De-risk the Software Supply Chain by Expanding Unparalleled Detection Coverage With Qualys VMDR and Software Composition Analysis

QIDs/CVEs
When it comes to cybersecurity, speed is key in getting an edge over attackers. But when you consider that vulnerabilities weaponize 24 days faster than then they are remediated on average, cybersecurity stakeholders have a lot of catching up to do.
While there are many ways defenders can reduce their MTTR and improve their odds against attackers, perhaps none are as important as achieving an effective risk-based approach to vulnerability prioritization. However, this is easier said than done. Here’s why:
The industry-standard cataloging doctrine of Common Vulnerabilities and Exposures (CVEs) that relies on the Common Vulnerability Scoring System (a.k.a. CVSS Scores) lacks business context, leaving out information relative to asset criticality, relevance within the organization, etc. Without this information, CVSS scores can leave defenders with more than 50% of their vulnerability queue being tagged as ‘high-risk’ or ‘critical,’ thus slowing remediation workflows between security and IT Operations. A better mechanism for measuring and prioritizing vulnerabilities is needed. Qualys has heard the call loud and clear.
Qualys has long provided a sophisticated alternative with its Qualys Identifier (QID) system, a testament to the company’s innovation in cybersecurity management. The QID system offers a refined strategy by consolidating similar CVEs under a single identifier, thereby streamlining the remediation process and enabling organizations to focus on truly impactful vulnerabilities. This approach not only simplifies the complexity associated with managing numerous CVEs but also enriches vulnerability management with detailed, actionable intelligence. As a result, organizations can prioritize their efforts more effectively, ensuring that critical vulnerabilities are addressed with the urgency they require.
Beyond the aggregation of CVEs, the QID system extends its coverage to include non-CVE vulnerabilities, misconfigurations, and security best practices, offering a comprehensive view of an organization’s security posture. This holistic approach ensures that organizations are not merely reactive to known vulnerabilities but are proactively safeguarding against a broad spectrum of potential security threats.
Qualys’s QID system exemplifies the company’s commitment to advancing cybersecurity management, providing organizations with a powerful tool that enhances their ability to secure their assets while maintaining compliance with regulatory standards.
VulnSigs Features
Our approach to vulnerability management sets a new standard in cybersecurity, distinguished by exceptional accuracy and comprehensive coverage. Our approach combines rapid Zero-Day detection and an average response time of less than 17 hours for addressing critical and Zero-Day vulnerabilities, setting us apart in threat response speed. We proudly cover 92% of the CISA KEV catalog, demonstrating our robust detection capabilities against a wide array of threats.
Key features of our methodology include exploit-based checks that offer insights from an attacker’s perspective, deep analysis that surpasses NVD CPE limitations for greater accuracy, and wide-ranging coverage across various technologies. We extend our protection to include non-CVE vulnerabilities, misconfigurations, and security best practices, ensuring a comprehensive defense strategy. Our distinct advantage also lies in Kernel Package Protection, which discerns vulnerabilities across all kernel packages, including inactive ones, through dynamic evaluation methods. Our methods exceed standard software inventory assessments by focusing on actual file presence, offering an unmatched level of detection.
Our streamlined and effective vulnerability management solutions empower organizations to secure their assets comprehensively, ensuring readiness against both current and emerging cyber threats.
At Qualys, we’re dedicated to empowering organizations to navigate the complex landscape of cybersecurity with confidence. That’s why we’re thrilled to unveil the integration of Software Composition Analysis (SCA) into our renowned Vulnerability Management, Detection, and Response (VMDR) platform. This pivotal addition enhances VMDR’s capabilities, offering organizations unprecedented visibility and control over software supply chain vulnerabilities within their production environments.
Qualys VMDR: Unmatched Detection Coverage
At the forefront of vulnerability management, Qualys VMDR stands as a testament to our commitment to providing unparalleled detection coverage. Our platform is known for its comprehensive approach, covering breadth, depth, and accuracy in identifying vulnerabilities across diverse environments.
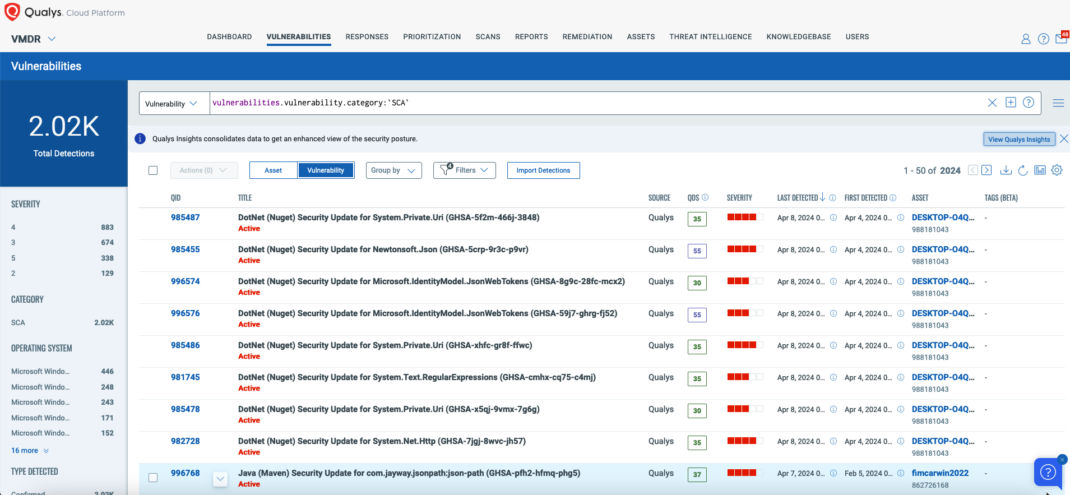
Breadth of Coverage: Qualys VMDR offers extensive coverage across a wide range of assets, including endpoints, servers, cloud instances, containers, and web applications. This breadth ensures that organizations can effectively manage vulnerabilities across their entire digital infrastructure, regardless of complexity or scale.
Depth of Analysis: Leveraging advanced scanning techniques and threat intelligence feeds, Qualys VMDR delves deep into the underlying systems and applications to identify vulnerabilities that may pose a risk to the organization. Whether it’s known vulnerabilities, Zero-Day exploits, or emerging threats, VMDR provides in-depth analysis to stay ahead of evolving cyber threats.
Accuracy in Identification: With a focus on precision and reliability, Qualys VMDR utilizes advanced algorithms and machine learning capabilities to accurately identify vulnerabilities and prioritize them based on severity and potential impact. Our platform adheres to Six Sigma standards, achieving a remarkable accuracy rate of 99.99966%. By minimizing false positives and false negatives, VMDR enables organizations to focus their resources on addressing the most critical security risks.
Introducing Software Composition Analysis
In today’s dynamic digital landscape, the proliferation of open-source components in application development has presented both opportunities and challenges. While open-source components offer agility and innovation, they also introduce inherent risks, particularly concerning security vulnerabilities. Recent high-profile attacks on widely used software packages have highlighted the critical importance of addressing vulnerabilities within the software supply chain.
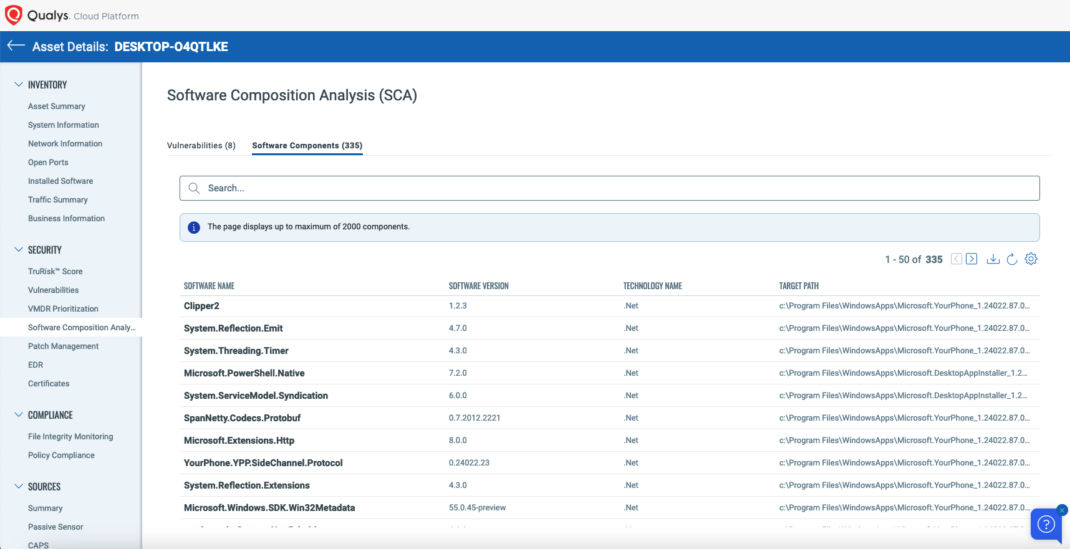
Software Composition Analysis (SCA) addresses this challenge head-on. By providing continuous and real-time visibility into open-source and commercial software components in production environments, SCA empowers organizations to detect and remediate potential risks proactively. Leveraging the Qualys Agent, SCA scans for vulnerabilities across a wide array of languages and platforms, including Java, Go, .NET, Python, Node JS, Rust, Ruby, PHP, and more.
Key Features of Runtime Software Composition Analysis
- Real-time Visibility: Gain continuous insight into deeply embedded open-source packages and commercial software components, enabling proactive threat mitigation.
- Comprehensive Coverage: Detect vulnerabilities across various languages and platforms, with over 13,000 new signatures covering more than 11,000 Common Vulnerabilities and Exposures (CVEs).
- Actionable Insights: Receive detailed reports highlighting vulnerabilities, severity levels, potential impacts, and recommendations for remediation, empowering security teams to take decisive action.
- Customizable Scanning: Tailor scans to suit specific environment needs, including targeting specific paths or expanding coverage scope as required.
- Seamless Integration: Integrate SCA seamlessly into existing workflows for Vulnerability Management, ensuring efficient and automated reporting without disruption.
De-risk Your Business with the Qualys Enterprise TruRisk™ Platform
In conjunction with Software Composition Analysis, Qualys offers the Enterprise TruRisk Platform, a comprehensive solution designed to measure, communicate, and eliminate risk effectively. By leveraging TruRisk, organizations can gain a holistic view of their risk landscape, enabling informed decision-making and proactive risk mitigation strategies.
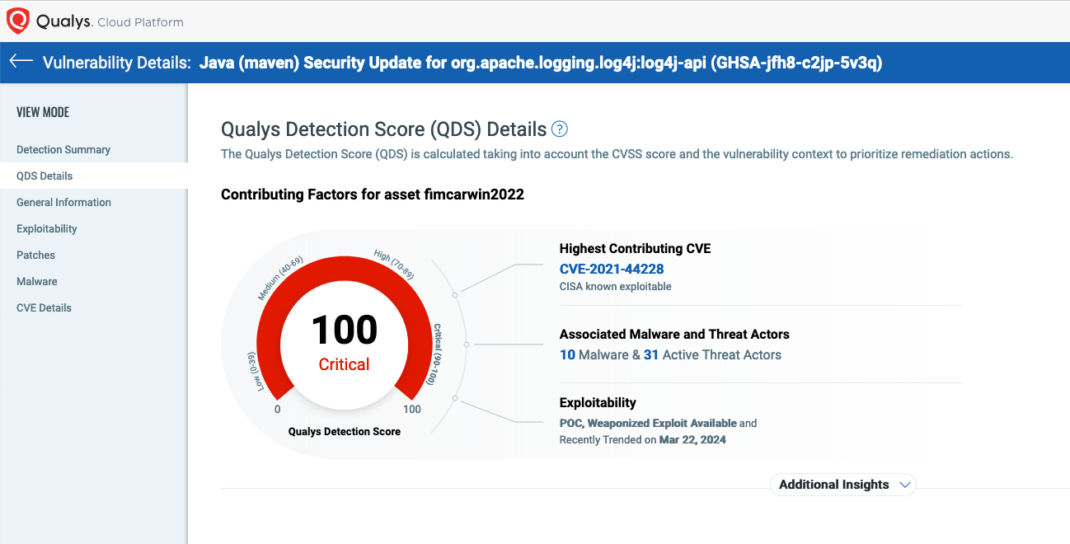
- Measure Risk 6x Faster: The Qualys Enterprise TruRisk Platform empowers organizations to measure risk swiftly, offering a streamlined process that is six times faster than competitive Vulnerability Management (VM) platforms. By leveraging advanced analytics and automation capabilities, TruRisk enables organizations to assess their risk posture rapidly, allowing them to make informed decisions with confidence.
- Communicate Risk from 200K+ Vulnerabilities: With access to over 200,000 vulnerabilities sourced from 25+ threat intelligence feeds, the Qualys Enterprise TruRisk Platform provides organizations with unparalleled insights into their risk landscape. By aggregating and analyzing data from diverse sources, TruRisk offers a comprehensive view of potential threats, enabling organizations to prioritize and address vulnerabilities effectively.
- Eliminate Critical Risk 60% Faster: The Qualys Enterprise TruRisk Platform enables organizations to eliminate critical risk swiftly, offering a one-click workflow and seamless integration with IT Service Management (ITSM) platforms. By streamlining the remediation process and automating repetitive tasks, TruRisk accelerates time-to-resolution by 60%, allowing organizations to mitigate critical vulnerabilities and reduce exposure rapidly.
Upcoming Enhancements in Q2, 2024:
One reason VMDR stands out as a leader in IDC’s Worldwide Device Vulnerability Management Forecast is because of innovation. With that in mind, Qualys is preparing a number of cutting-edge enhancements for Q2, 2024, to help customers strengthen their ability to detect, prioritize, and remediate vulnerabilities throughout their environments.
Full File System Level Crawling
In a forthcoming release, Qualys will provide full-file, system-level crawling beyond open-source software components. This feature will enable organizations to gain comprehensive visibility into all software components and dependencies within their environments, regardless of their origin or nature.
By extending file system-level crawling capabilities, Qualys VMDR will empower organizations to identify and assess vulnerabilities across the entire software stack, including proprietary applications and custom code. This holistic approach to vulnerability management will enable organizations to strengthen their security posture and mitigate risks effectively.
View Low-impact Vulnerabilities in Linux distributions
Detection enhancements will add support to cover low-impact unpatched vulnerabilities, for CVEs that are typically ignored by Linux distributions. Qualys will offer an opt-in solution for customers who want to identify such vulnerabilities to provide comprehensive security posture and proactive risk management.
CVE-Based Reporting
In a future release, Qualys will provide CVE-based reporting within Qualys VMDR. This feature will enable organizations to generate detailed reports based on Common Vulnerabilities and Exposures (CVEs), allowing for more granular analysis and prioritization of vulnerabilities.
By leveraging CVE-based reporting, organizations can gain deeper insights into the specific vulnerabilities affecting their systems, enabling them to make informed decisions about risk mitigation strategies. This upcoming release further underscores our commitment to delivering innovative solutions that address the evolving needs of our customers.
Source Detection for Each QID
In an upcoming release, Qualys will provide source detection for each Qualys ID (QID). This feature will offer insight into which sensor type—Agent, Software Composition Analysis, Scanner, or Custom QID with Custom Assessment and Remediation (CAR)—detected a specific vulnerability.
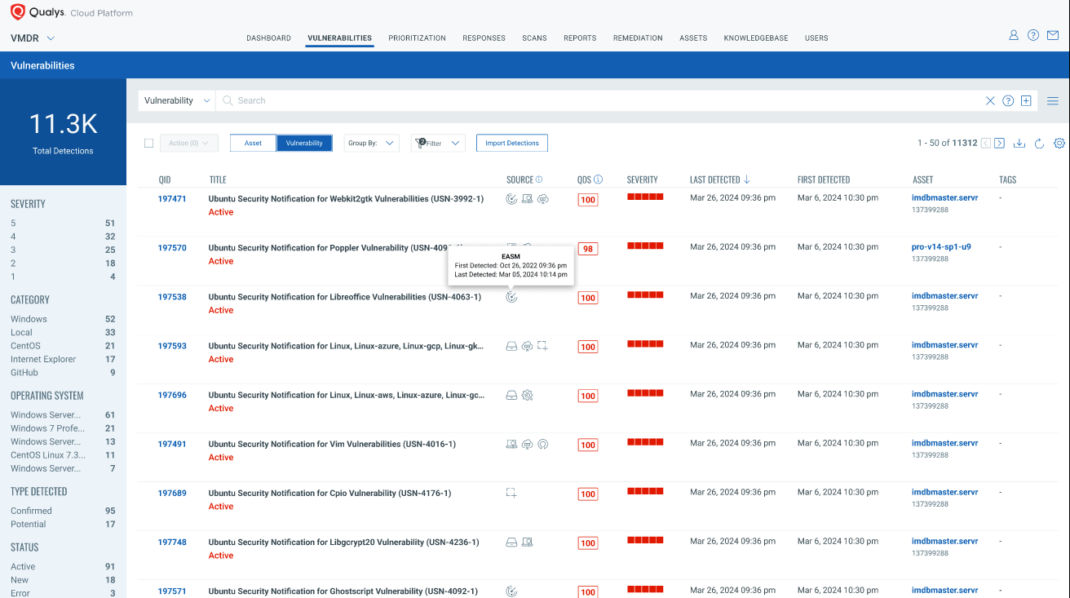
Understanding the source of each vulnerability detected by Qualys VMDR is invaluable for organizations in prioritizing remediation efforts and optimizing their cybersecurity strategies. By providing source detection for each QID, Qualys VMDR empowers organizations to make informed decisions about vulnerability management, ensuring resources are allocated effectively and risks are mitigated promptly.
Stay tuned for more updates on this upcoming release and how it will further enhance the capabilities of Qualys VMDR in providing comprehensive visibility and protection against cybersecurity threats.
Conclusion
The integration of Software Composition Analysis into the Qualys VMDR platform represents a significant milestone in our commitment to providing comprehensive cybersecurity solutions. By offering real-time visibility into software supply chain vulnerabilities and empowering organizations to measure, communicate, and eliminate risk with the Enterprise TruRisk Platform, Qualys enables businesses to navigate today’s threat landscape with confidence.
Try Qualys VMDR to know the TruRisk of your organization.