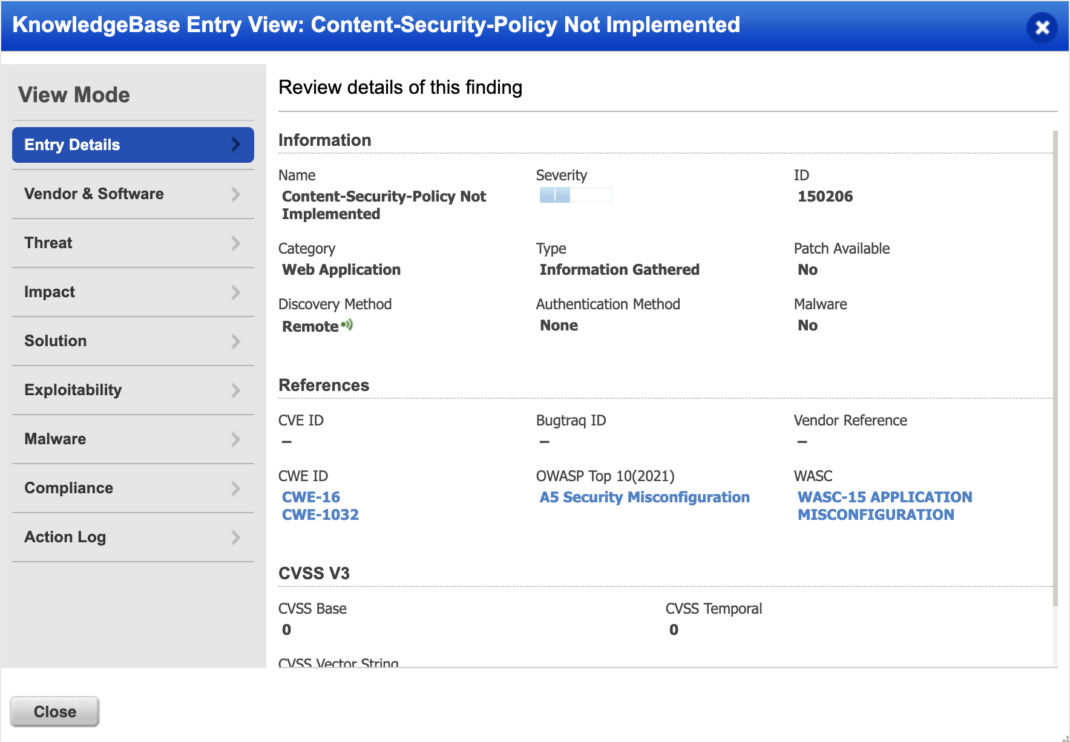
Creating Awareness of External JavaScript Libraries in Web Applications

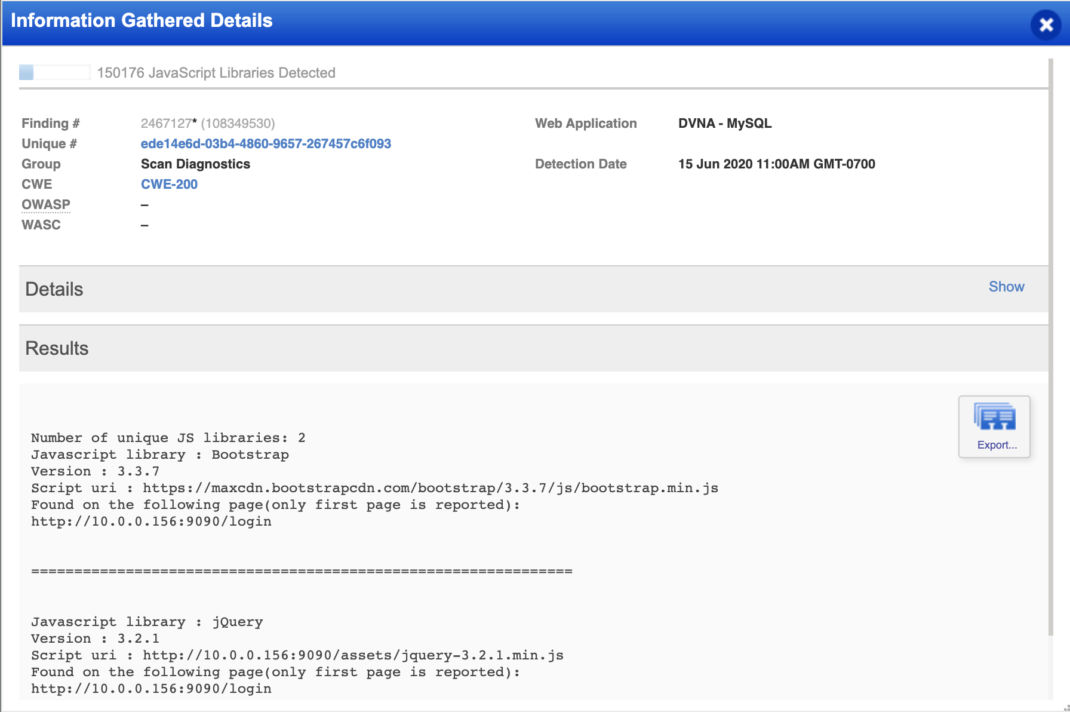
Qualys Web Application Scanning (WAS) routinely reviews and solicits customer feedback regarding vulnerabilities. This may be to enhance the detection or the detection’s reporting. Previously, all JavaScript libraries detected on an application are reported under the Information Gathering QID 150176. This included internal and external JS libraries. This may not be ideal as organizations may wish to report and address the libraries separately. While any outdated library introduces security risks, external JS has additional risks associated with its use. For this reason, Qualys WAS introduces QID 150545 to highlight external JS utilized by an application.
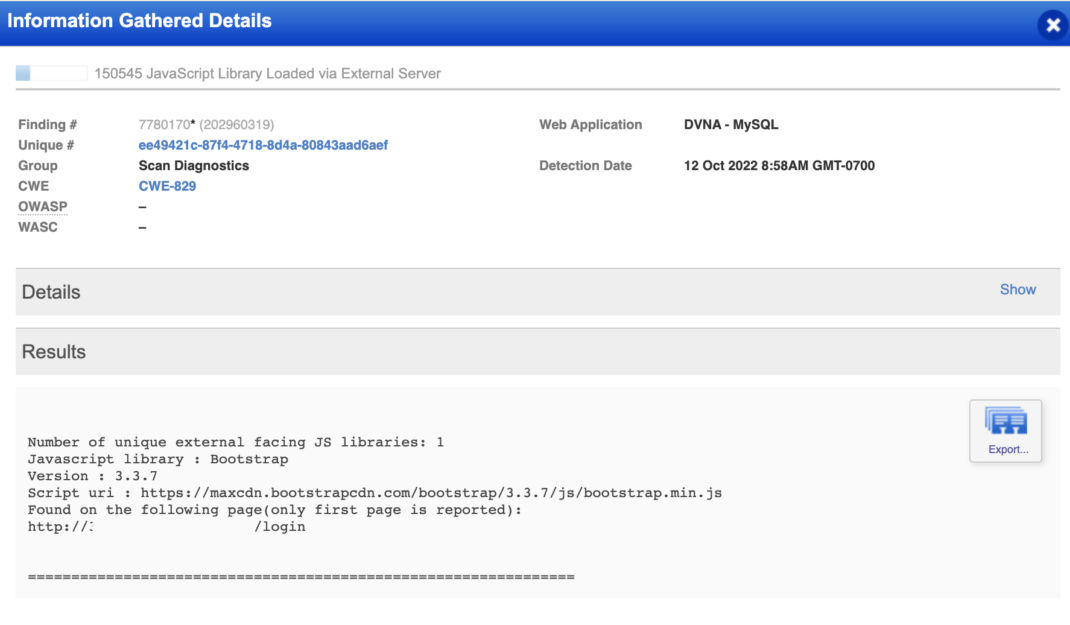
New QID 150545: JavaScript Library Loaded via External Server
A new QID is added that will separate the external JS libraries, QID 150545. This new QID can be will be detected in both Discovery and Vulnerability scans.
Previous:
QID 150176
Now:

QID 150545
External JavaScript Risks
Lack of Availability
If JS is loaded from an external domain, the domain needs to be always available. If the loading fails, the JS will not be loaded into the application. Additionally, the file could be renamed, or the URL could change and this would also cause the resource to fail to load.
External Control
When utilizing external JS, the external organization controls the source. Any changes made to the source file will be loaded into the application. This may cause performance or functionality issues.
Performance Impact
This is becoming more negligible, however utilizing external resources will lead to overall slower page loads.
4th Party JS
The external, or third party, JS may load additional JS from other domains. The more abstracted the JS becomes the less control an organization will have.
Defenses
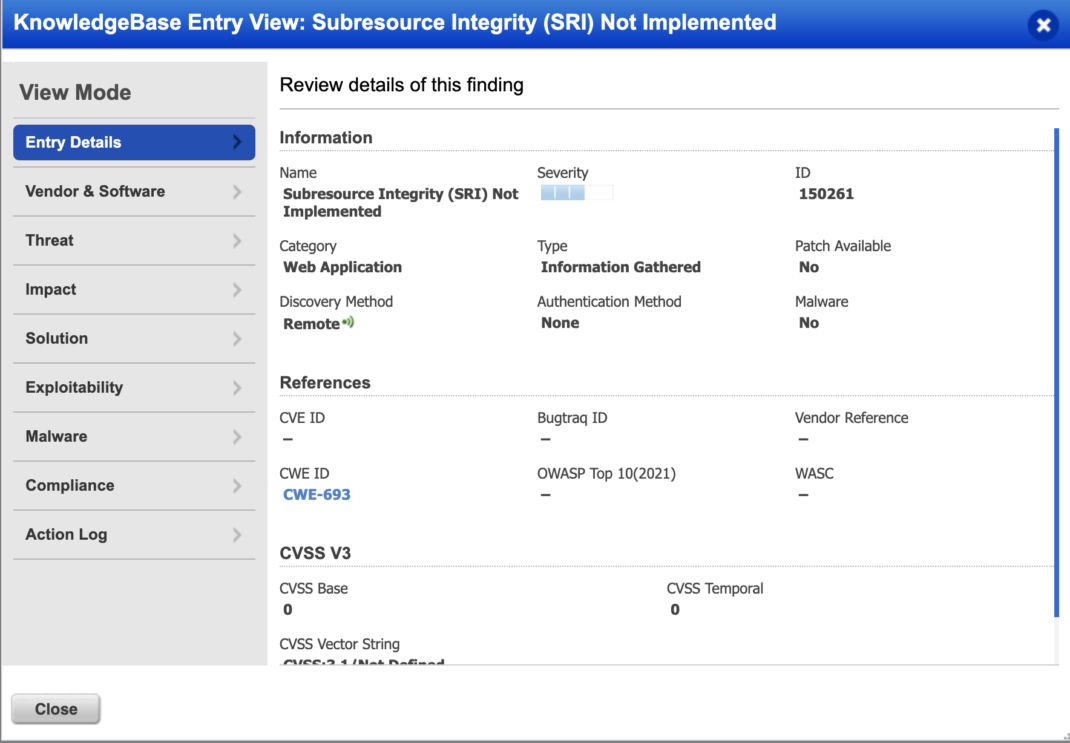
Sub Resource Integrity (SRI)
SRI allows for a hash of the file to be verified when fetching the JS file. This will ensure the file has not been modified from what is expected.
Qualys WAS will detect if SRI is not in use with QID 150261 Sub Resource Integrity (SRI) Not Implemented
Content Security Policy (CSP)
CSP allows developers to whitelist domains from where resources are loaded. This includes JS, images, font and more.
Qualys WAS will detect if CSP is not in use with QID 150206 Content-Security-Policy Not Implemented