Deploy Virtual Patches on Qualys WAF Based on Detected Web App Vulnerabilities

In this blog post I’ll dive into how the new features in Qualys WAF help security professionals protect their web apps from attack.
Virtual Patching
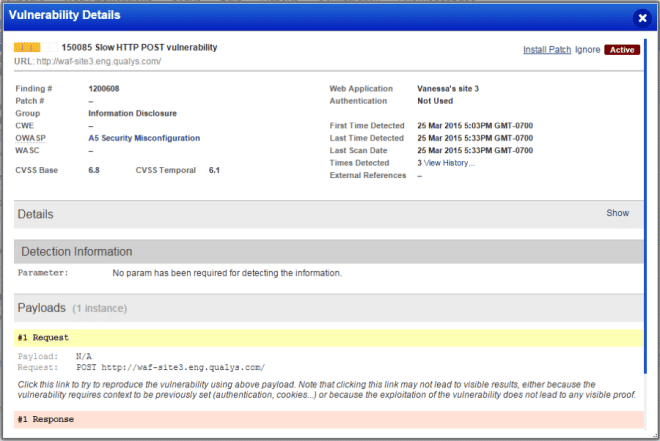
Virtual patching provides users the ability to quickly and accurately deploy custom WAF rules based on vulnerabilities detected in web apps by the Qualys WAS service. This functionality is incredibly simple; the user only needs to look at the vulnerabilities detected via WAS, find a vulnerability they would like to mitigate, and click "Install Patch." The Qualys Platform will then automatically deploy a WAF rule to block any exploit attempts of this particular vulnerability. To make this work, Qualys is adding a definition into each WAS detection that defines how Qualys WAF protects for that detected vulnerability. The initial release provides comprehensive coverage of high severity vulnerabilities, and the set of WAF rules that can be created from associated WAS detections will continue to evolve and grow.
Figure 1: Virtual Patch Deployment
Extended Protection
Virtual Patching complements existing WAF functionality with protection that is specific to your domain. Qualys WAF already provides easy-to-use sliders that allow you to define protection levels for notifications and for blocking access. Virtual patching allows you to fine-tune your protections without making large-scale changes to existing security policies. As virtual patches are created directly from a known vulnerability, this approach allows you to roll out a comprehensive set of protections while minimizing false positives – giving you more confidence to deploy blocking in your WAF.
Protection While You Fix Your Web Apps
Deploying virtual patches in this way becomes incredibly powerful when we begin to think about the software deployment lifecycle. Try though we might, it is inevitable that a development team will inadvertently introduce a defect into production – for instance, an unsanitized form input that makes an application vulnerable to a SQL injection (SQLi) attack. While WAF will typically detect and block the exploit for this particular vulnerability, applying a virtual patch directly from the vulnerability lets you not only guarantee that a future exploit of that particular form field will be blocked, but also greatly narrow the scope of the blocking rule; in this case, you may want to block only SQLi to the form field in question. Applying a blocking rule in this way helps limit the risk of a customer-impacting false positive while also ensuring protection of the application during the time the engineering team needs to develop and deploy the fix for the application defect.
Protection at Scale
In addition to the efficiency of deploying virtual patches in this way, the Qualys platform lets these patches be deployed quickly at great scale. Assume for a moment that the application mentioned above is deployed on global scale, in six different data centers in four different countries. Leveraging the Qualys Platform, a user would need only deploy a single virtual patch, and the platform will automatically roll out protection to all six data centers, regardless of how many WAF appliances are in place… and all in less than 90 seconds.
Customizable Event Response
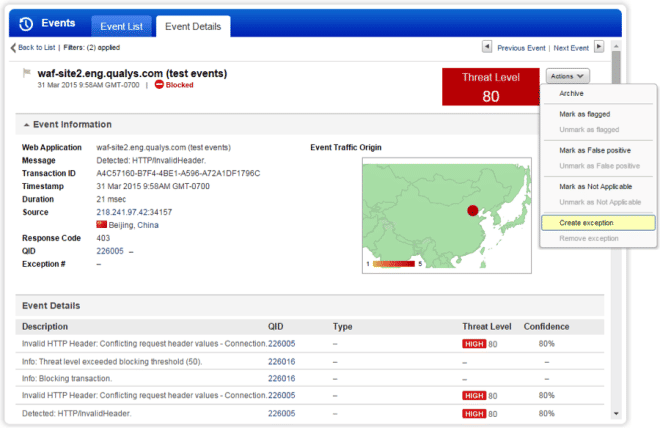
While virtual patching extends Qualys WAF via integration with Qualys WAS, Customizable Event Response adds functionality and control to your reporting of security events. In some events, apparently malicious payloads may be detected by a WAF appliance which are either unimportant or "false positive" in an individual application environment. A robust event management tool like that included in Qualys WAF 2.0 allows the user to quickly and flexibly respond to security events where they would like to see a different response in the future. Simply choose a security event from the "Events" screen in the Portal and mark it for Exception.
Figure 2: Customized Event Response Configuration
The Qualys Platform will then deploy a WAF rule to whitelist that particular event with as narrow a scope as possible – if, for example, an event depicts an exploit of a single form field or parameter, the exception rule will be created to only cover that exact exploit on that exact parameter – thus minimizing the noise of unimportant events while also ensuring that the applied WAF protections maintain a high level of security and a minimal false negative rate.
Availability and Resources
Qualys WAF 2.0 is available now. Sign up now for a free trial.
Additional resources are available: