Solorigate/Sunburst : Theft of Cybersecurity Tools | FireEye Breach

Update Jan 5, 2021: New patching section with two new dashboard widgets showing the number of missing FireEye-related patches in your environment and the number of assets in your environment missing one of those patches.
Update Dec 23, 2020: Added a new section on compensating controls.
Update Dec 22, 2020: FireEye disclosed the theft of their Red Team assessment tools. Hackers now have an influential collection of new techniques to draw upon.
Using Qualys VMDR, the vulnerabilities for Solorigate/SUNBURST can be prioritized for the following Real-Time Threat Indicators (RTIs):
- Active Attacks
- Solorigate Sunburst (New RTI)

Original post: On December 8, 2020, FireEye disclosed theft of their Red Team assessment tools. These tools are used by FireEye to test and validate the security posture of their customers. According to FireEye, the hackers now have an influential collection of new techniques to draw upon. It is unclear today if the attackers intend to use the tools themselves or if they intend to release the tools publicly in some way.
“The attackers tailored their world-class capabilities specifically to target and attack FireEye. They are highly trained in operational security and executed with discipline and focus. They operated clandestinely, using methods that counter security tools and forensic examination,” said Kevin Mandia, CEO of FireEye. However, the stolen tools did not contain zero-day exploits.
In response to the breach, FireEye has provided Red Team tool countermeasures which are available on GitHub. These countermeasures include rules in multiple languages such as Snort, Yara, ClamAV and HXIOC. Since none of the leaked tools leverage zero-day attacks, FireEye also provided a listing of CVEs used by these tools.
An analysis of these tools shows that the functionality and capabilities may mimic some existing red team tools such as Metasploit or Cobalt Strike. Similar to how the Shadow Brokers leak led to outbreaks such as WannaCry, it is possible that this breach could lead to other commodity malware leveraging these capabilities. Any time there is high-fidelity threat intelligence such as the countermeasures provided by FireEye, it is important to look at it under the lens of how you can protect your organization going forward, as well as how you can validate if this has been used in your organization previously.
Mitigation & Protection
Snort is an open-source intrusion prevention system (IPS) which uses an open format for its rule structure. While many companies use the open-source version of Snort, commercial IPS tools are also able to leverage the Snort rule format. Most of these rules are tuned to specifically look for beacon traffic or components of remote access tools. If your organization is using an IPS or IDS, you should plug in these signatures to look for evidence of future exploitation.
ClamAV is an open-source antivirus engine which is now owned by Cisco. To prevent these tools from executing on the endpoint, the provided signatures can be imported into this AV engine or any other antivirus which uses the ClamAV engine.
Yara was designed by VirusTotal to help malware researchers both identify and classify malware samples. Yara can be used as a standalone scanning engine or built in to many endpoint security products as well. The provided rules can be imported into many endpoint security tools to match and block future execution of known malware.
Another important aspect for preventing the usage of these red teaming tools in your environment is to address the vulnerabilities they are known to exploit. There are 16 vulnerabilities which have been prioritized based on the CVSS score associated with them. Using a vulnerability management product such as Qualys VMDR, you can proactively search which endpoints or devices have these vulnerabilities and deploy patches or configuration fixes to resolve them before an adversary has a chance to exploit them.
Threat Hunting
Hunting for evidence of a breach is just as important as trying to prevent the breach. Two of the components FireEye released to help this search are HXIOC and Yara rules. These help define what triggers to look for to make the determination if the organization has been breached by these tools.
The HXIOC rules provided are based on the OpenIOC format originally created by Mandiant. These are similar to the STIX and CyBOX formats maintained by OASIS. The rules provided by FireEye call out many process names and associated command line arguments which can be used to hunt for the evidence of an attack.
By using the provided Yara rule which encompasses all of the Yara countermeasures, you can scan multiple directories using the standalone Yara engine by issuing the “yara -r all-rules.yara <path>”, where <path> is the location you want to recursively scan.
Alternatively, VirusTotal also has a useful API called RetroHunt which allows you to scan files submitted within the last 12 months. Florian Roth has gone through and submitted all of the provided Yara rules to RetroHunt and created a Google Sheets document containing all of the detections. In this document you can see valuable information such as the number of detections and file hashes for each of the detected samples.
Detect 16 Publicly Known Vulnerabilities using Qualys VMDR
Here is a prioritized list of CVEs published on Github by FireEye:
| CVE ID | Name | CVSS | Qualys QID(s) |
| CVE-2019-11510 | Pre-auth arbitrary file reading from Pulse Secure SSL VPNs | 10 | 38771 |
| CVE-2020-1472 | Microsoft Active Directory escalation of privileges | 10 | 91668 |
| CVE-2018-13379 | pre-auth arbitrary file reading from Fortinet Fortigate SSL VPN | 9.8 | 43702 |
| CVE-2018-15961 | RCE via Adobe ColdFusion (arbitrary file upload that can be used to upload a JSP web shell) | 9.8 | 371186 |
| CVE-2019-0604 | RCE for Microsoft Sharepoint | 9.8 | 110330 |
| CVE-2019-0708 | RCE of Windows Remote Desktop Services (RDS) | 9.8 | 91541, 91534 |
| CVE-2019-11580 | Atlassian Crowd Remote Code Execution | 9.8 | 13525 |
| CVE-2019-19781 | RCE of Citrix Application Delivery Controller and Citrix Gateway | 9.8 | 150273, 372305 |
| CVE-2020-10189 | RCE for ZoHo ManageEngine Desktop Central | 9.8 | 372442 |
| CVE-2014-1812 | Windows Local Privilege Escalation | 9 | 91148, 90951 |
| CVE-2019-3398 | Confluence Authenticated Remote Code Execution | 8.8 | 13475 |
| CVE-2020-0688 | Remote Command Execution in Microsoft Exchange | 8.8 | 50098 |
| CVE-2016-0167 | local privilege escalation on older versions of Microsoft Windows | 7.8 | 91204 |
| CVE-2017-11774 | RCE in Microsoft Outlook via crafted document execution (phishing) | 7.8 | 110306 |
| CVE-2018-8581 | Microsoft Exchange Server escalation of privileges | 7.4 | 53018 |
| CVE-2019-8394 | Arbitrary pre-auth file upload to ZoHo ManageEngine ServiceDesk Plus | 6.5 | 374547 |
Qualys released several remote and authenticated QIDs for CVEs published by FireEye. You can search for these QIDs in VMDR Dashboard by using the following QQL query:
vulnerabilities.vulnerability.qid: [38771, 91668, 43702, 371186, 110330, 91541, 91534, 13525, 150273, 372305, 372442, 91148, 90951, 13475, 50098, 91204, 110306, 53018, 374547]

Identify Vulnerable Assets using Qualys Threat Protection
In addition, Qualys customers can locate vulnerable host through Qualys Threat Protection by simply clicking on the impacted hosts. This helps in effectively identifying and tracking these vulnerabilities.

With VMDR Dashboard, you can track these 16 publicly known vulnerabilities, their impacted hosts, their status and overall management in real time. With trending enabled for dashboard widgets, you can keep track of these vulnerabilities trends in your environment using the FireEye Theft Top 16 CVEs & IOC Hashes dashboard.
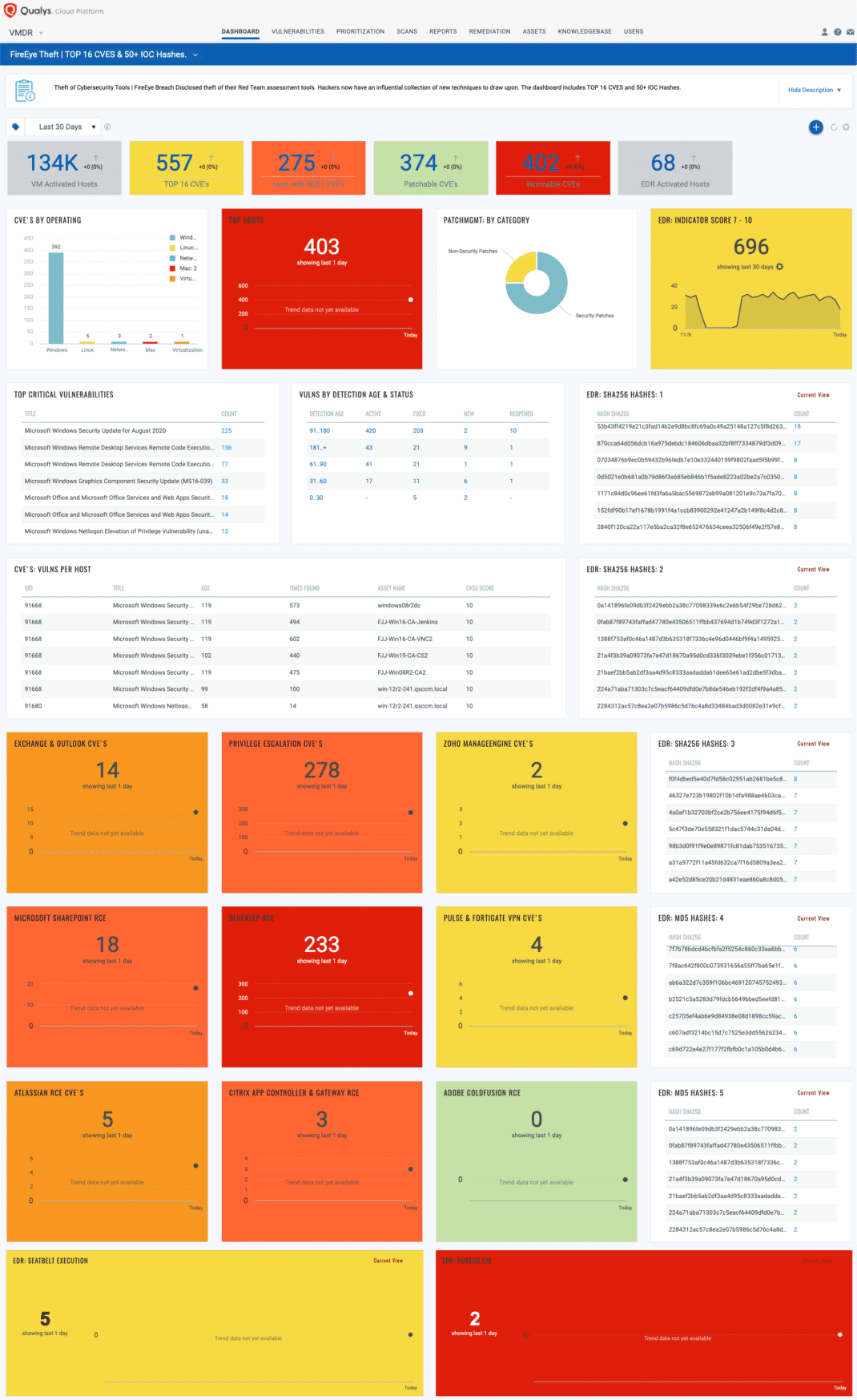
Compensating Controls for Reducing Risk of Vulnerabilities Leveraged by FireEye Red Team Tools
To reduce the overall security risk, it is important to address misconfigurations associated with the CVEs in addition to general security hygiene and system hardening.
Qualys customers can leverage the newly released policy “Compensating Controls for Reducing Risk of Vulnerabilities Leveraged by FireEye Red Team Tools.” This policy contains controls which can be used as workarounds / mitigations for these vulnerabilities if patching cannot be done immediately.
Control List:
| CVE IDs | Control ID | Statement |
| CVE-2020-1472 | 20002 | Status of the ‘Domain controller: Allow vulnerable Netlogon secure channel connections’ Group policy setting |
| CVE-2018-13379 | 20010 | Status of the source interface setting for SSL-VPN |
| CVE-2019-19781 | 13952 | Status of ‘Responder’ feature configured on the appliance |
| CVE-2019-19781 | 20011 | Status of the responder action configured on the device |
| CVE-2019-19781 | 20008 | Status of the responder policies configured on the device |
| CVE-2019-19781 | 20009 | Status of the responder global binds configured on the device |
| CVE-2016-0167 | 19440 | Status of Trust Center “Block macros from running in Office files from the Internet” setting for a user profile |
| CVE-2018-8581 | 20007 | Status of the ‘DisableLoopbackCheck’ setting |
| CVE-2019-0708 | 10404 | Status of the ‘Require user authentication for remote connections by using Network Level Authentication’ setting |
| CVE-2019-0708 | 7519 | Status of the ‘Allow users to connect remotely using Remote Desktop Services (Terminal Services)’ setting |
| CVE-2019-0708 | 1430 | Status of the ‘Terminal Services’ service |
| CVE-2019-0708 | 3932 | Status of the ‘Windows Firewall: Inbound connections (Public)’ setting |
| CVE-2019-0708 | 3948 | Status of the ‘Windows Firewall: Inbound connections (Private)’ setting |
| CVE-2019-0708 | 3949 | Status of the ‘Windows Firewall: Inbound connections (Domain)’ setting |
| CVE-2019-0708 | 3950 | Status of the ‘Windows Firewall: Firewall state (Public)’ setting |
| CVE-2019-0708 | 3951 | Status of the ‘Windows Firewall: Firewall state (Private)’ setting |
| CVE-2019-0708 | 3952 | Status of the ‘Windows Firewall: Firewall state (Domain)’ setting |
| CVE-2019-0708 | 11220 | List of ‘Inbound Rules’ configured in Windows Firewall with Advanced Security via GPO |
| CVE-2017-11774 | 13843 | Status of the ‘Do not allow folders in non-default stores to be set as folder home pages’ setting |
| CVE-2017-11774 | 20003 | Status of the ‘EnableRoamingFolderHomepages’ registry setting |
| CVE-2017-11774 | 20004 | Status of the ‘Do not allow Home Page URL to be set in folder Properties’ Group policy setting |
With Qualys Configuration Management, you can easily identify misconfigured systems in context of these vulnerabilities. The screenshot below shows the total passing and failing controls for the impacted assets in the report.

View control posture details with remediation steps. The screenshot below shows control pass/fail details along with actual evidence from impacted asset.

FireEye Disclosure of the Theft of their Red Team Assessment Tools
Hackers now have an influential collection of new techniques to draw upon. Qualys released a new RTI for Solorigate/SUNBURST vulnerabilities so customers can effectively prioritize these CVEs in their environment.
Using Qualys VMDR, the vulnerabilities for Solorigate/SUNBURST can be prioritized for the following real-time threat indicators (RTIs):
- Active Attacks
- Solorigate Sunburst (New RTI)

Remediate FireEye-Related Vulnerabilities with Qualys Patch Management
Identify and Install Needed Patches
To view the relevant missing patches in your environment that are required to remediate the vulnerabilities leveraged by the FireEye tools you may run the following QQL in the Patches tab of Qualys Patch Management:
(qid: [91541,372442,38771,91534,91204,110330,371186,91148,90951,43702,374547,372305,110306,50098,91668,13475,53018,13525,150273])

It is highly recommended to select all the patches returned by this QQL and add them to a new on-demand patch job. You can then target as many assets as possible and deploy the patch job as soon as possible. Note that the Qualys Cloud Agent will only deploy the right patch to the right asset, meaning the Qualys patch job will do the mapping of patch to asset (so you don’t have to) ensuring only the right patch is deployed to the right asset (in terms of binary architecture, OS version, etc). In addition, if a patch is not needed by a specific asset the Qualys agent will “skip” this asset and the patch will not be deployed.
The same QQL can be used in the patch assets tab in order to see all the assets that miss at least one of the FireEye-related patches:

Visualize Assets Requiring Patches
Qualys has created two dashboard widgets that you can import into the patch management dashboard. These widgets will show the number of missing FireEye-related patches in your environment and the number of assets in your environment missing one of those patches.
Steps to Import the Widget:
- Click on “Setting” icon in “Dashboard” section.
- Select “Import New Widget” option.
- Enter a name of your choice for the widget.
- Browse the JSON file to import.
- Click on “Import” button.
- On success, you should see the new widget in your Dashboard.
You can download these two dashboard widgets from the PatchMGMT-Fireeye-Widgets attachment at the bottom of the FireEye Theft dashboards article.
Hunting in Endpoint Detection and Response (EDR)
There are two components to hunt for evidence of these tools using the Qualys EDR. The first is looking for evidence of the files from the provided Yara signatures. Qualys has taken the file hashes from the RetroHunt tool and created a dashboard. With a single click you can find evidence of any matches in your environment.
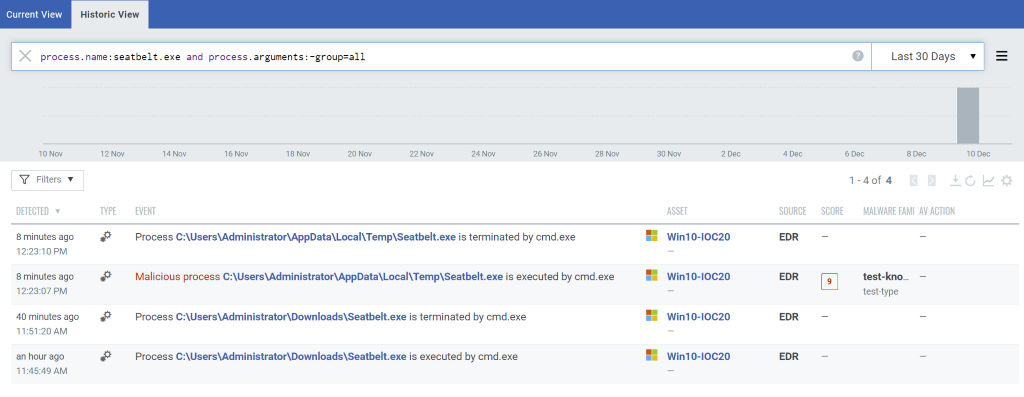
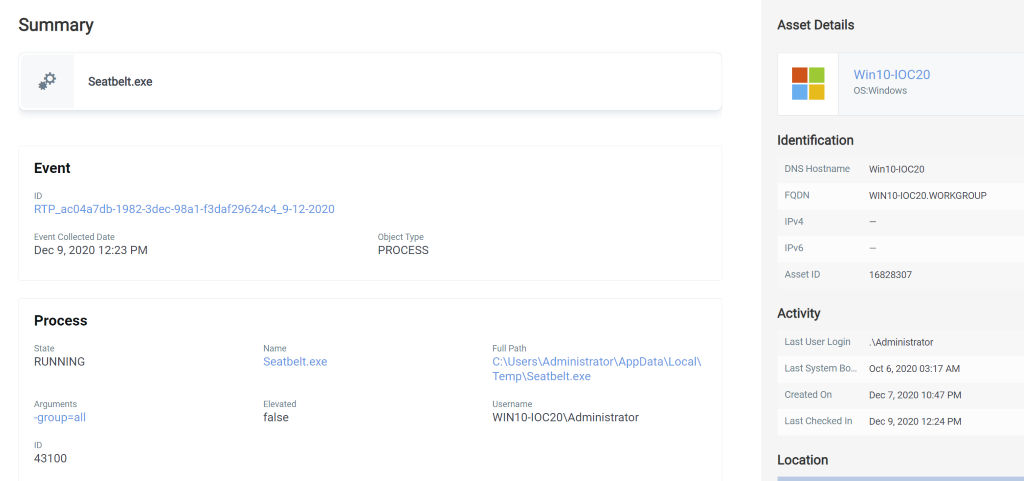
The second component is hunting for evidence of the processes outlined in the OpenIOC signatures. While these signatures cannot be imported directly into Qualys EDR, the Qualys Labs team is converting these into Qualys Query Language (QQL) which can be used in the Qualys EDR hunting page. An example provided here shows hunting for this Seatbelt signature. In the coming days, these hunting queries will be available to all Qualys EDR customers.
Get Started Now
Start your Qualys VMDR trial to automatically identify, detect and patch the high-priority publicly known vulnerabilities.
Start your Qualys EDR trial to protect the entire attack chain, from attack and breach prevention to detection and response using the power of the Qualys Cloud Platform – all in a single, cloud-based app.
Start your Qualys Threat Protection trial to access the Live Threat Intelligence Feed that displays the latest vulnerability disclosures and maps them to your impacted IT assets. You can see the number of assets affected by each threat, and drill down into asset details.
References
https://github.com/fireeye/red_team_tool_countermeasures
https://github.com/fireeye/red_team_tool_countermeasures/blob/master/CVEs_red_team_tools.md
thanks so much for this great, informative article about Fire Eye and Gov Agencies ‘ attack. The detailed counter action is very helpful.