Qualys WAF 2.0 Protects Against Critical Apache Struts Jakarta Vulnerability ( CVE-2017-5638 )
On March 8, 2017, Qualys published a detailed blog to describe a critical vulnerability in Apache Struts2 Jakarta multipart parser that exposes vulnerable applications to Remote Command Execution attacks. Exploits of this vulnerability can allow attackers to steal critical data or take control of your application servers.
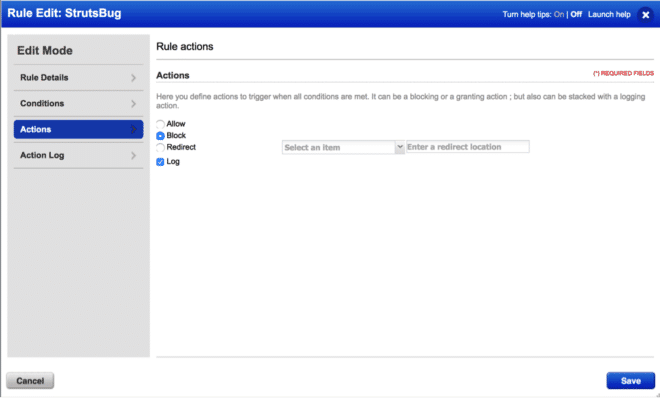
Qualys Web Application Firewall (WAF) 2.0 allows you to create custom security rules to detect and block attacks that try to exploit this vulnerability.
Since this vulnerability is triggered by invalid values in the Content-Type header for multipart HTTP requests, a simple custom rule could use the following conditions:
request.path EQUAL “/struts2-showcase/index.action”
request.header “Content-Type” NOT.EQUAL “multipart/form-data”
The above custom rule will detect and block requests that contain invalid Content-Type header values for a specific URL that accepts multipart requests.
We understand that each application is unique. Custom rules are very flexible and allow you to use various attributes of HTTP requests, clients, servers and transactions to detect attacks. Other possibilities for blocking this vulnerability are:
- Exploits disclosed so far indicate that the vulnerability can be triggered by specific patterns of Content-Type values. Such invalid Content-Type values be detected by a custom rule:
request.header “Content-Type” MATCH “^.*(%|\$){.*”
Keep in mind that other attack patterns might exist, so whitelisting of allowed content types is expected to be more effective than blacklisting. - Use regular expressions to whitelist all allowed Content-Type values in a custom rule:
request.header.content-type NOT.MATCH “multipart\/form\-data|content\-type2|content\-type3”
Whitelisting and blacklisting of content types can also be done in the HTTP Profiles of the Qualys WAF security configuration.
As you can see, a wide variety of custom rule conditions can be used to meet the specific security needs of your application.

For comprehensive protection, Qualys advises you to upgrade to Struts versions 2.3.32 or 2.5.10.1.
If you would like to learn more about custom rules and other security features of the Qualys WAF 2.0, please contact your Qualys Technical Account Manager or register for a free trial. Additional documentation is available on the Qualys WAF community and the Qualys website. If you are already using Qualys WAF, please contact Qualys Support with any questions you have.
Sebastien Poirier, Security Engineer on the Qualys WAF team, contributed to this article.
How about JSTL expressions ?
JSTL expressions of format ${expression} can trigger the vulnerability also. To include such patterns, you can use a regex such as “^.*(%|\$){.*”. As noted in the post, do consider only allowing valid content types for your website. Thanks for the comment.
What if I don’t have a WAF ? :)…
You might have seen this already, but Apache Security Bulletin recommends two workarounds: implement a Servlet filter to validate Content-Type or to remove the File Upload Interceptor from your stack. Please see link: https://cwiki.apache.org/confluence/display/WW/S2-045. Upgrading to Struts 2.3.32 or 2.5.10.1 is of course the ultimate solution.
whitelist-good, blacklist-bad, cause no catching up, like whack-a-mole, whitelist in app itself
I’m using Modsecurity. Can you help me create rules for modsecurity?
Many thank.
Hi Lee – Qualys WAF doesn’t use Modsecurity, so unfortunately can’t help there. But the general idea behind the rules would be the same, that is to check for invalid content in the headers. Worth checking the CRS for any existing rules around this.