QualysGuard WAS 3.1 New Features
Table of Contents
QualysGuard WAS 3.1 will be released in production in mid-November and includes a number of new features and enhancements to existing capabilities.
Highlights include: A new web application tree to navigate the layout of a scanned site, authentication records that can be reused for multiple web applications, and CVSS scores in web application and scan reports.
Web Application Enhancements
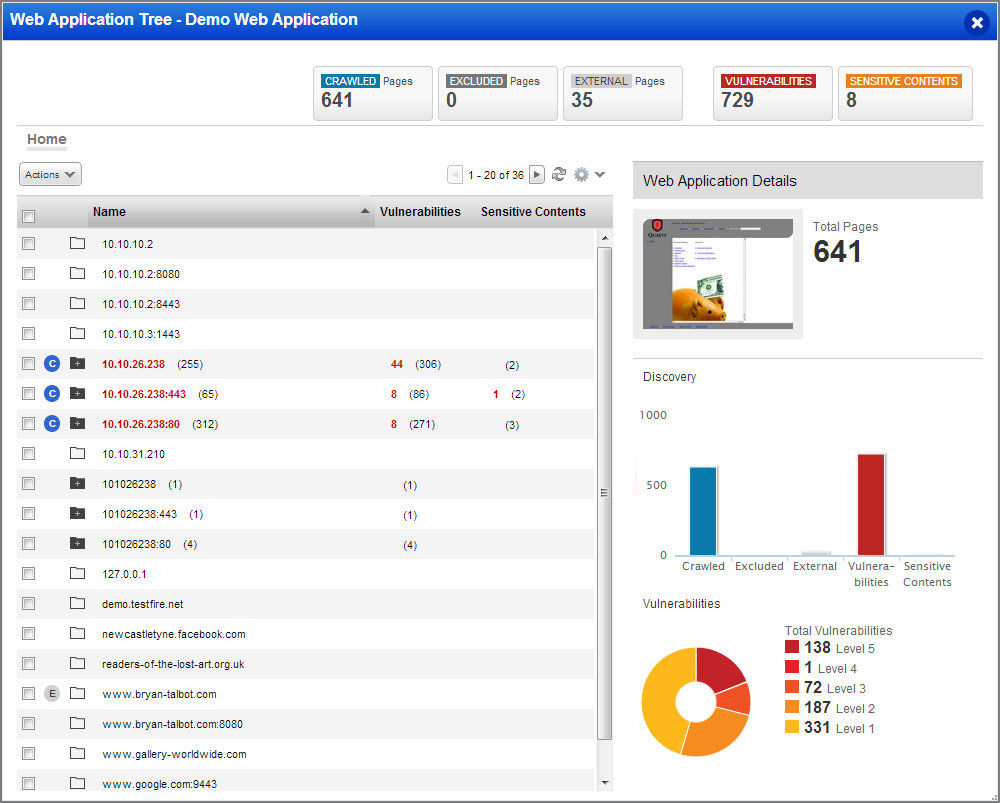
The New Web Application URL Tree: The web application URL tree allows you to easily locate information and perform actions on a web application. Now after running a quick discovery scan you can review the stucture of the site and decide if some areas should be white or black listed before running a vulnerability scan. After running a vulnerability scan you can also more easily identify the areas of the site have the most security issues.
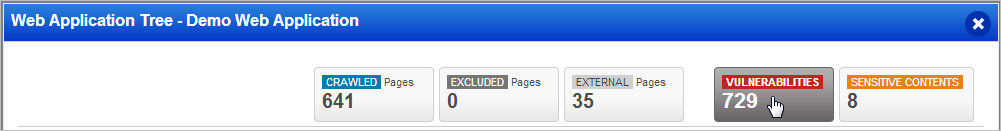
Filter the site tree: You can filter the view by crawled pages, excluded pages, external pages, vulnerabilities or sensitive content.
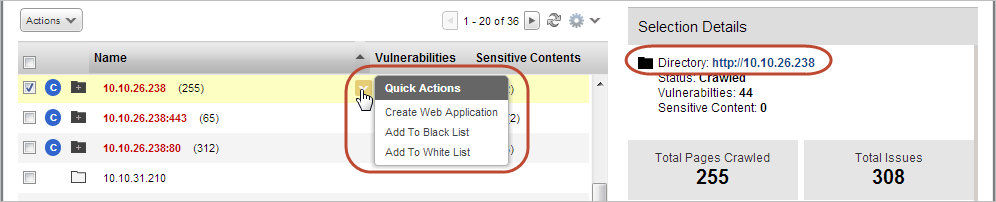
Take action: You can create a new web application or add the link to a black list or white list. You can also choose to view the link in your browser.
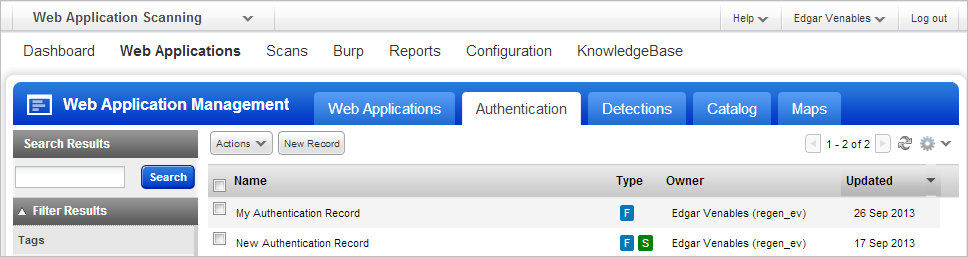
Authentication Records Are Now Independent: WAS authenticated scanning enables you to discover and validate vulnerabilities by performing more in-depth assessment of your web applications than unauthenticated scanning. In WAS 3.1 we’ve given authentication records their own place in the WAS UI, enabling you to manage authentication records independently from web application settings and easily create an authentication record once and associate it with multiple web applications. This is a major time saver for development, QA or portal environments that may share authentication.
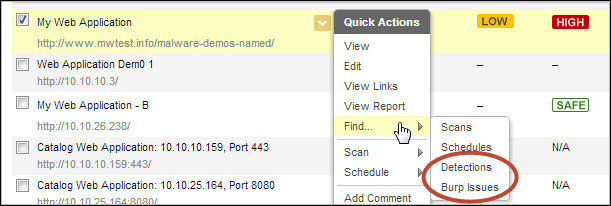
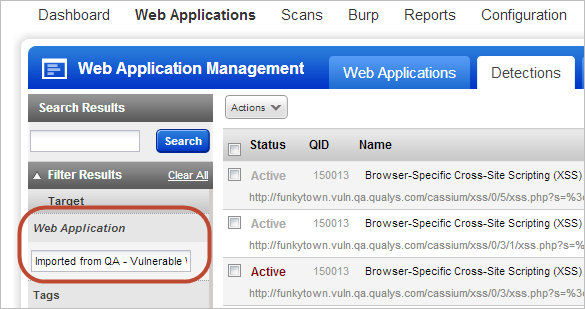
New Actions for Finding Detections and Burp Issues for a Web Application: Now you can easily find detections and Burp issues related to your web applications. We’ve added new actions to find the related security issues for a selected web application. This makes it easy to see the current vulnerabilities for a web application without having to run a report.
We’ll display detections or issues filtered for the web application you selected.
Catalog Entry Status Update: We’ve improved the catalog list to account for deleted web applications that were created from catalog entries. When you delete a web application that was created from a catalog entry, we automatically change that catalog entry’s status from “In Subscription” to “New”. This enables you to add this web application back into the subscription if needed at a later time.
Scanning Enhancements
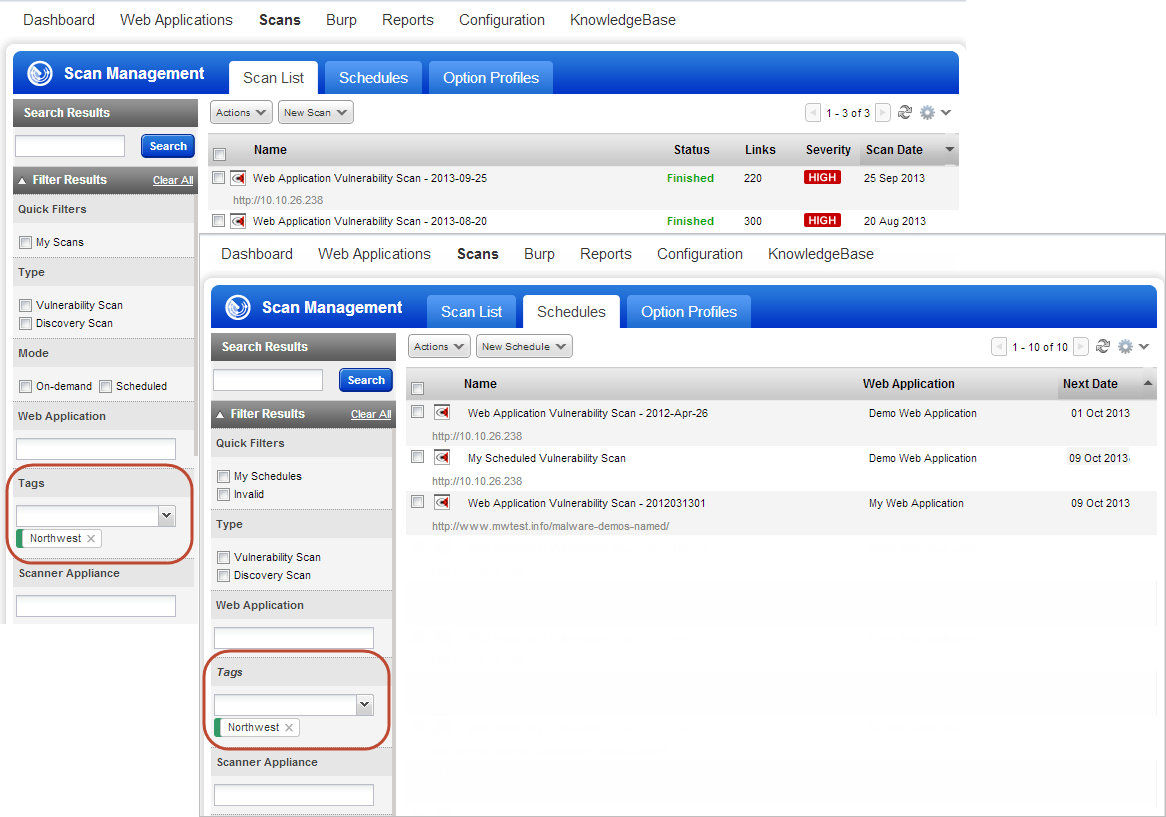
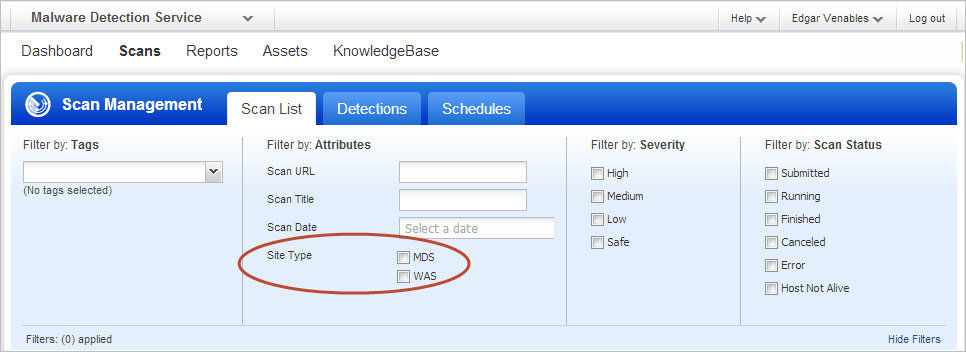
Filter Scans and Schedules by Tags: You can now filter scans and schedules by selecting tags, making it easy to find just the scans and schedules you need. When using this filter the list will display scans or schedules only for web applications that are assigned the selected tags.
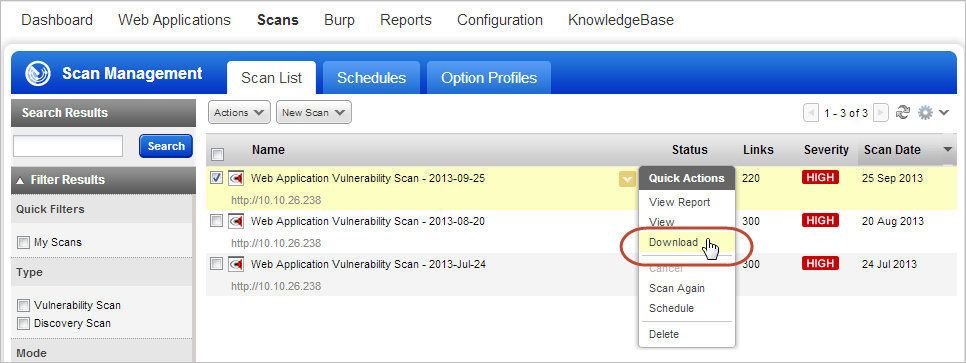
New Option to Download Scan Results in XML: We’ve added the option to download scan results in XML format from the scans list. This is a quick way to get XML scan results that can be used with our WAF integration parters including Citrix Netscaler, Imperva SecureSphere and the F5 ASM.
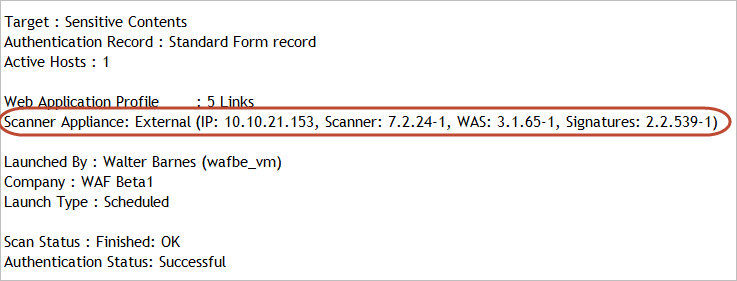
Scan Complete Notification Email Lists Appliance IP: We’ve updated the scan complete notification email to include the IP address of the scanner appliance used for the scan, making it easier to troubleshoot if there were issues with the scan, or to whitelist the source IP as needed.
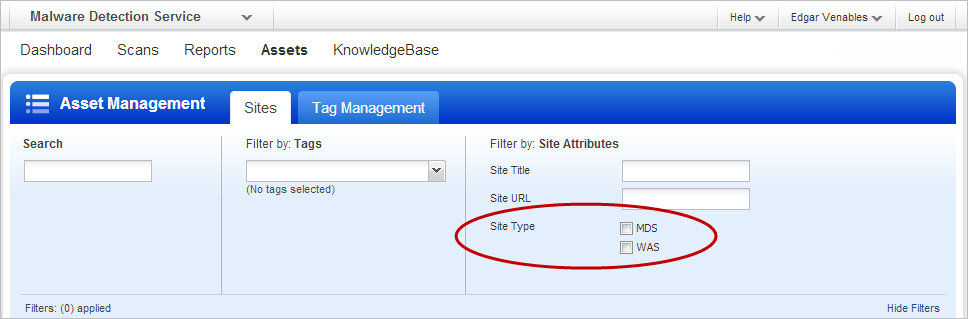
Filter Target Sites for Malware Monitoring in MDS: In the MDS application we’ve added site typefilters to the site list, scan list and schedule list. You can easily filtereach of these lists to show sites in your WAS application being monitored formalware, or sites that are being monitored for malware only.
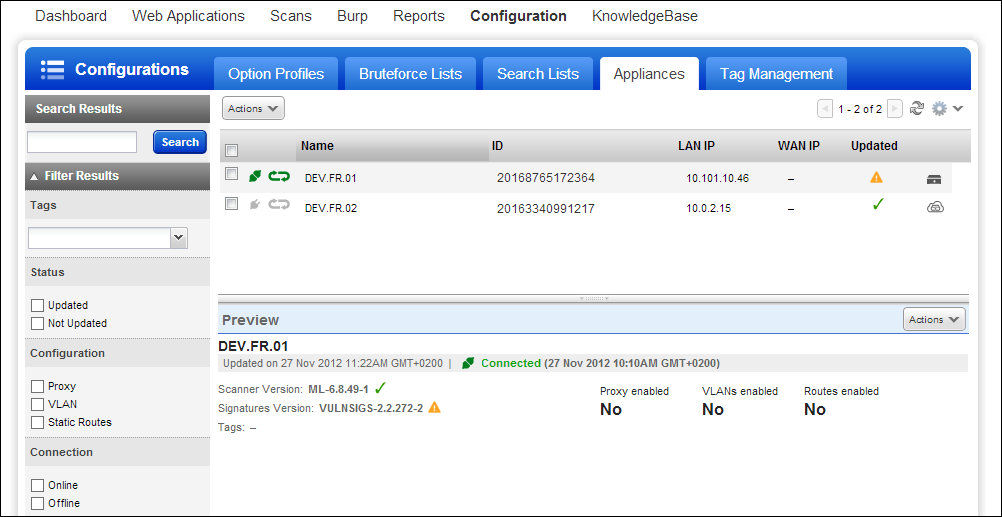
Enhancements to the Appliances List: The Appliances section now includes information about your virtual appliances in addtion to physical appliances.
Report Enhancements
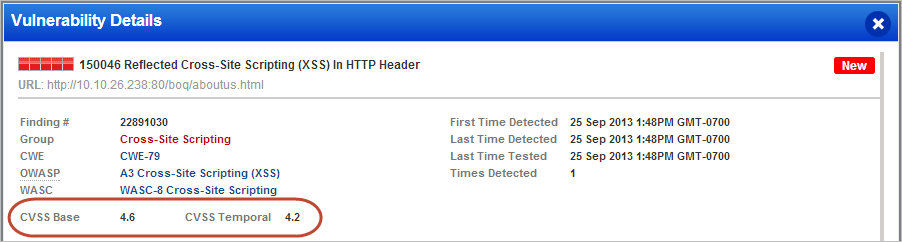
Added CVSS Scores to Scan and Web Application Reports: We’ve added CVSS Base and Temporal scores to the details displayed for vulnerabilities and sensitive content in scan and web application reports. This information is also included when viewing details from the detections list.
Web Application Details are Now included in XML and CSV Scan Reports: The XML and CSV output for downloaded web application reports and scan reports now shows web application settings in the Appendix section.
Example XML:
<APPENDIX>
<SCAN_LIST>
<SCAN>
<NAME><![CDATA[Vulnerability Scan -2013-Jul-24]]></NAME>
<REFERENCE>was/1374730201067.1096086</REFERENCE>
<START_DATE>2013-07-25T05:30:01Z</START_DATE>
<END_DATE>2013-07-25T05:53:31Z</END_DATE>
<MODE>Vulnerability</MODE>
<TYPE>Scheduled</TYPE>
<WEB_APPLICATION><![CDATA[Demo WebApplication]]></WEB_APPLICATION>
<AUTHENTICATION_RECORD><![CDATA[MyAuthentication Record
(ID=3904,Demo WebApplication)]]></AUTHENTICATION_RECORD>
<PROFILE><![CDATA[Initial WAS Options]]></PROFILE>
<SCANNER>External (IP:10.10.21.134, Scanner: 7.1.12-1,
WAS: 3.0.38-1, Signatures:2.2.492-1)</SCANNER>
<STATUS>Finished</STATUS>
<AUTHENTICATION_STATUS>Successful</AUTHENTICATION_STATUS>
</SCAN>
</SCAN_LIST>
<WEBAPP>
<ID>872172</ID>
<NAME><![CDATA[Demo WebApplication]]></NAME>
<URL><![CDATA[http://10.10.26.238]]></URL>
<OWNER>Edgar Venables(regen_ev)</OWNER>
<OPERATING_SYSTEM><![CDATA[Linux 2.4-2.6 / Embedded Device
/ F5Networks Big-IP]]></OPERATING_SYSTEM>
<SCOPE>Limit to URLhostname</SCOPE>
</WEBAPP>
</APPENDIX>
WAS Reports in XML – Findings are now Base64 Encoded:
Findings in all WAS reports in XML format are Base64 encoded. Findings include vulnerability detections, information gathered and sensitive content. If you have clients that consume XML content returned by the WAS application (using the API or UI), please update your clients so that WAS findings data is processed accurately.
Base64 encoded data usually will have the attribute set to“base64=true”. For example:
<FINDING>
<PAYLOAD><![CDATA[uid=%00%3Cscript%3E_q%3Drandom(X157105156Y1Z)%3C%2Fscript%3E]]></PAYLOAD>
<RESULTbase64="true"><![CDATA[Cl9mZWVkKCgKCgpbCiI=]]></RESULT>
</FINDING>
If the “base64=true attribute” is not set, the value will bein plain text. For example:
<FINDING>
<PAYLOAD><![CDATA[uid=%00%3Cscript%3E_q%3Drandom(X157105156Y1Z)%3C%2Fscript%3E]]></PAYLOAD>
<RESULT><![CDATA[_feed(("]]></RESULT>
</FINDING>
Reports that were updated
Findings shown in these WAS reports are now Base64 encoded:
- WAS v2 and v3 Scan Results
- Web Application Report
- Web Application Scan Report
Release Schedule
For details about the release dates and to subscribe to release notifications by email, please see the following:
- US Platform 1
- US Platform 2
- EU Platform
- API notifications (for all platforms)