Trusted scans simplified with Cyber-Ark PIM Suite integration
May 18, 2017: Please refer to Better Trusted Scanning with Qualys-CyberArk Integration.
April 29, 2013: Edited with new screenshot.
Trusted scans collect more detailed vulnerability information than “un-trusted” remote scans. That’s not surprising: with a trusted scan, the QualysGuard scanner logs into the target machine and reads configuration data including registry values and configuration files on the file system, just like a regular user session could. QualysGuard uses the configuration data to verify whether or not certain vulnerabilities exist. When running un-trusted remote scans, QualysGuard collects data by pinging network-accessible services on the target machine and interpreting the responses. QualysGuard then reports security issues that a remote attacker might use to access those systems. This approach misses local vulnerabilities such as those requiring user interaction from the browser or email client. Also, the response sometimes indicates the machine has a potential vulnerability, but not whether it is a confirmed vulnerability. Often a configuration value available via a trusted scan is required to determine if the potential vulnerability can be ignored or should be classified as a confirmed vulnerability.
For policy compliance, QualysGuard always performs trusted scans because system configuration data is required to verify compliance checks, such as password strength. For vulnerability management (VM) scans, QualysGuard administrators can choose either trusted or remote scans. But they often perform remote scans, even though they would benefit from the more detailed data collected in trusted scans.
In large organizations where thousands of machines are scanned regularly for vulnerabilities, managing passwords is a challenge. Currently administrators must manually provide QualysGuard with login credentials for each asset to be scanned. Password policies add more complexity; for example if a password ages out and gets changed, then those changes must be passed to QualysGuard so that its passwords remain current. The teams in charge of managing the scans usually don’t own the scanned machines.
Better Manageability with Cyber-Ark Integration
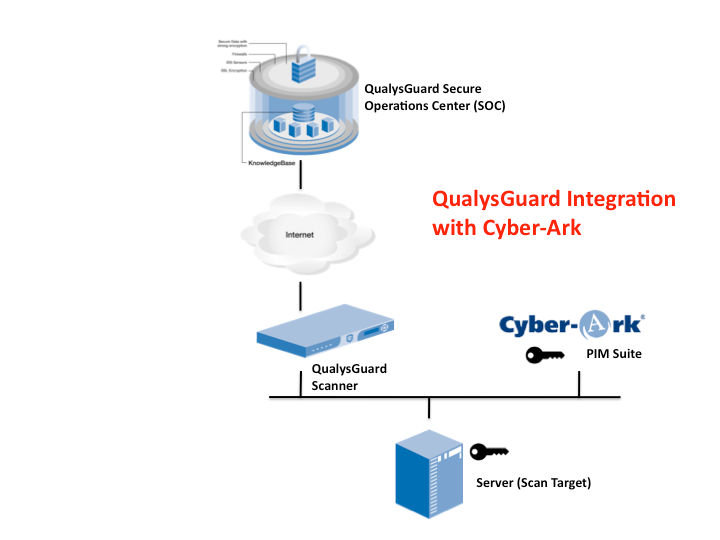
Using QualysGuard integration with Cyber-Ark Privileged Identity Management (PIM) Suite, management is simplified because organizations no longer need to store a copy of their passwords in QualysGuard. QualysGuard stores a pointer to the location of the password information in the Cyber-Ark Enterprise Password Vault® of the PIM suite, and the scanner appliance requests the password when it needs to perform the trusted scan. Because passwords are maintained in the Cyber-Ark Enterprise Password Vault®, the organization can change passwords at will or by using any policy via Cyber-Ark without having to worry about synchronizing those changes to QualysGuard.
Increased Security, Control and Audit of Login Credentials
While QualysGuard has industry-leading protections on the data it stores, some organizations that are particularly sensitive to password controls now have the assurance the QualysGuard no longer needs to store passwords centrally. In fact, an organization could set up a password policy to change its passwords via Cyber-Ark PIM Suite immediately after each password is used by QualysGuard to perform a trusted scan.
To revoke access, an administrator only needs to disable one user in Cyber-Ark instead of changing the relevant password on each target machine. Cyber-Ark can also store an audit trail of all uses to the login credentials.
How it Works
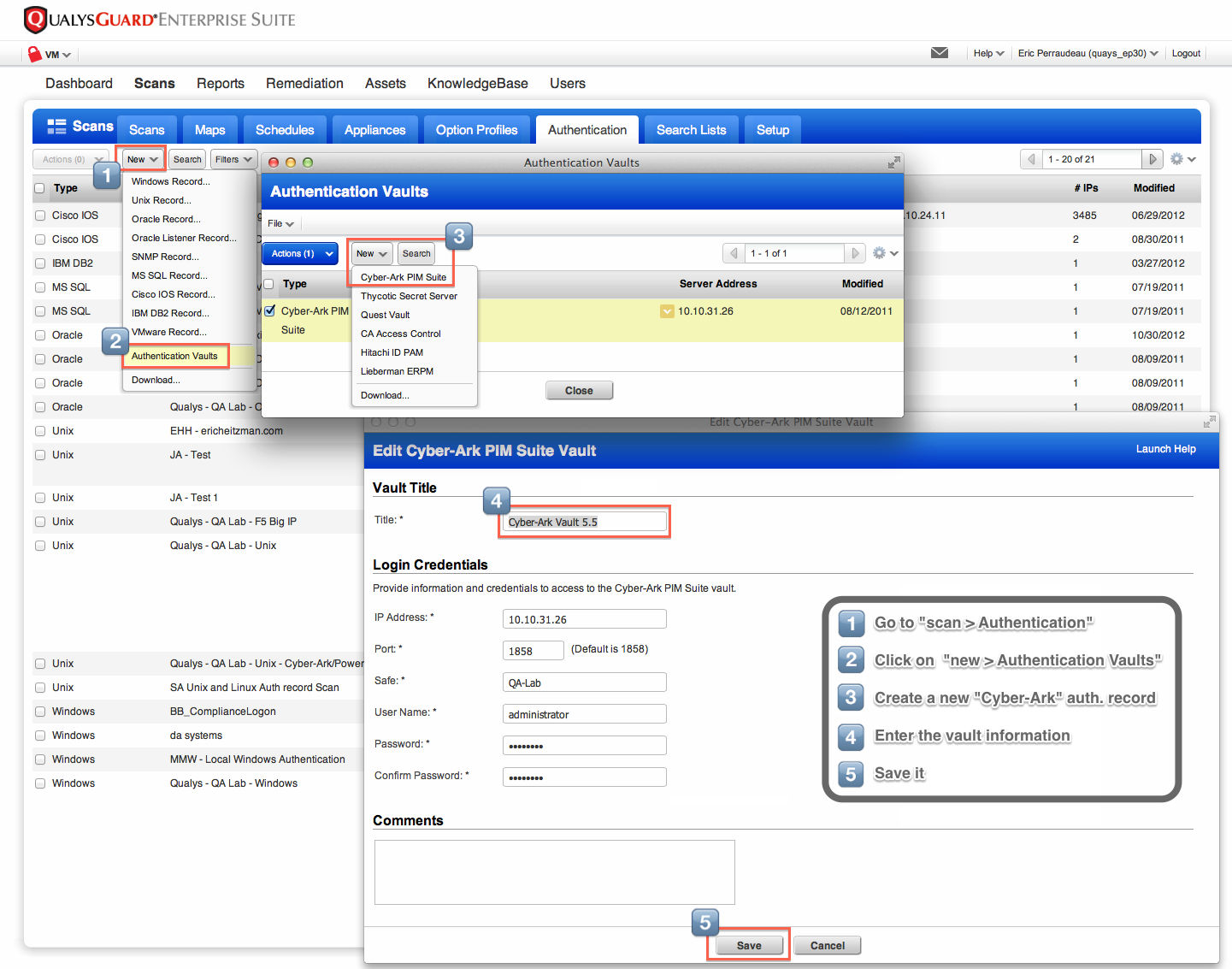
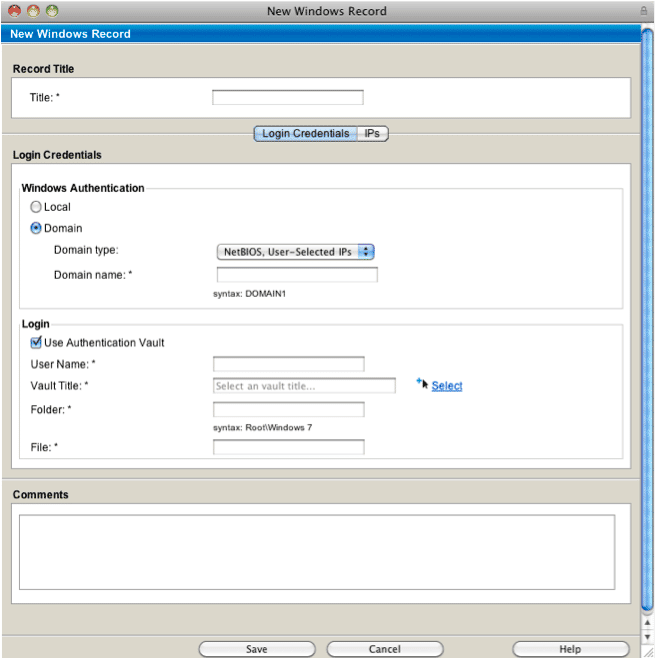
Configurating Trusted Scans: Without the Cyber-Ark integration, an admin configures QualysGuard with the logins and passwords that will be used for the trusted scans. With the Cyber-Ark integration, the admin configures QualysGuard with the Cyber-Ark Enterprise Password Vault® server and the correct safe within the vault where the passwords are stored (see Figure 1) and the Windows or Unix authentication record specifying an authentication vault for a specific trusted scan (see Figure 2).
Figure 1 – Create a Cyber-Ark authentication vault record in QualysGuard
Figure 2 – Create a Windows or Unix authentication record specifying the use of an authentication vault
Running Trusted Scans: When the scan is ready to run, QualysGuard sends a request to the scanner appliance to run the trusted scan. Instead of specifying the password of the target machine, QualysGuard specifies the IP address of the Cyber-Ark Enterprise Password Vault® server and the name of the safe. The scanner appliance then passes this information to Cyber-Ark and requests the password for the given username, which it uses to log into the target machine and perform the trusted scan. After performing the scan, the scanner deletes every trace of the password and sends the scan results back to QualysGuard. The process is done.
Better Information for Stronger Security
For organizations that currently perform trusted scans, password management is now easier and more secure. This integration will hopefully encourage organizations to expand their trusted scanning across their global assets to collect better vulnerability and compliance data from their systems.