New Adobe 0-Day Vulnerability – But Does It Matter ?
For the 2nd time in 2009 Adobe has to deal with a 0-day announcement. SecurityFocus BID 34736 has the exploit code, which should be straightforward for attackers to incorporate into their existing “outreach” mechanisms. Once again the JavaScript implementation in Adobe Reader is the culprit and Adobe officially recommends turning off JavaScript as a work-around, until a patch becomes available. While I expect that attacks will focus on the Windows platform, the vulnerability is truly cross-platform and affects Windows, Macs and Linux.
File format vulnerabilities of this kind represent a significant attack vector, but they continue to be neglected by IT administrators. Our ongoing analysis of the previous Adobe vulnerability APSA09-01 (released February 2009, patch available on March 10 as shown by the red line in the graph) shows no significant reduction in the number of exploitable machines.
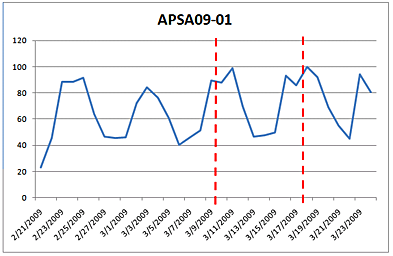
If this trend continues to persist for the Adobe Reader vulnerabilities, which it has in all 2008 and as demonstrated in Laws 2.0, attackers don’t need to rush anymore, they can take their time in figuring out the best way to get an infected PDF file into their victims.