Implementing the CIS 20 Critical Security Controls: Building Upon Foundational Cyber Hygiene
Most successful cyber attacks exploit known vulnerabilities for which patches are available, or take advantage of weak configuration settings that could have been easily hardened. You can significantly lower the risk of being victimized by this type of common, preventable attack by adopting the Center for Internet Security’s Critical Security Controls (CSCs).
This set of 20 structured InfoSec best practices offers a methodical and sensible plan for securing your IT environment, and maps to most security control frameworks, government regulations, contractual obligations and industry mandates.
The CSCs were first developed in 2008 and are periodically updated by a global community of volunteer cybersecurity experts from government, academia and industry. “The CIS Controls provide a prioritized approach to cyber security, starting with the most essential tasks and progressing to more sophisticated techniques,” Tony Sager, CIS Chief Evangelist, wrote recently.
In this blog series, we’re explaining how Qualys Cloud Platform — a single, integrated, end-to-end platform for discovery, prevention, detection, and response — and its Qualys Cloud Apps can help security teams of any size to broadly and comprehensively adopt the CIS controls.
In our first installment, we discussed how Qualys can help organizations slash 85% of cyber attack risk by adopting the first five of the Center for Internet Security’s 20 Critical Security Controls.
“There are 20 CIS Controls in all, and it will take time and effort to implement all of them – but the resulting cybersecurity posture and culture your organization will achieve will make it all worthwhile,” Sager wrote.
This week, we’ll explain the benefits of building upon that “foundational cyber hygiene” with the next five controls.
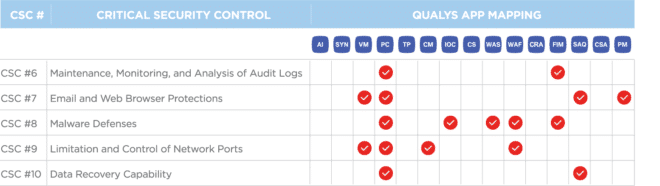
CSC 6
Maintenance, Monitoring, and Analysis of Audit Logs
Collect, manage, and analyze audit logs of events that could help detect, understand, or recover from an attack.
Audit logs are critical because often they provide the only clear evidence of insider or stealthy attacks. For this reason, InfoSec teams must make sure to activate the logging capabilities that come with most operating systems, network services, and firewall technologies. Logs should be comprehensive, accurate, and centrally stored so that they can be mined for insights, audits, and, when needed, incident response.
How Qualys Can Help
Qualys PC helps organizations validate key aspects of audit log configuration on a breadth of technologies including operating systems, network devices (including firewalls), database servers, and other server software.
QUALYS FILE INTEGRITY MONITORING (FIM)
Qualys FIM tracks file changes across global IT systems, including changes to security settings for log files, helping you detect and identify potential tampering with log files and critical settings. FIM logs file modification events centrally, providing another avenue of security event analysis to protect against more complex attacks while also providing a means to enforce change-control policies in your IT environment.
CSC 7
Email and Web Browser Protections
Minimize the attack surface and the opportunities for attackers to manipulate human behavior through their interaction with web browsers and email systems.
Hackers do their best to turn web browsers and email clients into traps to trick end users into performing actions that will help them gain access to their IT environment so it’s crucial for InfoSec teams to secure these two attractive breach vectors.
How Qualys Can Help
QUALYS VULNERABILITY MANAGEMENT (VM)
Qualys VM assesses the vulnerabilities of software on the endpoint with special attention on web browsers and email clients. It will identify out-of-date versions that may no longer be secure and ensure that no required critical patches are missing. It also validates critical ActiveX, Java, Adobe and other plug-in versions to make sure that vulnerabilities are known so they can be patched promptly.
Qualys PC can assess the configurations of the web browsers against CIS benchmark recommendations, to make sure that high-risk settings are disabled that may automatically execute plug-ins, scripts, and other content that can increase risk of compromise.
QUALYS SECURITY ASSESSMENT QUESTIONNAIRE (SAQ)
Qualys SAQ provides out-of-the-box questionnaires which can be distributed to internal and external parties to assess the effectiveness of your training and awareness programs, created to protect against phishing and social engineering methods.
QUALYS PATCH MANAGEMENT (PM) — Upcoming
Qualys Patch Management will ensure that browsers are updated by deploying their most recent version, mitigating the risk that infiltration could occur via human interaction with malicious payloads.
CSC 8
Malware Defenses
Control the installation, spread, and execution of malicious code at multiple points in the enterprise, while optimizing the use of automation to enable rapid updating of defense, data gathering, and corrective action.
Malware is a key component of cyber attacks as it can be used to compromise a wide variety of IT assets and can be deployed via many different avenues, including email attachments, malicious web pages, cloud services and removable media (such as USB devices). Keeping up with the constant change in malware delivery and obfuscation techniques is a significant challenge requiring that a variety of controls be in place.
How Qualys Can Help
QUALYS WEB APPLICATION SCANNING (WAS) AND WEB APPLICATION FIREWALL (WAF)
Qualys WAS and Qualys WAF are natively and tightly integrated for seamless identification and mitigation of risks and offer a complete solution for web app security.
Qualys WAS is a robust DAST (Dynamic Application Security Testing) product whose malware detection functionality scans an organization’s internet-facing websites, and identifies and reports infections, including zero-day threats via behavioral analysis. Detailed malware infection reports are provided for remediation. Meanwhile, Qualys WAF blocks attacks and lets you virtually patch web app vulnerabilities.
QUALYS INDICATION OF COMPROMISE (IOC)
Qualys IOC continuously monitors endpoints to detect suspicious activity, flagging telemetry data that could indicate malware or breaches on devices on and off the network. Analysis, hunting, and threat indicator processing is performed in the cloud on billions of active and past endpoint events. Those results are then coupled with threat intelligence data from Qualys Malware Labs and third-party threat intelligence sources to identify malware infections (indicators of compromise) and threat actor actions (indicators of activity).
Qualys PC allows customers to validate the configuration settings of anti-virus solutions, as well as check the list of running processes and software for potential malicious entries.
QUALYS FILE INTEGRITY MONITORING (FIM)
Qualys FIM can serve as a last line of detection, identifying changes to critical operating system and configuration files that may indicate a targeted attack or specially designed root-kit has been put in place.
CSC 9
Limitation and Control of Network Ports, Protocols, and Services
Manage (track/control/correct) the ongoing operational use of ports, protocols, and services on networked devices in order to minimize windows of vulnerability available to attackers.
Hackers constantly look for remotely accessible network services vulnerable to exploitation, such as poorly configured web, mail, file, and print servers, and domain name system (DNS) servers installed by default on a variety of devices, often without a business need. Many software packages automatically install and activate services without alerting users or administrators. Limiting unnecessary services reduces potential exposures to attack.
How Qualys Can Help
QUALYS VULNERABILITY MANAGEMENT (VM)
Qualys VM scans the organization’s assets for open ports and services, and processes, allowing you to quickly identify services so they can be analyzed for importance.
CM, an add-on to VM, enables you to receive immediate notification when new issues are identified on internal and external hosts, such as a new port, service, or other identified software, allowing teams to rapidly address potential problems.
Qualys PC assesses the organization’s hosts from the inside-out, to make sure that only required services and applications are running and that initial baseline configurations remain constant. Unnecessary ports and services that should be blocked or disabled are quickly identified.
QUALYS WEB APPLICATION FIREWALL (WAF)
Qualys WAF is an inline virtual appliance that terminates both client-side and server-side traffic on a single NIC. In addition to Secure Shell (SSH) for admin purposes, it opens http/s sockets on requested TCP ports (TCP 80, 443 or any transposed port).
CSC 10
Data Recovery Capability
The processes and tools used to properly back up critical information with a proven methodology for timely recovery of it.
After compromising machines, attackers often make significant changes to configurations and software, and subtle alterations to data, potentially jeopardizing organizational effectiveness with polluted information. After the attack is detected, it can be extremely difficult for organizations without a trustworthy data recovery capability to remove all traces of the attacker’s presence on the machine. Good backup and recovery practices are key for incident recovery.
How Qualys Can Help
Qualys PC assesses key configuration settings related to backups and restore features for a variety of technologies, such as databases and server applications. For example, if backup for a SQL database is enabled, then replication is enabled. The presence of mandatory software, such as backup software, can also be confirmed.
QUALYS SECURITY ASSESSMENT QUESTIONNAIRE (SAQ)
Qualys SAQ provides out-of-the-box questionnaires that can be used to assess backup and restore processes and procedures. Critical details of the disaster recovery process can be collected and validated against internal policies and best practices.
Stay tuned for the next post in our series, where we will cover controls 11 – 15.
To learn more about how Qualys Cloud Platform can help you drastically reduce your organization’s cyber risk and enhance compliance, download the Qualys Guide to Automating CIS 20 Critical Security Controls.