Are Your Vendors, Partners and Other Business Allies Putting Your Organization at Risk?
Qualys SAQ Automates the Process of Assessing Your Third Parties’ Security Posture
How compliant are vendors and other third parties with information security standards, your organization’s internal policies and government regulations? Making these assessments has never been easy, but it’s getting increasingly complicated, and the stakes are getting higher. While your organization may have gone to great lengths to secure its IT infrastructure, networks and assets, the vendors and other third parties with remote access to your systems and data can make you vulnerable to breaches.
The Risk From Your Network of Trusted Third Parties Is Real and Significant
How aware are you of the security policies, processes and practices of your suppliers, consultants, service providers and partners? If they’re careless, lax or inept with regards to security and compliance, you need to be proactive and find out, because they could be a conduit for attacks against your organization.
The threat is real. Many companies have had their data and systems compromised after business associates with access to their IT infrastructure got hacked. One example was 2013’s massive Target data breach. In that case, hackers stole login credentials to a Target billing system from one of the company’s contractors. The data cyber thieves then proceeded to plunder personal and credit card information from tens of millions of customers. In another high-profile incident, hackers last year stole 15 million T-Mobile customer records stored on a server belonging to Experian, which was providing credit check services to T-Mobile.
These Are Not Your Father’s Risk Assessments
These business-process control assessments are conducted via surveys and they evaluate critical areas of an organization such as its business continuity plans, physical and environmental security tools and practices, operational risk safeguards and human resources procedures.
Surveying your third parties is more complicated today than it was in the past. There are more rules and policies, courtesy of regulators, industry groups and your own internal corporate governance and policy watchdogs. And these rules aren’t getting simpler: They require deeper, more detailed and longer surveys to be able to evaluate levels of compliance.
Moreover, the universe of people you must poll — both inside your organization and outside — is becoming larger and more geographically dispersed. This trend is driven in part by an increase in outsourcing, as companies seek to reduce operating costs and focus on core competencies.
In addition, as business becomes increasingly digital, organizations find themselves having to give more and more third parties access to their IT systems.
You Must Automate These Third-Party Polls
The traditional way of conducting these third-party risk assessment surveys — emailing questionnaires and tracking responses on a spreadsheet — no longer cuts it.
This manual process of distributing surveys, collecting answers and aggregating results doesn’t scale. It’s extremely labor-intensive, costly and time-consuming, and highly prone to errors.
Qualys’ new Security Assessment Questionnaire (SAQ) automates and streamlines this entire life cycle, including survey design, response monitoring, data aggregation and report generation. The cloud-based SAQ frees risk assessment administrators from tedious manual tasks, ensures unparalleled accuracy and speeds up campaigns. With SAQ, an organization can quickly and precisely identify security and compliance gaps among third parties, as well as internally among its business units and employees.
Although it can be used as a standalone application, SAQ is also part of the Qualys Cloud Suite of security and compliance solutions, which lets you protect all your IT assets wherever they reside. Because it is built upon the Qualys Cloud Platform, SAQ lets users automate these risk assessments at scale, meeting the requirements of even the largest organizations. The tight control SAQ gives to organizations over their third-party risk assessments lets them protect themselves from partners with lax or negligent security practices.
How SAQ Helps You Orchestrate Security Assessments and Compliance Audits
SAQ simplifies the design, distribution, tracking and management of multiple internal and external risk assessment surveys from a web-based central console. No more emailed surveys and manual aggregation of results in spreadsheets: SAQ automates campaign creation, questionnaire distribution and result analysis.
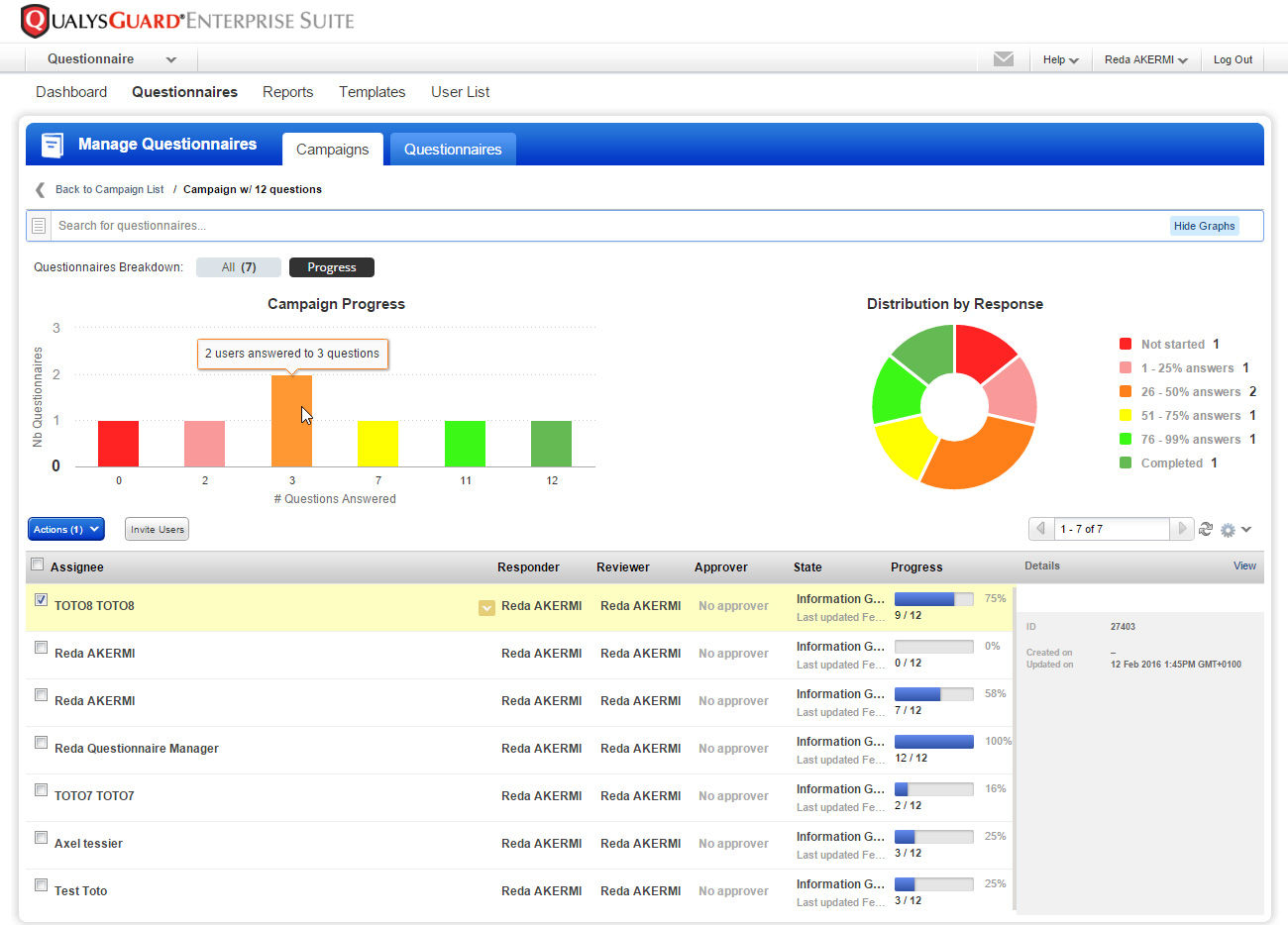
Design Surveys and Track Campaigns
SAQ’s wizard walks users through the creation of campaigns. Organizations can launch campaigns with pre-set due dates and notifications. They can assign reviewers and approvers to ensure accuracy of responses.
Questions can have various types of answer formats, such as multiple-choice check boxes, drop-down menus and open-ended text boxes. Survey designers can also require that evidence files be attached to certain answers.
The SAQ template library helps campaign administrators get started with pre-configured surveys for common regulations like HIPAA, Basel 3 and SOX, and industry standards like PCI. These predefined templates are prepared by security and risk experts and are always current on compliance requirements. Administrators can also craft their own templates and individual surveys with SAQ’s drag-and-drop Template Builder feature.
SAQ also gives organizations flexibility for designing campaigns with varying workflows. For example, a survey can be considered finalized once it’s been completed, or additional steps can be required, such as an expert’s review and a supervisor’s approval.
Distribute Questionnaires
SAQ eliminates the need to set up user accounts. You enter or select vendor emails and SAQ auto-provisions the surveys. Respondents can complete surveys on browser-based forms, and delegate questions they can’t answer. As deadlines approach, administrators are able to trigger reminder emails to respondents. Organizations can also set up recurring campaigns that need to be run with a specific frequency.
Track Campaigns and Analyze Results
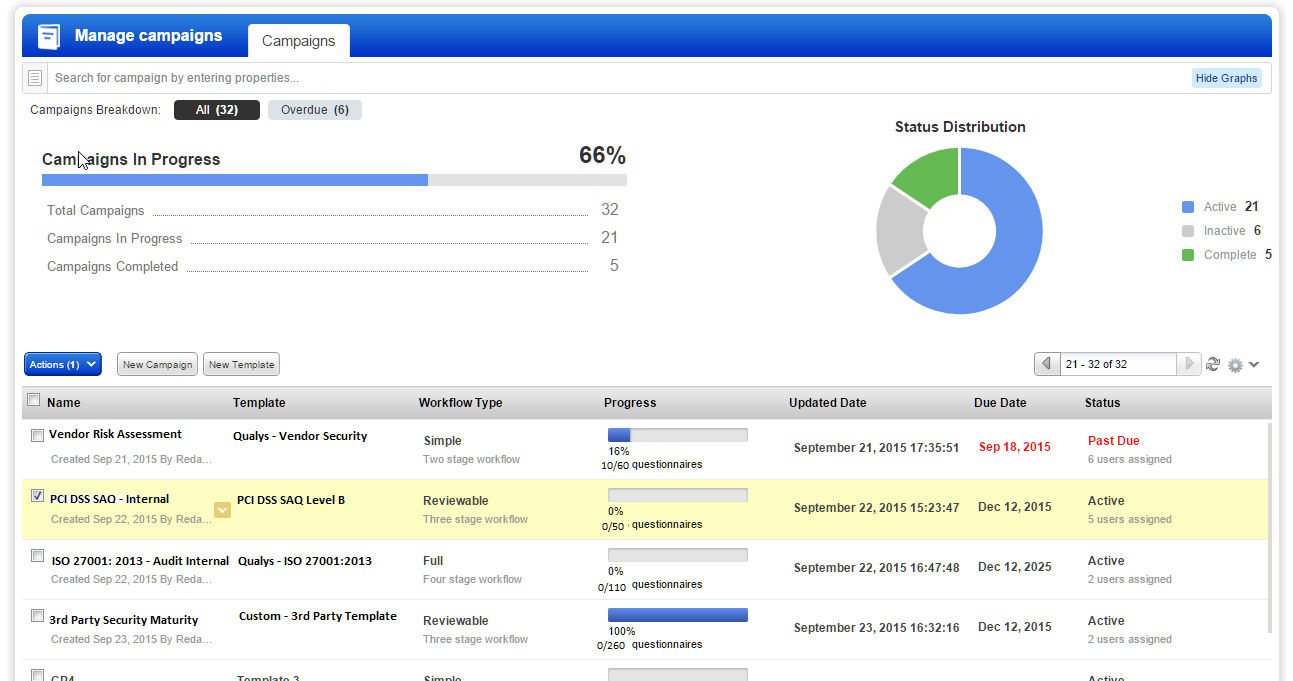 SAQ captures responses in real time and aggregates them in one place, so administrators can literally watch as questions are answered and track the progress of campaigns.
SAQ captures responses in real time and aggregates them in one place, so administrators can literally watch as questions are answered and track the progress of campaigns.
To help administrators further visualize campaign progress, SAQ displays charts that are updated live, and lets users drill down to see details down to individual respondent surveys. As such, SAQ helps administrators flag questionnaires that respondents may be having trouble understanding and that may need to be revised.
Campaign results can be sliced and diced using a variety of criteria, such as by vendor, recipient or specific questions. SAQ also generates proof of compliance with detailed reports.
SAQ also caters to a variety of users, including upper management via executive-level dashboards, as well as auditors and compliance officers with more granular views of the data. Users can create custom dashboards designed to reflect the risk and compliance postures of specific third parties. From the central console, administrators can track and manage simultaneously multiple campaigns at different stages of completion.
Excel at Your Security Assessments Without EXCEL Spreadsheets
Qualys SAQ is a self-contained, turnkey solution requiring no other tools or surveys, and it’s easy to use. It lets you get answers fast from your third parties so you can manage the risk of giving them access to your IT systems and protect your business.
Start your free trial today and see how SAQ can fine-tune and streamline your security assessment campaigns.
Register for our webcast with SANS Senior Analyst John Pescatore, “Automating CIS Critical Security Controls for Threat Remediation and Enhanced Compliance“.