Automate Host Discovery with Asset Tagging
Let’s assume you know where every host in your environment is. Wasn’t that a nice thought? The reality is probably that your environment is constantly changing. Knowing is half the battle, so performing this network reconnaissance is essential to defending it.
Tag, you’re mapped!
A common use case for performing host discovery is to focus scans against certain operating systems. This can be done a number of ways in QualysGuard, historically via maps or light scans followed by a manual workflow. Today, QualysGuard’s asset tagging can be leveraged to automate this very process. By dynamically tagging hosts by their operating system, one can split up scanning into the following:
- Frequent light scans that update QualysGuard with the current mapping of your network via dynamic asset tags.
- Targeted complete scans against tags which represent hosts of interest.
We step through how to set up your QualysGuard to do exactly this below.
Set up operating system tags
If you are unfamiliar with how QualysGuard’s asset tagging works, our tutorial is a great place to start. Let’s start by creating dynamic tags to filter against operating systems.
Open your module picker and select the Asset Management module.
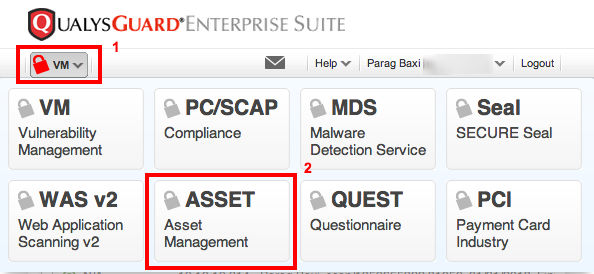
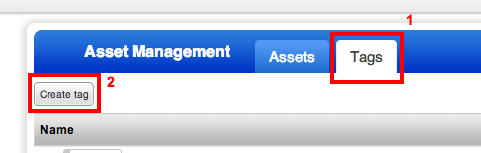
Click on Tags, and then click the Create tag button.
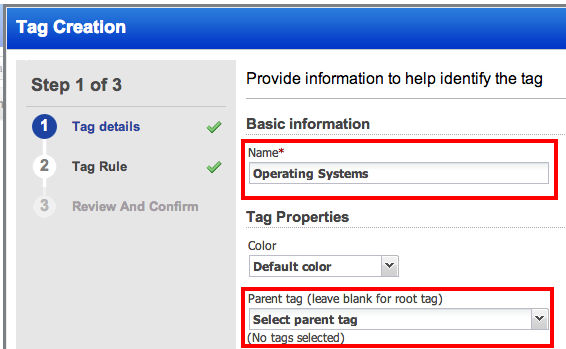
I prefer a clean hierarchy of tags. Let’s create a top-level parent static tag named, Operating Systems. Note this tag will not have a parent tag. Click Continue.
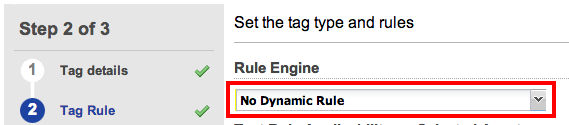
This tag will not have any dynamic rules associated with it. Click Continue.
Click Finish to create the parent tag.
We will create the sub-tags of our Operating Systems tag from the same Tags tab. These sub-tags will be dynamic tags based on the fingerprinted operating system. We will reference the community’s Asset tagging regular expression library for creating these dynamic tags.
Let’s create one together, let’s start with a Windows Servers tag. Mouseover the Operating Systems tag, and click on the dropdown arrow on the right. From the Quick Actions menu, click on New sub-tag.
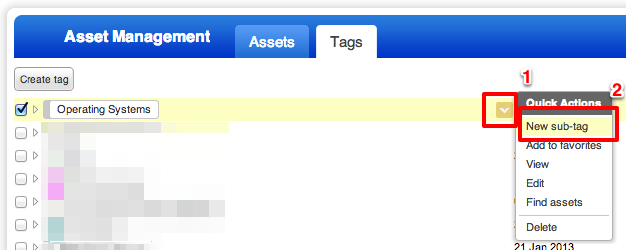
Name this Windows servers. The parent tag should autopopulate with our Operating Systems tag. Click Continue.
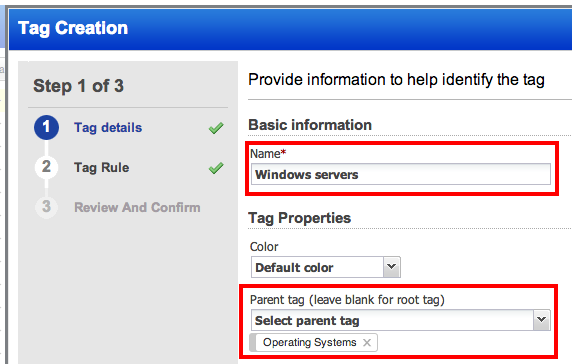
From the Rule Engine dropdown, select Operating System Regular Expression. From our Asset tagging regular expression library, input the following into the Regular Expression textbox:
^Windows .*Server((?!\/).)*$Also, check the Re-evaluate rule on save and Ignore Case checkboxes. Click Continue.
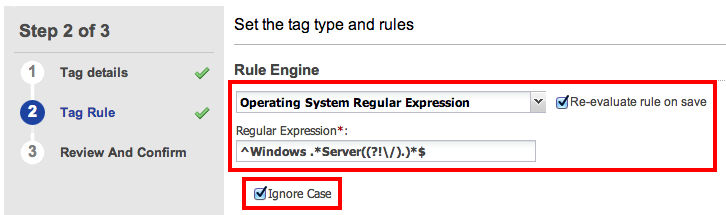
Click Finish. Our Windows servers tag is now created and being applied retroactively to all existing identified Windows server hosts. Feel free to create other dynamic tags for other operating systems.
Scan in breadth for host discovery
QualysGuard is now set to automatically organize our hosts by operating system. We can discover what assets are in our environment by frequently running a lightweight scan to populate these tags. Follow the steps below to create such a lightweight scan.
- Open the module picker and select the Vulnerability Management module.
- We will need operating system detection. From the top bar, click on Scans, and then Search Lists from the blue bar.
- Click on New…, and then Static List… button. Title this search list Operating System Detected and add QID, 45017, Operating System Detected. Click Save.
- Let’s import a lightweight option profile. Click Option Profiles from the blue bar.
- Click on New…, and then Import from Library… button.
- Select the Light Inventory Scan v.1, and then click Import. Making this global is optional.
- Add the Operating Systems Detected static list to this option profile.
The last step is to schedule a reoccuring scan using this option profile against your environment. You can even have a scan run continuously to achieve near real time visibility — see How to configure continuous scanning for more info.
Scan in depth against tags
After processing scan data in order to apply tags, QualysGuard will have an up-to-date inventory of operating systems in your environment. You can now run targeted complete scans against hosts of interest, e.g. those tagged with specific operating system tags.
This dual scanning strategy will enable you to monitor your network in near real time like a boss. For more reading on the trend towards continuous monitoring, see New Research Underscores the Importance of Regular Scanning to Expedite Compliance.
Note: The above types of scans should not replace maps against unlicensed IPs, as vulnerability scans, even light scans, can only be across licensed IPs.
Currently tags do not have scanners associated with them. Hence, if you have use specific scanners against specific asset groups, I recommend the following:
Very good article. Regarding the idea of running OS scans in order to discover new assets, I’m having a bit of trouble figuring out how mapping is utilized in the scenario you describe. It seems to me that for this idea to work, I need to work from asset groups that contain netblocks instead of IP addresses generated from maps, otherwise there no way I could discover assets. In other words, I want this to happen automatically across ranges and not have to keep updating asset groups manually. Can you elaborate on how you are defining your asset groups for this to work?
As a follow-up, I’ve found this pattern to work:
– Create asset groups consisting of the large ranges
– Run maps and/or OS scans across those ranges, tagging assets as you go. I personally like tagging via Asset Search matches instead of regular expression matches, if you can be that specific.
– Once you have the operating system tags assigned, create scans against OS tags such as Windows, Red Hat, etc.
This works well, the problem is that you end up scanning a lot of assets for the OS scan, so this method might not work if you don’t have a subscription that is large enough.