OpenBSD Multiple Authentication Vulnerabilities

Multiple authentication vulnerabilities in OpenBSD have been disclosed by Qualys Research Labs. The vulnerabilities are assigned following CVEs: CVE-2019-19522, CVE-2019-19521, CVE-2019-19520, CVE-2019-19519. OpenBSD developers have confirmed the vulnerabilities and also provided a quick response with patches published in less than 40 hours.
Vulnerability Details
- CVE-2019-19521 – An authentication-bypass vulnerability in OpenBSD’s authentication system: this vulnerability is remotely exploitable in smtpd, ldapd, and radiusd, but its real-world impact should be studied on a case-by-case basis. For example, sshd is not exploitable thanks to its defense-in-depth mechanisms.
- CVE-2019-19520 – Local privilege escalation via “xlock” – On OpenBSD, /usr/X11R6/bin/xlock is installed by default and is set-group-ID “auth”, not set-user-ID; the following check is therefore incomplete and should use issetugid() instead.
- CVE-2019-19522: Local privilege escalation via “S/Key” and “YubiKey” – If the S/Key or YubiKey authentication type is enabled (they are both installed by default but disabled), then a local attacker can exploit the privileges of the group “auth” to obtain the full privileges of the user “root”.
- CVE-2019-19519: Local privilege escalation via “su” – A local attacker can exploit su’s -L option to log in as themselves but with another user’s login class.
For technical details on this vulnerability, please see our security advisory.
Detecting the Vulnerability
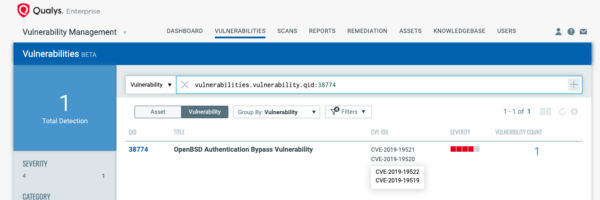
Qualys has issued QID 38774 for Qualys Vulnerability Management that covers authentication vulnerabilities in OpenBSD. This QID is included in signature version VULNSIGS-2.4.762-6.
QID 38774 – This detection includes both remote and authenticated checks:
- Remote – This detection sends a specifically crafted payload over LDAP and SMTP services to authenticate using “-schallenge” remotely.
- Authenticated (OpenBSD) – This executes “syspatch -l” command to check for the presence of patch applied on the system.
You can search for this new QID in AssetView or within the VM Dashboard by using the following QQL query:
vulnerabilities.vulnerability.qid:38774
vulnerabilities.vulnerability.(cveId:`CVE-2019-19519` OR cveId:`CVE-2019-19520` OR cveId:`CVE-2019-19521` OR cveId:`CVE-2019-19522`)
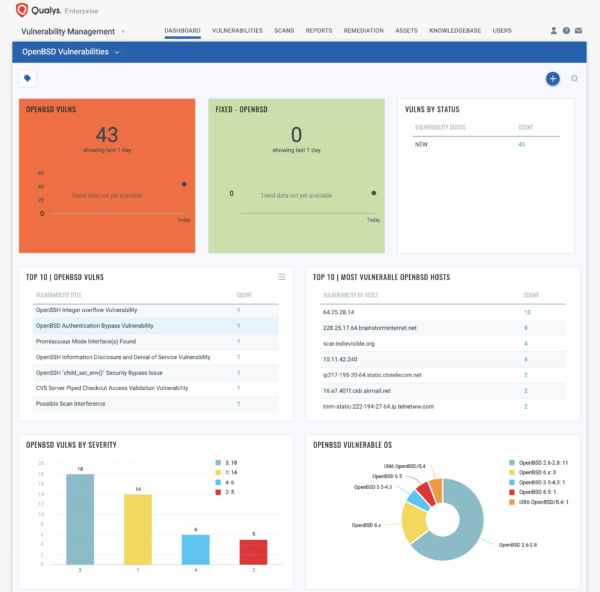
You can also create a Dashboard to track all OpenBSD Vulnerabilities as shown in the template below –
UPDATE:-
Qualys has also provided template information to create OpenBSD Vulnerabilities Dashboard leveraging data in Qualys Vulnerability Management subscription
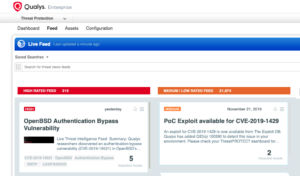
Finding Vulnerable Hosts
The fastest way to locate vulnerable hosts is though the Qualys Threat Protection Live Feed as seen here:
Remediation
To remediate this vulnerability, apply the latest patches for OpenBSD 6.5 and OpenBSD 6.6.
Qualys customers can scan their network with QID 38774 to detect vulnerable assets.
Hi Animesh, it’s strange. When I look in Threat Protect I see a number of assets linked to this, yet when I drill into those assets and click vulnerabilities, I don’t see the QID. Also, when performing an asset search, I get zero results too. Why might this be please? Thanks, Tony
Hi Tony,
Thanks for reaching out. When I performed the same query in Threat Protect, I was able to see vulnerability details on the asset. Please let us know, if this issue still persists. I can also share our lab results and screenshots for reference.
Thanks,