Microsoft Windows SMBv3 Remote Code Execution Vulnerability (CVE-2020-0796)

This month’s Patch Tuesday, Microsoft disclosed a remote code execution vulnerability in SMB 3.1.1 (v3) protocol. Even though initial release of the Patch Tuesday did not mention this vulnerability, details of the issue (CVE-2020-0796) were published accidentally on another security vendor’s blog. Microsoft published security advisory ADV200005 and technical guidance soon after the accidental disclosure of the vulnerability.
UPDATE March 12, 2020: Microsoft updated ADV200005 to include CVE-2020-0796 and released patches for affected Windows systems.
The Vulnerability
A critical remote code execution vulnerability exists in the way that the Microsoft Server Message Block 3.1.1 protocol handles certain requests. An unauthenticated attacker could exploit the vulnerability to execute arbitrary code on SMB server by sending a specially crafted packet to a targeted SMBv3 Server. To exploit the vulnerability against an SMB Client, an unauthenticated attacker would need to configure a malicious SMBv3 Server and convince a user to connect to it.
Affected Operating Systems
- Windows 10 Version 1903 for 32-bit Systems
- Windows 10 Version 1903 for ARM64-based Systems
- Windows 10 Version 1903 for x64-based Systems
- Windows 10 Version 1909 for 32-bit Systems
- Windows 10 Version 1909 for ARM64-based Systems
- Windows 10 Version 1909 for x64-based Systems
- Windows Server, version 1903 (Server Core installation)
- Windows Server, version 1909 (Server Core installation)
Microsoft released patches and have provided workarounds in a security advisory: disable SMBv3 compression and block the 445 TCP port on client computers and firewalls to prevent attackers from exploiting the vulnerability.
Exploits/PoC:
Update: There were no reports of active exploitation or PoC available in public domain at the time of initial release of this post.
On March 12, Kryptos Logic published a proof-of-concept, demonstrating the use of exploit code to crash vulnerable hosts (Denial of Service).
On March 13, a POC was published on GitHub that explained how “CVE-2020-0796 is caused by a lack of bounds checking in offset size, which is directly passed to several subroutines. Passing a large value causes buffer overflow, and crash the kernel. With further work, this could be developed into a RCE exploit.”
Systems with port 445 exposed to the Internet are at high risk for this vulnerability.
Detecting CVE-2020-0796 with Qualys VM
Qualys has issued QID 91614 for Qualys Vulnerability Management that covers CVE-2020-0796 across all impacted operating systems. This QID will be included in signature version VULNSIGS-2.4.837-4, and requires authenticated scanning or the Qualys Cloud Agent. Cloud Agents will automatically receive this new QID as part of manifest version 2.4.837.4-3. Details of the detection are also available at Microsoft Security Alert: March 10, 2020.
QID 91614 : Microsoft Guidance for Disabling SMBv3 Compression Not Applied (ADV200005)
This QID checks if SMBv3 is enabled on the host and if the following workaround is not applied –
“HKLM\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameter”;
DisableCompression -Type DWORD -Value 1
Update: Qualys released QID 91616 to check for patches applied for CVE-2020-0796 across all impacted operating systems using authenticated scanning or the Qualys Cloud Agent. All new changes are included in signature version VULNSIGS-2.4.841-3.
QID 91616: Microsoft Windows SMBv3 Compression Remote Code Execution Vulnerability (KB4551762)
Details on Qualys QIDs 91614 and 91616:
If you have not applied SMBv3 KB4551762 patch or SMBv3 workaround:
QIDs 91614 and 91616 will be posted in the scan results.
If you have applied SMBv3 workaround, but SMBv3 KB4551762 patch is not applied on the host:
QID 91616 will be posted in the scan results.
If SMBv3 KB4551762 patch is applied on the host:
No QID will be posted in the scan result.
Along with the two confirmed vulnerability QIDs, Qualys also released the following IG QID, to help customers track assets on which they have the mitigation applied. This QID can be detected via remote unauthenticated and authenticated scans or via Qualys Cloud Agent.
QID 48086: Microsoft Server Message Block (SMBv3) Compression Disabled
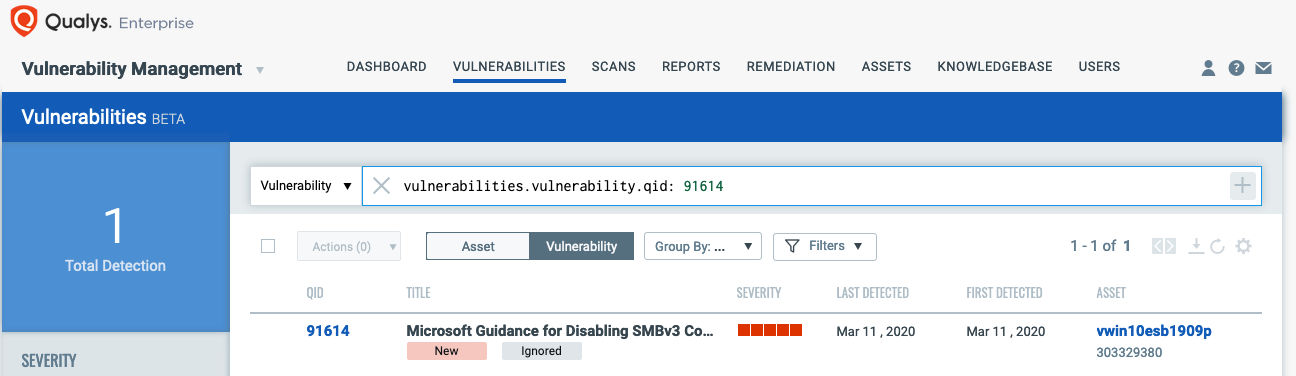
You can search within the VM Dashboard by using the following QQL query:
vulnerabilities.vulnerability.cveIds:CVE-2020-0796
vulnerabilities.vulnerability.qid:91614
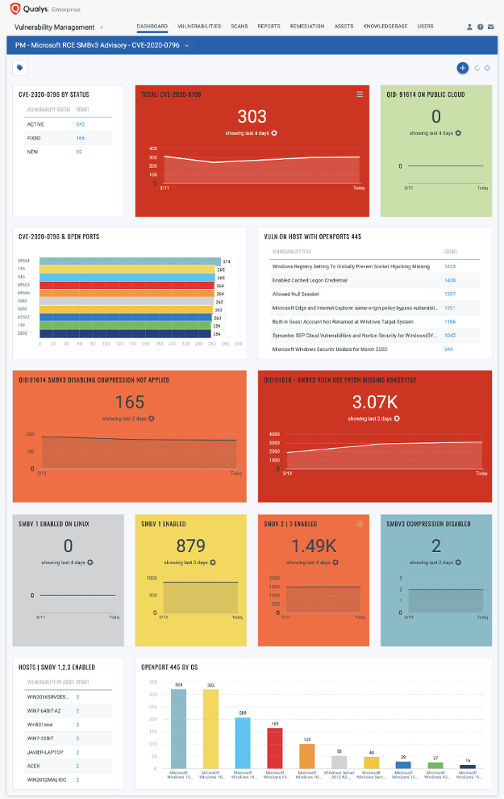
Detection Dashboard
You can also track all hosts impacted by CVE-2020-0796 vulnerability in your environment with the Microsoft RCE SMBv3 Vulnerability Dashboard that leverages data in your Qualys Vulnerability Management subscription, as shown below:
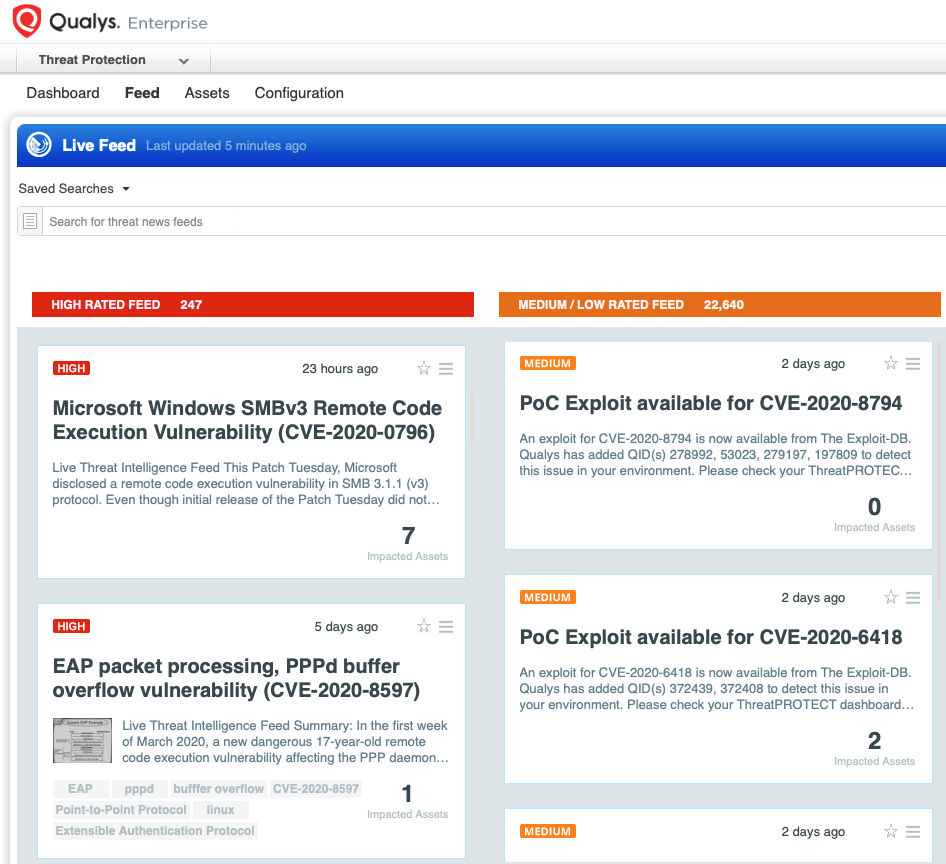
Qualys Threat Protection
Qualys customers can locate vulnerable hosts through Qualys Threat Protection. This helps accelerate identification and tracking of this vulnerability.
Simply click on the impacted assets number to see a list of hosts with this vulnerability.
Workaround
- Disable SMBv3 compression
You can disable compression to block unauthenticated attackers from exploiting the vulnerability against an SMBv3 Server with the PowerShell command below –
Set-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters” DisableCompression -Type DWORD -Value 1 -Force
- Block TCP port 445 at the enterprise perimeter firewall
TCP port 445 is used to initiate a connection with the affected component. Blocking this port at the network perimeter firewall will help protect systems that are behind that firewall from attempts to exploit this vulnerability.
Remediation
Customers should install patch updates KB4551762 for affected operating systems to be protected from this vulnerability.
The biggest confusion with the Vulnerability (including myself at first) is the workaround instructions specifically calling out ‘Servers’. All impacted devices can act as a Server where SMB is concerned as they both run the underlying services of lanmanworkstation and lanmanserver. You can see the latter referenced in the registry path of the workaround, HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters, and therefore you MUST do this on all impacted OS not just Server 1903/1909. This nullifies the ‘wormable’ aspect of this vulnerability spreading unauthenticated between devices. It does NOT protect against a client connecting to a malicious host but this is a less critical issue IMO.
Kudos to the Qualys detection as it appears to account for this by flagging all devices not just the Server OS.
There is now a patch for this vulnerability.
The blog post has been updated with the patch information.
Anyone have an idea when this patch will be available in the patch catalog and machines reporting in? Or maybe I’m not seeing something? I have several dozen hosts reporting this vulnerability in VM but when applying the filter cve:CVE-2020-0796 or KB:KB4551762 in the patch catalog, I can see the KB, but none of my machines are reporting in?
Had posted a query yesterday wondering if this patch was available to my hosts. I had numerous dozens reporting this vulnerability but when looking to patch it using the PM module, even though it was showing in the patch catalog, no hosts in that module were reporting that the patch was missing or installed. Despite the fact that I manually installed it on one test machine i use.
But, a/o this morning, I could actually deploy it to everything. Odd that it took so long? I’ve opened a ticket with support a few days ago when I first discovered this problem.