Securing your Cloud and Container DevOps Pipeline
Organizations are aggressively moving workloads to public cloud platforms, such as Amazon’s AWS, Google Cloud, and Microsoft’s Azure, upping the ante for InfoSec teams, which must protect these new environments.
Driving this growth in cloud computing adoption is its essential role in digital transformation initiatives, which help businesses be more efficient, effective, flexible and innovative in areas like e-business, supply chain management, customer support and employee collaboration.
Digital transformation projects are typically delivered using web and mobile apps created in DevOps pipelines, where developers and operations staff work collaboratively at every step of the software lifecycle, releasing apps or app updates frequently.
But security must be integrated throughout the DevOps process — planning, coding, testing, releasing, deploying, monitoring — in an automated way, organically building it into the software lifecycle instead of bolting it on at the end.
That way, vulnerabilities, misconfigurations, policy violations, malware and other safety issues can be addressed before code is released, reducing the risk of exposing your organization and your customers to cyber attacks.
In a recent webcast, Hari Srinivasan, Qualys’ Director of Product Management for Cloud and Virtualization Security, explained how Qualys can help you secure your cloud and container deployments across your DevOps pipeline.
DevSecOps: Automating security
DevSecOps engineers must ask themselves a number of key questions regarding the automation of security checks in the DevOps development and deployment pipeline, according to Srinivasan.
Atop the list is whether their team is able to identify vulnerabilities and other security issues during the appdev build process, so that they can be remediated at this stage. Second is to find out if the necessary security checks can be automated and meshed into the DevOps CI/CD (continuous integration / continuous deployment) tool chain.
Also important: Determining whether it’s possible to obtain security information that the application owner and the developers can understand and act upon. And last but not least is to see if security information can be transmitted downstream for processing in SIEM and ticket systems.
Qualys secures DevSecOps in clouds
There are three main uses cases Qualys supports for securing DevOps in cloud deployments.
First, after integrating Qualys into your DevOps pipeline, you’ll be able to obtain a clear picture of the vulnerabilities and mis-configurations of your operating systems and web applications. Second, you’ll be able to remediate these security problems before launching an app or a chunk of code into production. Finally, you’ll have the chance to place the lightweight and versatile Qualys Cloud Agent into your DevOps environment to provide continuous monitoring.
For example, in an AWS environment, after creating AMI (Amazon Machine Image), you spin up sample instances and run Qualys scans on them.
After identifying and fixing the vulnerabilities and mis-configurations, you would end up with a hardened AMI base instance, and proceed to seed a Qualys Cloud Agent on it, before releasing it to production.
“Because Qualys Agents are lightweight, they’re extremely suited for embedding into an image, and provide instant visibility when these environments are deployed,” Srinivasan said.
Qualys functionality for vulnerability management, policy compliance and web application scanning is supported via REST APIs so you can programmatically integrate it with your DevOps tools.
Once AMIs have been released live, Qualys helps you monitor and track their security posture via dynamic and interactive dashboards in which you can search and tag instances based on attributes, and use pre-built or custom widgets to monitor deployments.
“There’s one widget you can add that tracks if there are instances that are being spun up from an unapproved AMI,” Srinivasan said.
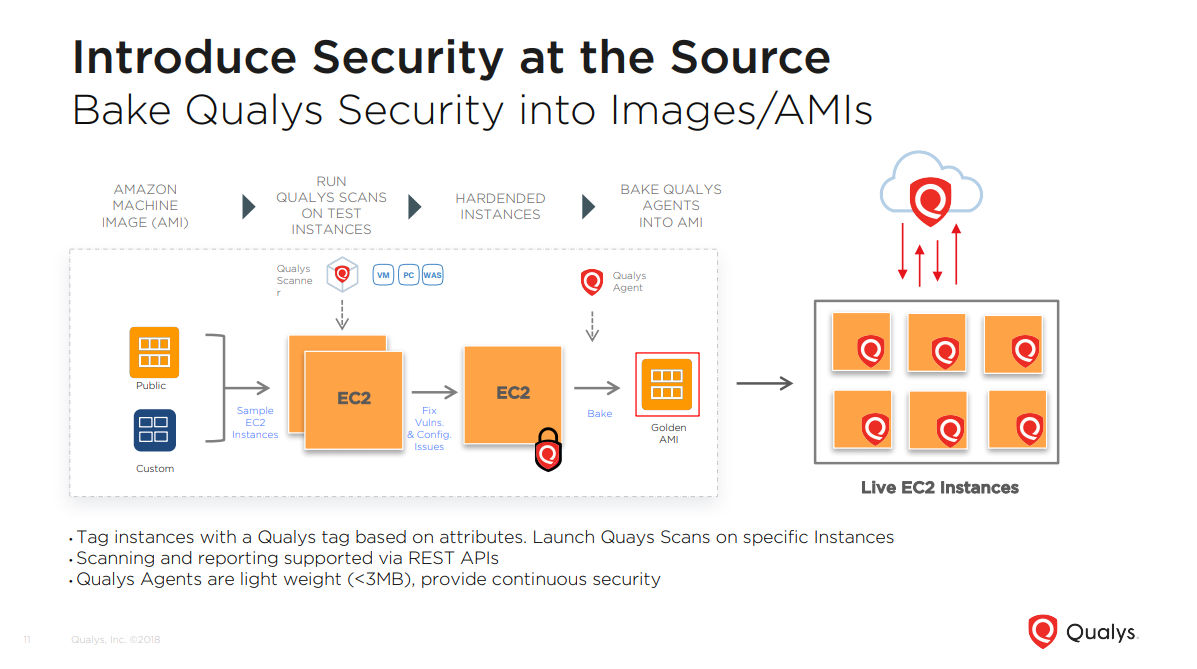
In addition, the Qualys Cloud Connector for AWS continuously discovers instances and collects their metadata including AMIs using API integration. Connectors may be configured to connect to one or more AWS accounts with user-provided, read-only credentials. That way, they can automatically detect and synchronize changes to virtual machine instance inventories from all Amazon EC2 Regions and Amazon VPCs.
As with AWS, Qualys has similar native integrations with Microsoft Azure and Google Cloud Platform to do vulnerability management, policy compliance, malware detection, web app scanning and other critical tasks on your cloud instances.
How Qualys secures containers in DevOps
If the elasticity, agility and speed of virtualized cloud environments are a challenge, container technology takes everything up a notch. Docker containers churn much faster than virtual machines, and are much more lightweight because, unlike VMs, they can be spun up without provisioning a guest operating system for each one.
This is a big reason for their raging popularity in DevOps teams, as they let developers create and deploy applications more quickly and efficiently, and with an increased level of portability. Applications can be smaller, often focused on one or a few capabilities, and be more easily distributed across an IT environment.
Qualys Container Security, now in beta, has been designed to help InfoSec teams for continuous discovery, tracking and protection of containers in DevOps pipelines and deployments at any scale. “It provides you with total visibility and continuous security for containers,” Srinivasan said.
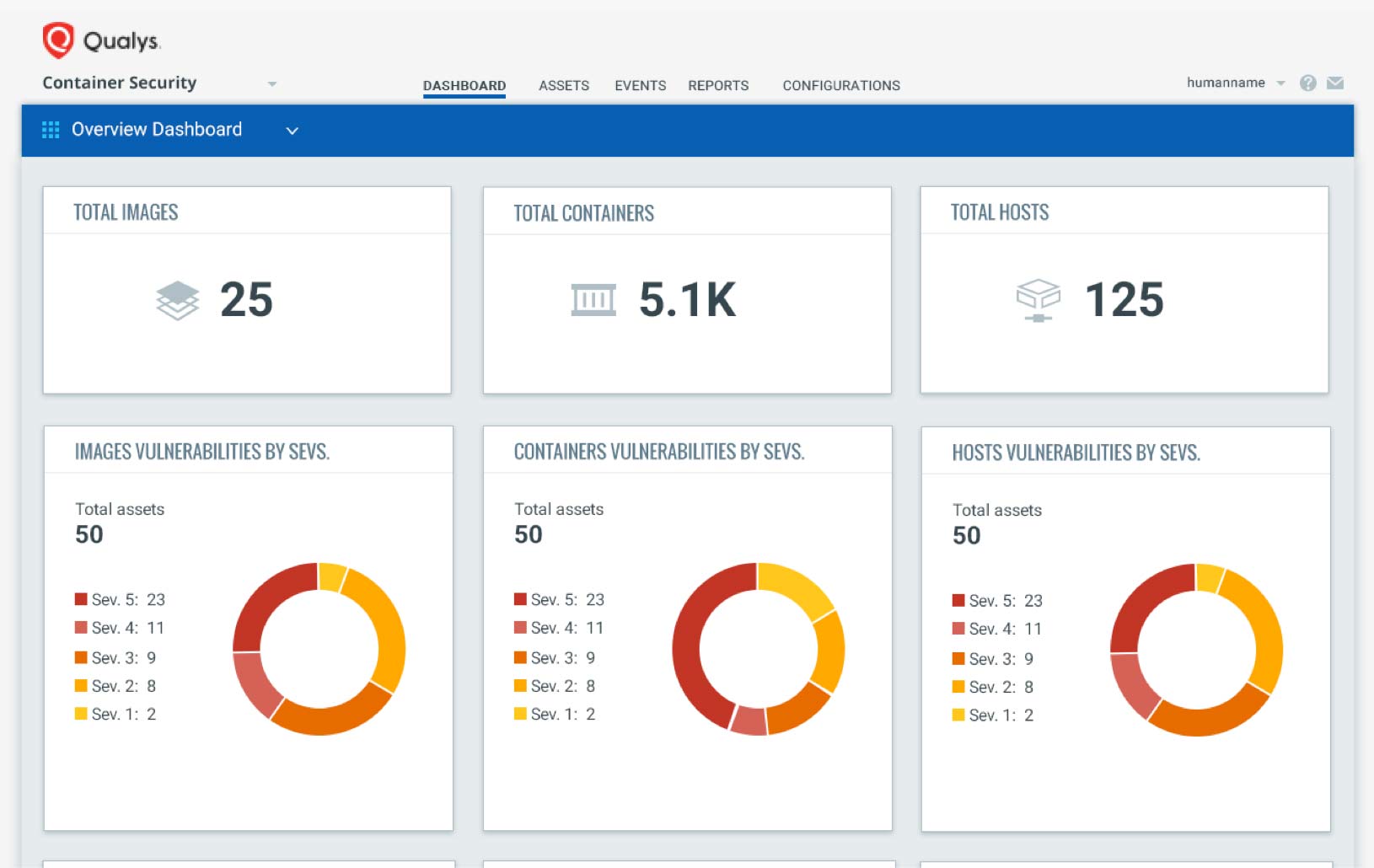
Specifically, Qualys CS offers:
- Discovery, inventory, and near-real time tracking of container events
“With Qualys CS, you can identify the environment where containers are deployed, the source of those containers, and where these images are stored. You can also ensure that discovery is being done on a continuous basis,” he said.
- Vulnerability analysis for image registries and containers
Qualys CS provides high accuracy vulnerability scanning of images, registries and containers in addition to the underlying host operating system, across the complete chain. This includes a plug-in for Jenkins which users can use to identify the vulnerabilities in the images in the build process.
- Event and change tracking
“Qualys CS gives you the ability to identify what events are happening in those container environments, and who’s making the change, so it provides you with an audit trail of events,” he said. With that information in hand, you can flag malicious behavior, raise alerts and do anything else necessary to mitigate the issues.
- REST APIs integration
All Qualys CS functionality is available via APIs so you can integrate that with your CI/CD toolchain.
In addition, Qualys CS features a native container sensor, which is distributed as a Docker image. Users can download and deploy these sensors directly on their container hosts, add them to the private registries for distribution, or integrate them with orchestration tools for automatic deployment across elastic cloud environments.
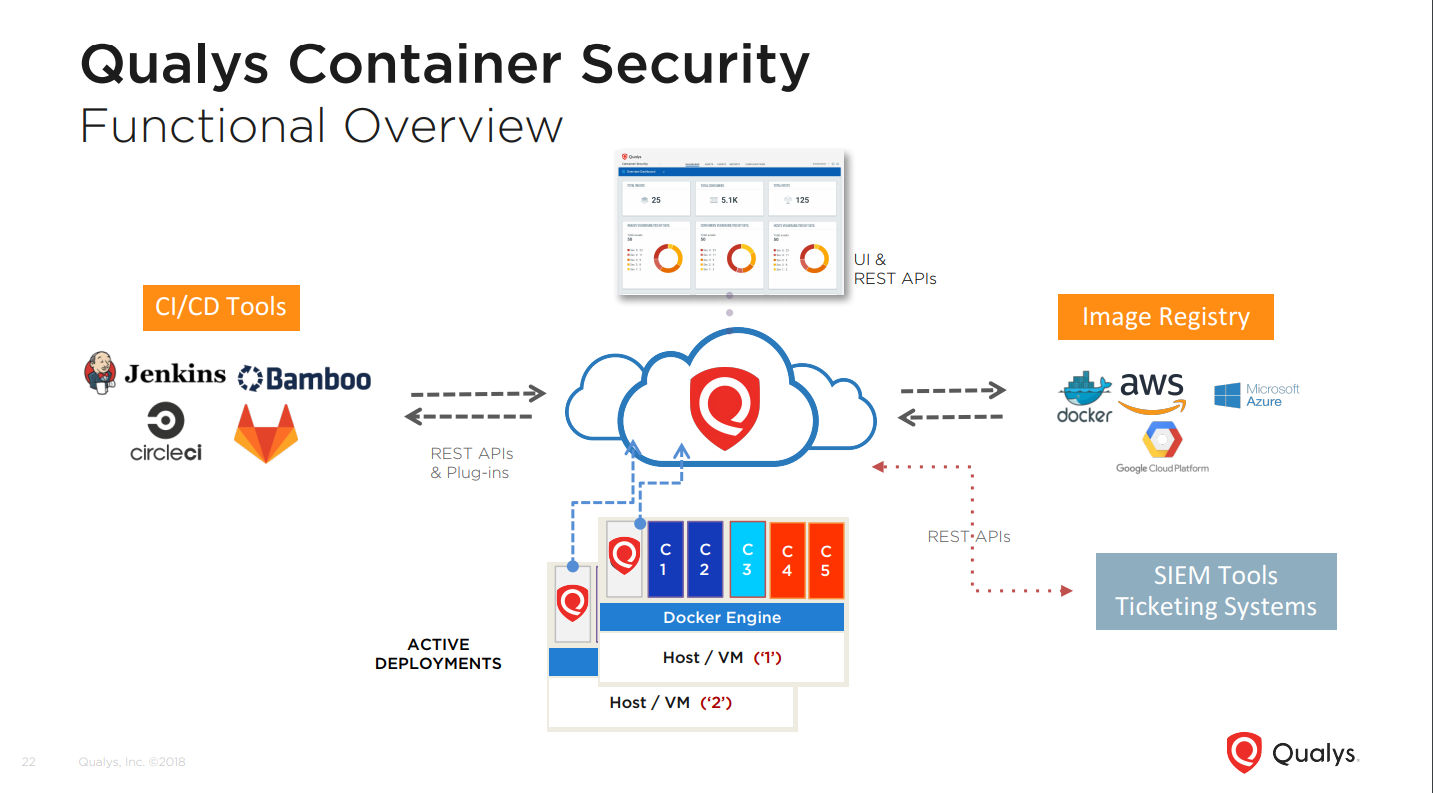
“Qualys Container Security provides you with an automated capability of continuously assessing security across the complete pipeline, be it the ‘build’, be it the ‘registry’ where images are hosted, and additionally the ‘runtime’ environment,” Srinivasan said. “It spans across the entire pipeline chain.”
The release also includes a Jenkins plug-in for vulnerability analysis. The entire feature is available as REST APIs for both the CI/CD tool chain integration and also the for the southbound tools like ticketing systems and SIEM tools.
We invite you to listen to a recording of the webcast, which has a lot more details about these topics and about Qualys Container Security, as well as a live demo of the product and a Q&A session with the audience.
See all of the presentations in the Continuous Security and Compliance Webcast Series.