Android Security Evaluation Framework: ASEF
Have you ever looked at your Android applications and wondered if they are watching you as well?
 Whether it’s a bandwidth-hogging app, aggressive adware or even malware, it would be interesting to know if they are doing more than what they are supposed to and if your personal information is exposed. Is there really a way to automatically evaluate all your apps, even hundreds of them, to harvest their behavioral data, analyze their run pattern, and at the same time provide an interface to facilitate a vast majority of evolving security tests with most practical solutions?
Whether it’s a bandwidth-hogging app, aggressive adware or even malware, it would be interesting to know if they are doing more than what they are supposed to and if your personal information is exposed. Is there really a way to automatically evaluate all your apps, even hundreds of them, to harvest their behavioral data, analyze their run pattern, and at the same time provide an interface to facilitate a vast majority of evolving security tests with most practical solutions?
To answer these questions, I created the Android Security Evaluation Framework (ASEF) to perform this analysis while alerting you about other possible issues. Use it to become aware of unusual activities of your apps, expose vulnerable components and help narrow down suspicious apps for further manual research.
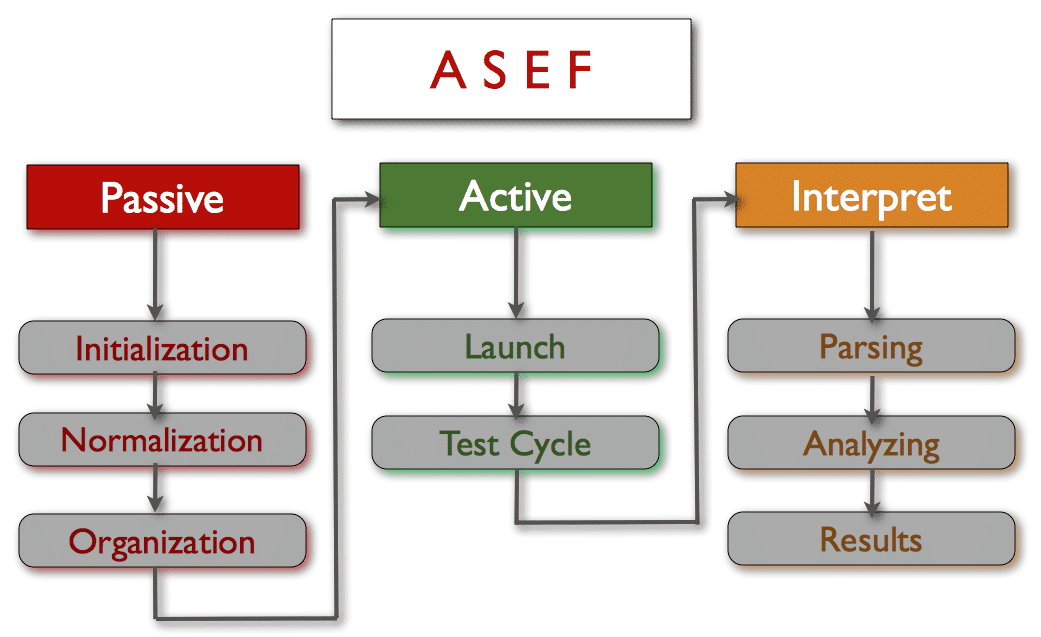
ASEF Framework
The framework takes a set of apps, either pre-installed on a device or as individual APK files, and migrates them to the test suite which runs through test cycles on a pre-configured Android Virtual Device (AVD). The technique is to simulate the entire lifecycle of an Android app on an Android device (virtual/physical) and collect data while triggering behavioral aspects of it. In simple words, download an Android app from an internet, install it on an Android device, launch it and mess with it (e.g clicking different buttons, scrolling up/down, swipe etc..) While doing so, collect an activity log using adb (Android debug bridge utility which is available as a part of an Android SDK) and network traffic using tcpdump (a widely used packet capturing tool).
Behavioral Analysis
During such a simple yet thorough approach of performing a behavioral analysis for various apps, interesting results were found about apps leaking sensitive information like IMEI, IMSI, SIM card or a phone number of a device. Some malicious apps might just send this data in clear text over the Internet and are much easier to be caught by analyzing collected behavioral data. However some malicious apps can be sophisticated enough to detect the default settings of a virtual Android device and might behave differently in such settings. In order to overcome such limitations, a virtual device can be custom built by fine-tuning the kernel and also altering default settings to emulate a real device or it can be replaced by a physical Android device.
Open Source
ASEF is now available as open source at http://code.google.com/p/asef/. With it, users can gain access to security aspects of android apps by using this tool with its default settings. An advanced user can fine-tune this, expand upon this idea by easily integrating more test scenarios, or even find patterns out of the data it already collects. ASEF will provide automated application testing and facilitate a plug and play kind of environment to keep up with the dynamic field of Android Security.
At Black Hat
If you are at Black Hat USA 2012 and/or B-Sides Las Vegas, come to my talk where I discuss the test cycles and results so far. And if not, read the A S E F Getting Started guide for an architectural overview of the framework and more details on the motivations behind the project.
Meanwhile, give ASEF a try and help improve this project with your comments, feedback and contributions.