Detect NTP Amplification Flaws
Update 2: Cloudflare just published an interesting piece on the latest attack that they have been exposed to, which peaked at 400 Gbps. It is amazing that only 4529 NTP servers can generate 400 Gbps traffic. It that sense NTP is a better amplifier than DNS, where 30,956 servers were needed for a 300 Gbps attack. Paul Vixie from Farsight Security explains how to solve the problem at least theoretically, but he believes the incentives to do it are just not there as the owners of the network are not directly affected. He dealt with a similar issue with DNS, but decided instead to adapt BIND to recognize reflection attacks. It is not the "right" solution, but the most practical…
Update: Animesh Jain from our Vulnerability Research Team has published a technical post with more in depth information on the probing mechanism and indicators used to implement this specific detection. Excellent insight into the inner workings of a remote detection.
Original: Symantec recently reported on the increasing use of the NTP (Network Time Protocol) in Denial of Service attacks. Over Christmas of 2013, servers for a number of gaming sites were taken down in NTP DoS attacks, including the popular Battle.net, League of Legends and Steam. Now regardless of whether you care about online gaming, this attack might affect you, as the hackers might have involved your servers in the attack.
In a Denial of Service attack, the hacker typically floods the target machine or service with too many requests for the service to handle, in essence exhausting the processing capacity of the servers, or simply generates so much traffic that the network connection of the service is overwhelmed. In either case the result is the same: the service becomes unresponsive and its users are prevented from logging in and accessing the system.
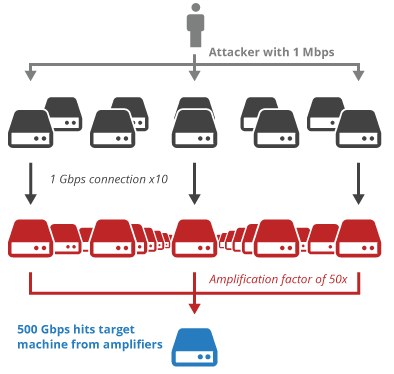
To make these attacks work even against well connected systems, the hacker needs to use many machines to generate enough request or traffic. Often a botnet with thousands of computers is necessary to generate the traffic directly, however, there is also another attack style that generates the traffic indirectly – the so called reflection attack. In a reflection attack, the hacker enlists vulnerable or misconfigured machines on the internet to generate the traffic for the attack. For example in a Domain Name System (DNS) reflection attack, the hacker sends a DNS request to a DNS server on the Internet, but includes as the source IP address for the request the address of the service to attack. This way, the response to the DNS request, which is typically 10x larger than the request, gets sent to the targeted service and clogs its network with useless data. BTW, this only works because DNS uses UDP, a sessionless protocol where source addresses can be spoofed.
Fig 1: Amplification attack as illustrated on the Cloudflare blog
DNS is not the only protocol that can be abused that way. NTP has a similar flaw where a short request of 200+ bytes can generate a response of several kilobytes, amplifying the request by a factor of 100-200! The problem lies in the “monlist” command of the NTP protocol, which is useful for troubleshooting, but not really needed in day-to-day use of NTP. Unfortunately, it is enabled by default in most NTP installations (maybe even in yours) and was used by the attackers over the Christmas holiday to attack the mentioned gaming servers.
The flaw in NTP has been assigned CVE-2013-5211 and the US-CERT has sent out alert TA14-013A “NTP Amplification Attacks Using CVE-2013-5211” informing of the patched NTP server in version 4.2.7 for all major operating systems.
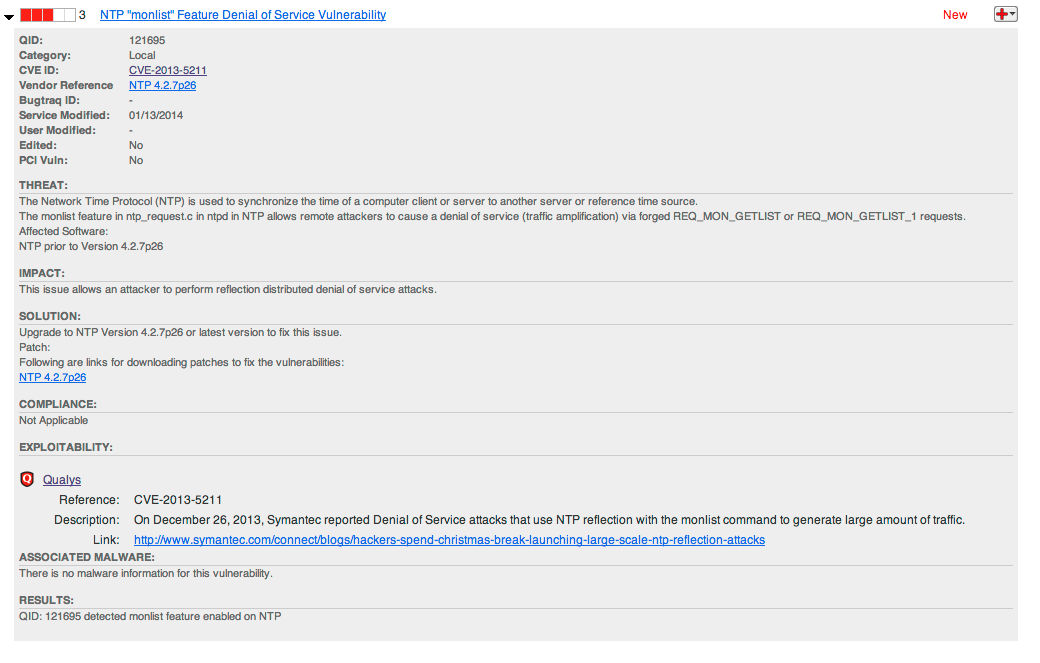
You can use QualysGuard to verify if your servers can be abused in the described way. Scan your Internet facing machines with QualysGuard and look for QID 121695 “NTP monlist Feature Denial of Service Vulnerability” in your scan results. The detection is remote, i.e. the scan does not need to be authenticated. If you find your servers to be vulnerable, please update or implement the work-around described in the US-CERT advisory, disabling the monlist command – you are making the Internet a safer and better working place for all of us.
The Open NTP Project is also be a handy resource, as you can plug your external IP addresses and search through their database of affected machines.
Happy scanning for QID 121695 and let me know your results.
Fig 2: 121695 detected on a Qualys demo machine