Top 4 New Settings in Security Compliance Manager for Windows 8.1
Most organizations enforce system configuration policies to reduce the chance of misconfiguration and improve their overall security posture. For Microsoft Windows systems, many organizations rely on guidance from Microsoft Security Compliance Manager (SCM) for proper configuration. For organizations deploying Windows 8.1, this Top 4 list helps you understand and implement the new settings introduced in SCM for Windows 8.1.
As an engineer on the Qualys Policy Compliance product team, I routinely compare compliance benchmarks, and have compiled this list based on my work. If you are already familiar with previous version of Windows, this blog post can help you to quickly adopt the new changes.
1. Windows Defender
Windows Defender is your first line of defense against spyware, viruses and malicious software. It helps to identify and remove them. On Windows 8 and above, it runs in the background and notifies when some action is needed from the user.
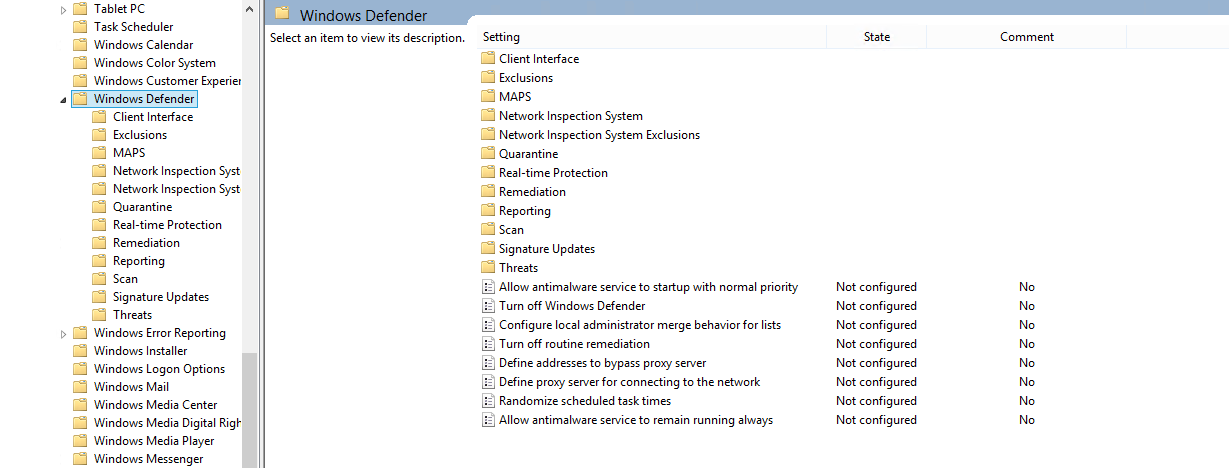
In Windows 8.1, Microsoft has introduced more options related to scanning, reporting, real-time protection and many more in Windows Defender. Of the over 90 settings in Windows Defender, the following are the most important ones you should enable if Windows Defender is the only anti-malware present on the target system.
- Turn on behavior monitoring
- Scan removable drives
- Scan packed executables
- Scan all downloaded files and attachments
- Check for the latest virus and spyware definitions before running a scheduled scan
2. Local Security Authority (LSA) Protection
LSA is a process to prevent code injection that could compromise credentials. LSA, which also includes the Local Security Authority Server Service (LSASS) process, validates users for local and remote sign-ins and enforces local security policies.
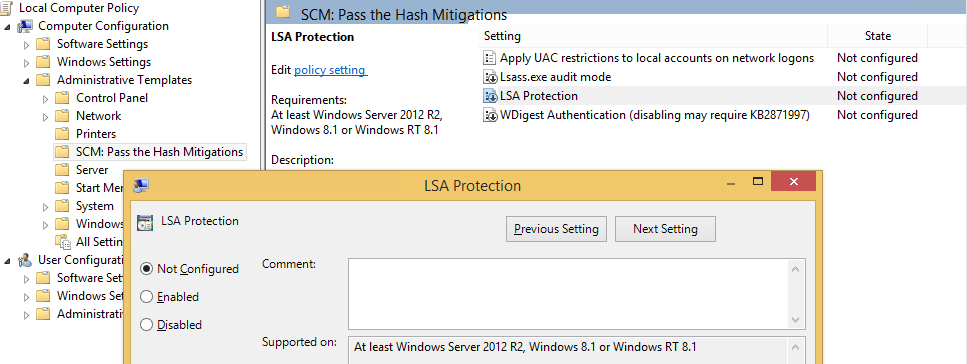
It is recommended to enable the protected process settings in Windows 8.1 (although they are not available in Windows RT 8.1). These settings improve protection for credentials stored and managed by LSA by preventing memory reads and code injection by non-protected processes. Additional protection is achieved when this process is used along with Secure Boot. Protected process requirements for plug-ins and drivers to load in LSA are:
- Signature Verification –
- The plug-in that is loaded in LSA needs to be digitally signed with Microsoft signature.
- Plug-ins that are drives, such as smart card drivers, need to be digitally signed by using WHQL certification.
- Plug-ins that are not signed will fail to load in LSA
- Plug-ins should be compliant with SDL process guidelines otherwise plug-ins digitally signed with Microsoft signature but are non-compliant will may result in failing them to load in LSA.
Enable audit mode of lsass.exe using the below steps:
- Open registry path “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\LSASS.exe”
- Set key to Auditlevel=dword:00000008
- Now reboot the computer
After reboot you can check event 3065 and 3066 to determine if the plug-in and driver are loaded in LSA.
Event 3065: This event records that a code integrity check determined that a process (usually lsass.exe) attempted to load a particular driver that did not meet the security requirements for Shared Sections. However, due to the system policy that is set, the image was allowed to load.
Event 3066: This event records that a code integrity check determined that a process (usually lsass.exe) attempted to load a particular driver that did not meet the Microsoft signing level requirements. However, due to the system policy that is set, the image was allowed to load.
These events will not be generated when the kernel debugger is attached and enabled on the system.
Audit mode can be enabled for multiple computers in a domain, by modifying HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\LSASS.exe registry key.
Note – For the GPO to take effect when the audit level value setting is created in the Group Policy Object (GPO), the GPO changes must be replicated to all domain controllers.
More information related to LSA is available here: https://technet.microsoft.com/en-us/library/dn408187.aspx
3. Enhanced Mitigation Experience Toolkit (EMET)
EMET 5.1 is a new toolkit for system administrators, and is compatible with Windows 7 onwards and designed to secure Windows targets against attacks. Much software today is vulnerable in a way that normal users typically cannot see or detect, which creates opportunities for attackers to exploit the target either for data collection or denial of service. EMET is effective in detecting and blocking attack techniques and common actions used to exploit memory corruption-related vulnerabilities.
Once you install EMET you can configure it either through EMET user interface or through the group policy editor. Here are some setting recommendations using the group policy editor.
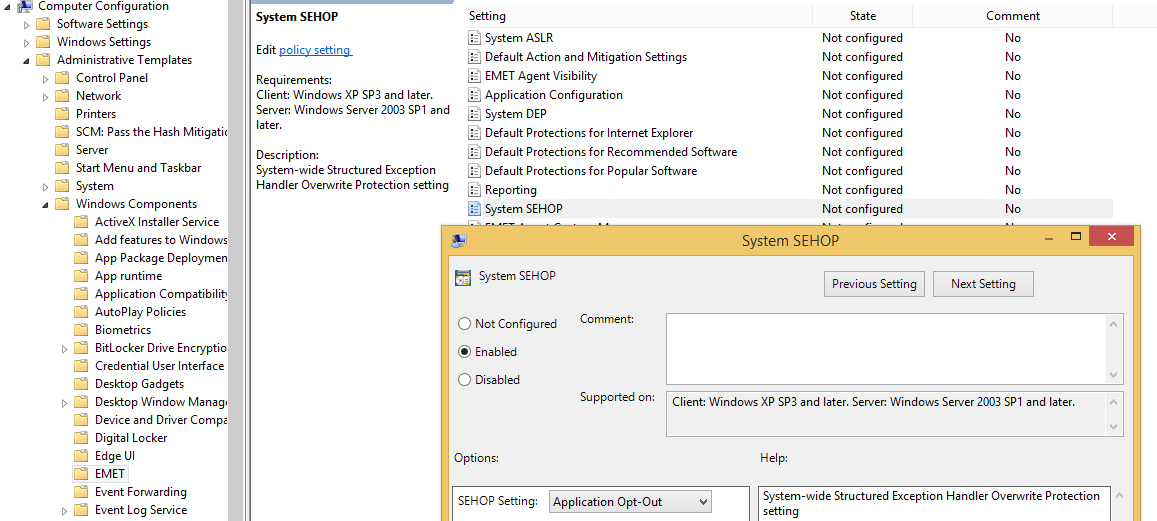
Recommendation 1: Enable System SEHOP settings. When software suffers from memory corruption vulnerabilities, an exploit may be able to overwrite a data structure that controls how the software handles exceptions. Structured Exception Handler Overwrite Protection (SEHOP) verifies the integrity of those structures before they use the handle. Keep this setting to “Enable: Application Opt-Out”.
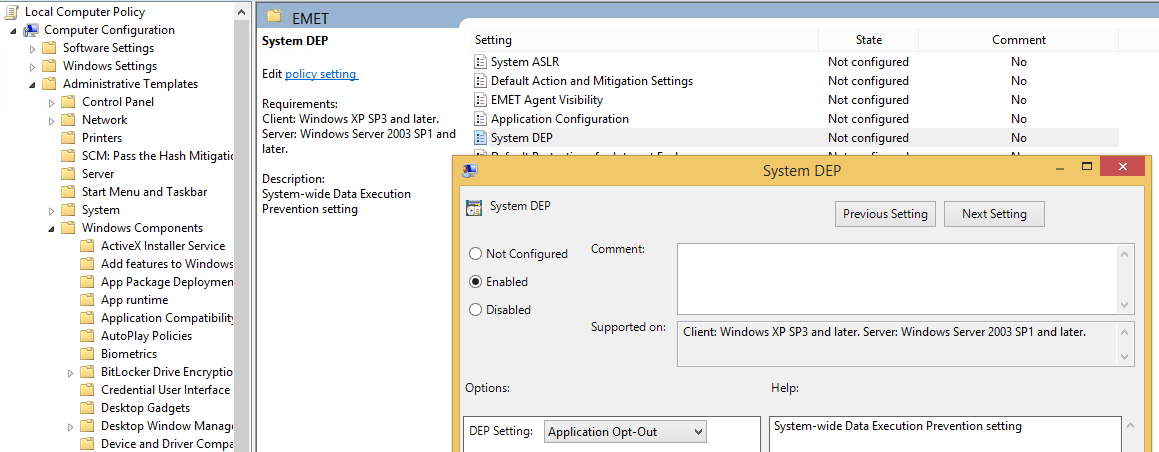
Recommendation 2: Enable System DEP setting. Data Execution Protection (DEP) is used to prevent the execution of code from memory pages that are not explicitly marked as executable, but this flag typically needs to be set while compiling the binary. The “System DEP” setting through EMET also prevents execution of code not explicitly marked as executable, even when the flag was not set at compile time. Set it to “Enable: Application Opt – Out”.
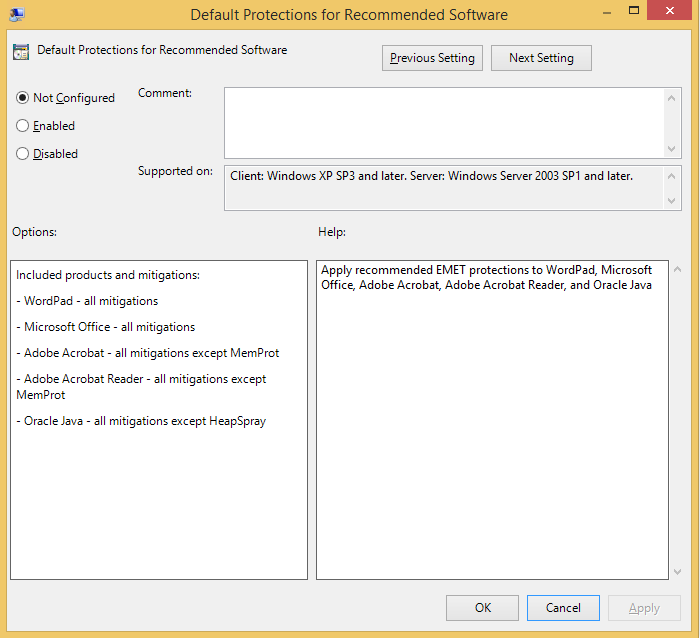
Recommendation 3: Microsoft allows you to specify that applicable EMET protections be applied to two sets of software: recommended software and popular software. Enabling default protections for these two sets of software improves the security to your machine.
Popular software includes browsers, PDF readers, compression tools, video players and Internet Messenger.
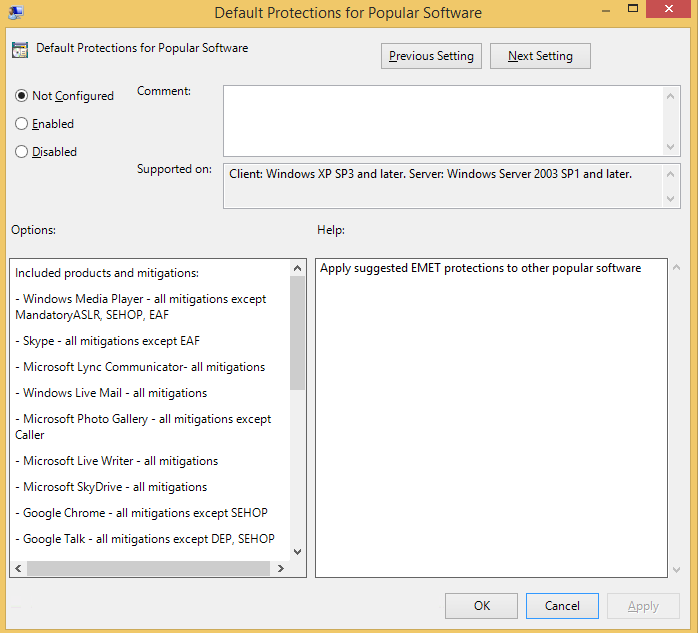
The set of recommended software includes Adobe reader, Microsoft Office and WordPad.
4. Miscellaneous Settings
In addition to the critical new SCM settings for Windows 8.1 above, organizations should also refer to some of the settings below:
- Restrict delegation of credentials to remote servers.
When running in restricted mode, participating apps do not expose credentials to remote computers. You should note, however, that restricted mode may limit access to resources. - Automatically send memory dumps for OS-generated error reports.
This policy setting controls whether memory dumps in support of OS-generated error reports can be sent to Microsoft automatically. This policy does not apply to error reports generated by 3rd-party products, or additional data other than memory dumps. - Set what information is shared in Search.
It is recommended to set to Not Configured or Disabled, depending on organization policy, to avoid leakage of user information and location to Bing search. - Configure Group Policy Caching.
If you enable or do not configure this setting, the Group Policy will cache the policy information after every background processing session. This minimizes bandwidth usage as it just checks the link speed and does not download the latest version of policy information. If this setting is disabled the Group Policy client will not cache applicable GPOs or settings.
Configuration, compliance and ultimately improving your organization’s security posture can be a daunting task. But with the help of pre-built compliance benchmarks and tools, this goal can be achieved successfully and with a reasonable effort.