The Shadow Brokers Release Zero Day Exploit Tools
On Friday, a hacker group known as The Shadow Brokers publicly released a large number of functional exploit tools. Several of these tools make use of zero-day vulnerabilities, most of which are in Microsoft Windows. Exploiting these vulnerabilities in many cases leads to remote code execution and full system access.
Both end-of-support and current Windows versions are impacted, including Windows 2003, XP, Vista, 7, 2008, 8, and 2012. Microsoft has released patches for each vulnerability across all supported platforms, but will not be releasing patches for end-of-support versions of Windows. It is highly recommended that any end-of-support Windows systems be replaced or isolated, as these systems will often be impacted by new vulnerabilities, without the availability of a patch.
For zero-day vulnerabilities in Operating Systems, you can use your existing asset inventory information from Qualys AssetView, and search for any OS to determine how many vulnerable assets are deployed. This can be done without additional scanning if the data is relatively fresh.
Detecting the Vulnerabilities
Qualys has released five new QIDs to detect these zero-day vulnerabilities:
-
91361 Microsoft Windows SMBv3 Remote Code Execution – Shadow Brokers (ETERNALSYNERGY) MS17-010
-
91359 Microsoft Windows Remote Privilege Escalation – Shadow Brokers (ETERNALROMANCE) MS17-010
-
91360 Microsoft Windows SMBv1 and NBT Remote Code Execution – Shadow Brokers (ETERNALBLUE) MS17-010
-
91357 Microsoft Windows SMBv1 Remote Code Execution – Shadow Brokers (ETERNALCHAMPION) CVE-2017-0146 & CVE-2017-0147
-
53007 IBM Lotus Domino Remote Code Execution – Shadow Brokers (EWORKFRENZY)
We are also updating the QID we mentioned in a previous blog post to include the Shadow Brokers exploit name:
- 87284 Microsoft Internet Information Services 6.0 Buffer Overflow Vulnerability – Shadow Brokers (EXPLODINGCAN)
These new QIDs are used by Qualys Vulnerability Management to detect the vulnerabilities using an authenticated scan or the Qualys Cloud Agent.
Qualys ThreatPROTECT provides one-click access to a list of impacted assets though the Live Feed, as well as a detailed analysis of The Shadow Brokers’ leak, written directly by a vulnerability researcher.
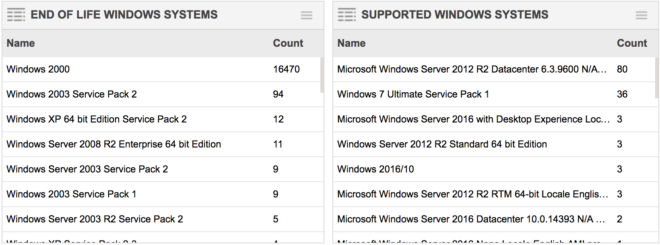
Tracking and Managing Windows Assets
Qualys AssetView can help you locate and track legacy and current Windows assets in dynamic widgets. These widgets can be clicked to get full lists of Windows assets, grouped by Operating System, and the lists can be exported for sending to remediation or evergreening teams.
Blocking Exploits
Qualys Web Application Firewall (WAF) can block any attempts to exploit the “EXPLODINGCAN” vulnerability if upgrading or disabling WebDAV is not an option. Full details are posted here: Protect Against Critical IIS 6.0 Buffer Overflow vulnerability (CVE-2017-7269) with Qualys WAF.
Get Started Now
To start detecting and protecting against critical vulnerabilities, get a Qualys Suite trial. All features described in this article are available in the trial.
EWOKFRENZY not EWORKFRENZY
What about EsteemAudit?