Oracle Plugs Struts and Shadow Brokers hole along with 299 Total Vulnerabilities
Today Oracle released a total of 299 new security fixes across all product families. It is important to note that it fixed 25 instances of the infamous Apache Struts vulnerability which could allow a remote attacker to take complete control of the server running Struts. The struts fix was applied to 19 instances of Oracle Financial Services Applications along with WebCenter, WebLogic, Siebel, Oracle Communications, MySQL and Oracle Retail.
Oracle also released Patch 25878798 for Solaris 10 and 11.3 which fixed the second Shadow Brokers EXTREMEPARR vulnerability CVE-2017-3622. EXTREMEPARR has a CVSS Base Score of 7.8, and if successfully exploited allows a local privilege escalation in the ‘dtappgather’ component. The other Shadow Brokers vulnerability CVE-2017-3623 (a.k.a. “Ebbisland” or “Ebbshave”) was previously addressed by Oracle in several Solaris 10 patch distributions issued since January 26th 2012 and does not affect Solaris 11.
Out of the 299 total fixes MySQL, Financial Services, Retail and Fusion Middleware take the lion’s share of fixes and the distribution is shown in the chart below. Majority of the vulnerabilities in the Financial Services, Retail and Fusion Middleware could be exploited via the HTTP protocol and attackers can take complete control of the system remotely without the need of any credentials.
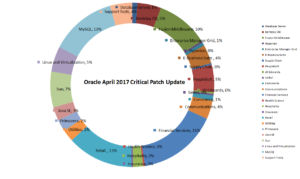
In databases, MySQL has seen its share of vulnerabilities rise drastically as compared to the Oracle Database server and today’s release was no different with 39 MySQL bugs fixed out of which 11 could be remotely exploitable without authentication. This is a large number as compared to just 3 bugs in the Oracle Database Server. All vulnerabilities for MySQL could be exploited using the MySQL protocol used by clients to connect to the database server and organizations should create a details inventory of their MySQL servers for their exposure within the organization and outside.
Java SE was patched with 8 security fixes out of which 7 are exploitable remotely without authentication. AWT, JCE and other java networking components were affect and could be exploited using FTP, SMTP and multiple other protocols. 21 Sun systems products were patched which included Solaris, Sun ZFS Storage Appliance and Solaris Cluster. Out of these, 8 vulnerabilities can be exploitable remotely. The most affected component in Oracle Linux was the Oracle VM Virtual Box and 6 of these issues are remotely exploitable.
The chart below shows a list of remotely exploitable vulnerabilities in today’s release:
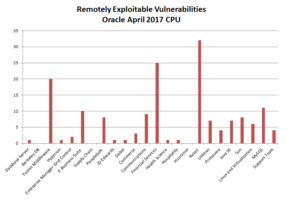
Overall, this was another large security update with 299 fixes from Oracle touching all product lines, fixing Apache Struts embedded into products and patching a total of 162 remotely exploitable vulnerabilities.