Qualys FIM: Be Compliance Ready with Intuitive, Ready-to-Use File Monitoring Profiles
Requirements for file-level security are often set by laws, regulations, and audit standards. These include identification of what must be protected, the various controls required to implement security, and outcomes required to successfully pass audits for compliance. This blog describes these and how Qualys File Integrity Management (FIM) provides ready-to-use profiles to implement specific use cases.
Enterprise SecOps teams have two major priorities for file-level security that affect how security controls are selected, deployed, and managed. Obviously, they must effectively address all issues and actions that may affect file integrity. They also must document all security processes and report results for compliance auditors. Drivers include a plethora of laws and regulations such as PCI DSS, NERC CIP (CIP 010), FISMA, SOX, NIST (S17), HIPAA, CIS controls, GDPR, and more.
Before addressing compliance, first let’s consider the vital controls that ensure file-level security.
A solution for file-level security should detect changes from a baseline established for files and file paths. Security teams should receive instant alerts about suspect variants. Monitoring for indicators of compromise such as file tampering may reveal illicit activity, and security teams must be alerted whenever these changes occur. To ensure the security of business and customer data, organizations must integrate file change monitoring into their continuous efforts to maintain cyber safety and hygiene – especially in environments with highly sensitive data.
However, deciding the scope of what to monitor is a challenge for most SecOps teams. If not configured correctly, teams can be inundated with event notifications. Identifying events of interest within hundreds of thousands or even millions of events is a huge effort. One must closely monitor files that are relevant to the important parts of the IT ecosystem – files that are not expected to change without a business requirement.
How Do You Decide What to Monitor?
It is important to be extremely methodical when deciding what files to monitor. A thorough plan is vital to the success of your file monitoring practices. Some of these requirements may be predetermined by relevant laws and regulations, such as highly specific prescriptions by the PCI DSS. Consider these decision factors:
What data is critical for the organization and must be continuously monitored?
It is infeasible for an organization to monitor every action taken on every file. You must separate “critical” files from merely “important” ones in order to pinpoint files requiring constant monitoring.
What type of actions or activities should be monitored for variable files?
Certain files such as logs and parts of an operating system are continuously modified. Monitoring them for all sorts of activities would be highly inefficient as most results would be meaningless. By contrast, you should track file removals and all changes to security settings.
What are the most vulnerable attack surface areas in the environment?
Analyze your environment to identify information that may be lucrative for an attacker; this determination will tell you where to focus application of file-level monitoring security controls.
Superficial and inaccurate monitoring parameters generate millions of events with no context, rather than useful and actionable alerts. Stay focused on the top priorities:
- Assess your network and environment
- Compile a file inventory
- Determine critical assets
- Establish roles and authority for users.
How Does Qualys File Integrity Monitoring Help You?
Qualys File Integrity Monitoring (FIM) contains its own library of out-of-the-box monitoring profiles. Qualys security analysts have deep insight and rich subject matter expertise. They create OOTB profiles to provide you with a set of highly critical files that must be monitored for specific activities.
The use of these profiles will save your SecOps team a major amount of time as they are preconfigured to match monitoring scope with requirements of each compliance standard. As an additional benefit, these profiles are fine-tuned and categorically exclude files that cause false positives.
This built-in expertise helps you to kickstart your monitoring efforts and adhere to PCI DSS requirements 10.5.5 and 11.5 as well as other compliance standards mentioned above.
This screenshot shows the library of monitoring profiles available out-of-the-box with Qualys FIM.
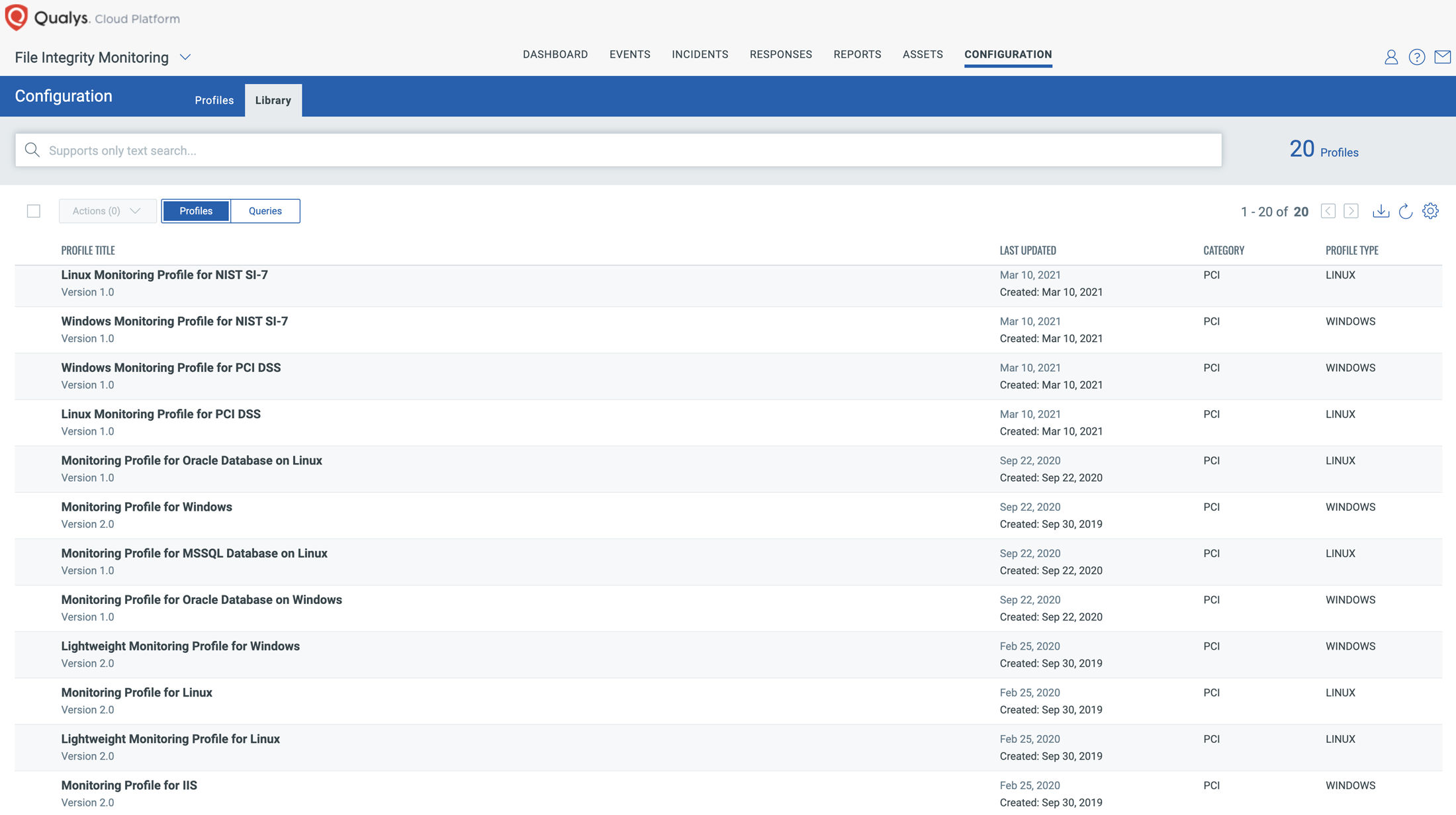
Qualys highly recommends that enterprise customers use the lightweight monitoring profiles from its library. With the help of research and analysis by our team of security experts, these lightweight profiles have been created to continuously monitor a small set of extremely critical OS files such as boot loader, kernel parameters, configuration files, initialization files, system volume files, critical binaries, and authentication files. It is critically important that they be monitored on a real-time basis for any kind of anomalous behavior.
Using these profiles ensures negligible processing load and helps you achieve various compliance mandates for the associated assets.
Secure the CI/CD Pipeline
Finally, let’s consider file-level security in a typical DevOps CI/CD workflow. When a DevOps team deploys golden images to run their workloads, the Qualys Cloud Agent already deployed in your environment is baked-in with FIM for the images, which automatically enables the out-of-the-box FIM profiles, for instance. This capability ensures file integrity monitoring required for your compliance programs is initiated before images are deployed in production.
Security teams may also apply application-specific FIM profiles based on the workloads and applications deployed on the instance. Once the images are in production, FIM continuously monitors changes to the critical files and paths per the selected profiles.
In conclusion, the out-of-the-box monitoring profiles of Qualys FIM can ease the mammoth task of monitoring the ever-changing ocean of files stored by your organization. These tightly configured profiles will help you stay vigilant for changes in critical files and enable compliance with relevant industry mandates and regulations.
Acknowledgments
Lavish Jhamb, Mohd Anas Khan, and Mukesh Choudhary provided technical guidance.