How to Detect Issuer Certificates and Comply with Google Chrome’s New Entrust Certificate Policy Using Qualys Certificate View
Google has announced that Chrome 127 and higher will no longer trust certain TLS certificates issued by Entrust, effective November 1, 2024. This change is significant and could potentially disrupt businesses relying on Entrust-issued certificates. Google stated that “publicly disclosed incident reports have highlighted a pattern of concerning behaviors by Entrust that fall short of expected standards, eroding confidence in their competence, reliability, and integrity.”
As organizations prepare for this transition, it’s crucial to identify and replace affected certificates promptly. Qualys Certificate View, which is included with the Vulnerability Management Detection and Response (VMDR) bundle, is here to help organizations discover, inventory, and report on all assets that present Entrust certificates.
Google Announcement Impact
When Google Chrome stops trusting Entrust TLS certificates, any websites or services using these certificates will face security warnings, which can erode user trust and potentially lead to a loss in traffic or business. Ensuring compliance with the new policy is essential to maintain smooth and secure operations. In addition to Chrome, other browsers may follow the same approach in the upcoming days.
Potentially Impacted Entrust & AffirmTrust Root Certificates
The following Entrust and AffirmTrust root certificates, whose earliest Signed Certificate Timestamp (SCT) is dated after October 31, 2024, will no longer be trusted by default by the browsers, due to the compliance failures that resulted in the publicly disclosed incident reports that highlighted a pattern of concerning behaviors by Entrust CA that didn’t meet the required expectations and the confidence levels for using these Certificates for the actual communications.
- Entrust Root Certification Authority – EC1
- Entrust Root Certification Authority – G2
- Entrust.net Certification Authority (2048)
- Entrust Root Certification Authority
- Entrust Root Certification Authority – G4
- AffirmTrust Commercial
- AffirmTrust Networking
- AffirmTrust Premium
- AffirmTrust Premium ECC
Certificates issued by Entrust or AffirmTrust on or before October 31, 2024, will remain valid until their expiration date, usually one year. However, organizations must transition to another trusted CA provider to maintain trust across all major browsers.
For Entrust/AffirmTrust certificates classified as publicly trusted CAs, it is crucial to move to another trusted CA provider. Maintaining a different certificate for multiple browsers is not technically feasible. We recommend treating this as a mission-critical project to ensure a trusted model is supported by all major browsers.
Qualys VMDR – Certificate View Impact Analysis
Anonymized data from Qualys VMDR has identified approximately 8,500 unique certificate hashes across our customer base using Entrust certificates that will be impacted by this change in policy. Interestingly, 20% of these certificates will continue to be valid after October 31, but it is advisable to take proactive action to renew or replace them with new digital certificates.
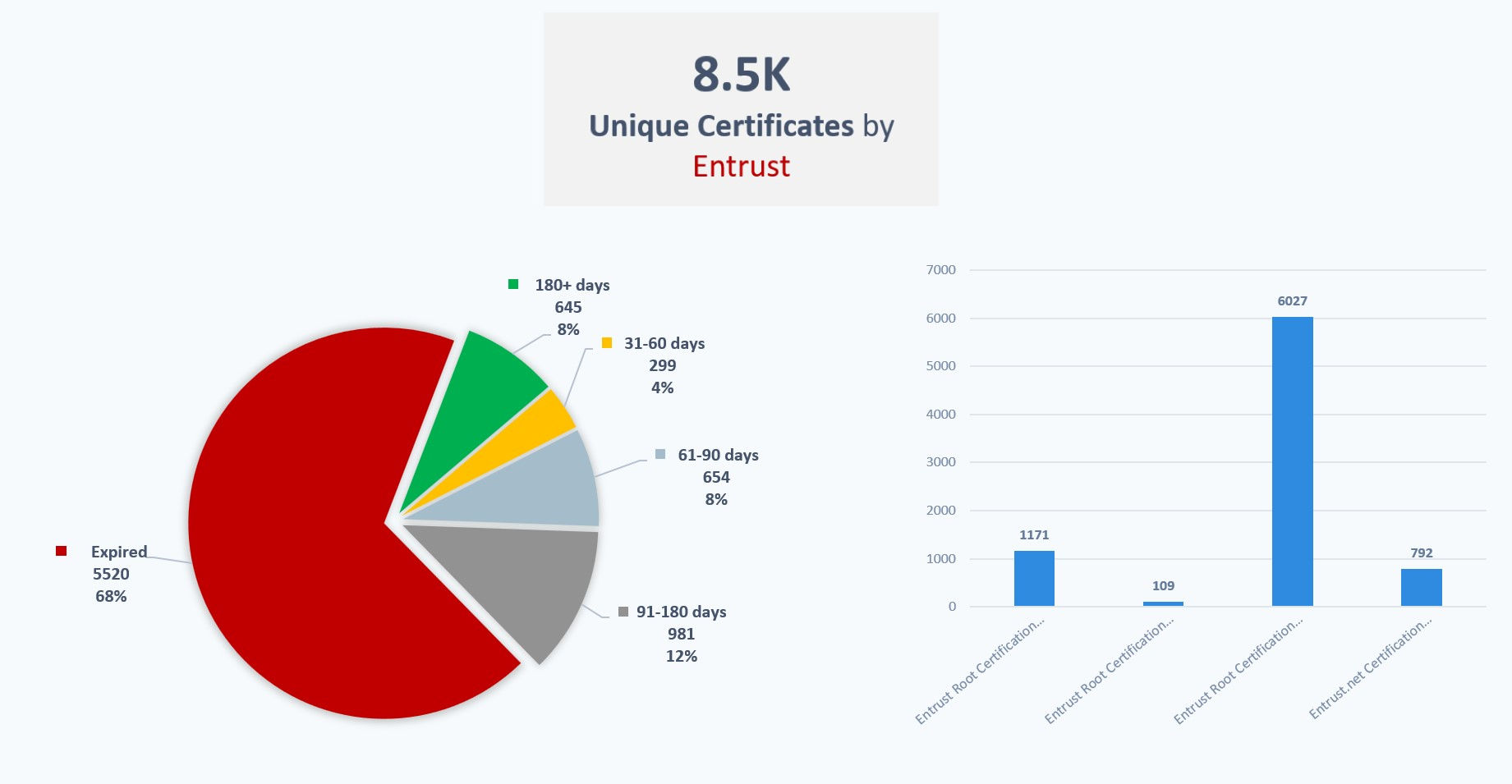
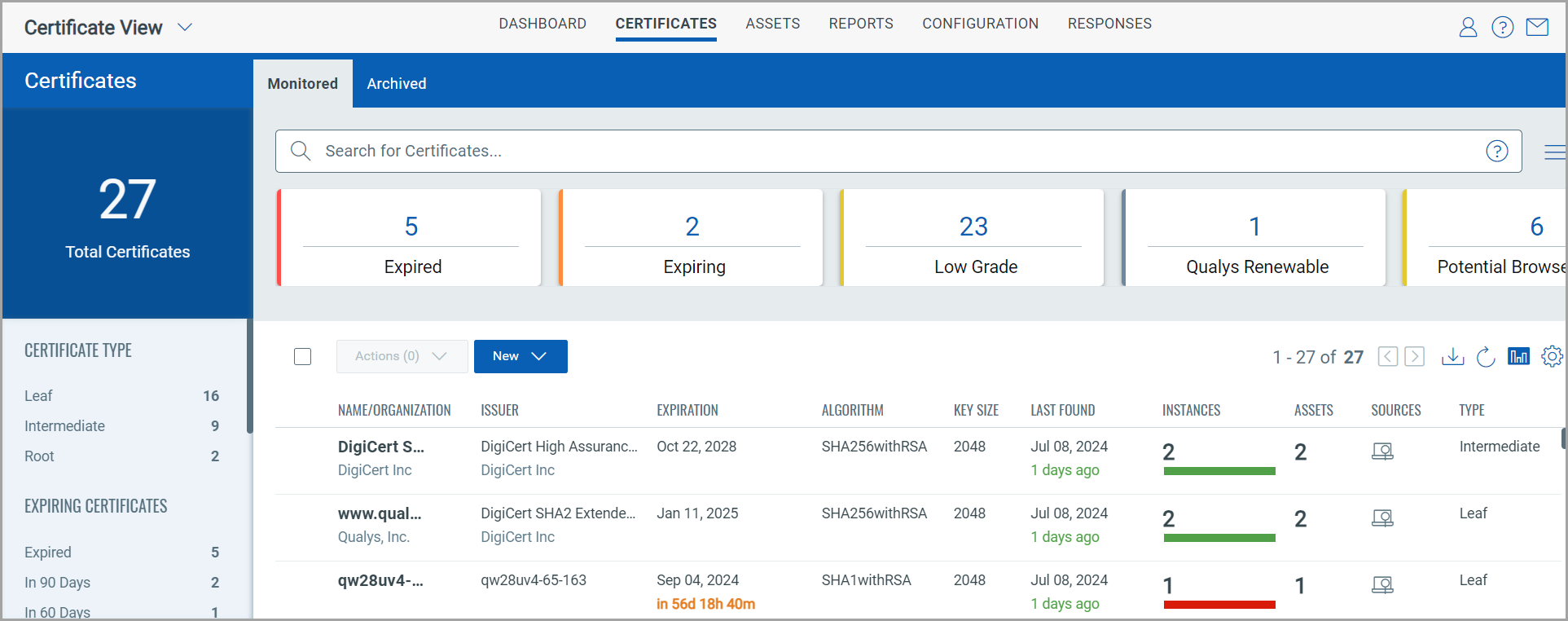
Qualys Certificate View Overview
Qualys Certificate View is designed to streamline the management of your certificate inventory. With its powerful features, you can quickly identify certificates by issuer, including those from Entrust, across your entire organization. By leveraging Certificate View, you can stay ahead of compliance requirements and ensure your organization’s certificates are up-to-date and trusted. This proactive approach will help you avoid potential disruptions and maintain the security and trust of your services.
Detect Potential Browser Distrust Certificates
The upcoming release of CertView 3.7 will add capabilities to detect the listed certificates, allowing them to be uniquely classified so customers can determine how many are in use within their organization. Customers who continue using these certificates without updating them before October 31, 2024, will encounter untrusted certificate warnings starting November 1, 2024, and these certificates will be blocked.
To view Entrust or AffirmTrust certificates, use the following query in Certificate View or create a new dashboard widget to monitor the status:
certificate: (browserDistrust: potential)
This query will quickly identify all certificates issued by Entrust that need to be replaced before the deadline.
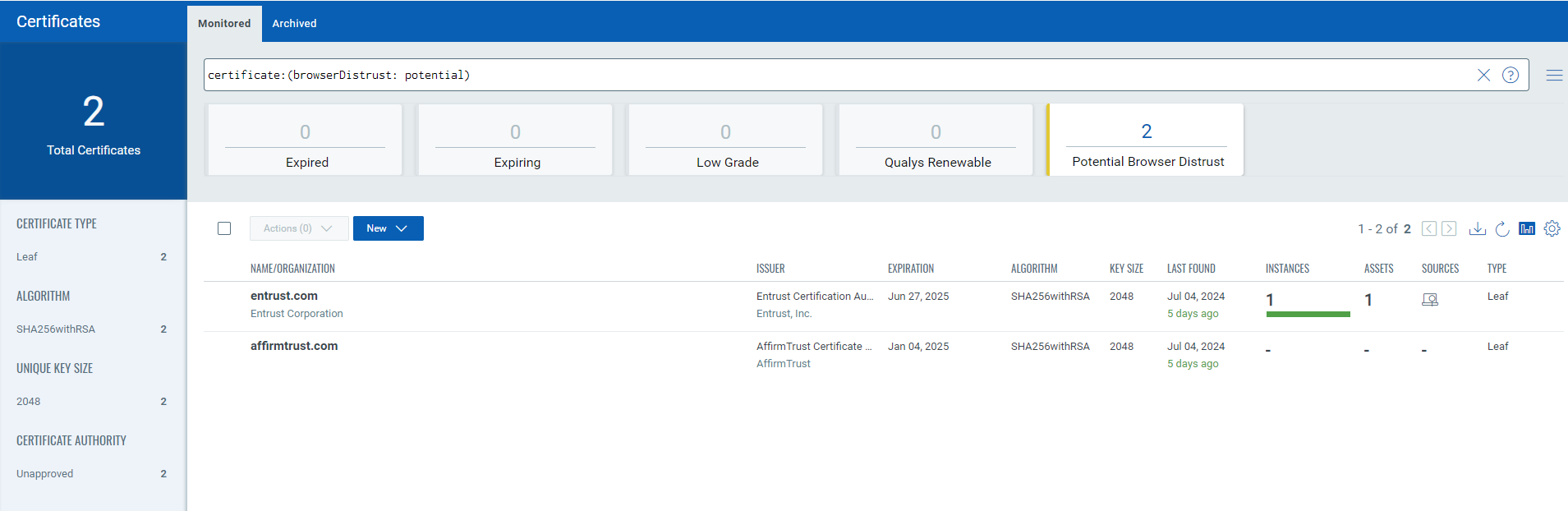
You can save this query as a dashboard widget for continuous monitoring, ensuring that any new Entrust certificates are promptly detected and managed.
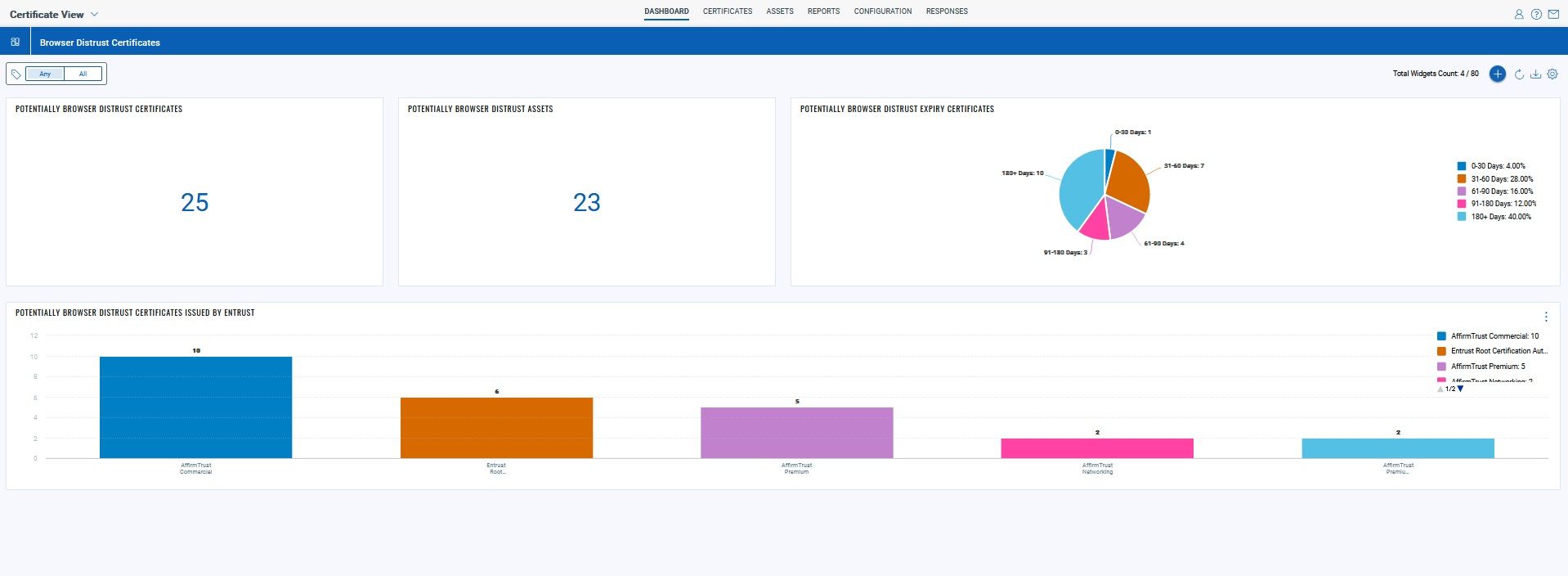
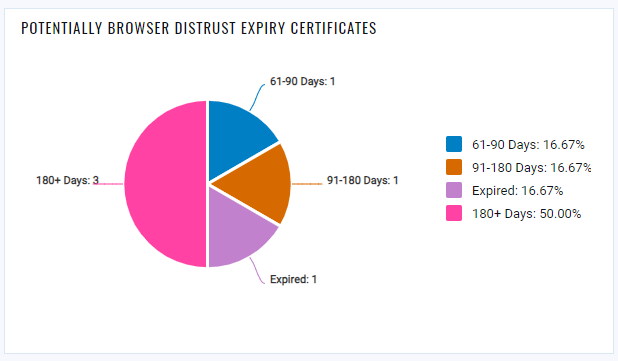
Customers can also use the following queries to track certificates that are expiring in the upcoming days.
In the upcoming Qualys Certificate View release, customers will be able to download a provided JSON file and import it into Certificate View to understand the impact of these certificates across their infrastructure.
Achieve Comprehensive Coverage
Existing VMDR customers who perform regular scans are already collecting certificate data within their current cybersecurity management scope. To extend this coverage, ensure that Certificate View is entitled with VMDR-enabled IP ranges and activated on each public cloud connector.
Use Certificate View to discover certificates on digital assets hosted on public services, such as web hosts or app providers, ensuring comprehensive certificate analysis. Simply add the domains of these sites into Certificate View, and it will perform a lightweight scan to detect TLS services and analyze their certificates. Provide either Fully Qualified Domain Names (FQDNs) or IP addresses of the public sites you want to scan. Certificate View will scan a list of standard ports to collect certificate information, giving you a complete view of your certificates across all assets.
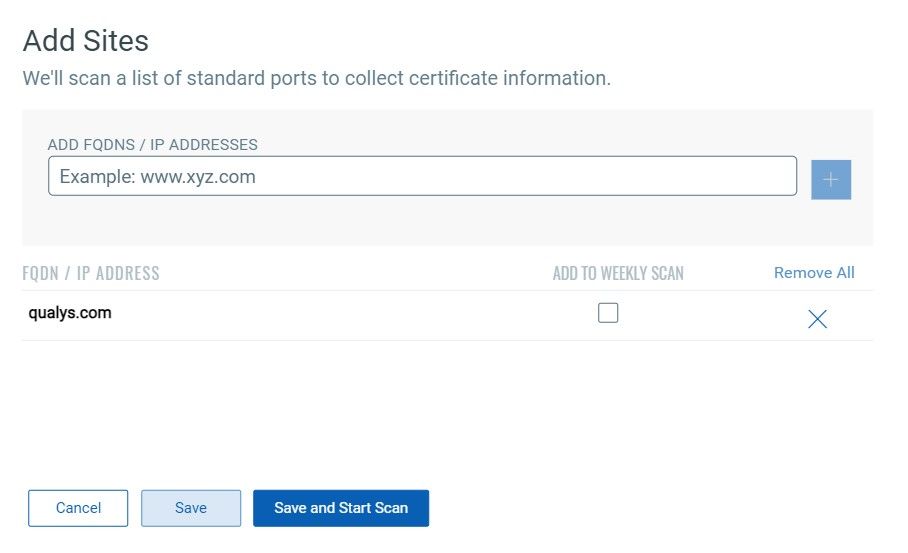
Certificate View Expansions:
Root and Intermediate Certificate Visibility & Mitigate Risk
In the upcoming release in July, customers will gain additional visibility for their root and intermediate certificates, not just limited to leaf certificates. This will include detailed assessment reports, certificate strength, signature algorithm, cipher suites, and expiration monitoring. For every leaf certificate, you can view the certificate path, providing complete visibility of your certificates.
Enroll or Renew Your Certificates
With the integrated renewal process in Certificate View, customers can use the enrollment options to initiate the renewal process for their certificates that are about to expire. This workflow assists in sending a renewal request to DigiCert. You can enroll, renew, and even auto-renew certificates issued by DigiCert, as well as those from DigiCert acquisitions such as Thawte, Mocana, and GeoTrust. This streamlined process ensures that your certificates remain up-to-date and compliant with security standards.
Certificate View Rapid Certificate Deployment Option
The latest Certificate View release enables bulk deployment of certificates using the Qualys Cloud Agent for upcoming expiration, allowing proactive remediation. Customers can reach out to the respective Technical Account Manager to activate this feature.
Certificate View Upcoming Capabilities – Automated Certificate Renewal
Qualys Certificate View is expanding its capabilities to support renewals using the Automated Certificate Management Environment (ACME) protocol, enabling automation of the issuance and renewal of certificates. Customers can create a Certificate Signing Request (CSR) that involves generating a server-side request that must be copied and pasted into a field for your CA. After that, the agent can download and install the certificate and inform the assigned contact about it.
With these expansions, customers can review whether a public trusted CA, such as Entrust/AffirmTrust, issued their certificates and utilize these new capabilities to renew or issue new certificates.
Conclusion
The upcoming change in Chrome’s trust policy for Entrust-issued TLS certificates underscores the importance of robust certificate management. Certificate View empowers your organization to navigate this transition seamlessly, ensuring compliance and maintaining trust with your users.
Start your Risk-Free Trial of VMDR
If you are not already using VMDR to measure, communicate, and eliminate risk, we invite you to start a risk-free trial for thirty days. Begin using Certificate View to safeguard your business against potential disruptions and ensure your certificates comply with the latest standards.
References
Contributors
- Ramesh Ramachandran, Principal Product Manager, VMDR
- Siddharth Batia, Director, Product Management CSAM & EASM
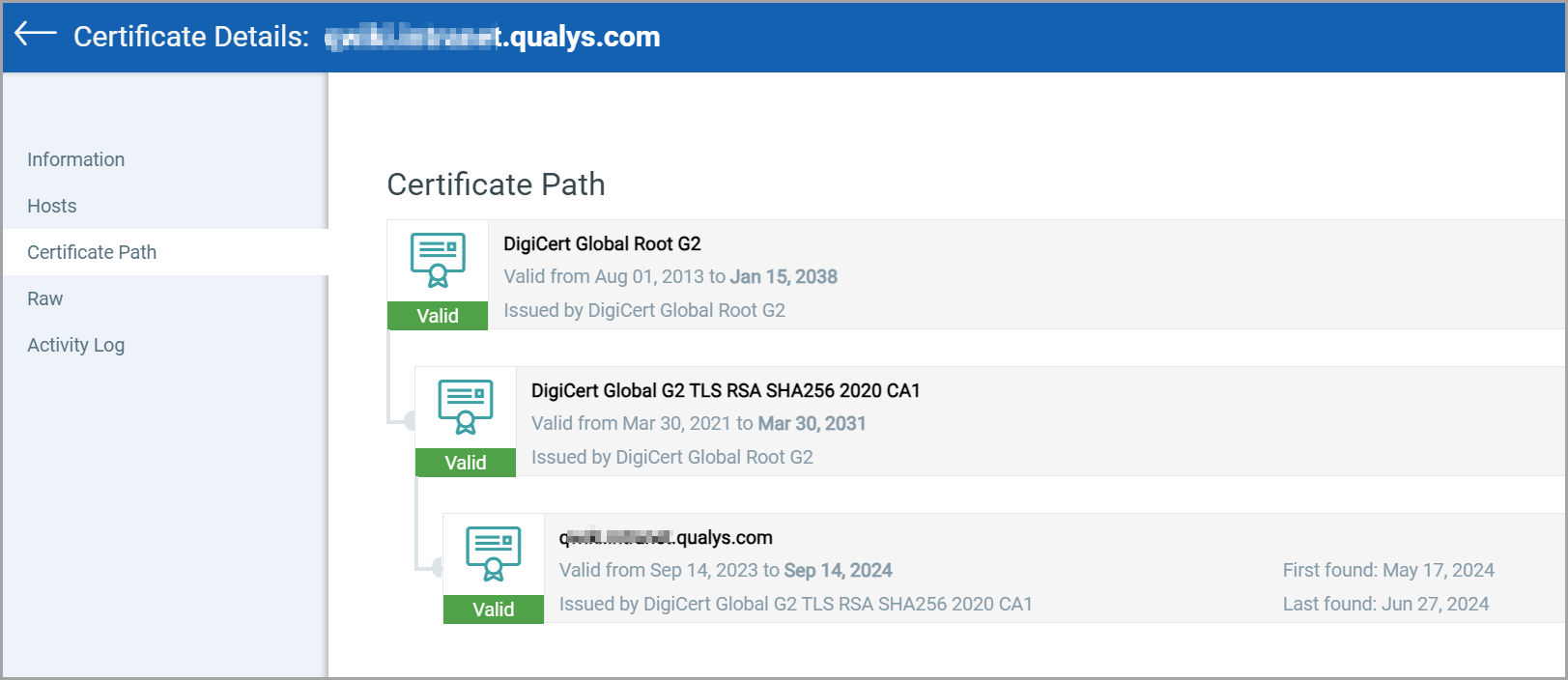
SSLlabs seems to be flagging (T) Entrust certificates migrated to SSL.com.
SSL labs seems to be falsely flagging (T) for Entrust migrated certificate to SSL.com