Microsoft and Adobe Patch Tuesday, September 2024 Security Update Review
Last updated on: September 11, 2024
Table of Contents
- Microsoft Patch Tuesday for September 2024
- Adobe Patches for September 2024
- Zero-day Vulnerabilities Patched in September Patch Tuesday Edition
- Critical Severity Vulnerabilities Patched in September Patch Tuesday Edition
- Other Microsoft Vulnerability Highlights
- Microsoft Release Summary
- Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
- Rapid Response with Patch Management (PM)
- Qualys Monthly Webinar Series
Microsoft’s September Patch Tuesday updates are out, addressing a range of vulnerabilities across multiple products. Let’s dive into the key updates and their implications.
Microsoft Patch Tuesday for September 2024
Microsoft Patch’s Tuesday, September 2024 edition addressed 79 vulnerabilities, including six critical and 71 important severity vulnerabilities.
In this month’s updates, Microsoft has addressed four zero-day vulnerabilities known to be exploited in the wild.
Microsoft has not addressed vulnerabilities in Microsoft Edge (Chromium-based) in this month’s edition.
Microsoft Patch Tuesday, September edition includes updates for vulnerabilities in Microsoft Office and Components, Windows Hyper-V, Windows DHCP Server, Microsoft Streaming Service, Microsoft Management Console, Windows MSHTML Platform, Microsoft Dynamics 365 (on-premises), and more.
Microsoft has fixed several flaws in multiple software, including Spoofing, Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Security Feature Bypass, and Remote Code Execution (RCE).
The September 2024 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
| Spoofing Vulnerability | 3 | Important: 3 |
| Denial of Service Vulnerability | 8 | Important: 8 |
| Elevation of Privilege Vulnerability | 30 | Critical: 3 Important: 27 |
| Information Disclosure Vulnerability | 11 | Important: 11 |
| Remote Code Execution Vulnerability | 23 | Critical: 4 Important: 19 |
| Security Feature Bypass Vulnerability | 4 | Important: 4 |
Adobe Patches for September 2024
Adobe has released eight security advisories to address 28 vulnerabilities in Adobe Media Encoder, Adobe Audition, Adobe After Effects, Adobe Premiere Pro, Adobe Illustrator, Adobe Acrobat and Reader, Adobe ColdFusion, and Adobe Photoshop. 19 of these vulnerabilities are given critical severity ratings. Successful exploitation of these vulnerabilities may lead to arbitrary code execution.
Zero-day Vulnerabilities Patched in September Patch Tuesday Edition
CVE-2024-38014: Windows Installer Elevation of Privilege Vulnerability
Windows Installer is a Windows operating system component that allows users to install and uninstall software. It’s been a part of Windows since Windows 2000 and is the preferred installation format for many popular software applications.
An attacker may gain SYSTEM privileges on successful exploitation of the vulnerability.
CISA acknowledged the active exploitation of CVE-2024-38014 by adding it to its Known Exploited Vulnerabilities Catalog and requesting users patch the flaw before October 1, 2024.
CVE-2024-38217: Windows Mark of the Web Security Feature Bypass Vulnerability
The Mark of the Web (MoTW) is a Windows security feature that identifies files downloaded from the internet as potentially unsafe.
An attacker could host a malicious file on an attacker-controlled server to exploit the vulnerability. The attacker must convince a targeted user to download and open the malicious file. Successful exploitation of the vulnerability may allow the attacker to interfere with the Mark of the Web functionality.
CISA acknowledged the active exploitation of CVE-2024-38217 by adding it to its Known Exploited Vulnerabilities Catalog and requesting users patch the flaw before October 1, 2024.
CVE-2024-38226: Microsoft Publisher Security Features Bypass Vulnerability
Microsoft Publisher is a desktop publishing application that helps users create professional-looking publications. It’s part of the Microsoft 365 suite and useful for industries requiring high-quality publication design.
An attacker who exploits this vulnerability could bypass Office macro policies blocking untrusted or malicious files.
CISA acknowledged the active exploitation of CVE-2024-38226 by adding it to its Known Exploited Vulnerabilities Catalog and requesting users patch the flaw before October 1, 2024.
CVE-2024-43491: Microsoft Windows Update Remote Code Execution Vulnerability
The stack vulnerability allows an attacker to perform remote code execution.
Microsoft mentioned in the advisory that “Microsoft is aware of a vulnerability in Servicing Stack that has rolled back the fixes for some vulnerabilities affecting Optional Components on Windows 10, version 1507 (initial version released July 2015). This means that an attacker could exploit these previously mitigated vulnerabilities on Windows 10, version 1507 (Windows 10 Enterprise 2015 LTSB and Windows 10 IoT Enterprise 2015 LTSB) systems that have installed the Windows security update released on March 12, 2024—KB5035858 (OS Build 10240.20526) or other updates released until August 2024. This vulnerability does not impact all later versions of Windows 10.”
CISA acknowledged the active exploitation of CVE-2024-43491 by adding it to its Known Exploited Vulnerabilities Catalog and requesting users patch the flaw before October 1, 2024.
Critical Severity Vulnerabilities Patched in September Patch Tuesday Edition
CVE-2024-38018: Microsoft SharePoint Server Remote Code Execution Vulnerability
Microsoft SharePoint is a web-based document management and collaboration platform that helps share files, data, news, and resources. The application transforms business processes by providing simple sharing and seamless collaboration.
In a network-based attack, an authenticated attacker with minimum Site Member permissions could execute code remotely on the SharePoint Server.
CVE-2024-38216 & CVE-2024-38220: Azure Stack Hub Elevation of Privilege Vulnerability
Azure Stack Hub is part of the Azure Stack portfolio. The software enables users to run apps in an on-premises environment and deliver Azure services in the user’s datacenter.
Successful exploitation of the vulnerability may allow an attacker to gain unauthorized access to system resources. The vulnerability may also allow an attacker to perform actions with the same privileges as the compromised process.
CVE-2024-43464: Microsoft SharePoint Server Remote Code Execution Vulnerability
An attacker may upload a specially crafted file to the targeted SharePoint Server and craft specialized API requests to trigger the deserialization of the file’s parameters. An authenticated attacker with Site Owner permissions may exploit the vulnerability to execute arbitrary code in the context of SharePoint Server.
CVE-2024-38119: Windows Network Address Translation (NAT) Remote Code Execution Vulnerability
Network Address Translation (NAT) allows multiple devices to share a public IP address. It’s commonly implemented in routers, firewalls, and residential gateways.
An attacker must win a race condition to exploit the vulnerability. An attacker must access the restricted network to exploit the vulnerability successfully.
CVE-2024-38194: Azure Web Apps Elevation of Privilege Vulnerability
Azure Web Apps allow users to host web applications in various programming languages such as .NET, Java, and Node. js, Python, and PHP. It provides automatic scaling, load balancing, and high availability to ensure your application is always up and running.
An authenticated attacker may exploit an improper authorization vulnerability in Azure Web Apps to elevate privileges over a network.
Other Microsoft Vulnerability Highlights
- CVE-2024-38227 & CVE-2024-38228 are remote code execution vulnerabilities in Microsoft SharePoint Server. An authenticated attacker with Site Owner permissions may exploit the vulnerability to execute arbitrary code in the context of SharePoint Server.
- CVE-2024-38237 is an elevation of privilege vulnerability in Kernel Streaming WOW Thunk Service Driver. An attacker who successfully exploited this vulnerability could gain SYSTEM privileges.
- CVE-2024-38238, CVE-2024-38241, CVE-2024-38242, CVE-2024-38243, CVE-2024-38244, & CVE-2024-38245 are elevation of privilege vulnerabilities in Kernel Streaming Service Driver. On successful exploitation, an attacker may gain SYSTEM privileges.
- CVE-2024-38246 is an elevation of privilege vulnerability in Win32k. An attacker must win a race condition to exploit the vulnerability. On successful exploitation, an attacker may gain SYSTEM privileges.
- CVE-2024-38247 is an elevation of privilege vulnerability in the Windows Graphics Component. On successful exploitation, an attacker may gain SYSTEM privileges.
- CVE-2024-38249 is an elevation of privilege vulnerability in the Windows Graphics Component. An attacker who successfully exploited this vulnerability could gain SYSTEM privileges.
- CVE-2024-38252 & CVE-2024-38253 are elevation of privilege vulnerabilities in the Windows Win32 Kernel Subsystem. An attacker who successfully exploited this vulnerability could gain SYSTEM privileges.
- CVE-2024-43457 is an elevation of privilege vulnerability in the Windows Setup and Deployment. On successful exploitation, an attacker may gain SYSTEM privileges.
- CVE-2024-43487 is a security feature bypass vulnerability in Windows Mark of the Web. Successful exploitation of the vulnerability may allow an attacker to bypass the SmartScreen user experience. An attacker must send the user a malicious file and convince them to open it to exploit the vulnerability.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, Windows TCP/IP, SQL Server, Windows Security Zone Mapping, Windows Installer, Microsoft Office SharePoint, Windows PowerShell, Windows Network Address Translation (NAT), Azure Network Watcher, Azure Web Apps, Azure Stack, Windows Mark of the Web (MOTW), Dynamics Business Central, Microsoft Office Publisher, Windows Standards-Based Storage Management Service, Windows Remote Desktop Licensing Service, Windows Network Virtualization, Windows Kerberos, Windows Remote Access Connection Manager, Windows Win32K – GRFX, Microsoft Graphics Component, Windows Storage, Windows Win32K – ICOMP, Windows Authentication Methods, Windows Kernel-Mode Drivers, Windows AllJoyn API, Windows Setup and Deployment, Microsoft Office Visio, Microsoft Office Excel, Azure CycleCloud, Windows Admin Center, Power Automate, Microsoft Outlook for iOS, Windows Update, Microsoft AutoUpdate (MAU), and Windows Libarchive.
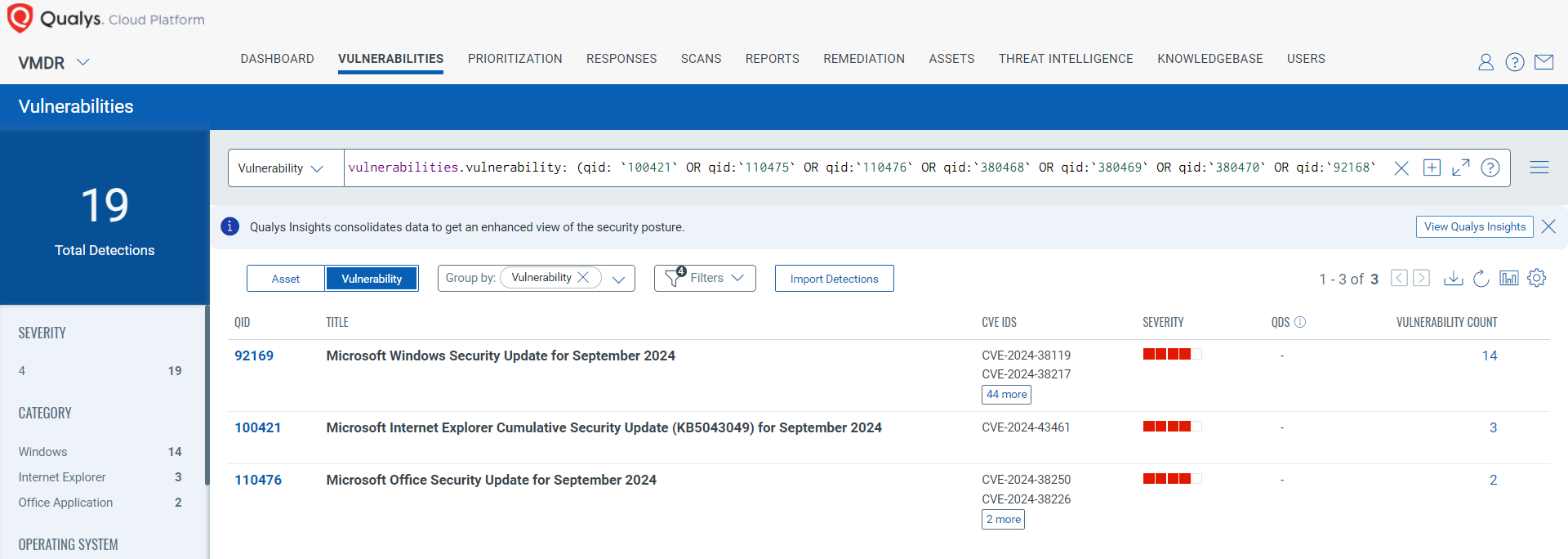
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: (qid: `100421` OR qid:`110475` OR qid:`110476` OR qid:`380468` OR qid:`380469` OR qid:`380470` OR qid:`92168` OR qid:`92169` OR qid:`92170` OR qid:`92171` OR qid:`92172`)
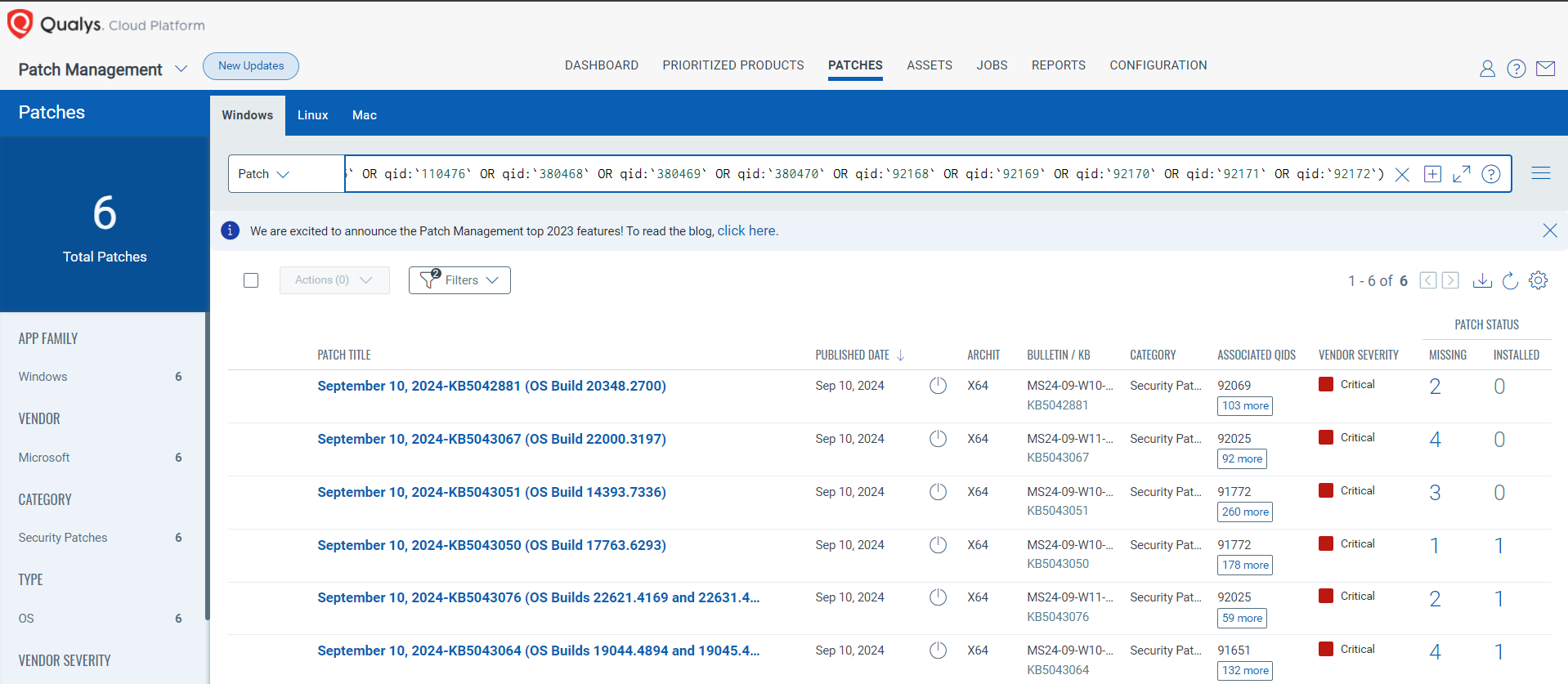
Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
(qid: `100421` OR qid:`110475` OR qid:`110476` OR qid:`380468` OR qid:`380469` OR qid:`380470` OR qid:`92168` OR qid:`92169` OR qid:`92170` OR qid:`92171` OR qid:`92172`)
The next Patch Tuesday falls on October 8, and we’ll be back with details and patch analysis. Until next Patch Tuesday, stay safe and secure. Be sure to subscribe to “This Month in Vulnerabilities and Patch’s webinar.’
Qualys Monthly Webinar Series
The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those that are a part of this month’s Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
Join the webinar
This Month in Vulnerabilities & Patches