Implementing the CIS 20 Critical Security Controls: Slash Risk of Cyber Attacks by 85%
If a CISO needed to cut cyber attack risk by 85%, how would this security chief go about accomplishing that? Would the CISO even know where to begin? It’s safe to say that such a mandate would be considered daunting, and maybe even overwhelming.
CISOs are scrambling to protect IT infrastructures whose boundaries are increasingly fluid due to the adoption of mobility, cloud computing, IoT, and other new technologies. They get bombarded daily with information — research studies, threat warnings, vendor announcements, regulatory requirements, industry recommendations. Making sense out of it all is a challenge.
And yet, that dramatic cyber-attack risk reduction is an attainable goal for organizations that apply the first five of the Center for Internet Security’s 20 Critical Security Controls.
This structured and prioritized set of foundational InfoSec best practices offers a methodical and sensible approach for securing your IT environment. It maps effectively to most security control frameworks, government regulations, contractual obligations and industry mandates.
In this blog series, we’ll explain how Qualys Cloud Platform — a single, integrated, end-to-end platform for discovery, prevention, detection, and response — can help security teams of any size to broadly and comprehensively adopt the CIS controls.
Qualys Cloud Platform’s robust, scalable, and extensible architecture powers Qualys’ cloud-based IT security and compliance apps, giving you a continuous, always-on assessment of your global security and compliance posture, with instant visibility across all your IT assets, wherever they reside.
Qualys solutions can provide in-depth assessment and validation of all 20 Critical Security Controls and related technologies to ensure that they are in place, properly configured, and free from vulnerabilities.
In this first installment, we’ll address the first five controls, which provide what CIS calls “foundational cyber hygiene.”
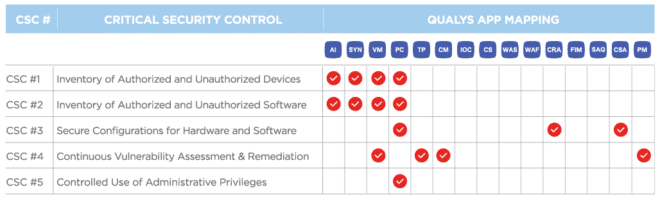
CSC 1 & CSC 2
Inventory of Authorized and Unauthorized Devices:
Actively manage (inventory, track, and correct) all hardware devices on the network so that only authorized devices are given access, and unauthorized and unmanaged devices are found and prevented from gaining access.
Inventory of Authorized and Unauthorized Software:
Actively manage (inventory, track, and correct) all software on the network so that only authorized software is installed and can execute, and that unauthorized and unmanaged software is found and prevented from installation or execution.
These first two controls address the importance of having visibility into your IT environment. You can’t protect — nor defend yourself from — devices and software that you don’t know are in your network. These blind spots are proliferating as organizations adopt technologies and processes that blur traditional network boundaries, making it easy for end users to bypass the IT department, and providing a plethora of intrusion opportunities for hackers.
How Qualys Can Help
Qualys AI helps customers continuously discover systems — both hardware and software — connected to their organizations’ public and private networks, wherever they reside. This powerful solution also maintains critical attributes of assets such as IP address, location, hardware, software information and more, providing instant visibility across your IT environment.
This data is collected using a variety of tools and methods, including Qualys network scanners and Qualys’ groundbreaking Cloud Agents. Qualys AI collects detailed information about assets and their components, and keeps it up to date. It provides fast searching across these attributes using a powerful search engine, and allows you to organize the systems, aligning them with their business purpose.
Tap powerful Qualys asset discovery and classification technology to complement the ServiceNow CMDB, providing detailed data on new and changed IT assets. The data comes from Qualys AI, which leverages Qualys’ highly distributed and scalable cloud platform, and various data collection tools, to compile and continually update a full inventory of your IT assets everywhere: on-premises, in elastic clouds and mobile endpoints.
QUALYS VULNERABILITY MANAGEMENT (VM) AND QUALYS POLICY COMPLIANCE (PC)
Qualys VM and Qualys PC further augment the inventory data from the AI and SYN apps enabling you to manage and track mandatory and prohibited software, operating systems and devices. Each app has out-of-the-box signatures to check detailed requirements, such as specific software details, identification of out of date/end-of-lifed versions, and service status, as well as patch information for critical software.
CSC 3
Secure Configurations for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers
Establish, implement, and actively manage (track, report on, correct) the security configuration of laptops, servers, and workstations using a rigorous configuration management and change control process in order to prevent attackers from exploiting vulnerable services and settings.
This control is about preventing exposure due to misconfiguration. Weak security settings, such as unchanged default passwords, ports inadvertently left open, excessive admin privileges, misconfigured certificates, and faulty authentication processes, are broadly exploited by cyber attackers, and — when breaches occur as a result — consequences include sharp penalties from government regulators.
How Qualys Can Help
Qualys PC is the gold standard for assessing IT security configurations, letting you continuously reduce risk and comply with internal policies and external regulations. Qualys PC provides automated technical control assessment across a wide variety of technologies, including operating systems, network devices, server applications and databases.
With out-of-the-box library content based on industry- and vendor-recommended best practices, such as the CIS Benchmarks and the Defense Information Systems Agency’s (DISA) Security Technical Implementation Guides (STIGs), you can fast-track your compliance assessments, or you can customize your control requirements to suit your unique needs.
Qualys PC helps you prevent configuration drift and meet a variety of regulatory requirements. It provides mandate-based reporting to easily identify areas of concern ahead of audits while optimizing the data collection process using your choice of baseline standards.
With PC, you can prioritize and track remediation and exceptions, demonstrating a repeatable, auditable process for compliance management focused on the most critical issues first.
QUALYS CLOUD SECURITY ASSESSMENT (BETA)
Qualys CSA provides unparalleled visibility and continuous security of public cloud infrastructures so you can identify cloud assets, and assess their configurations against industry best practices from groups like CIS and vendors like Amazon AWS, Microsoft Azure, and Google Cloud. CSA enables businesses to continuously monitor and secure their public cloud infrastructure against misconfigurations, malicious behavior, and non-standard deployments. It integrates with cloud platform providers’ native APIs to continuously discover all resources and provide full visibility into your entire cloud infrastructure. It also provides topological views of the infrastructure and relationships across other cloud resources.
Qualys Certificate Assessment provides visibility and continuous monitoring of SSL/TLS configurations and certificates across all assets, including enabled protocols and cipher suites, along with a score to quickly highlight the security posture of the configuration. It also analyzes the algorithms and key sizes used in those certificates, quickly allowing isolation and remediation of certificates with weaker keys or algorithms.
CSC 4
Continuous Vulnerability Assessment and Remediation
Continuously acquire, assess, and take action on new information in order to identify vulnerabilities, remediate, and minimize the window of opportunity for attackers.
Thousands of new software vulnerabilities are disclosed every year, each one representing a potential opportunity for hackers to break into a network. That’s why organizations must know at all times which vulnerabilities are present in their IT assets; understand the level of risk each one carries; and plan and prioritize remediation of affected IT assets accordingly. This fourth control directs organizations to properly manage vulnerabilities so that they can “immunize” their IT assets against the most common cyber attacks: opportunistic strikes designed to exploit common, disclosed vulnerabilities.
How Qualys Can Help
QUALYS VULNERABILITY MANAGEMENT (VM)
Qualys VM gives you immediate, global visibility into where your IT systems might be vulnerable to the latest threats, and how to protect them. It helps you to continuously secure your IT infrastructure, so that your organization can withstand attacks seeking to exploit unpatched and improperly configured systems.
Qualys VM assigns remediation tickets, manages exceptions, lists required patches for each host, integrates with existing IT ticketing systems, and generates comprehensive reports to help drive remediation of found vulnerabilities.
QUALYS CONTINUOUS MONITORING (CM)
Qualys CM enables customers to receive immediate notifications of newly identified issues in order to proactively address potential problems, providing continuous surveillance of both internal and external hosts, helping infrastructure teams to reduce exposure.
Qualys TP helps you automatically prioritize the vulnerabilities that pose the greatest risk to your organization by correlating active threats against your vulnerabilities. Qualys TP includes a Live Threat Intelligence Feed where Qualys security engineers continuously validate and rate new threats from internal and external sources, highlighting emerging concerns about vulnerabilities that pose an immediate threat to your business, including details about which assets may be affected.
Qualys TP allows teams to quickly visualize which of their systems are exposed to active threats, such as zero-days, denial-of-service attacks, actively attacked vulnerabilities, and easy exploits requiring little skills.
QUALYS PATCH MANAGEMENT (UPCOMING)
Qualys Patch Management (PM) will enable remediation at scale by deploying security patches to operating systems and applications to remediate code-based vulnerabilities.
CSC 5
Controlled Use of Administrative Privileges
The processes and tools used to track/control/prevent/correct the use, assignment, and configuration of administrative privileges on computers, networks, and applications.
Users with administrative privileges are particularly attractive for hackers. Compromising one of those accounts gives intruders broad access within the breached device and network, boosting their ability to do harm. Consequently, InfoSec teams must closely monitor these accounts.
Critical Security Control 5 requires minimizing the use of administrative privileges.
How Qualys can help
Qualys PC account controls provide full visibility into accounts with administrative privileges, so you can validate that they’re being used only where needed. Qualys PC hosts a variety of related out-of-the-box controls to check processes, files and objects for valid permissions. Group membership and rights for Windows systems as well as “User Account controls (UAC)” can also be validated in order to help organizations minimize the use of the administrative accounts/access.
Stay tuned for the next post in our series, where we will cover controls 6 – 10.
To learn more about how Qualys Cloud Platform can help you drastically reduce your organization’s cyber risk and enhance compliance, download the Qualys Guide to Automating CIS 20 Critical Security Controls.

This looks bogus; you are implementing intrusion detection before prevention.
Where is the common sense?
9 out of 10 attacks succeed through human factors: None of the 20 address that risk – how can you claim “85%” when you have already ignored 90% of the problem?