Analysis: Adobe Flash Player Zero Day CVE-2011-0611
Adobe recently released an advisory warning about a zero day vulnerability affecting Adobe Flash Player 10.2.153.1 being exploited in the wild. The attack uses a flash .swf file embedded inside a seemingly innocuous .doc file. The embedded .swf file uses ActionScript to perform a heap spray and then loads another malicious swf files created via the loadBytes() function.
(Click figure below for full resolution image).
Sample
File: Disentangling Industrial Policy and Competition Policy.doc
MD5: 96cf54e6d7e228a2c6418aba93d6bd49
SHA1: 820699d9999ea3ba07e7f0d0c7f08fe10eae1d2d
CVE: CVE-2011-0611
File Type: MS Word.doc file with embedded flash .swf file
Analysis of the Malware:
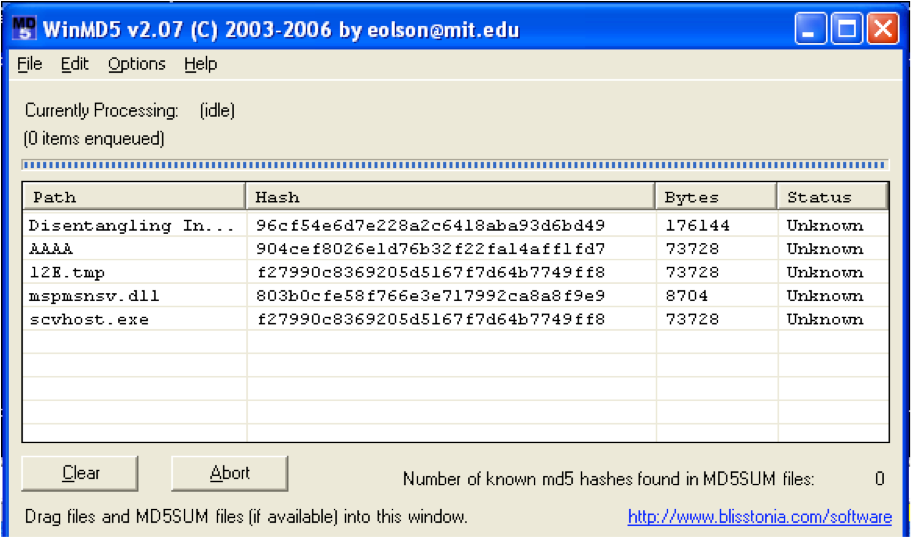
- On opening the .doc file, the vulnerability in flash player is exploited and it creates “scvhost.exe” and “AAAA” files in the %temp% directory. The “scvhost.exe” is the malware dropper and file “AAAA” is a dummy word file that will be shown to the user after the exploited is completed.
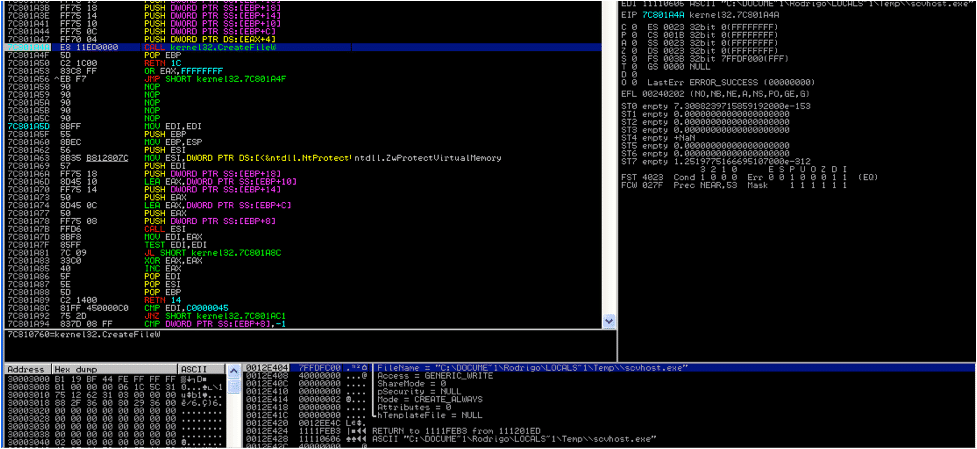
- Once scvhost.exe is created, this file is then executed using the command “cmd /c “%temp%\\scvhost.exe””.
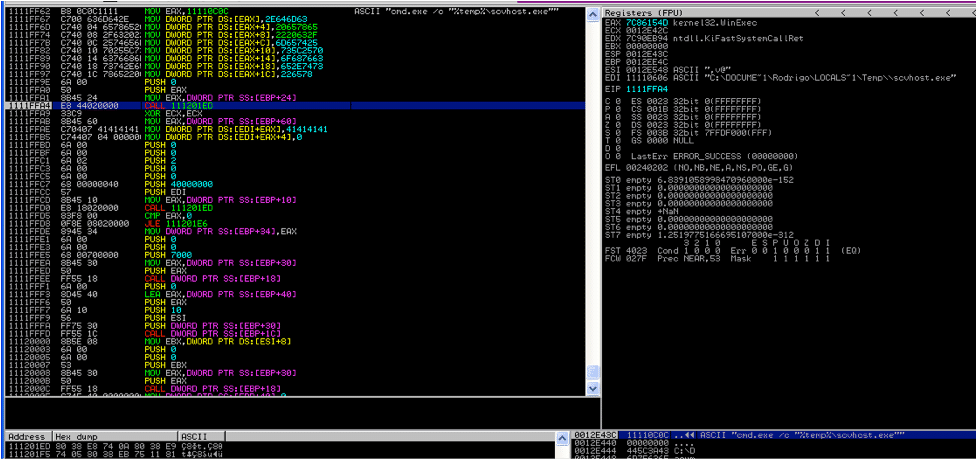
- The malware then replaces the original .doc malicious file with the innocuous “AAAA” file it created and then opens it. It also kills “hwp.exe” process. It does this by executing the following command:
cmd.exe /c "dir /s %windir%\system32\*.sys&&taskkill /im hwp.exe /f & dir /a /s %windir%\system32\*.msc && copy %temp%\\AAAA "C:\Documents and Settings\Rodrigo\Desktop\Disentangling Industrial Policy and Competition Policy.doc " /y && "C:\Documents and Settings\Rodrigo\Desktop\Disentangling Industrial Policy and Competition Policy.doc" - The scvhost.exe process on startup stops the “WmdmPmSN” service. The scvhost.exe process now copies the “SFC_OS.dll” to a temp file.

- Copies the windows %system32%\\mspmsnsv.dll to %programfiles%\\commonfiles\\bak.dll. The system32%\\mspmsnsv.dll file is then moved to %temp% dir and set to delete on restart.
- Svchost.exe then creates the malicious %system32%\\mspmsnsv.dll and msimage.dat.

- Svchost.exe then copies this %system32%\\mspmsnsv.dll to %system32%\\dllchace\\mspmsnsv.dll
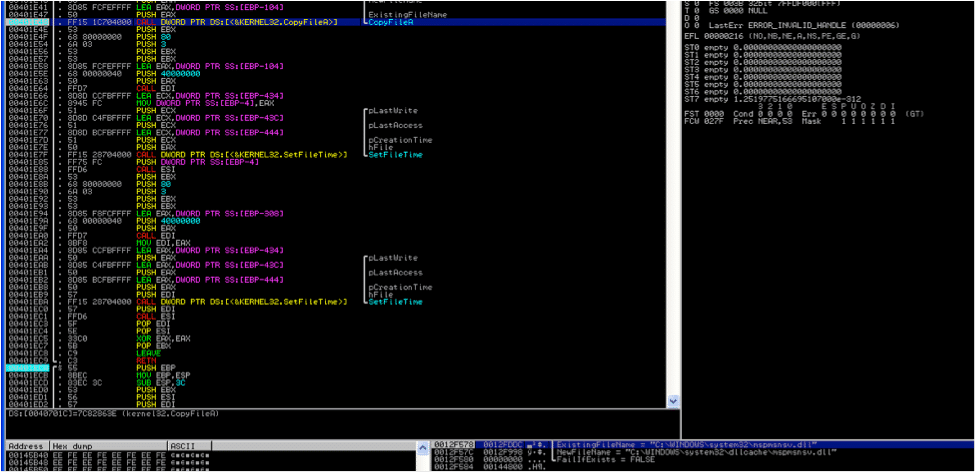
- Svchost.exe is then moved to a %temp%\\[tempfilename] and is then set to delete on reboot and starts the “WmdmPmSN” service. Thus leaving no trace of any malicious executable on system.

- Once the service restarts it tries to connect to its masters at liciayee.dyndns-free.com.
Files Created and MD5:
Conclusion
As a best practice, avoid opening unexpected e-mails or attachments and do no click on links from un-trusted sources. Adobe has released a critical security advisory APSA11-02 and is in the process of finalizing a fix for Adobe Flash Player 10.2.x, Adobe Acrobat X (10.0.2) and earlier 10.x and 9.x versions for Windows and Macintosh, Adobe Reader X (10.0.1) for Macintosh, and Adobe Reader 9.4.3 and earlier 9.x versions for Windows and Macintosh.Google Chrome users can update to Chrome version 10.0.648.205. Verify the version of Google Chrome installed on your system. QualysGuard customers can scan for QID: 119144 for Adobe Flash and QID: 119145 for Adobe Reader/Acrobat for detecting this vulnerability in their network.