Microsoft and Adobe Patch Tuesday, July 2024 Security Update Review
Last updated on: July 10, 2024
Table of Contents
- Microsoft Patch Tuesday for July 2024
- Adobe Patches for July 2024
- Zero-day Vulnerabilities Patched in July Patch Tuesday Edition
- Critical Severity Vulnerabilities Patched in July Patch Tuesday Edition
- Other Microsoft Vulnerability Highlights
- Microsoft Release Summary
- Discover and Prioritize Vulnerabilities inVulnerability Management, Detection & Response (VMDR)
- Rapid Response withPatch Management (PM)
- EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
- Qualys Monthly Webinar Series
July’s Patch Tuesday brings a midsummer wave of updates, addressing critical vulnerabilities and enhancing security across the Microsoft ecosystem. Let’s discover the highlights from Microsoft’s Patch Tuesday updates for July 2024.
Microsoft Patch Tuesday for July 2024
Microsoft Patch Tuesday’s July 2024 edition addressed 142 vulnerabilities, including five critical and 134 important severity vulnerabilities. In this month’s security updates, Microsoft has addressed four zero-day vulnerabilities known to be exploited in the wild. Microsoft did not address any vulnerabilities in Microsoft Edge (Chromium-based).
Microsoft Patch Tuesday, July edition includes updates for vulnerabilities in Microsoft Office and Components, .NET and Visual Studio, Windows Kernel, Windows DHCP Server, Windows TCP/IP, Windows Internet Connection Sharing (ICS), Microsoft Streaming Service, Windows Hyper-V, Microsoft Windows Codecs Library, and more.
Microsoft has fixed several flaws in multiple software, including Spoofing, Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Security Feature Bypass, and Remote Code Execution (RCE).
The July 2024 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
| Spoofing Vulnerability | 7 | Important: 7 |
| Denial of Service Vulnerability | 17 | Important: 17 |
| Elevation of Privilege Vulnerability | 26 | Important: 26 |
| Information Disclosure Vulnerability | 9 | Important: 9 |
| Remote Code Execution Vulnerability | 59 | Critical: 5 Important: 54 |
| Security Feature Bypass Vulnerability | 24 | Important: 24 |
Adobe Patches for July 2024
Adobe has released three security advisories to address seven vulnerabilities in Adobe Premiere Pro, Adobe InDesign, and Adobe Bridge. Six vulnerabilities are given critical severity ratings. Successful exploitation of these vulnerabilities may lead to arbitrary code execution.
Zero-day Vulnerabilities Patched in July Patch Tuesday Edition
CVE-2024-38112: Windows MSHTML Platform Spoofing Vulnerability
Windows MSHTML is a browser engine that renders web pages frequently connected to Internet Explorer. Even though the Internet Explorer (IE) 11 desktop application has reached the end of support, MSHTML vulnerabilities are still relevant today and are being patched by Microsoft.
An attacker must send the victim a malicious file and convince the victim to execute it.
CISA acknowledged the active exploitation of CVE-2024-38112 by adding it to its Known Exploited Vulnerabilities Catalog and requesting users patch the flaw before July 30, 2024.
CVE-2024-35264: .NET and Visual Studio Remote Code Execution Vulnerability
An attacker must win a race condition to exploit the vulnerability. An attacker may exploit this vulnerability by closing an http/3 stream while the request body is being processed, leading to a race condition. Successful exploitation of the vulnerability may allow an attacker to perform remote code execution on target systems.
CVE-2024-37985 – Arm: CVE-2024-37985 Systematic Identification and Characterization of Proprietary Prefetchers
An attacker must take additional actions before exploitation to successfully prepare the target environment to exploit the vulnerability. On successful exploitation, an attacker may view heap memory from a privileged process running on the server.
CVE-2024-38080: Windows Hyper-V Elevation of Privilege Vulnerability
Windows Hyper-V allows hardware virtualization. IT professionals and software developers use virtualization to test software on multiple operating systems. Hyper-V enables working professionals to perform these tasks smoothly. With the help of Hyper-V, one can create virtual hard drives, virtual switches, and numerous different virtual devices, all of which can be added to virtual machines.
Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
CISA acknowledged the active exploitation of CVE-2024-38080 by adding it to its Known Exploited Vulnerabilities Catalog and requesting users patch the flaw before July 30, 2024.
Critical Severity Vulnerabilities Patched in July Patch Tuesday Edition
CVE-2024-38023: Microsoft SharePoint Server Remote Code Execution Vulnerability
Microsoft SharePoint is a web-based document management and collaboration platform that helps share files, data, news, and resources. The application transforms business processes by providing simple sharing and seamless collaboration.
An authenticated attacker with Site Owner permissions may exploit the vulnerability by uploading a specially crafted file to the targeted SharePoint Server and crafting specialized API requests to trigger the deserialization of the file’s parameters. This would enable the attacker to execute remote code in the SharePoint Server context.
CVE-2024-38060: Microsoft Windows Codecs Library Remote Code Execution Vulnerability
The Microsoft Windows Codecs Library is a collection of codecs that Windows Media Player and other apps use to play and create media files. Codecs can comprise two parts: an encoder that compresses the media file and a decoder that decompresses it.
An authenticated attacker may exploit the vulnerability by uploading a malicious TIFF file to a server.
CVE-2024-38077: Windows Remote Desktop Licensing Service Remote Code Execution Vulnerability
Windows Remote Desktop Services (RDS) licensing, also known as Remote Desktop Protocol (RDP) licensing, is a Windows component allowing users to control a remote computer over a network connection. RDS licensing is important when setting up RDS environments, and the Remote Desktop License Server is a critical element of this process.
An unauthenticated attacker could connect to the Remote Desktop Licensing Service and send a malicious message that may lead to remote code execution.
CVE-2024-38074 & CVE-2024-38076: Windows Remote Desktop Licensing Service Remote Code Execution Vulnerability
An attacker may send a specially crafted packet to a server set up as a Remote Desktop Licensing server. Successful exploitation of the vulnerability may lead to remote code execution.
Other Microsoft Vulnerability Highlights
- CVE-2024-38024 & CVE-2024-38094 is a remote code execution vulnerability in Microsoft SharePoint Server. An authenticated attacker with Site Owner permissions or higher could upload a specially crafted file to the targeted SharePoint Server and craft specialized API requests to trigger the deserialization of the file’s parameters. This would enable the attacker to execute code remotely in the SharePoint Server context.
- CVE-2024-38054 & CVE-2024-38052 are elevation of privilege vulnerabilities in the Kernel Streaming WOW Thunk Service Driver. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
- CVE-2024-38059 is an elevation of privilege vulnerability in Win32k. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
- CVE-2024-38085 is an elevation of privilege vulnerability in the Windows Graphics Component. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
- CVE-2024-38100 is an elevation of privilege vulnerability in Windows File Explorer. Upon successful exploitation of the vulnerability, an attacker could gain administrator privileges.
- CVE-2024-38021 is a remote code execution vulnerability in Microsoft Office. An attacker may craft a malicious link to bypass the Protected View Protocol. An attacker may exploit the vulnerability to leak local NTLM credential information and perform remote code execution.
- CVE-2024-38066 is an elevation of privilege vulnerability in Windows Win32k. Upon successful exploitation of the vulnerability, an attacker could gain administrator privileges.
- CVE-2024-38079 is an elevation of privilege vulnerability in the Windows Graphics Component. An attacker must first log on to the system to exploit this vulnerability. An attacker could then run a specially crafted application to exploit the vulnerability and take control of an affected system. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
- CVE-2024-38099 is the denial-of-service vulnerability in Windows Remote Desktop Licensing Service. An attacker must deduce the necessary algorithm to exploit this vulnerability and gain unauthorized access to specific remote procedure call (RPC) endpoints.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, Windows Remote Desktop, Windows Message Queuing, Windows Performance Monitor, Microsoft Office Outlook, Microsoft Office, Windows Image Acquisition, Line Printer Daemon Service (LPD), Windows Themes, Windows Online Certificate Status Protocol (OCSP), XBox Crypto Graphic Services, Windows PowerShell, Windows Filtering, , NDIS, Windows Distributed Transaction Coordinator, Windows Workstation Service, Microsoft Graphics Component, Windows BitLocker, Windows Win32K – ICOMP, Active Directory Certificate Services, Active Directory Domain Services, Windows Kernel-Mode Drivers, Windows Win32K – GRFX, Windows Enroll Engine, Windows LockDown Policy (WLDP), Windows Remote Desktop Licensing Service, Active Directory Federation Services, Windows Win32 Kernel Subsystem, Azure Kinect SDK, Microsoft Defender for IoT, Microsoft WS-Discovery, Azure CycleCloud, Windows COM Session, Windows Fax and Scan Service, Windows MSHTML Platform, NPS RADIUS Server, Intel, and Active Directory Rights Management Services.
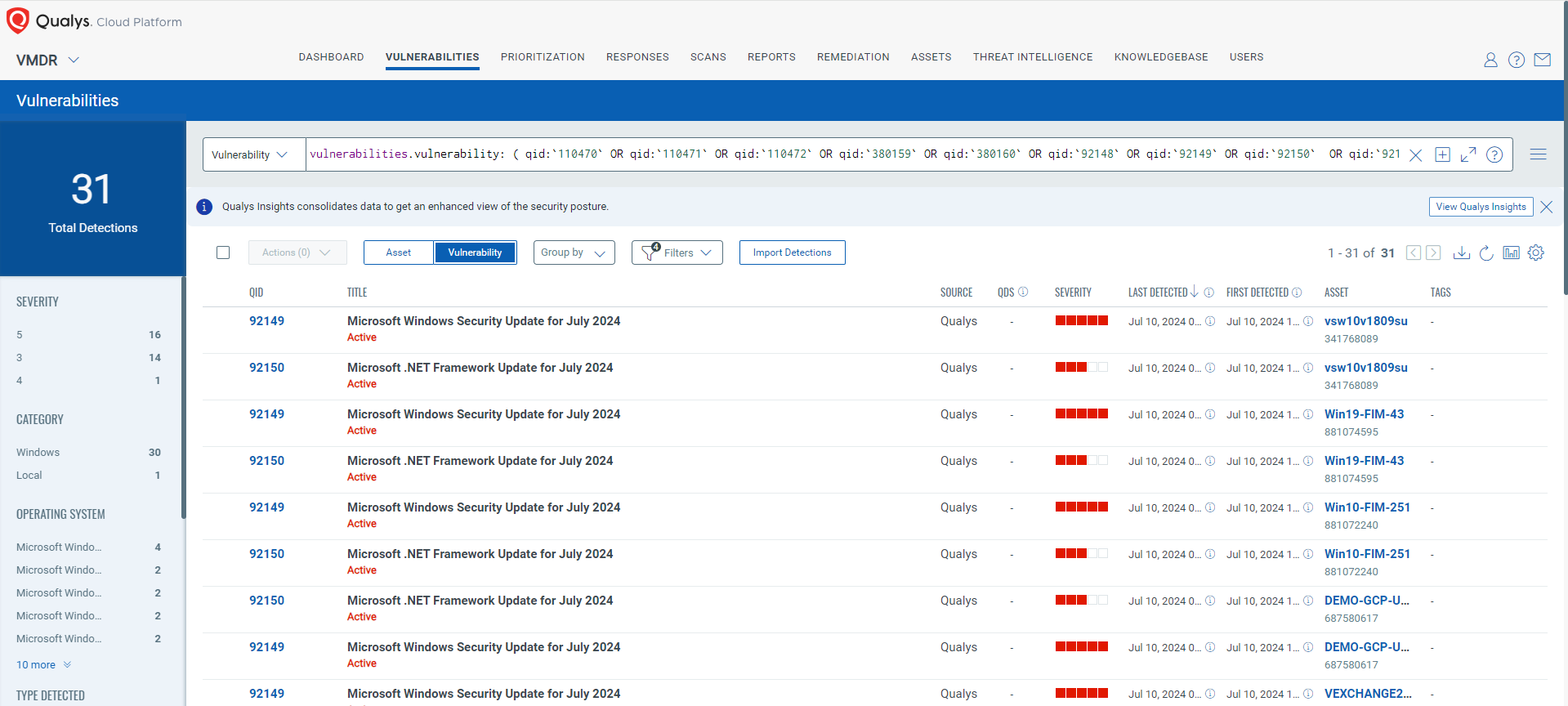
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: ( qid:`110470` OR qid:`110471` OR qid:`110472` OR qid:`380159` OR qid:`380160` OR qid:`92148` OR qid:`92149` OR qid:`92150` OR qid:`92151` OR qid:`92152` OR qid:`92153` )
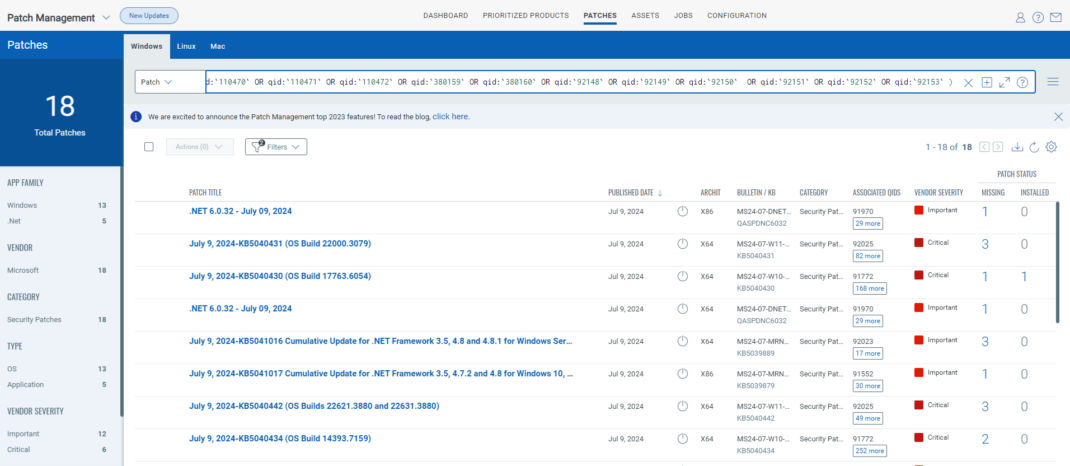
Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid:`110470` OR qid:`110471` OR qid:`110472` OR qid:`380159` OR qid:`380160` OR qid:`92148` OR qid:`92149` OR qid:`92150` OR qid:`92151` OR qid:`92152` OR qid:`92153` )
EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
With Qualys Policy Compliance’s Out-of-the-Box Mitigation or Compensatory Controls reduce the risk of a vulnerability being exploited because the remediation (fix/patch) cannot be done now, these security controls are not recommended by any industry standards such as CIS, DISA-STIG.
Qualys Policy Compliance team releases these exclusive controls based on Vendor-suggested Mitigation/Workaround.
Mitigation refers to a setting, common configuration, or general best practice, existing in a default state, that could reduce the severity of exploitation of a vulnerability.
A workaround is a method, sometimes used temporarily, for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned.
The following Qualys Policy Compliance Control IDs (CIDs), and System Defined Controls (SDC) have been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:
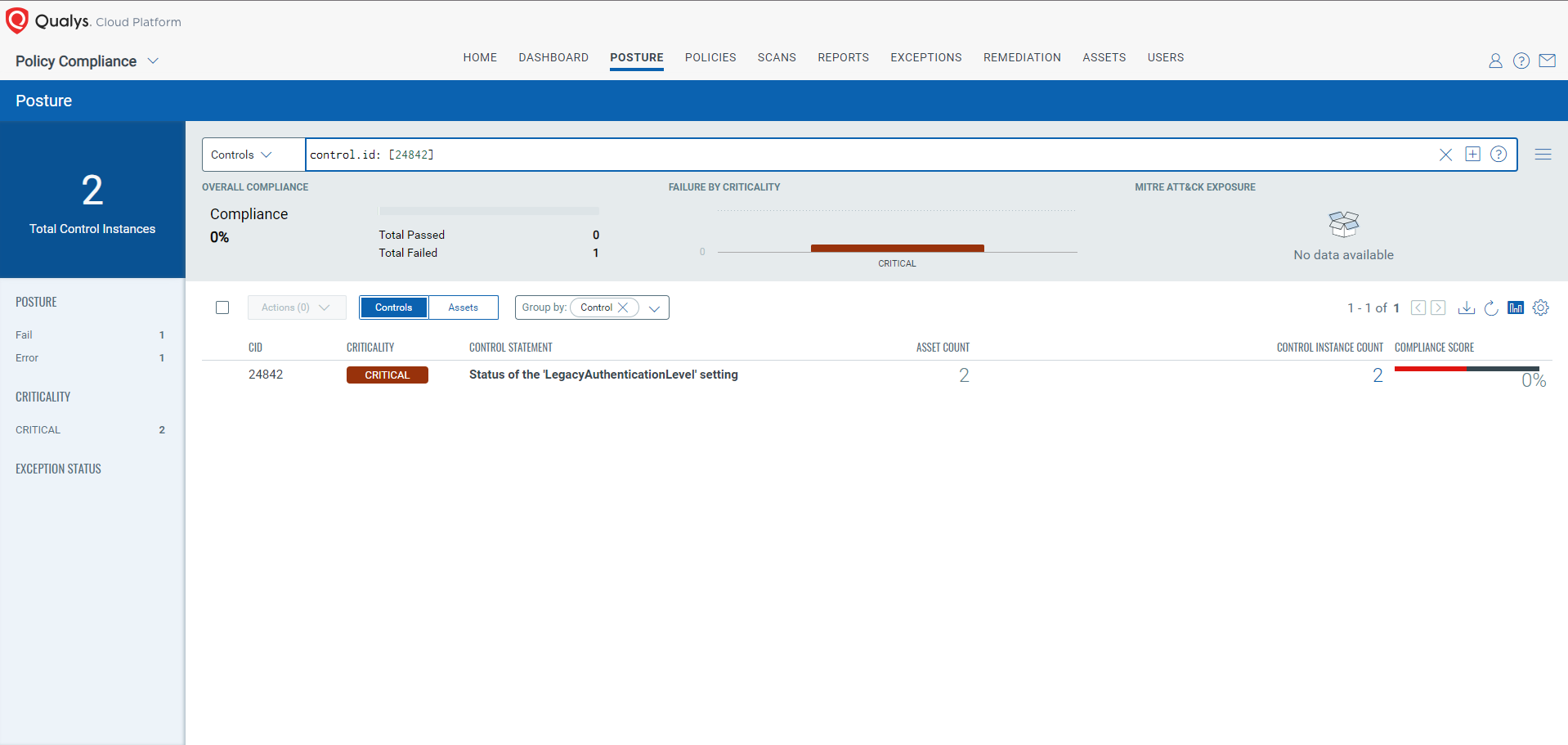
CVE-2024-38061: DCOM Remote Cross-Session Activation Elevation of Privilege Vulnerability
This vulnerability has a CVSS:3.1 7.5 / 6.5
Policy Compliance Control IDs (CIDs):
- 24842 Status of the ‘LegacyAuthenticationLevel’ setting
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [24842]
CVE-2024-38077: Windows Remote Desktop Licensing Service Remote Code Execution Vulnerability
This vulnerability has a CVSS:3.1 9.8 / 8.5
Policy Compliance Control IDs (CIDs):
- 9786 Status of the ‘Remote Desktop Licensing’ service
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [9786]
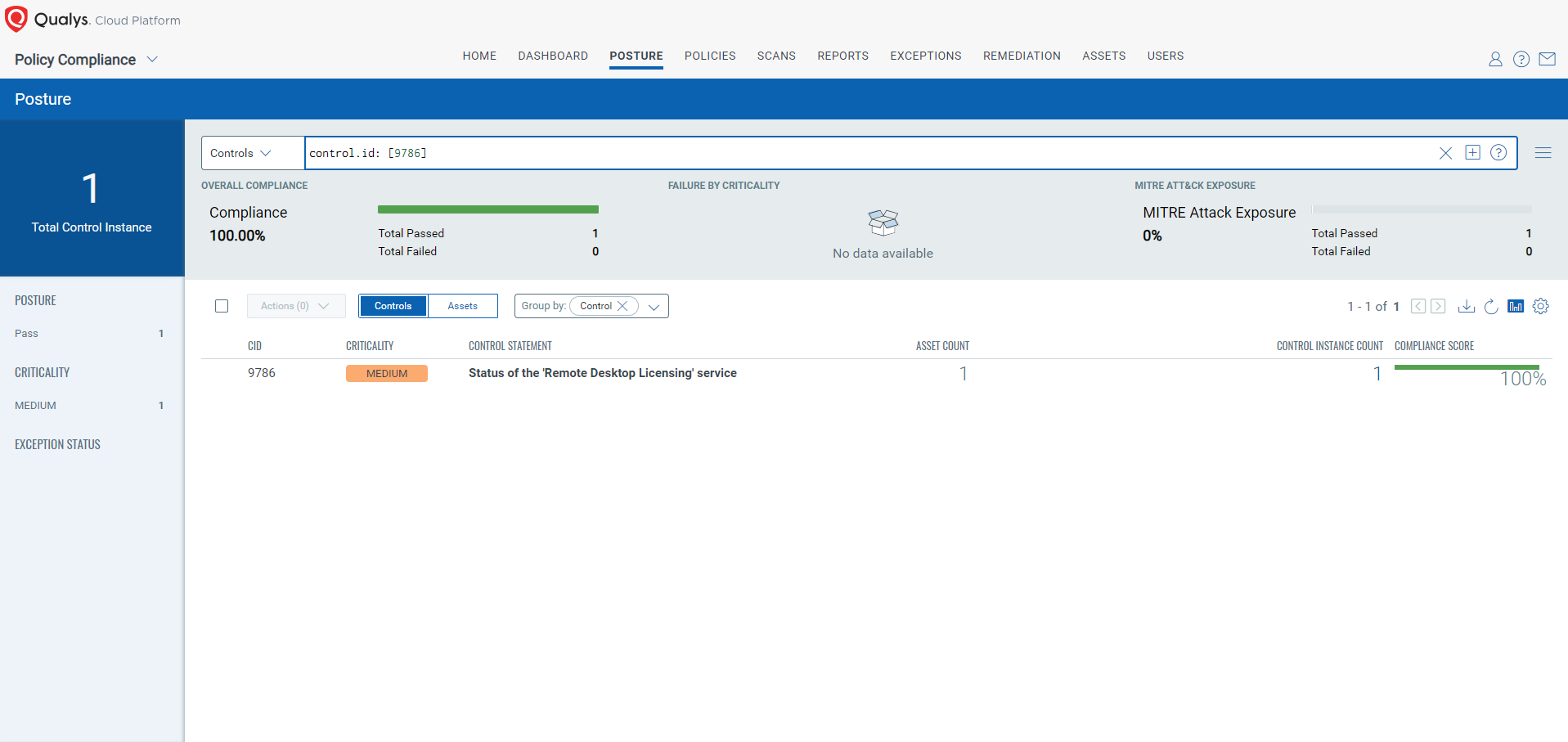
CVE-2024-38074: Windows Remote Desktop Licensing Service Remote Code Execution Vulnerability
This vulnerability has a CVSS:3.1 9.8 / 8.5
Policy Compliance Control IDs (CIDs):
- 9786 Status of the ‘Remote Desktop Licensing’ service
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [9786]
CVE-2024-38076: Windows Remote Desktop Licensing Service Remote Code Execution Vulnerability
This vulnerability has a CVSS:3.1 9.8 / 8.5
Policy Compliance Control IDs (CIDs):
- 9786 Status of the ‘Remote Desktop Licensing’ service
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [9786]
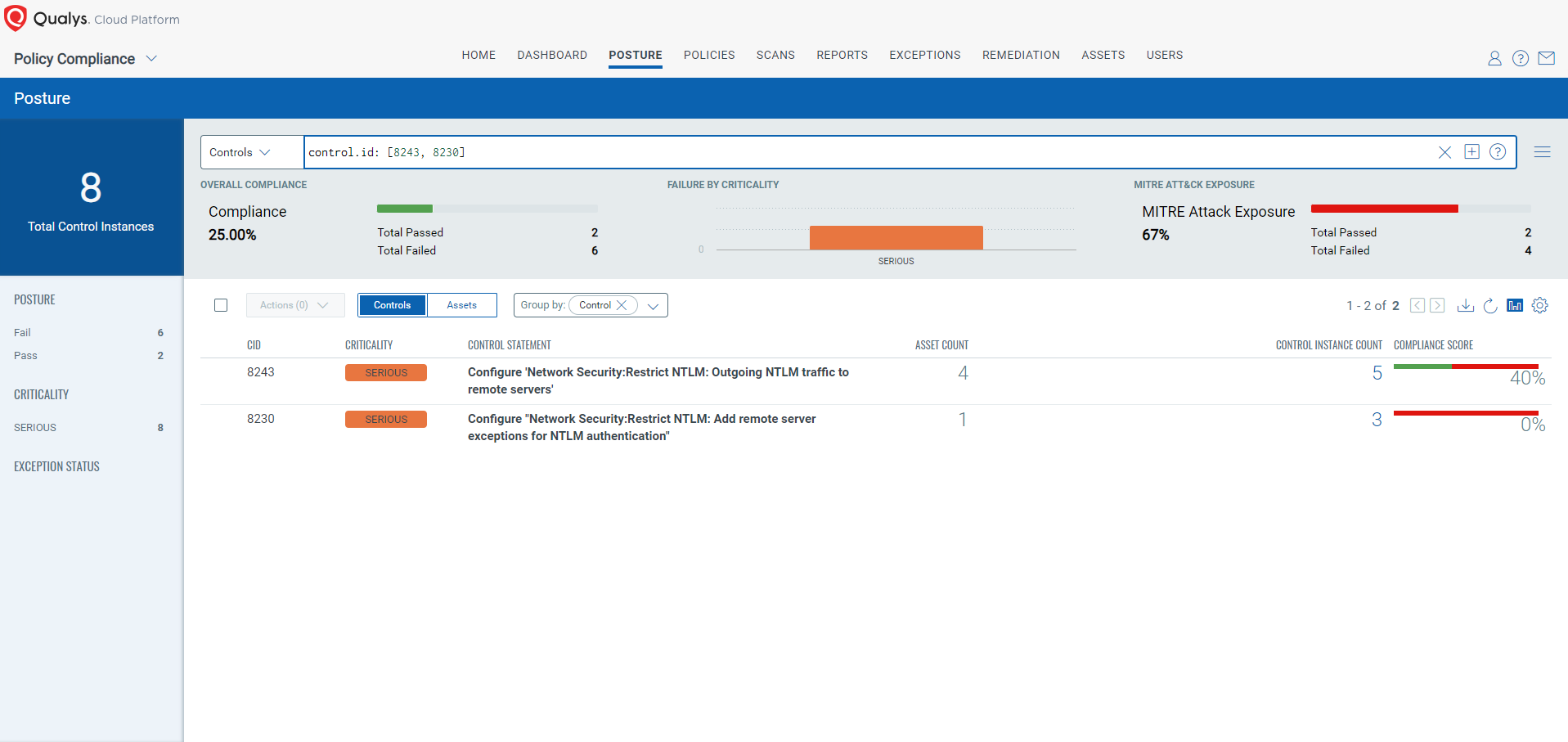
CVE-2024-38030: Windows Themes Spoofing Vulnerability
This vulnerability has a CVSS:3.1 6.5 / 5.7
Policy Compliance Control IDs (CIDs):
- 8243 Configure ‘Network Security:Restrict NTLM: Outgoing NTLM traffic to remote servers’
- 8230 Configure ‘Network Security:Restrict NTLM: Add remote server exceptions for NTLM authentication’
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [8243, 8230]
The next Patch Tuesday falls on August 13, and we’ll be back with details and patch analysis. Until next Patch Tuesday, stay safe and secure. Be sure to subscribe to the ‘This Month in Vulnerabilities and Patch’s webinar.’
Qualys Monthly Webinar Series

The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those that are a part of this month’s Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
Join the webinar
This Month in Vulnerabilities & Patches