.com/gdpr where you can download our free guide and watch our webcast.
To find out more about WAS and WAF, you can visit the Qualys WAS Community and the Qualys WAF Community, and sign up for a free trial.