PCI DSS 4.0: Get Audit-Ready for the New Requirements
Last updated on: June 7, 2024
The Payment Card Industry Data Security Standard (PCI DSS) originated in 2004 and is managed by the PCI Security Standards Council to ensure security for the global payment industry. This mandate applies to all entities worldwide that store, process, or transmit payment cardholder data or sensitive authentication data or could impact the security of the cardholder data environment (CDE). PCI DSS version 4.0 was announced in March 2022 and has 64 new requirements that organizations must meet.
The requirements are divided into two phases, with 13 requirements becoming mandatory on March 31, 2024, and the remaining 51 becoming mandatory on March 31, 2025. Regardless of whether your credit card provider uses transaction tokenization, you must still comply with many of these requirements.
In this blog, we’ll assume you have some familiarity with PCI DSS, and our aim is to summarize the new requirements and how Qualys can help ensure compliance. Download our latest PCI DSS 4.0 whitepaper for more details.
New Requirements in PCI DSS 4.0
A key difference between PCI DSS 3.2.1 and 4.0 is a greater emphasis on continuous monitoring and a shift to a more flexible framework that allows for greater customization and the ability to align security measures with true risks and business priorities. This allows organizations to implement more effective controls based on real-world scenarios. For example, a firm with a large cloud infrastructure can adopt more cloud-native solutions to ensure efficiency while also maintaining compliance.
PCI DSS 4.0 also emphasizes taking a more risk-based approach to cybersecurity implementation. Firms should now understand and focus more on true risks based on robust threat intelligence to prioritize and remediate vulnerabilities and threats. This allows more efficient resource allocation and ensures faster resolution for more critical issues.
Below are a few primary differences between the previous and current PCI versions:
| Area of Focus | PCI DSS 3.2.1 | PCI 4.0 |
|---|---|---|
| Emphasis | More static and prescriptive, more rigidly defined requirements. | More flexible and customizable, risk-based with continuous monitoring. |
| Risk-based prioritization | More formal risk assessment analyses and processes. | More focused on risk analyses, stronger true risk prioritization. |
| Vulnerability scanning | External scans require an Authorized Scanning Vendor (ASV). | External scans require ASV, and internal scans must be authenticated. |
| Cloud infrastructures | Recommendations offered for cloud usage. | Focuses on more enhanced and flexible cloud security. |
| Security training | Security awareness training required, but limited guidance is offered. | More comprehensive training required, more focus on roles and responsibilities. |
| Wireless environments | Input offered to ensure more secure wireless networking. | Additional enhancements and requirements for modernization. |
| Reporting | More specific guidelines, less flexibility. | Reports require more details, may need customized and on-demand reports, more evidence is required. |
| Software DevOps | Secure Software Lifecycle (SLC) requirements are outlined. | Additional security requirements are introduced. |
| Encryption | Encryption is specified but with limited details. | Expanded to ensure passwords are protected against misuse. |
| Scanning frequency | Specified but not risk based. | Updated to ensure scanning is risk-based and related to analyses. |
| Custom software | Specifies protection but without specific guidelines. | Inventories must be maintained to facilitate patching. |
How Qualys Can Help
Below are a few examples of specific new PCI DSS 4.0 requirements with details about what they mean and how Qualys solutions can help ensure compliance.
| PCI DSS 4.0 New Requirement | What it Means? | How Qualys Helps? |
|---|---|---|
| 5.3.2.1: The frequency of periodic malware scans is based on the entity’s targeted risk analysis per Requirement 12.3.1. | Each PCI DSS requirement that provides flexibility for how frequently it is performed must be supported by a targeted risk analysis that is documented and includes threat identification, threat factors, risk priorities, etc. | The Qualys Enterprise TruRisk™ Platform lets you prioritize risk by overall business impact and remediate efficiently with risk-based patching, AI-powered adaptive mitigation, and an integrated workflow across teams. Several Qualys apps also detect and protect against malware. |
| Req 6.3.2: An inventory of bespoke or custom software and open source or third-party components incorporated into software is maintained to facilitate vulnerability and patch management. | To address this requirement, you should be able to write your own vulnerability detection logic that’s designed to detect vulnerabilities in first-party custom applications. | Qualys Custom Assessment and Remediation (CAR) is specifically designed to help you create your own detection logic to ensure results are fully integrated with Qualys out-of-the-box scanning results. |
| Req 8.6.3: Passwords/ passphrases for accounts used by applications and systems are protected against misuse. | New requirements were added to ensure account privileges, Multi-factor Authentication (MFA), and password complexity. It’s important to ensure your configuration assessment solution is up to date with these new requirements. | Qualys Policy Compliance was updated to meet these new requirements by ensuring full protection against misuse. |
| 10.4.1.1: Automated mechanisms are used to perform audit log reviews. | This covers the importance of security events and logs, in that all audit logs are to be reviewed to identify anomalies or suspicious activity. | This includes File Integrity Monitoring (FIM) solutions, and Qualys FIM covers this by monitoring for file anomalies or suspicious activity and logging file changes. |
| 10.7.2: Failures of critical security control systems are detected, alerted, and addressed promptly, including but not limited to failure of the following critical security control systems: Network security controls, IDS/IPS, FIM… | Failures of critical security control systems, such as change-detection mechanisms, must be detected, alerted, and addressed promptly. | Qualys FIM meets this requirement with continuous file monitoring and alerts for failures. |
| Req 11.3.1.2 and 11.3.2: Internal scans are performed via authenticated scanning. External vulnerability scans are performed as follows: At least once every three months. Via an Approved Scanning Vendor (ASV). | Relates to vulnerability management and specifically the new requirements call for authenticated internal scanning as well as external scanning performed by an ASV. | Qualys Vulnerability Management, Detection & Response (VMDR) provides authenticated internal scanning and Qualys is an ASV capable of performing external scanning to meet these requirements. |
| Req 11.3.1.1: All other applicable vulnerabilities (those not ranked as high-risk or critical per the entity’s vulnerability risk rankings at Requirement 6.2.1) are addressed periodically based on the entity’s targeted risk analysis per Requirement 12.3.1. | This focuses on addressing lower ranked vulnerabilities at a frequency in accordance with the entity’s risk. Adding this new requirement to an older 6.3.3 requirement for patching critical or high-security vulnerabilities within one month of release emphasizes the importance of an integrated patch solution. | Qualys VMDR and Patch Management (PM) allow you to prioritize patching based on risk and automate as much as possible to ensure rapid patch deployment. The Qualys Enterprise TruRisk™ Platform lets you prioritize risk by overall business impact and remediate efficiently with risk-based patching. |
Executive Audit-Ready Dashboard for PCI DSS 4.0 Provided by Qualys Enterprise TruRisk Platform
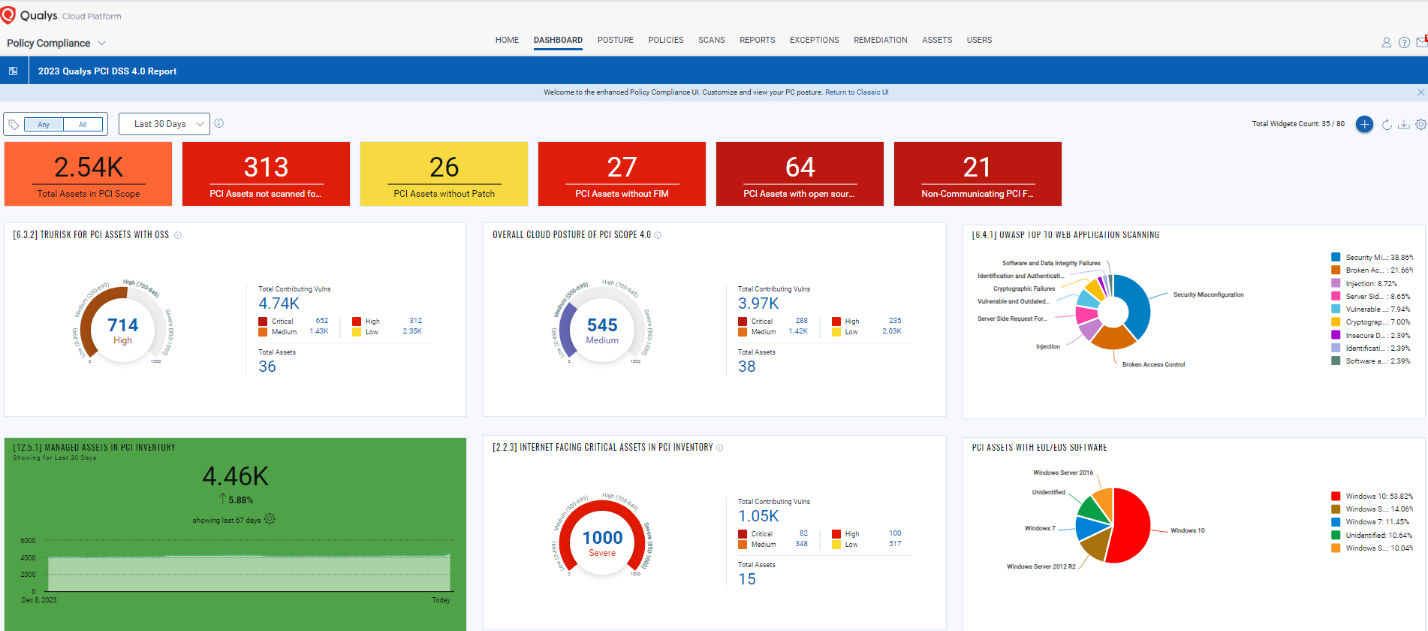
Qualys Enterprise TruRisk Platform Apps for PCI DSS 4.0
The Qualys Enterprise TruRisk Platform includes more than a dozen apps that can help ensure audit-ready compliance with PCI DSS 4.0.
| Qualys App | PCI DSS 4.0 Benefits |
|---|---|
| Qualys Policy Compliance (PC) | Enables continuous assessment of the cardholder data environment. Qualys PC provides a ready-to-use mandate-based template for PCI DSS 4.0 consisting of security checks that automate the assessment of in-scope PCI assets. These checks automatically scan technical secure configuration assessment requirements. |
| Qualys Security Assessment Questionnaire (SAQ) | Helps mid-sized and smaller enterprises use an instrument prescribed by PCI DSS 4.0 called a Self-Assessment Questionnaire (SAQ). As the link explains, there are nine different SAQs that correspond to your type of organization and environment. Eligible organizations can use the SAQ to self-evaluate their compliance with PCI DSS. Validation results are submitted to the organization’s acquiring bank or payment brand(s) with an Attestation of Compliance. |
| Qualys Vulnerability Management, Detection, and Response (VMDR) | A foundational solution for managing CDE cyber risks (Req. 2, 5, 6, 11). It addresses the third goal for a CDE vulnerability management program and Requirement 11’s need for regularly testing the security of CDE systems and networks. VMDR excels at detecting internal and external risks and efficiently responding to vulnerabilities. Authenticated scanning is a new PCI DSS 4.0 requirement. Unlike other scanners, VMDR performs authenticated scans, such as for certificate inventory. VMDR also includes Qualys PCI ASV Compliance to ensure compliance for external scans, which require ASV. |
| Qualys Web Application Scanning (WAS) | Continuously detects vulnerabilities and misconfigurations of CDE internal and external-facing web applications (Req. 6, 11). This app finds malware in web apps and informs DevOps teams on exposed payment data and other PII. |
| Qualys File Integrity Monitoring (FIM) | Provides “low-noise” CDE integrity monitoring efforts and compliance (Req. 1, 10, 11, 12), including unauthorized modification and change detection that accurately separates false alerts from positive hits and allows for whitelisting. This is important for new requirement 11.3.1.1 as auditors will be more restrictive in not allowing low level alerts to be ignored. Qualys FIM also includes File Access Monitoring (FAM) to alert on unauthorized file access and agentless network device support. Both are now needed to comply with new PCI DSS 4.0 requirements. |
| Qualys CyberSecurity Asset Management (CSAM) | Includes External Attack Surface Management (EASM) and provides an accurate, context-rich inventory of all CDE cyber assets to identify security gaps (Req. 2) and CSAM provides full visibility and control of the CDE’s external attack surface (Req. 2, 12). |
| Qualys Patch Management (PM) | Enables automating the entire patching process for operating systems, mobile devices and third-party applications – even for remote devices within the cardholder data environment (Req. 1, 6, 10, 11). |
| Custom Assessment & Remediation (CAR) | PCI DSS 4.0 requires organizations to maintain an up-to-date inventory of all bespoke and custom software, including APIs. CAR creates reusable custom detections and remediations while allowing for the deployment of custom configurations. |
| Qualys TotalCloud (TC) | PCI DSS 4.0 includes several requirements that refer to cloud controls, such as access controls, monitoring and logging, incident response, patching and updates, scans, and more. Qualys TotalCloud can measure risk with 360-degree scanning to detect vulnerabilities and detect malware with up to 99 percent accuracy. |
| Qualys Multi-Vector Endpoint Detection and Response (EDR) | EDR is recommended to integrate vulnerability management of the CDE with endpoint threat detection and response (Req. 5, 12). |
| Qualys Context XDR | Extended Detection and Response should be added to accelerate the remediation of complex, advanced threats to the CDE using MITRE ATT&CK-driven threat hunting and analytics (Req. 10). |
Learn How the Qualys Platform Helps You Pass PCI DSS 4.0 Audits
PCI DSS 4.0 covers a broad range of requirements, and many of these elements represent standard best practices for implementing and maintaining a comprehensive enterprise cybersecurity program. With various integrated Qualys security applications, such as VMDR, Web Application Scanning, Policy Compliance, FIM, Patch Management, CAR and several others, the Qualys Enterprise TruRisk Platform can play a key role to help drive your PCI DSS 4.0 compliance process.
Qualys experts have created a whitepaper to help you better understand PCI DSS 4.0, what’s new, and which Qualys applications should be used (and how) to address PCI DSS 4.0 requirements.